Con Inc and the Red Pilled Antifa
Part 1: Disinformation and Chaos for Hire
Thread 🧵
Would the average person recognize a PSYOP or PSYACT if they were specifically targeted by it? This was a question that came up months ago. I am not talking about the normal media brainwashing that we see by and large that target huge areas of the population. I am talking about the kind that targets specific individuals.
I argue that most would not. Even the most trained intelligence agent would probably have a hard time recognizing an op that was being run against them. For one, there is the emotional state attached to these ops. It is difficult to distance oneself from those emotional gut reactions and recognize the source of the attacks. For another, there is the element of confusion to it. It is designed to be that way.
Other people might disagree with me on this assessment. In the end, it really doesn't matter if I am right or if they are. What matters is identifying the PSYOP itself and leveling the playing field.
So let me ask you. Do you feel like you are in the middle of a PSYOP?
Boone Cutler and General Flynn did a wonderful job in educating people on 5th Generation Warfare and what it entails in their book. If you haven't read it, I would highly suggest that you do. But this particular article isn't a book review. It isn't an expansion of what we know of psychological operations. It is an outline of patterns of behavior within the movement that suggest that certain individuals have been targeted as part of a PSYOP. It is a story so large that I cannot write about everything in just one article. So I am attempting to give the highlights in the hopes that others can step forward and help fill in the gaps of missing information.
I will leave a trail of breadcrumbs. It is your job to make a meal out of them.
Hopefully, all will become clear in the near future.
If you have never heard of Con Inc and never considered that there could be a group of people that are the equivalent to Red Pilled Antifa, welcome to my world. Up until a few weeks ago...
I realize now that we all had pieces of evidence to this. It was right in front of all of our faces. We missed it. We missed the clues, the news stories, and the patterns. I have never been one for interpreting comms, but now I read back and see them everywhere. We missed all the breadcrumbs that everyone was dropping right in front of our little noses. The picture was there. We just never pieced it together. And we all had pieces to this puzzle.
Let's begin...
How do you keep a stolen election once you've stolen it?
#ConInc #RedPilledAntifa

Part 1: Disinformation and Chaos for Hire
Thread 🧵
Would the average person recognize a PSYOP or PSYACT if they were specifically targeted by it? This was a question that came up months ago. I am not talking about the normal media brainwashing that we see by and large that target huge areas of the population. I am talking about the kind that targets specific individuals.
I argue that most would not. Even the most trained intelligence agent would probably have a hard time recognizing an op that was being run against them. For one, there is the emotional state attached to these ops. It is difficult to distance oneself from those emotional gut reactions and recognize the source of the attacks. For another, there is the element of confusion to it. It is designed to be that way.
Other people might disagree with me on this assessment. In the end, it really doesn't matter if I am right or if they are. What matters is identifying the PSYOP itself and leveling the playing field.
So let me ask you. Do you feel like you are in the middle of a PSYOP?
Boone Cutler and General Flynn did a wonderful job in educating people on 5th Generation Warfare and what it entails in their book. If you haven't read it, I would highly suggest that you do. But this particular article isn't a book review. It isn't an expansion of what we know of psychological operations. It is an outline of patterns of behavior within the movement that suggest that certain individuals have been targeted as part of a PSYOP. It is a story so large that I cannot write about everything in just one article. So I am attempting to give the highlights in the hopes that others can step forward and help fill in the gaps of missing information.
I will leave a trail of breadcrumbs. It is your job to make a meal out of them.
Hopefully, all will become clear in the near future.
If you have never heard of Con Inc and never considered that there could be a group of people that are the equivalent to Red Pilled Antifa, welcome to my world. Up until a few weeks ago...
I realize now that we all had pieces of evidence to this. It was right in front of all of our faces. We missed it. We missed the clues, the news stories, and the patterns. I have never been one for interpreting comms, but now I read back and see them everywhere. We missed all the breadcrumbs that everyone was dropping right in front of our little noses. The picture was there. We just never pieced it together. And we all had pieces to this puzzle.
Let's begin...
How do you keep a stolen election once you've stolen it?
#ConInc #RedPilledAntifa

Has Anyone Done a Dig on Blackbox?
On November 22, 2022, Jeffrey Pedersen (aka IntheMatrixxx) made a post on Truth Social asking a single question.
"Has anyone done a dig on Black Box?"
Having never heard about this company, many on Truth Social were intrigued by this question. There was a lot of speculation.
Note: This post was the beginning of the takedown portion of the PSYOP to destroy We The Media.

