
This morning, NBC released a scorching article on #APT41’s campaign to steal Covid relief funds from U.S. State Governments, based on a @SecretService investigation. 🧵
nbcnews.com/tech/security/…
nbcnews.com/tech/security/…
.@rufusmbrown and I spoke on this very topic @labscon_io (video coming we’re told), as a continuation of research we published in March of 2022 on a persistent #APT41 campaign to gain access into U.S. State Government networks.
mandiant.com/resources/blog…
mandiant.com/resources/blog…
Our initial research uncovered new 0-days, malware variants, updates to their tried-and-true toolset, and more, all to gain access to state government networks. So much net new, but one question we persistently (heh) lost sleep over was WHY? What were they after? 

The search for this answer was the topic of our #LabsCon22 talk. We presented evidence that pointed towards #APT41 wanting something to do with state benefits data:
In one environment, #APT41 deployed #LOWKEY malware on an app server responsible for financial benefits. #LOWKEY was configured to listen for requests to specific URLs, which in this case, matched the benefits app name allowing their C2 traffic to blend in. 

One of the first questions we asked was, how many states use this benefits app? Scan data gave us an idea, but it also gave us something else… Of all servers we found, one stood out a bit… because it was the only one not in the U.S. 

Inspecting the server further, we found:
1. a custom web app leaking PII data for US citizens belonging to one state.
2. A custom Baidu map with pins located in the Xindu Province of Chengdu.
Neat, but we didn’t see this server used firsthand, so no attribution to #APT41 :(
1. a custom web app leaking PII data for US citizens belonging to one state.
2. A custom Baidu map with pins located in the Xindu Province of Chengdu.
Neat, but we didn’t see this server used firsthand, so no attribution to #APT41 :(

At separate victim, nearly HALF of all systems infected with #DEADEYE malware were associated to this benefits app. #APT41 clearly invested time fortifying themselves into this part of the network. In this same victim, we also found another nifty malware, #FASTPACE....
FASTPACE (aka skip2.0), initially reported on by @ESETresearch in 2019, was one of the first MSSQL backdoors documented. In the report, #FASTPACE targeted MSSQL versions 11/12 while the one we found targeted version 13, showing continued dev investment into this capability.
FASTPACE equipped #APT41 with powerful capabilities, including stealthy in-mem database manipulation, access to user accounts without proper auth, and disabling logging. This was the very first time we observed #FASTPACE being used in an intrusion. 

At yet ANOTHER victim, #APT41 heavily targeted these same state benefits servers. Even after eradicating #APT41 from several victims, they would quickly re-compromise and immediately resume targeting of benefits servers. 
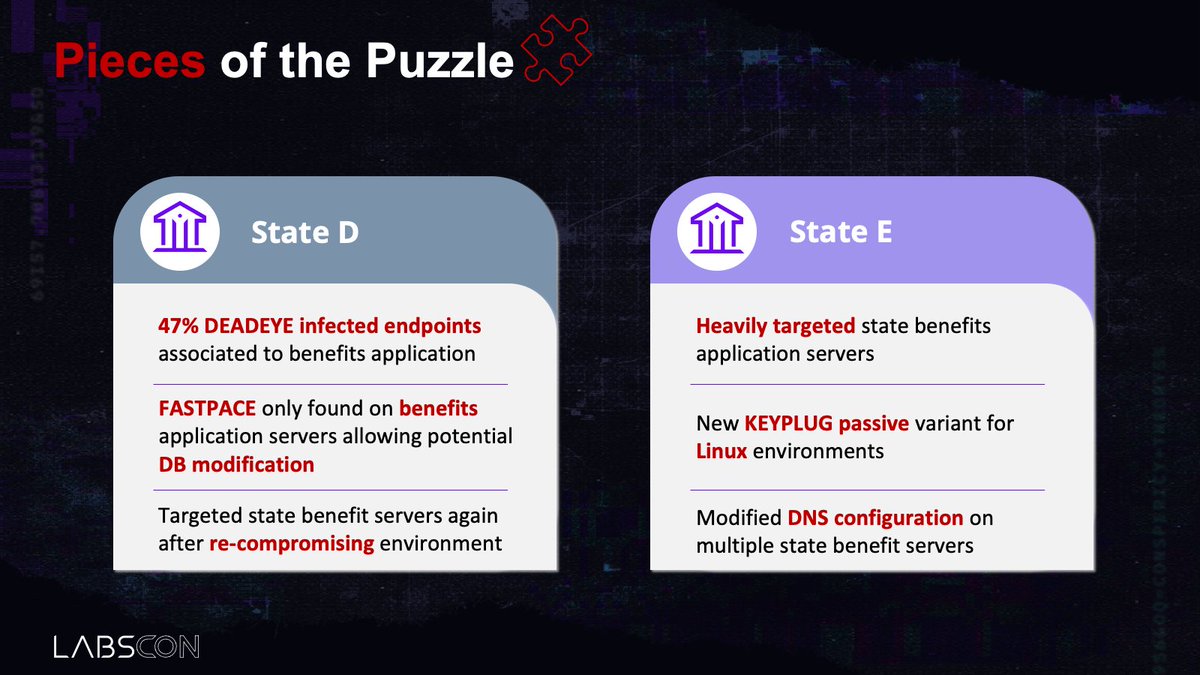
Along with deploying their malware on these servers, we found evidence of them tampering with DNS configurations to capture backend API auth requests to these applications. To do this, they first deployed the LINUX variant of #KEYPLUG on these servers.
Then, they modified the /etc/hosts files to point to #APT41 C2. Any auth traffic to this specific API would then re-route to #APT41. On the server was an x509 certificate masquerading as this specific API domain to further disguise the redirection. 

Existing access to these benefits servers + traffic interception of critical API calls/auth requests would provide APT41 all the crucial tools/data to manipulate contents, or do whatev ¯\_(ツ)_/¯
Everything, in totality, pointed towards #APT41’s ardent desire to hit U.S. state gov benefits data. Although we’re closer to answering our initial question of WHY, I don’t think we’re truly satisfied or ever will be, even with the additional details uncovered in the NBC article.
In this investigation, our main focus has been on what we don’t know, but what we do know is this marks a clear escalation and further signifies #APT41 is undeterred from their September 2020 indictments.
• • •
Missing some Tweet in this thread? You can try to
force a refresh




