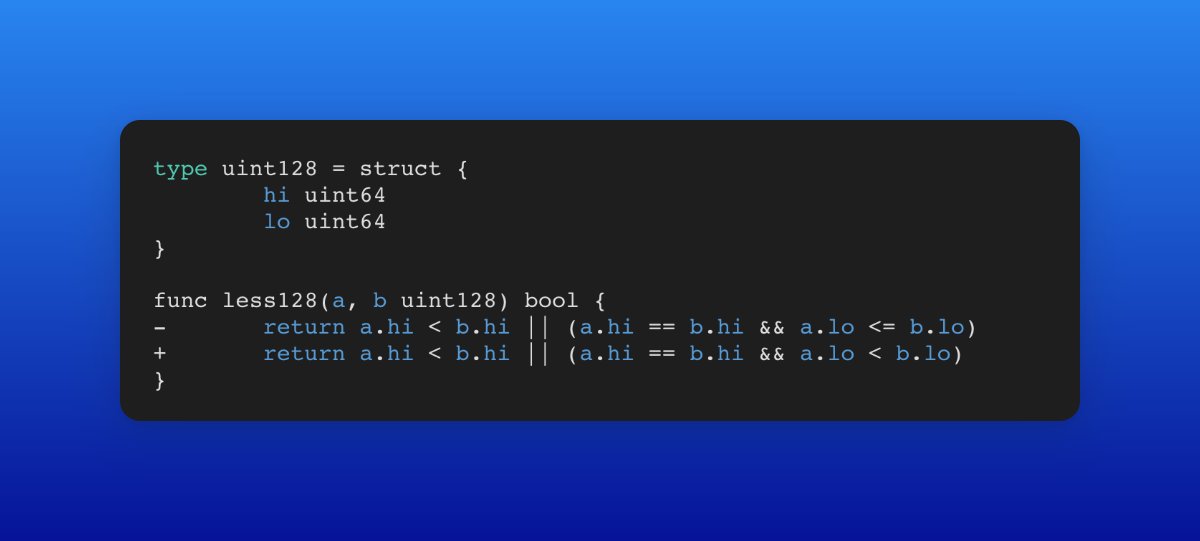
1. Session, Cookie, JWT, Token, SSO, and OAuth 2.0 - here's what you need to know
These terms are essential for identifying, authenticating, and authorizing users online. Let's dive in👇
These terms are essential for identifying, authenticating, and authorizing users online. Let's dive in👇

2. WWW-Authenticate
🔹 Oldest & most basic method
🔹 Browser asks for username & password
🔹 Lacks control over login life cycle
🔹 Rarely used today
🔹 Oldest & most basic method
🔹 Browser asks for username & password
🔹 Lacks control over login life cycle
🔹 Rarely used today
3. Session-Cookie
🔹 Server maintains session storage
🔹 Browser keeps session ID
🔹 Works mainly with browsers, not mobile app friendly
🔹 Server maintains session storage
🔹 Browser keeps session ID
🔹 Works mainly with browsers, not mobile app friendly
4. Token
🔹 Compatible with mobile apps
🔹 Client sends token to server for validation
🔹 Compatible with mobile apps
🔹 Client sends token to server for validation
5. JWT (JSON Web Token)
🔹 Standard representation of tokens
🔹 Digitally signed & verifiable
🔹 No need to save session info server-side
🔹 Standard representation of tokens
🔹 Digitally signed & verifiable
🔹 No need to save session info server-side
6. SSO (Single Sign-On) & OAuth 2.0
🔹 SSO: Log in once, access multiple sites
🔹 Uses CAS (central authentication service)
🔹 OAuth 2.0: Authorize one site to access info on another
🔹 SSO: Log in once, access multiple sites
🔹 Uses CAS (central authentication service)
🔹 OAuth 2.0: Authorize one site to access info on another
Subscribe to our system design newsletter to get a Free System Design PDF (158 pages): blog.bytebytego.com 
Like/Retweet the first tweet below to share the learning:
https://twitter.com/sahnlam/status/1639129932713562112
• • •
Missing some Tweet in this thread? You can try to
force a refresh