On November 22, 2022, Jeffrey Pedersen (aka IntheMatrixxx) made a post on Truth Social asking a single question.
"Has anyone done a dig on Black Box?"
Having never heard about this company, many on Truth Social were intrigued by this question. There was a lot of speculation.
Note: This post was the beginning of the takedown portion of the PSYOP to destroy We The Media.
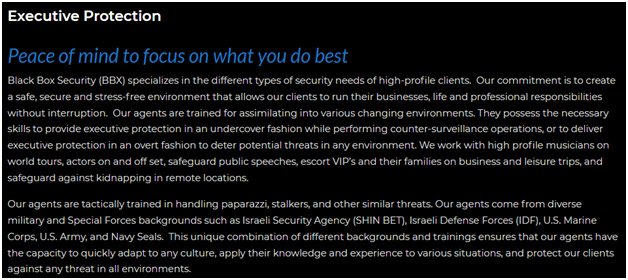
For those that don't know, Black Box Security is a company that offers executive protection services for high-profile clients. Per their website, they "work with high profile musicians on world tours, actors on and off set, safeguard public speeches, escort VIP’s and their families on business and leisure trips, and safeguard against kidnapping in remote locations." Their employees are selected from "diverse military and Special Forces backgrounds such as Israeli Security Agency (SHIN BET), Israeli Defense Forces (IDF), U.S. Marine Corps, U.S. Army, and Navy Seals."
On the surface, it looks like some bad arse military guys who go around and offer a secure environment for their clientele. The reality is that Black Box and other companies like them are employed by the handlers and contract holders of those musicians, actors, and other VIP's. What has been reported to go on behind closed doors offers a disturbing glimpse of control, abuse, and a mixture of Stasi tactics, psychological manipulation, and blackmail.

On the surface, it looks like some bad arse military guys who go around and offer a secure environment for their clientele. The reality is that Black Box and other companies like them are employed by the handlers and contract holders of those musicians, actors, and other VIP's. What has been reported to go on behind closed doors offers a disturbing glimpse of control, abuse, and a mixture of Stasi tactics, psychological manipulation, and blackmail.
The most famous story regarding this particular company involves Britney Spears. Brittney was in a conservatorship under her father, Jamie Spears, who employed the services of Black Box Security to "protect" her. The following is just a few excerpts regarding what happened to her.
Quote:
"...the pop star's bedroom was bugged with an audio recording device that monitored her personal conversations at home."
Robin Greenhill of Tri Star Sports & Entertainment, who worked closely with Britney's father Jamie Spears, wanted to mirror the singer's phone with an iPad hooked up to her iCloud account to track her text messages with friends.
Alex Vlasov, a former employee of Black Box Security, "described the restrictions placed on the pop star 'like a minor who needs their parents' consent.'"
"Once Vlasov began questioning Black Box's practices, he alleges that Yemini [the CEO of Black Box Security] took out his gun and placed it on his desk in front of Vlasov. 'So you don't like how I run my business?' Vlasov claimed Yemini asked him."
"Vlasov claimed his bosses informed him that this responsibility was coming directly from the company's 'client.' The client, he says, was Jamie."
Quote:
"...the pop star's bedroom was bugged with an audio recording device that monitored her personal conversations at home."
Robin Greenhill of Tri Star Sports & Entertainment, who worked closely with Britney's father Jamie Spears, wanted to mirror the singer's phone with an iPad hooked up to her iCloud account to track her text messages with friends.
Alex Vlasov, a former employee of Black Box Security, "described the restrictions placed on the pop star 'like a minor who needs their parents' consent.'"
"Once Vlasov began questioning Black Box's practices, he alleges that Yemini [the CEO of Black Box Security] took out his gun and placed it on his desk in front of Vlasov. 'So you don't like how I run my business?' Vlasov claimed Yemini asked him."
"Vlasov claimed his bosses informed him that this responsibility was coming directly from the company's 'client.' The client, he says, was Jamie."
In short, we see a pattern of intimidation, manipulation, control, blackmail, and abuse in order to control the actions of another.
Keep in mind the types of individuals that are employed by these companies.
And this is hardly the only company out there that engages in this practice. We see a pattern of behavior and tactics used throughout the entertainment industry on certain individuals. This isn't the only example we have seen of this either.

