Breaking assumptions tend to cause interesting effects...
Lets mess with processes- ill likely post code later
POC: raw.githubusercontent.com/jonaslyk/temp/…
Lets mess with processes- ill likely post code later
POC: raw.githubusercontent.com/jonaslyk/temp/…

Allright - ever wondered what are the assertions for image file of a running a process?
pretty much nothing is safe to assume- its impossible to link a running process to its "origin data".
pretty much nothing is safe to assume- its impossible to link a running process to its "origin data".
The file locks are easily bypassed(as unprivileged) and involving a filesystem driver is not even a requirement.
In the posted poc i use webdav to programmatically write the content of the emulated file used for spawning the "forked" copy.
In the posted poc i use webdav to programmatically write the content of the emulated file used for spawning the "forked" copy.
then i use the variation between what is a valid path in win32 vs nt - a nt path can contain 0x00 just fine- win32, not so much.
Normally NTFS will limit the imagenames to valid NTFS chars though.
Normally NTFS will limit the imagenames to valid NTFS chars though.
but there is no NTFS involved here- so I spawn the process with just 0x00 for name.
I use NtCreateUserProcess directly, skipping win32 layer- that would make it impossible.
I use NtCreateUserProcess directly, skipping win32 layer- that would make it impossible.
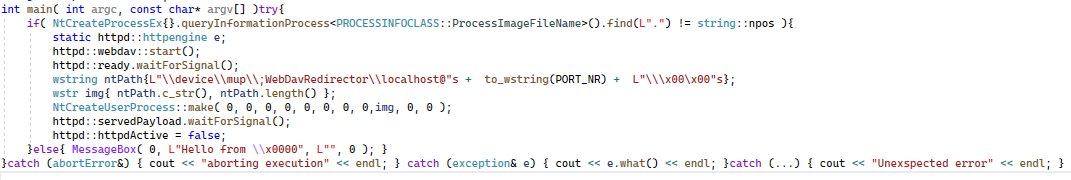
every tool i tried errors in diferent ways, system informer is 100% nr. 1 at providing relevant and correct info though 
• • •
Missing some Tweet in this thread? You can try to
force a refresh