
#redteam tip: @Fortinet self protection bypass
Fortinet is using minifilter to prevent copying or deleting files in the app's installed location.
If you Reverse engineer the responsible driver, You will notice that there are some exceptions


Fortinet is using minifilter to prevent copying or deleting files in the app's installed location.
If you Reverse engineer the responsible driver, You will notice that there are some exceptions


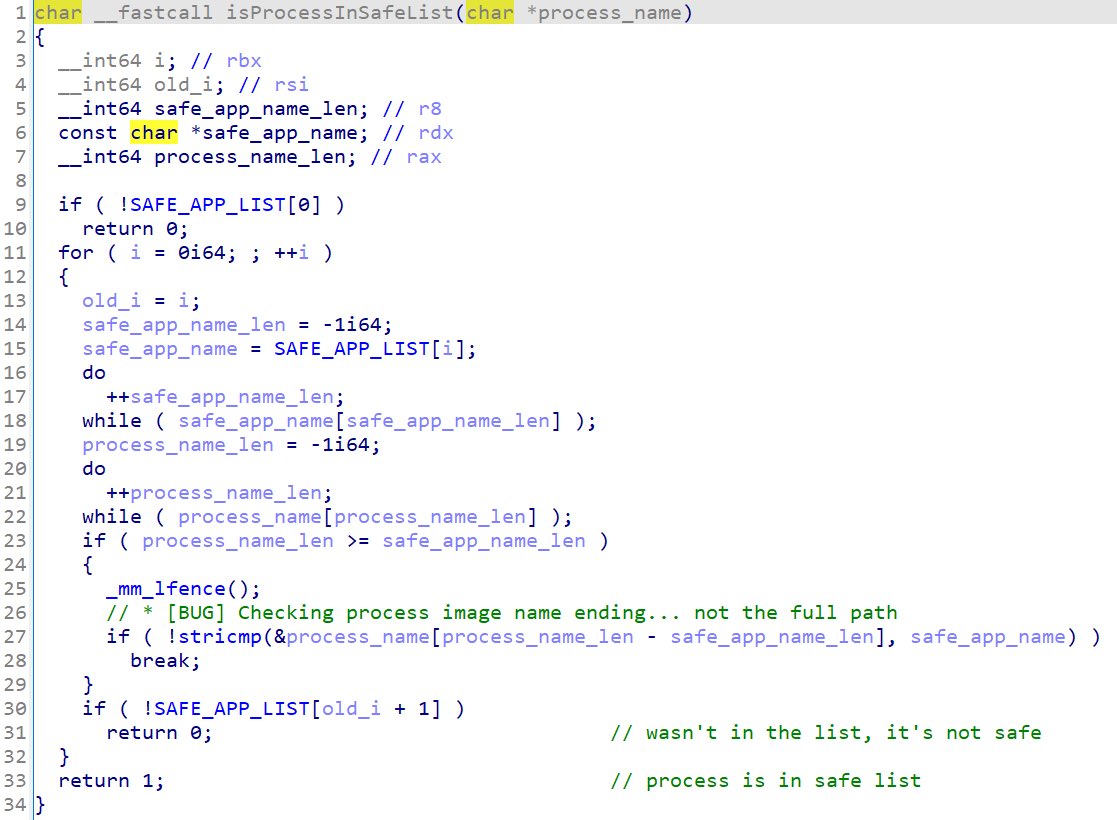
and some processes are able to copy/delete files in that location.
But the problem is that "it is only checking the end of the process image name and not the full path".
Since many fortinet exe files has dll hijack vulnerability and runs as a service, using this vulnerability
But the problem is that "it is only checking the end of the process image name and not the full path".
Since many fortinet exe files has dll hijack vulnerability and runs as a service, using this vulnerability
you can run your code as NT AUTHORITY/SYSTEM or all the users who logs in to the system.
And also it can be used as a persistent method.
Or even by hooking some functions, you will be able to get the server, username and password of the VPN that the user connects to.
And also it can be used as a persistent method.
Or even by hooking some functions, you will be able to get the server, username and password of the VPN that the user connects to.
There is always such simple problems in the popular applications. Maybe there is same bug in some others apps if you just check them :)
Many thanks to @NtCreateThread
Many thanks to @NtCreateThread
• • •
Missing some Tweet in this thread? You can try to
force a refresh