Keep in mind the types of individuals that are employed by these companies.
And this is hardly the only company out there that engages in this practice. We see a pattern of behavior and tactics used throughout the entertainment industry on certain individuals. This isn't the only example we have seen of this either.

Kanye West
On November 3, 2022, the first news stories started appearing regarding Kanye West and a some text messages he received from his personal trainer Harley Pasternak. These read like an ultimatum and threat from someone who supposedly was an employee to their employer.
"Second option, I have you institutionalized again where they medicate the crap out of you, and you go back to Zombieland forever. Play date with the kids just won't be the same."
Some excerpts from the articles regarding that incident:
"This is not the first time Pasternak has targeted West with mental health claims."
"What should be obvious by now is that I was raised to stand for my truth regardless of the consequences,” Kanye wrote. “So I will say this again I was mentally misdiagnosed and nearly drugged out of my mind to make me a manageable well behaved celebrity.”

On November 3, 2022, the first news stories started appearing regarding Kanye West and a some text messages he received from his personal trainer Harley Pasternak. These read like an ultimatum and threat from someone who supposedly was an employee to their employer.
"Second option, I have you institutionalized again where they medicate the crap out of you, and you go back to Zombieland forever. Play date with the kids just won't be the same."
Some excerpts from the articles regarding that incident:
"This is not the first time Pasternak has targeted West with mental health claims."
"What should be obvious by now is that I was raised to stand for my truth regardless of the consequences,” Kanye wrote. “So I will say this again I was mentally misdiagnosed and nearly drugged out of my mind to make me a manageable well behaved celebrity.”
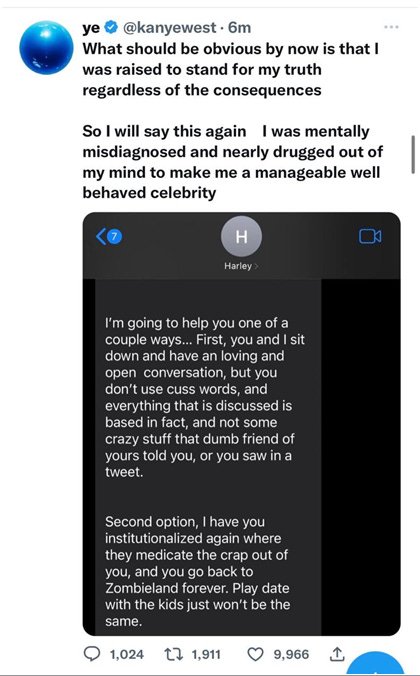
Here are Kanye's own words regarding the tactics used against him.
Source:
Source:
I think Tucker Carlson summed this situation up perfectly in this video.
If these tactics can be used against individuals in the entertainment industry, could they be employed against groups of individuals? Could they be used to influence a situation towards a specific goal?
"Have you ever wondered why all of these supposedly creative people reach exactly the same conclusion every time? They are all on the same page. How could that happen? It's an interesting question." ~ Tucker Carlson
Source:
If these tactics can be used against individuals in the entertainment industry, could they be employed against groups of individuals? Could they be used to influence a situation towards a specific goal?
"Have you ever wondered why all of these supposedly creative people reach exactly the same conclusion every time? They are all on the same page. How could that happen? It's an interesting question." ~ Tucker Carlson
Source:
The Case of Harvey Weisnstein
"In the fall of 2016, Harvey Weinstein set out to suppress allegations that he had sexually harassed or assaulted numerous women. He began to hire private security agencies to collect information on the women and the journalists trying to expose the allegations. According to dozens of pages of documents, and seven people directly involved in the effort, the firms that Weinstein hired included Kroll, which is one of the world’s largest corporate-intelligence companies, and Black Cube, an enterprise run largely by former officers of Mossad and other Israeli intelligence agencies."
Just what lengths will companies like Black Cube go to?
Intelligence analysts, undercover agents, avatar operators, linguists, and operations experts.

