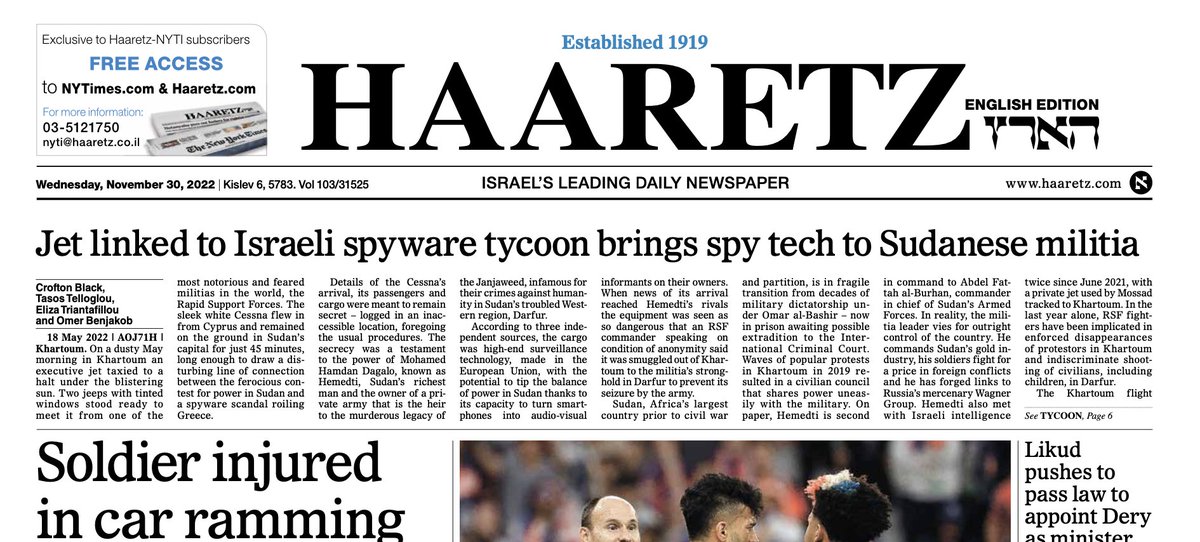
🚨SCOOP: My new @Haaretzcom investigation reveals new Israeli cyber companies developed technology that exploits the heart of the online economy - ads - not just for mass surveillance, but also to hack phones 👇
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🚨This is surveillance capitalism at its finest! The world of "digital arms" has evolved, moving into the realm of ad-based intelligence (AdInt). This is how this next-gen digital weapon leaked into the private cyber arms sector >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🏁There's a digital arms race taking place over the last 5 years to use ads not just for geolocation - but also as a cyber weapon >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
NSO also tried to get into the game and developed a yet-reported product called Truman to try to take the lead in developing an offensive AdInt market. But the twist? They never got to launch it >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🌐 Enter Insanet: Not just a catchy name, but a nod to the insanity of their tech. Founded in 2019, they're the only firm to every legally sell an offensive AdInt technology >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🎯Insanet managed to legally navigate these turbulent waters, selling a product that many deemed... well, insane!
https://twitter.com/DonnchaC/status/1702349380630577662
🖥️Their product - "Sherlock." This tool exploited ads to infiltrate devices - peak of surveillance capitalism. It has the power to breach Windows, iPhones, AND Androids. A universal hacking tool >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
💰The price tag for such a vector? An eye-watering 6 million euros for a single infection. If Pegasus is considered the nuclear bomb of digital arms, Sherlock is the warhead >>
haaretz.com/israel-news/20…

haaretz.com/israel-news/20…

🌐 Who's behind Insanet? A group of seasoned cyber entrepreneurs with strong Israeli intelligence ties and young innovators with a dual background in military cyber units and the ad industry >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🚫Insanet's journey wasn't smooth sailing. Although they could initially legally sell Sherlock, the Israeli Defense Ministry soon reigned in their permit. They did manage to sell Sherlock to one (nondemocratic) country >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🤝Amidst all this regulatory uncertainty, Insanet sought partnerships: They held discussions with other firms like Paragon, Nemesis, and Candiru, aiming to merge technologies to try to overcome regulatory barriers >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🖥️ A leaked 2019 Candiru sales document shows how Sherlock was billed alongside their PC spyware. As a vector, it can breach Windows, iPhones, AND Androids. At the time, no one knew Insanet existed & the tool was (mis)attributed to Candiru
citizenlab.ca/2021/07/hookin…

citizenlab.ca/2021/07/hookin…

🏁Rayzone was an industry leader in AdInt. They even coined the term! And their Echo software is considered the best in the non-offensive field >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🖥️Initially focusing on geo-surveillance, amid market pressure, Rayzone also pivoted to develop an offensive ad-based tool - and they, too, secured the coveted Defense Ministry's approval (despite reports claiming otherwise & despite massive delays) >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🔍So, where does this leave the world of digital arms? The debate rages on: AdInt - is it civilian or military tech?
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🖥️Even anonymous and GDPR compliant AdInt can still have HLS value: Cobwebs, which specializes in OSINT, offers tech that can locate a mobile device via ad data. The company illustrates this capability through a potential target in Iran!
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🚨 The #COVID19 pandemic boosted the anonymous/OSINT AdInt industry. With heightened demand for digital tracking, firms like Intelos, revealed here for the first time, pitched means for governments to monitor citizen behaviors via ad data 🦠📲
haaretz.com/israel-news/20…

haaretz.com/israel-news/20…

🎯 Up till now, companies using open sources for civilian clients weren't under state supervision, while cyber companies like Insanet faced tight oversight. The lines are blurring >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🌍 The global implications? Israeli firms developed tech that was meant to counter terrorism, but as they are sold to nations with questionable track records, they are frequently abused and turned on journalists and human rights defenders >>
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🌌 Israel, under U.S. pressure, reduced the list of countries cyberarms could be sold to. But a dark market is already looming! Beyond regulated sales, a shadow market may sell these new digital weapons to questionable states or even private entities!
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🔄 It's a cycle: Tech evolves, exploits are patched, regulations tighten, spyware companies adapt and hacking continues. But one thing is clear: the digital arms race has reached a new frontier
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
🛑 It's new era of digital warfare and the lines between ads, tech, and espionage blur. As technology continues to advance, the need for well-governed ethical use and strict regulations becomes paramount
haaretz.com/israel-news/20…
haaretz.com/israel-news/20…
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter