📣🧵#reInvent RECAP: Key Security Launches
Did you miss our big event in Las Vegas? Don't worry. We got you covered. Here's what's newly launched for all things security🔐
See below (in no particular order)⬇️
Did you miss our big event in Las Vegas? Don't worry. We got you covered. Here's what's newly launched for all things security🔐
See below (in no particular order)⬇️
New for #AWSControlTower – Comprehensive Controls Management makes it easier for regulated customers to make AWS available for use by their developers. Use it to apply managed preventative, detective, and proactive controls to accounts
go.aws/3P9ChLV
go.aws/3P9ChLV

#AmazonSecurityLake automatically centralizes security data from cloud, on-premises, and custom sources into a purpose-built data lake stored in your account. Automate your central management of security data
go.aws/3VTSR4O
go.aws/3VTSR4O

#AmazonGuardDuty now offers threat detection for Amazon Aurora to identify potential threats to data stored in Aurora databases
go.aws/3UAFCVx
go.aws/3UAFCVx

#AmazonMacie automated data discovery is a new capability that allows you to gain visibility into where your sensitive data resides on #AmazonS3 at a fraction of the cost of running a full data inspection across all your S3 buckets
go.aws/3Fv9ZrX
go.aws/3Fv9ZrX

#AmazonInspector support for Lambda Functions enables unified, continuous, and automated security vulnerability assessments for applications running on AWS Lambda
go.aws/3P4h8mg
go.aws/3P4h8mg

#AWSVerifiedAccess a new secure connectivity service that allows enterprises to enable local or remote secure access for their corporate applications without requiring a VPN
go.aws/3P7c00H
go.aws/3P7c00H

XKS is a feature of #AWSKMS that uses keys stored in systems outside of AWS. Store AWS KMS customer managed keys on a hardware security module that you operate on premises or at any location of your choice
go.aws/3VDObjA
go.aws/3VDObjA

#AmazonVerifiedPermissions allows you to focus on building simple authorization policies and your applications—instead of building an authorization engine for your multi-tenant consumer applications
Follow @AWSIdentity for more ➕
go.aws/3HfmGsb
Follow @AWSIdentity for more ➕
go.aws/3HfmGsb

#AWSWickr is an end-to-end encrypted enterprise communications service that offers advanced security features and facilitates one-to-one chats, group messaging, voice and video calling, file sharing, screen sharing, and more. Collaborate more securely📱
go.aws/3VFhdPW
go.aws/3VFhdPW

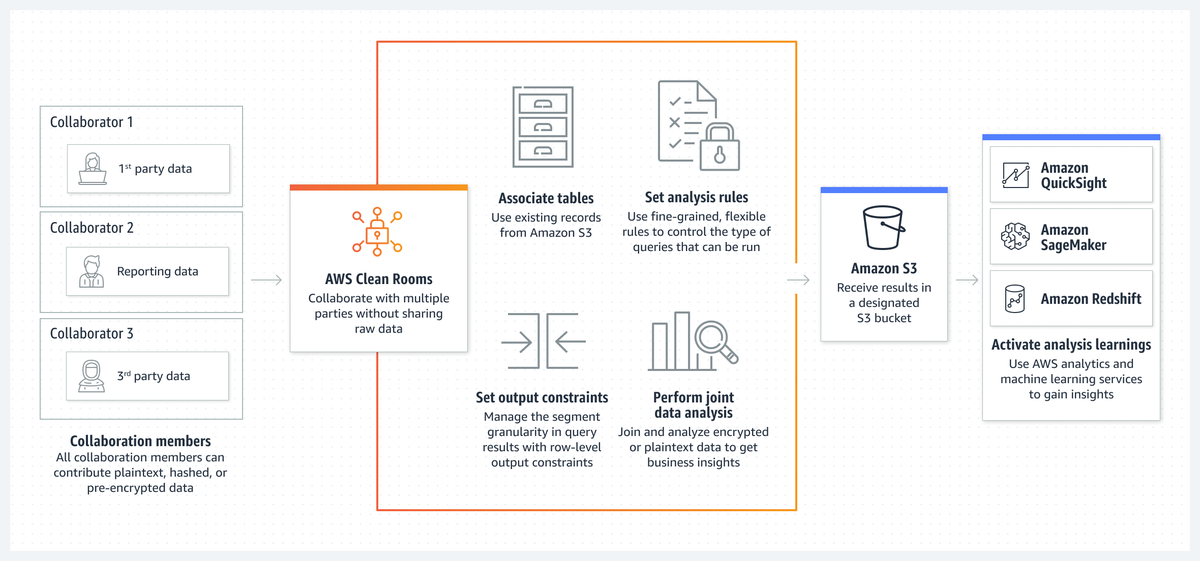
#AWSCleanRooms allows users to analyze and collaborate on datasets with business partners without revealing underlying data 🧹
go.aws/3Bal1jN
go.aws/3Bal1jN
Thanks for joining us at #reInvent! See you next year 👋
Follow @AWSSecurityInfo and the AWS Security blog for more updates on security services, trends and best practices 👇
go.aws/3uskXrV
Follow @AWSSecurityInfo and the AWS Security blog for more updates on security services, trends and best practices 👇
go.aws/3uskXrV
• • •
Missing some Tweet in this thread? You can try to
force a refresh