"In the fall of 2016, Harvey Weinstein set out to suppress allegations that he had sexually harassed or assaulted numerous women. He began to hire private security agencies to collect information on the women and the journalists trying to expose the allegations. According to dozens of pages of documents, and seven people directly involved in the effort, the firms that Weinstein hired included Kroll, which is one of the world’s largest corporate-intelligence companies, and Black Cube, an enterprise run largely by former officers of Mossad and other Israeli intelligence agencies."
Just what lengths will companies like Black Cube go to?
Intelligence analysts, undercover agents, avatar operators, linguists, and operations experts.
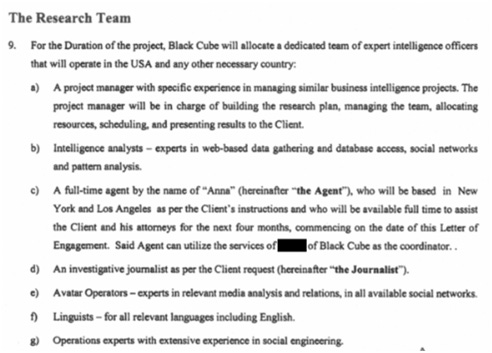
What is an avatar operator?
According to this Wired article about Private Espionage, avatar operators are "experts in social media who specialized in creating fake Facebook pages, LinkedIn profiles, and the like for field operatives."
wired.com/story/the-murk…

According to this Wired article about Private Espionage, avatar operators are "experts in social media who specialized in creating fake Facebook pages, LinkedIn profiles, and the like for field operatives."
wired.com/story/the-murk…
"Two sources with knowledge of Weinstein’s work with Black Cube said that the firm creates fictional companies to provide cover for its operatives."
Fake companies complete with fake websites, fake phone numbers, and fake addresses. Fake online profiles to fit their fake narrative for their fake personas.
What was the price for such services? $200,000 with $300,000 as a bonus if certain goals were met. They weren't.
Fake companies complete with fake websites, fake phone numbers, and fake addresses. Fake online profiles to fit their fake narrative for their fake personas.
What was the price for such services? $200,000 with $300,000 as a bonus if certain goals were met. They weren't.
The Companies Behind This
You can't just open up a web browser and search for "disinformation for hire", "Mossad for hire", or "dark PR firms" and find a list of companies "near me". Many of these companies pass themselves off as social engineering firms or PR based firms. Some websites say they specialize in OSINT, intelligence agencies, or social media influence. Most of them are based in Israel, which could arguably be called the intelligence capital of the world. Many are hiding behind fake LLCs.
One thing is for certain, when you start uncovering the names of these companies, you start realizing just how lucrative of a business this industry is. There is another thing you will notice. When one company gets reported on, it is often dissolved and reformed as another company.
Here is just a sample of the company names that I found that were engaged in this type of business.
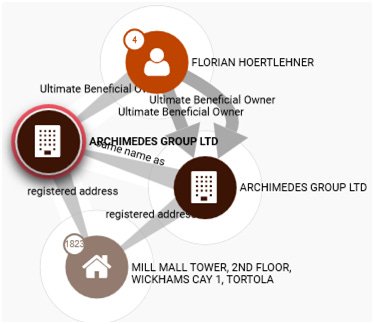
Archimedes Group
Black Cube
Bravo-Idea
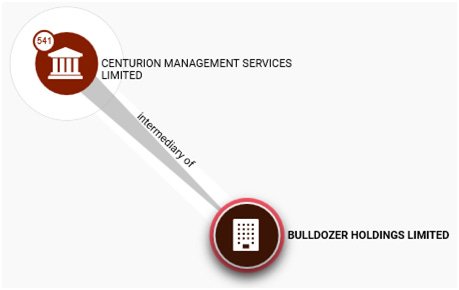
Bulldozer Holdings Ltd
Cambridge Analytica
Cat@Net
Grey Content Ltd
HBGary Federal
KOI
KS Process and Software Ltd.
NSO Group
Pragmatico
Psy-Corp
S2T Unlocking Cyberspace
Team Jorge
Voyager Labs
You can't just open up a web browser and search for "disinformation for hire", "Mossad for hire", or "dark PR firms" and find a list of companies "near me". Many of these companies pass themselves off as social engineering firms or PR based firms. Some websites say they specialize in OSINT, intelligence agencies, or social media influence. Most of them are based in Israel, which could arguably be called the intelligence capital of the world. Many are hiding behind fake LLCs.
One thing is for certain, when you start uncovering the names of these companies, you start realizing just how lucrative of a business this industry is. There is another thing you will notice. When one company gets reported on, it is often dissolved and reformed as another company.
Here is just a sample of the company names that I found that were engaged in this type of business.
Archimedes Group
Black Cube
Bravo-Idea
Bulldozer Holdings Ltd
Cambridge Analytica
Cat@Net
Grey Content Ltd
HBGary Federal
KOI
KS Process and Software Ltd.
NSO Group
Pragmatico
Psy-Corp
S2T Unlocking Cyberspace
Team Jorge
Voyager Labs
Something else came up which might be noteworthy. I noticed that some of these company names were leaked in the Panama Papers.
offshoreleaks.icij.org/nodes/10051163
offshoreleaks.icij.org/nodes/240371311


