Block ads on your networks now.
The system designed to follow us around the net with ads is now a blinking national security & human rights threat.
By @omerbenj
haaretz.com/israel-news/20…

The system designed to follow us around the net with ads is now a blinking national security & human rights threat.
By @omerbenj
haaretz.com/israel-news/20…
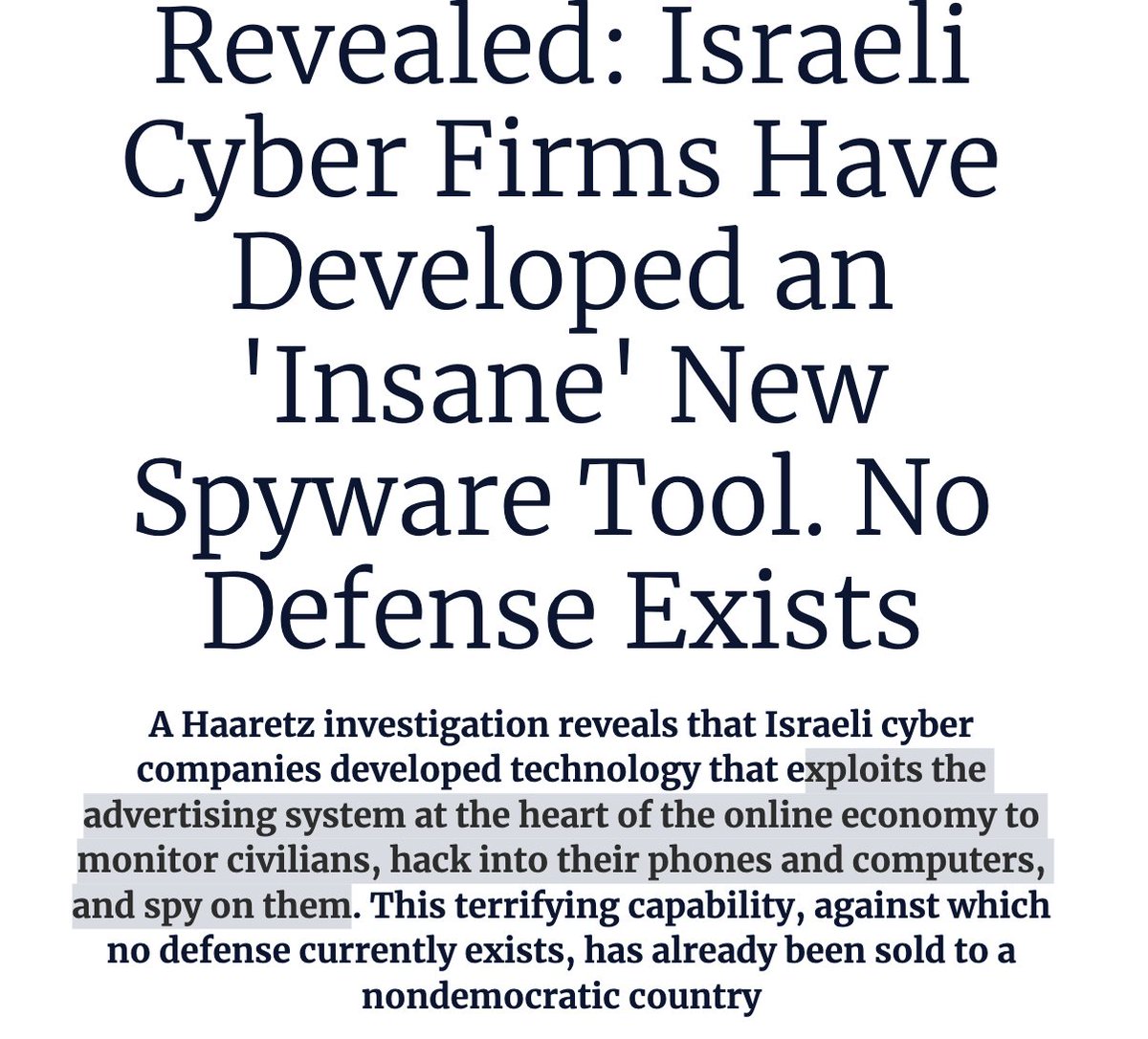
2/ Once the capability was limited to governments.
Now, in a predictable step, mercenary spyware companies are selling it.
Leveraging ads to remotely infect you with #Pegasus-like spyware.
Analogy: a devastating & unfixable backdoor chasing you device around the internet.
Now, in a predictable step, mercenary spyware companies are selling it.
Leveraging ads to remotely infect you with #Pegasus-like spyware.
Analogy: a devastating & unfixable backdoor chasing you device around the internet.

3/ The incentives are simple: ad companies will do everything they can to make sure you get tracked & shown ads.
So do their customers.
Even the newspapers that do good reporting on privacy.
All that effort has basically forced security vulnerabilities onto the entire world.
So do their customers.
Even the newspapers that do good reporting on privacy.
All that effort has basically forced security vulnerabilities onto the entire world.
4/ Any network, government to corporate, university to nonprofit should BLOCK ALL ADS & TRACKING at the gateway.
We cannot expect users to individually fight trench warfare to protect their security against the ad industry colossus has been weaponized against them.
We cannot expect users to individually fight trench warfare to protect their security against the ad industry colossus has been weaponized against them.
5/ Of course ads-that-hack-you have already made their way into the hands of dictatorships.
This is a terrifying zero-click frontier of compromise that we've largely sleepwalked into.
This is a terrifying zero-click frontier of compromise that we've largely sleepwalked into.

6/ "What can I do to stop this as an individual?"
Sure, you can use adblockers on your desktop browser, but that's a leaky band aid *at best.*
And Phones are a tricky place to do comprehensive ad-blocking.
The fact that so many apps incorporate ads makes it much, much worse.
Sure, you can use adblockers on your desktop browser, but that's a leaky band aid *at best.*
And Phones are a tricky place to do comprehensive ad-blocking.
The fact that so many apps incorporate ads makes it much, much worse.
7/ Here's one way you get hacked through ad networks
1️⃣I'm the bad guy, I find your phone using what ad networks know about you
2️⃣I send you an ad through their networks including malicious code
3️⃣ You scroll along & BOOM your phone = silently infected.
No action needed.
1️⃣I'm the bad guy, I find your phone using what ad networks know about you
2️⃣I send you an ad through their networks including malicious code
3️⃣ You scroll along & BOOM your phone = silently infected.
No action needed.
8/ Shoutout to @WydenPress @RonWyden who has been been tireless on malvertising.
Calling for the US to block the threat of malicious ads on sensitive networks.
*and*
Scrutinizing the ad-blocking industry for shady practices (e.g. taking cash to let certain ads through).


Calling for the US to block the threat of malicious ads on sensitive networks.
*and*
Scrutinizing the ad-blocking industry for shady practices (e.g. taking cash to let certain ads through).


• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter