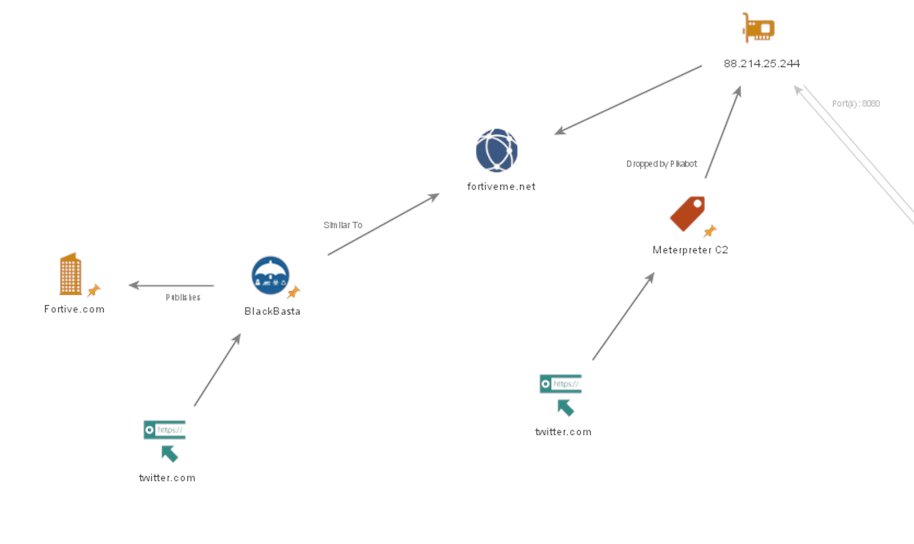
1/ New #MuddyWater 🇮🇷Infra detected; moves to #Metasploit and #HPAnywhere/#Teradici tool added?
@GroupIB_TI released a great report detailing MuddyWater’s use of SimpleHelp Remote Support Software. They tracked the #APT's infrastructure using Etags.
Let's take a look! 🧐 👇👇
@GroupIB_TI released a great report detailing MuddyWater’s use of SimpleHelp Remote Support Software. They tracked the #APT's infrastructure using Etags.
Let's take a look! 🧐 👇👇

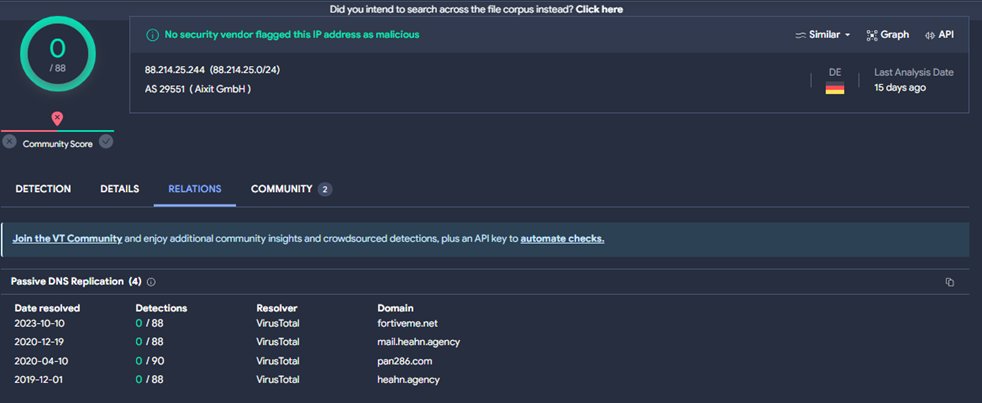
2/ First Etag(153): 🔟results.
First IP of interest: 👉164.132.237[.]67
If we now pivot on the SSH hash, we match on another IP:
👉3.6.222[.]144.
Looking at this IP, the SSL certificate presented mentions O=Teradici Corporation...
First IP of interest: 👉164.132.237[.]67
If we now pivot on the SSH hash, we match on another IP:
👉3.6.222[.]144.
Looking at this IP, the SSL certificate presented mentions O=Teradici Corporation...

3/ Teradici (now HP Anywhere) allows for remote access to machines from any PCoIP client. 💻⬅️🌐⬅️💻
Indicating that MuddyWater may also be using HP’s Anywhere/Teradici as well as SimpleHelp?🧐
Indicating that MuddyWater may also be using HP’s Anywhere/Teradici as well as SimpleHelp?🧐

4/ Using the hash presented by this IP you can find another 176 hosts on the internet:
👉http.html_hash:-1480707872
Searching for “ssl:Teradici” you find 2060 hosts!
HP Anywhere/Teradici is a remote desktop software: teradici.com, using PCoIP technology.

👉http.html_hash:-1480707872
Searching for “ssl:Teradici” you find 2060 hosts!
HP Anywhere/Teradici is a remote desktop software: teradici.com, using PCoIP technology.