offshoreleaks.icij.org/nodes/10051163
offshoreleaks.icij.org/nodes/240371311
The Panama Papers
If you have never heard of the Panama Papers, here is your crash course. In 2016, 11.5 million leaked documents were published. In these papers were the names of over 214,000 foreign companies, some of which date back to the 1970's.
The Panama Papers was the biggest data leak ever. Bigger than Wikileaks even. And the repercussions from this leak are still being felt. There are still being articles and arrests happening because of this.
These documents originated from a law firm called Mossack Fonseca, which just happened to be the 4th largest law firm in the world. What they detailed was a trail of political corruption which was being exhibited around the world and the dark money accompanying it through the use of offshore accounts. In other words, they detail a lot of financial fraud along with tax evasion and the avoidance of a lot of sanctions and the law.
If you want to read more about these leaks, then I would start here.
Note: You can download or search the leaked information and databases for the Pandora Papers, Paradise Papers, Panama Papers, and Offshore Leaks from here.
If you have never heard of the Panama Papers, here is your crash course. In 2016, 11.5 million leaked documents were published. In these papers were the names of over 214,000 foreign companies, some of which date back to the 1970's.
The Panama Papers was the biggest data leak ever. Bigger than Wikileaks even. And the repercussions from this leak are still being felt. There are still being articles and arrests happening because of this.
These documents originated from a law firm called Mossack Fonseca, which just happened to be the 4th largest law firm in the world. What they detailed was a trail of political corruption which was being exhibited around the world and the dark money accompanying it through the use of offshore accounts. In other words, they detail a lot of financial fraud along with tax evasion and the avoidance of a lot of sanctions and the law.
If you want to read more about these leaks, then I would start here.
Note: You can download or search the leaked information and databases for the Pandora Papers, Paradise Papers, Panama Papers, and Offshore Leaks from here.
Dark Services
You might be looking at this at this point and wondering what this has to do with the MAGA movement. So far we have discussed attacks on individuals and using manipulation and coercion to influence that targeted individual. But what happens when you target a grassroots movement?
Let's look at what we actually know is being offered as services to clients first and then question whether the MAGA movement and individuals within the MAGA movement has indeed been targeted.

