Part 2 - Crypto 🧵
While Bitcoin launched in 2008, it relied on architecture whose blueprint had been created at least a decade earlier. The fundamental building block of that architecture is what is known as a hashing algorithm.
While Bitcoin launched in 2008, it relied on architecture whose blueprint had been created at least a decade earlier. The fundamental building block of that architecture is what is known as a hashing algorithm.
In the 1990s, the Secure Hash Algorithm (SHA), the predecessor to Bitcoin’s hash function, was created by NSA. The details of this algorithm were released in a 1993 paper and quickly adopted by the National Institute of Standards and Technology (NIST). 



Much like Crypto AG machines, hashing functions take a text input and ‘scramble’ it.
But while a message sent through a Crypto AG device was designed to be decodable at the other end with the right key (ie. machine settings), information sent through a hash function cannot.
But while a message sent through a Crypto AG device was designed to be decodable at the other end with the right key (ie. machine settings), information sent through a hash function cannot.

This is because hash functions are designed to be irreversible—known as a one-way or “trap-door” function—and discard information during hashing. Despite this, every piece of information leaves an imprint on the final output, ensuring each message digest is unique.
However unlike Crypto AG, hashing functions typically do not rely on secret algorithms—they’re public. These functions instead derive security through irreversibility. A secure hash is easy to verify, but inspecting the output cannot tell you what input was used to create it. 

As a result, hash functions are not a form of encryption but a form of cryptographic security.
So then what is a hash function’s purpose if all it does is transform a block of text of any length into a unique string of 64 seemingly random characters?
So then what is a hash function’s purpose if all it does is transform a block of text of any length into a unique string of 64 seemingly random characters?
A hash can be thought of as a digital certificate of authenticity.
Consider a contract that is 1,000 pages long. That contract could be digitally digested to produce a unique 64-digit hash. If even a single comma were changed, the resulting hash would be completely different.
Consider a contract that is 1,000 pages long. That contract could be digitally digested to produce a unique 64-digit hash. If even a single comma were changed, the resulting hash would be completely different.
Another common use is in protecting stored passwords: storing plain text passwords is entirely insecure. But hashed passwords can be stored securely and easily verified while remaining impossible to reverse.
So how does all this hashing relate to Bitcoin?
The primary purpose of hashing in Bitcoin is to digest the transactions completed over the bitcoin network down into a verifiable distributed ledger known as the blockchain.
The primary purpose of hashing in Bitcoin is to digest the transactions completed over the bitcoin network down into a verifiable distributed ledger known as the blockchain.
The blockchain is a digital archive of every transaction ever completed by the Bitcoin network. While it’s commonly thought that Bitcoin is ‘anonymous’, all transactions completed over the network are in full view of anyone with the tools to explore the blockchain. 



Multiple independent nodes process this ledger of all transactions through the hashing algorithm and compare their results. New blocks of transactions are added to the ledger only when the hash values agree across the majority of nodes.
To incentivize this validation work, “block rewards” of Bitcoin currency are paid to nodes in transaction fees. This process of validating the blockchain ledger through hashing and receiving a reward is known as mining.
The computational goal of mining is to digest the hash of the current ledger of transactions and add a “nonce” (Number ONly used onCE) such that the combined resulting hash value comes in below a specified threshold, which is currently a hash that begins with 17 zeros.
As there’s no way to extrapolate a nonce that will combine to produce a target hash, miners must try values at random. Assuming a rate of one try per second, mining one block would take 600x the current age of the universe.
The enormous computing power this number of guesses requires is known as “proof of work”, and is primarily responsible for the gargantuan energy demands of most cryptocurrencies. Despite this, Bitcoin is designed around a system of mining rewards that diminishes over time. 