5/ Second IP of Interest:
👉164.132.237[.]65
Open port 10443 but no banner information...if we pivot off of that hash we return 36 results.
Looking at the first IP:
👉 44.202.249[.]7
It also has the default Sliver C2 port 31337 open, including SSL certificate settings:👇

👉164.132.237[.]65
Open port 10443 but no banner information...if we pivot off of that hash we return 36 results.
Looking at the first IP:
👉 44.202.249[.]7
It also has the default Sliver C2 port 31337 open, including SSL certificate settings:👇


6/ Issuer: CN=operators, Subject: CN=multiplayer.
Building a Shodan search returns 287 results!
See Michael K’s thread 🔥 on hunt Sliver C2 here:
Additionally IP 5.34.180[.]39 has a MetaSploit certificate on port 3790:
CN=MetasploitSelfSignedCA
Building a Shodan search returns 287 results!
See Michael K’s thread 🔥 on hunt Sliver C2 here:
https://twitter.com/MichalKoczwara/status/1645002394734845956
Additionally IP 5.34.180[.]39 has a MetaSploit certificate on port 3790:
CN=MetasploitSelfSignedCA

7/ Third IP of interest: 137.74.131[.]29:443.
Has interesting header when pivoted from returns 17 results, first being a MetaSploit C2 - 164.132.237[.]79. This IP is hosted on the same ISP subnet as 3 previously reported MW C2’s by GIB. 🔥👉This IP hasn’t been identified as MW.

Has interesting header when pivoted from returns 17 results, first being a MetaSploit C2 - 164.132.237[.]79. This IP is hosted on the same ISP subnet as 3 previously reported MW C2’s by GIB. 🔥👉This IP hasn’t been identified as MW.


8/ This IP does share hostname:
👉6nc110821hdb[.]co
with 51.255.19[.]178 which is a SimpleHelp server attributed to MW.
👉IP: 137.74.131[.]24 is a MuddyWater IP address. The domain nc6jan20pol[.]co is shared across this and another IP.
👉6nc110821hdb[.]co
with 51.255.19[.]178 which is a SimpleHelp server attributed to MW.
👉IP: 137.74.131[.]24 is a MuddyWater IP address. The domain nc6jan20pol[.]co is shared across this and another IP.
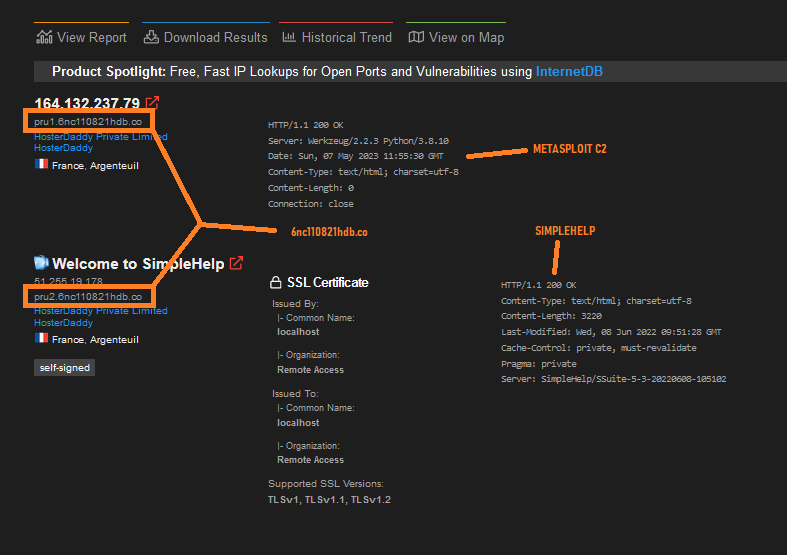
9/ This IP was using the same Etag reported by GIB but now doesn’t return in that search, instead can still be found by the header or a hostname search. 

10/ (Last one)
The Last IP of interest: 👉149.202.242[.]85. This IP is also running Metasploit with port 3790 open.
More evidence of change by MuddyWater to use MetaSploit.
Interesting changes (MetaSploit and Teradici) since the Group-IB report. Thanks for reading! 🙂
The Last IP of interest: 👉149.202.242[.]85. This IP is also running Metasploit with port 3790 open.
More evidence of change by MuddyWater to use MetaSploit.
Interesting changes (MetaSploit and Teradici) since the Group-IB report. Thanks for reading! 🙂

@MichalKoczwara @TLP_R3D @RustyNoob619 @GroupIB_TI @Gi7w0rm @1ZRR4H @thehappydinoa @BridewellCTI @BushidoToken @Kostastsale
• • •
Missing some Tweet in this thread? You can try to
force a refresh