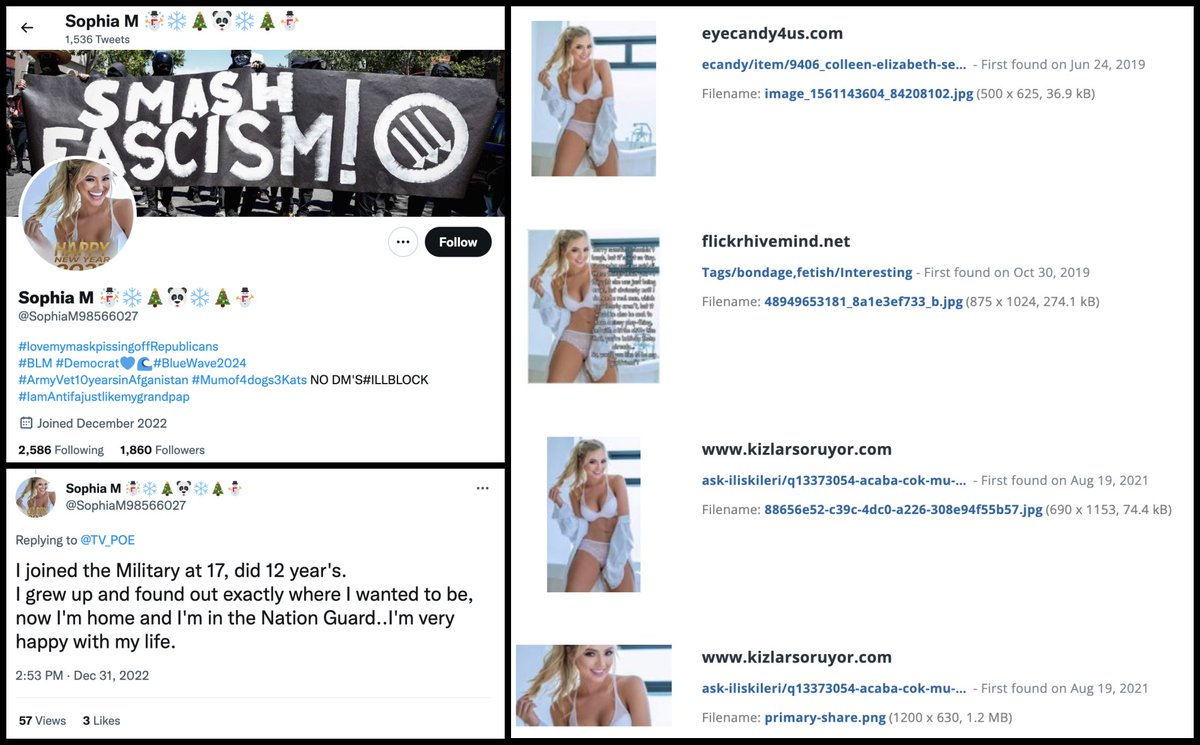
About three years ago, a bunch of accounts with GAN-generated faces moved their companies to Las Vegas, where their companies were nearly destroyed. #NewYearsShenaniGANs
(GAN = "generative adversarial network", the AI technique used by thispersondoesnotexist.com)
cc: @ZellaQuixote
(GAN = "generative adversarial network", the AI technique used by thispersondoesnotexist.com)
cc: @ZellaQuixote

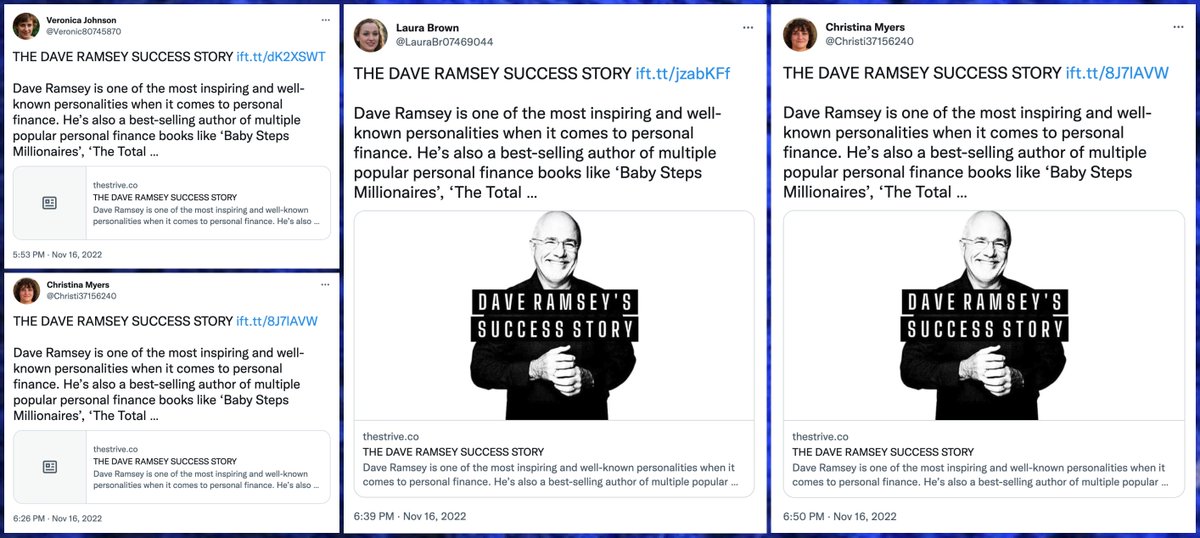
The duplicate tweets about moving a company to Las Vegas are from a botnet consisting of 37 accounts created on Sept 28th/29th, 2022. All 37 accounts have GAN-generated face pics, and (with the exception of a few early tweets) all tweet exclusively via automation service IFTTT. 





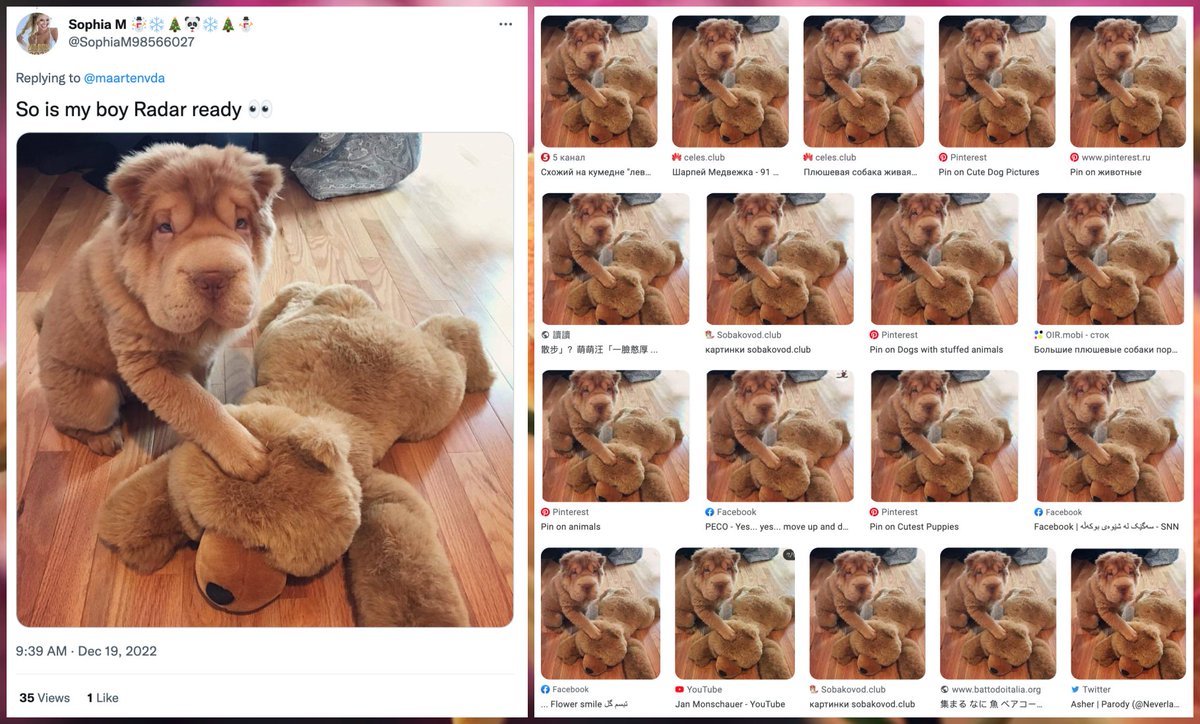
GAN-generated face pics (at least, the ones in common usage generated by StyleGAN) have the telltale trait that the major facial features (especially the eyes) are in the same location on every image. This becomes obvious when the images are blended together.