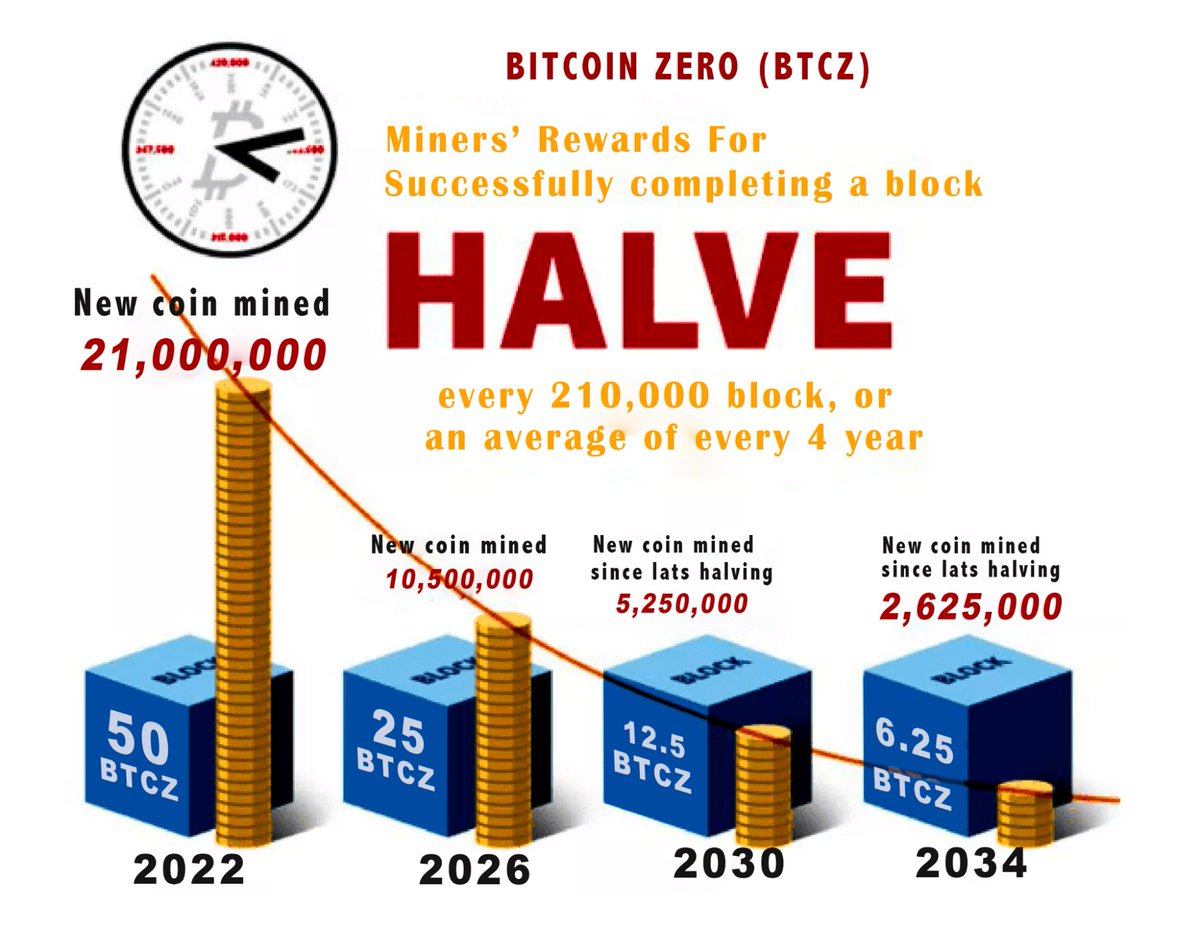

This ‘halving’ of rewards accomplished 2 things: it allowed early miners to amass a disproportionate share of available coins and created an artificial scarcity, driving up the price over time. As a result, early adopters became Bitcoin ‘oligarchs’
So who mined the first blocks?
So who mined the first blocks?
In October 2008, ‘Satoshi Nakamoto’ released the infamous Bitcoin white paper, outlining the cryptocurrency's technical specs and motivations. Described as a peer-to-peer network “for electronic transactions without relying on trust," Bitcoin began circulating a few months later. 

