
1/ #QuasarRAT 🐀 was observed being delivered via #OneNote. Shoutout to @dr4k0nia for helping me with deobfuscating the "injector" ✏️ and showing me some .NET dark arts.
C2: ghcc.duckdns[.]org:4782
Extracted configuration: github.com/RussianPanda95… twitter.com/i/web/status/1…



C2: ghcc.duckdns[.]org:4782
Extracted configuration: github.com/RussianPanda95… twitter.com/i/web/status/1…

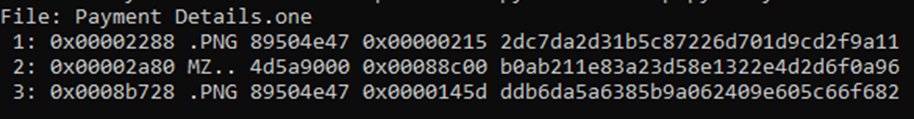


@dr4k0nia 2/
➡️Dropped CAB file: %temp%\OneNote\16.0\Exported\{3990CE71-148C-4B04-8347-A8BB7F676C8D}\NT\0\view.EXE
➡️Dropped VBS payload: %temp%\IXP000.TMP\new.vbs"
➡️Dropped CAB file: %temp%\OneNote\16.0\Exported\{3990CE71-148C-4B04-8347-A8BB7F676C8D}\NT\0\view.EXE
➡️Dropped VBS payload: %temp%\IXP000.TMP\new.vbs"

@dr4k0nia 3/ The cab file extracts and executes new.vbs file (MD5: f7e7099eea0cc25fc49d04cd53c573a1), which retrieves the PowerShell script from hxxps://transfer[.]sh/get/MHXbtP/ss.ps1 (404 now) but you can still grab the script from VT (MD5: 970aca768e68faa580f758a1a379686b)
@dr4k0nia 4/
The PS script contains the .NET payload that comes with QuasarRAT and the injector.
The VBS file is 300 MB and contains a lot of garbage data. My laptop CPU couldn't handle me scrolling down to find the right thing, so a bit of a struggle there 😄
The PS script contains the .NET payload that comes with QuasarRAT and the injector.
The VBS file is 300 MB and contains a lot of garbage data. My laptop CPU couldn't handle me scrolling down to find the right thing, so a bit of a struggle there 😄
• • •
Missing some Tweet in this thread? You can try to
force a refresh