The content tweeted by this botnet is repetitive, with tweets being duplicated verbatim across multiple accounts. Most of the tweets appear to be fragments of articles published by Success magazine. 


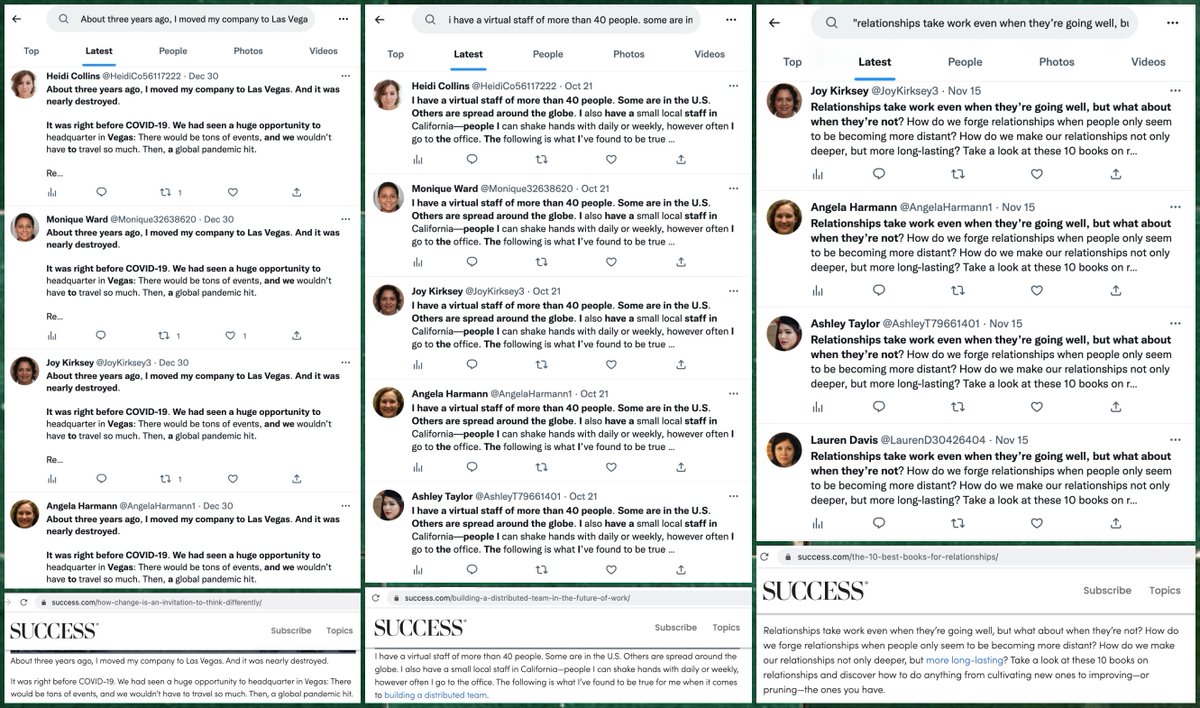
In addition to the repetitive tweets copied from Success magazine, this network also occasionally tweets links to two websites - strive(dot)co and teamfearless(dot)com. These tweets are infrequent - only 253 of the network's 9165 tweets (2.8%). 
More on GAN-generated profile pics and their use on Twitter and other platforms here:
Some tips for identifying GAN-generated profile pics:
https://twitter.com/conspirator0/status/1322704400226394112
Some tips for identifying GAN-generated profile pics:
https://twitter.com/conspirator0/status/1457051817699860483
• • •
Missing some Tweet in this thread? You can try to
force a refresh