Satoshi was the earliest prolific miner of Bitcoin. Some of these initial coins were given away for free during Bitcoin’s early days to encourage adoption but the vast majority of these original coins were never distributed by Satoshi and remain unspent to this day. 
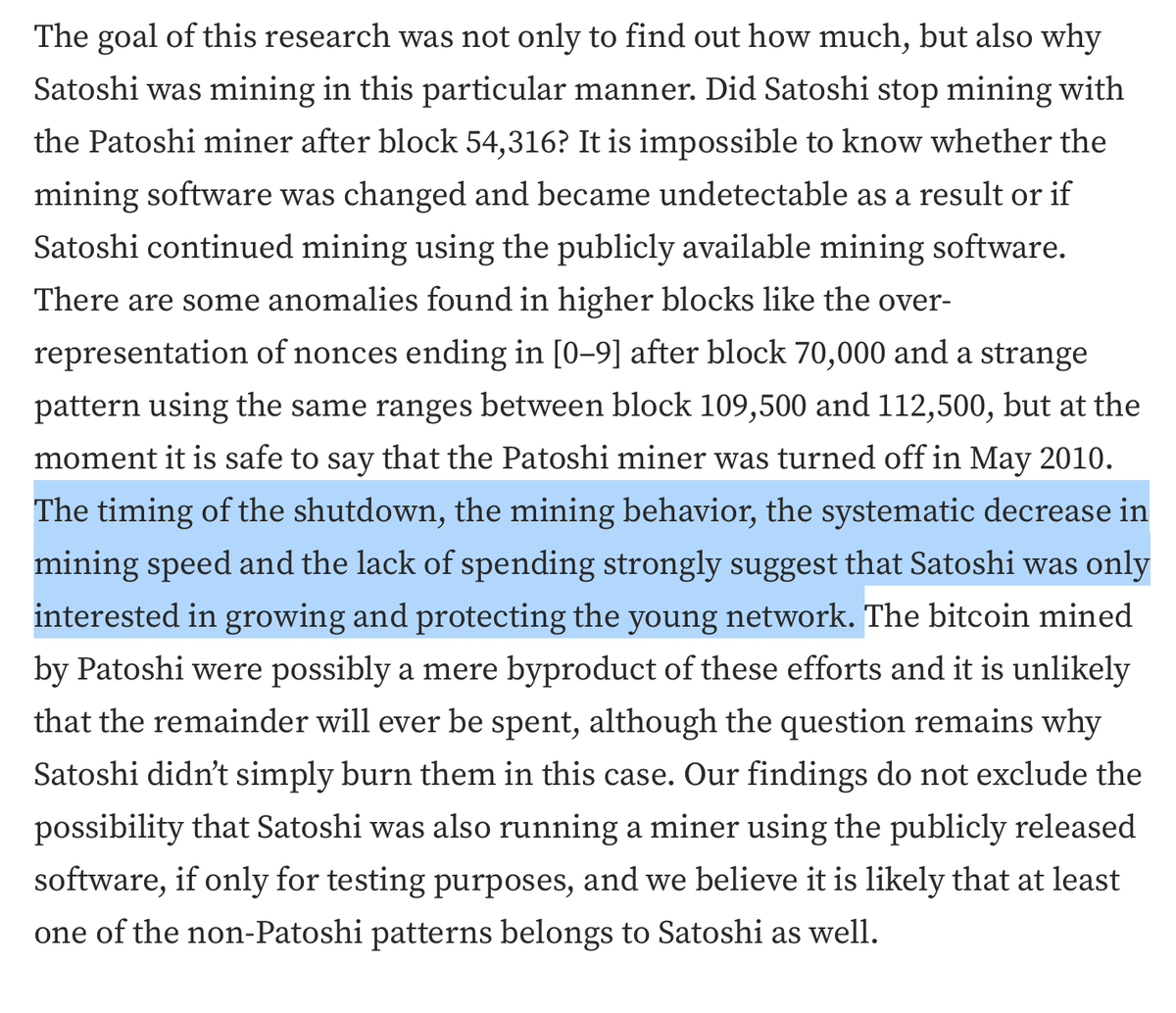
In fact, it is estimated that Satoshi still owns wallets containing ~1.1 million of the ~19 million total coins mined to date. At the current value of $23,000 per coin, Satoshi’s Bitcoin holdings are worth $25 BILLION, placing him among the top 50 wealthiest people in the world. 


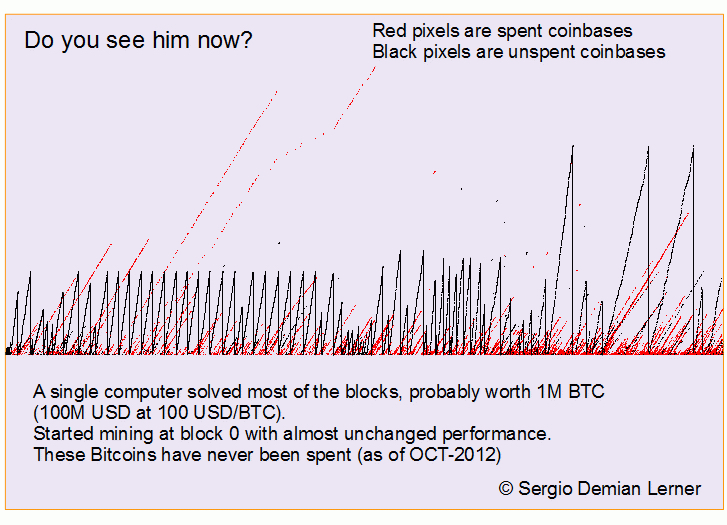
In December 2010, Satoshi insisted that Bitcoin not be used to fund Wikileaks, the whistleblowing portal exposing govt corruption. One of his last posts expressed his desire to de-emphasize his role as the “mysterious founder” of Bitcoin. Shortly after, he disappeared forever. 


Since then, the mysterious Satoshi has never come forward. The myth of Satoshi has since become entrenched in cryptocurrency lore as a die-hard crusader for ‘open-source’ currency, who took a stand for privacy and against financial centralization and burdensome regulation.
Some even believe the name ‘Satoshi Nakamoto’, long presumed to be a pseudonym, may have been a tongue-in-cheek reference to the CENTRAL INTELLIGENCE Agency itself. 

Whoever Satoshi was, it’s hard to imagine a better time to have launched. Bitcoin was born against the backdrop of the most dramatic global stock market collapse in history, a calamity from which public confidence in centralized banking has never fully recovered.
During the first few years after Bitcoin’s launch, coins traded for pennies. But with the emergence of the Silk Road in Feb 2011, a portal for buying and selling illicit drugs online, Bitcoin finally found a use. As a result, its price skyrocketed from 30¢ to $30 in 6 months.
But since the collapse of the Silk Road in 2013, Bitcoin has largely remained a purely speculative asset marked by an ever-increasing series of boom & bust cycles initiated by massive fraud: the Mt.Gox exchange collapse, the 2018 crypto crash, and the FTX collapse. 

By late 2021, the price of a single coin reached an all-time high of over $67k. Despite these sky-high valuations, there’s no indication the wild price spikes were fueled by demand for an alt 𝘤𝘶𝘳𝘳𝘦𝘯𝘤𝘺, since total transactions have remained relatively stable since 2016. 


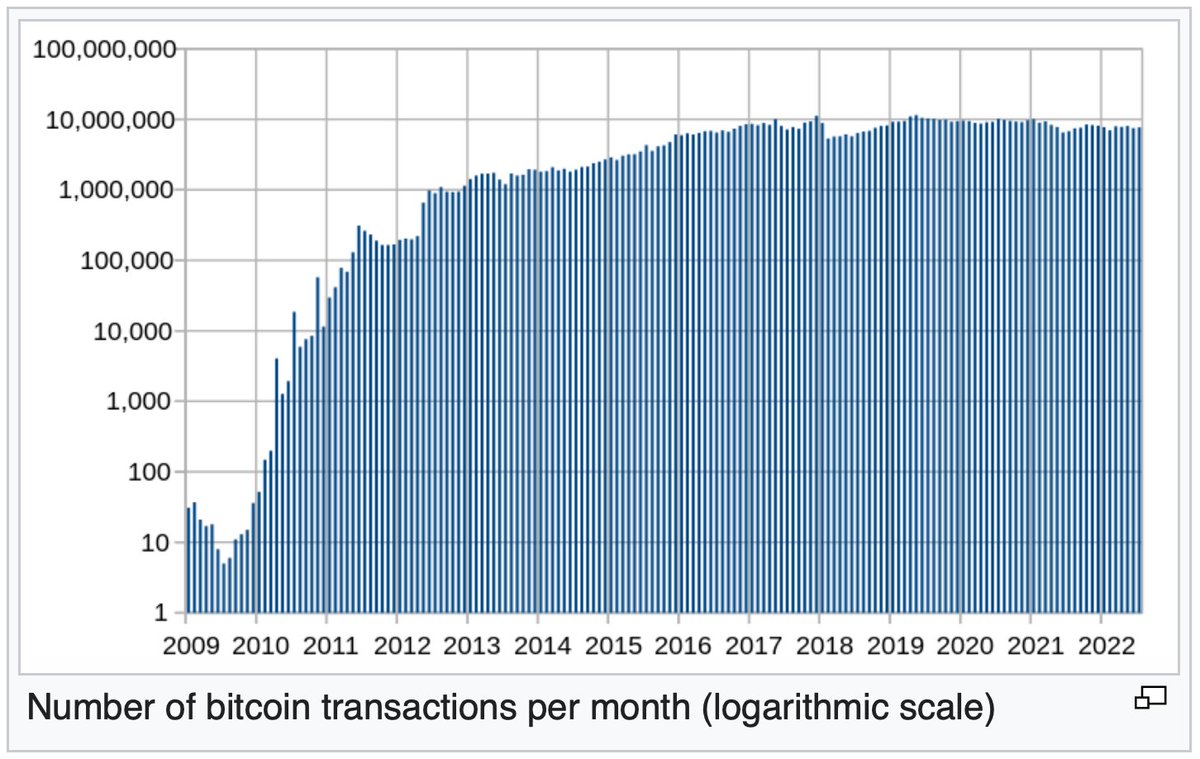
Instead, the price spikes of bitcoin heavily indicate that most of the BTC held are for speculative reasons—demonstrated in 2020 when Bitcoin surged from <$10,000 to >$60,000 in the 12 months after the Federal Reserve rolled out a 3 trillion dollar bailout of the investor class. 

But possibly the most suspicious yet lesser known aspect of how Bitcoin works is the way it generates cryptographic keys for transactions, using a relatively new type of cryptography called asymmetric or ‘public-key cryptography.’
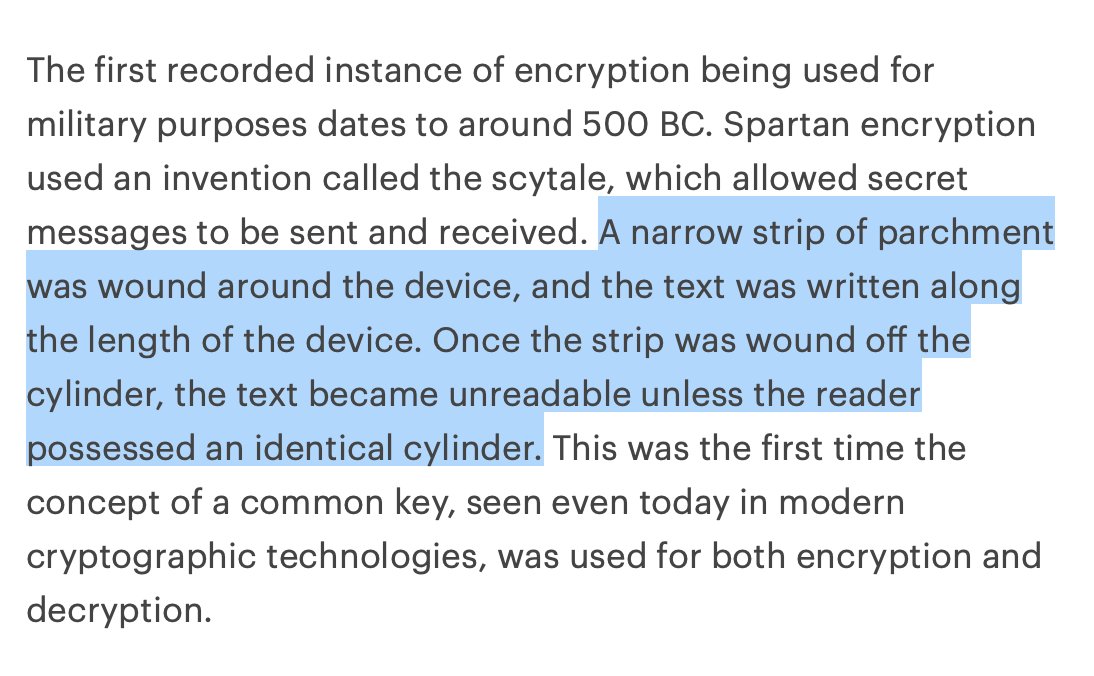
From ancient Egypt all the way through to Crypto AG, symmetric-key cryptography had been the dominant mode of cryptography. But with the advent of modern computing, this new method of public-key cryptography became possible.
A symmetric key is used to both encrypt and decrypt, and thus must be shared between sender and recipient. This makes this type of encryption computationally simple yet vulnerable since sharing this common key exposes it to being intercepted.
By contrast, asymmetric key encryption uses the recipient's public key to encrypt but their private key to decrypt. Crucially, the private key need not be known by the sending party. This decentralizes authentication, eliminating the need for a trusted exchange of keys. 


So how does this relate to Bitcoin?
At the time of launch, Bitcoin’s developers had two broad methods available to generate these asymmetric public & private keys: RSA and Elliptic Curve Cryptography (ECC).

At the time of launch, Bitcoin’s developers had two broad methods available to generate these asymmetric public & private keys: RSA and Elliptic Curve Cryptography (ECC).


Developed in the 1970s, RSA is one of the oldest public key cryptosystems. It derives its security through factorization of very large prime numbers. Despite resulting in larger keys, RSA is still the most widely used public-key method for securing communication online. 


ECC—developed by Neal Koblitz in the 1980s—generates keys using simple mathematically defined curves, allowing much smaller seed keys than RSA for equivalent security. Reduced computational intensity is partly why ECC became the basis for most cryptocurrencies, including Bitcoin. 
Both methods can generate a public key from a private key without revealing the private key, thus, both were suitable for verifying transactions.
But starting in the 1990s, the NSA blatantly began backing ECC over RSA.

But starting in the 1990s, the NSA blatantly began backing ECC over RSA.


When Satoshi released his paper laying out the blueprint for Bitcoin in 2008, it featured an ECC that Bitcoin still uses today, called secp256k1. Many crypto experts have remarked on this unusual choice, as at the time secp256k1 was not well researched.
Just one year earlier, researchers had proven it was possible to construct ECCs to create a kleptographic backdoor in a better known curve called ‘Dual_EC_DRBG’. Once discovered by the crypto community, NIST promptly withdrew Dual_EC_DRBG from its guidelines. 

But in 2013, NSA whistleblower Edward Snowden leaked documents indicating the NSA deliberately inserted cryptographic backdoors as part of its BULLRUN decryption program, and had even paid RSA Security $10 million to insert a compromised curve into their encryption software. 



The leaked Snowden docs definitively demonstrated that the NSA had been developing and pushing for backdoors in at least some of the ECC class of crypto, developed by Koblitz, the co-author of the algorithm central to generating Bitcoin’s public and private keys. 



As yet, no similar vulnerabilities have emerged in Bitcoin’s encryption.
But a mere month before Satoshi released his Bitcoin paper, Koblitz released a paper of his own in which he lavished praise on both ECC crypto and the NSA. The timing could not have been more suspect.
But a mere month before Satoshi released his Bitcoin paper, Koblitz released a paper of his own in which he lavished praise on both ECC crypto and the NSA. The timing could not have been more suspect.

Why did the creator of ECC crypto release a paper praising what is now known to be at least partially backdoored? And did Satoshi get 'lucky' and just happen to choose an ECC standard that wasn’t backdoored? Or was there something more sinister at work?
• • •
Missing some Tweet in this thread? You can try to
force a refresh