You might be looking at this at this point and wondering what this has to do with the MAGA movement. So far we have discussed attacks on individuals and using manipulation and coercion to influence that targeted individual. But what happens when you target a grassroots movement?
Let's look at what we actually know is being offered as services to clients first and then question whether the MAGA movement and individuals within the MAGA movement has indeed been targeted.
Let's say you want your school to win a national competition. Well, you can hire a black PR firm to generate votes online. That happened in Taiwan.
"In 2011, singers from schools across Taiwan competed in a popular TV competition. Peng’s alma mater won; its performer received more than 41 million online votes, almost twice the Taiwanese population. A school official confirmed to the Reporter that the school had requested help from Peng in the competition but declined to comment further."
How about make Volodymyr Zelensky seem popular?
"Ukraine’s young new president Volodymyr Zelensky — hailed in the West as an ambitious reformer — is an enthusiastic social media user, deploying his popular Instagram and Facebook accounts to reach large audiences during his recent election campaign.
"But according to a recent investigation by VoxUkraine, Zelensky’s Facebook page had the most active fake users of any Ukrainian politician — 27,926 inauthentic accounts. They posted almost a quarter of all comments during the period analyzed. Similar ratios were seen for other top politicians."
Forge letters from the NAACP to politicians?
"The American Clean Energy and Security Act of 2009 was meant to curb greenhouse gas emissions, which apparently didn't sit too well with opponents of climate change. Rep. Tom Perriello (D-VA) received letters from both the NAACP and the Hispanic non-profit Creciendo Juntos, asking him to vote against the bill for economic reasons.
"It turned out that the lobbyist firm Bonner & Associates, which has a history of astroturfing and defrauding the government, had fabricated the letters, from the letterhead to the signatures. The very similar looking letters can still be found online."
Fake excitement over McDonald's Quarter Pounder?
"The release of the Quarter Pounder in Japan was a pretty big deal, judging by the size of the crowds. In fact, it was a record-setting day for the McDonald's in Osaka.
"As it turns out, McDonalds had recruited 1,000 part-time employees to line up - starting at midnight before the store even opened - and generate buzz for the burger. The 'customers' were paid for their time and had their meal compensated. McDonalds admitted to the ploy, but said it was part of a 'customer feedback' for 'market research.'
"The employees were paid roughly $11 bucks an hour for their work."
"In 2011, singers from schools across Taiwan competed in a popular TV competition. Peng’s alma mater won; its performer received more than 41 million online votes, almost twice the Taiwanese population. A school official confirmed to the Reporter that the school had requested help from Peng in the competition but declined to comment further."
How about make Volodymyr Zelensky seem popular?
"Ukraine’s young new president Volodymyr Zelensky — hailed in the West as an ambitious reformer — is an enthusiastic social media user, deploying his popular Instagram and Facebook accounts to reach large audiences during his recent election campaign.
"But according to a recent investigation by VoxUkraine, Zelensky’s Facebook page had the most active fake users of any Ukrainian politician — 27,926 inauthentic accounts. They posted almost a quarter of all comments during the period analyzed. Similar ratios were seen for other top politicians."
Forge letters from the NAACP to politicians?
"The American Clean Energy and Security Act of 2009 was meant to curb greenhouse gas emissions, which apparently didn't sit too well with opponents of climate change. Rep. Tom Perriello (D-VA) received letters from both the NAACP and the Hispanic non-profit Creciendo Juntos, asking him to vote against the bill for economic reasons.
"It turned out that the lobbyist firm Bonner & Associates, which has a history of astroturfing and defrauding the government, had fabricated the letters, from the letterhead to the signatures. The very similar looking letters can still be found online."
Fake excitement over McDonald's Quarter Pounder?
"The release of the Quarter Pounder in Japan was a pretty big deal, judging by the size of the crowds. In fact, it was a record-setting day for the McDonald's in Osaka.
"As it turns out, McDonalds had recruited 1,000 part-time employees to line up - starting at midnight before the store even opened - and generate buzz for the burger. The 'customers' were paid for their time and had their meal compensated. McDonalds admitted to the ploy, but said it was part of a 'customer feedback' for 'market research.'
"The employees were paid roughly $11 bucks an hour for their work."
Fake excitement for book sales. Tank the sales of another book. Fake protests. Fake interest. Stage photo ops for the news. Fake news sites and news stories in order to discredit an opponent. Fake political donations in order to discredit someone. Fake online personalities and their followers. Start hashtag campaigns. Bury an unfavorable news story. Promote another. Fake friendships in order to get insider information or to sabotage an effort. Build profiles of online personalities. Send threats to the opposition. Harass others. Artificially inflate the value of cryptocurrency. Create deep fake photos in order to discredit someone. Send sex toys to someone's house in order to create a fake sex scandal and affair. (Yes. This actually happened.) Create enough chaos to start a civil war or civil unrest. Steal an election.
The list really does go on and on. There isn't a job too big or too small for these companies... as long as the price is right. And it isn't limited to online activity or just social media. It oftentimes bleeds into reality.
By the way, in case you are wondering, the cost to delay an election in a small country is $6.4 million.
"In one of the meetings, Meidan [from Team Jorge] suggested destabilizing Chad as a means to delay the elections. In another meeting, the advisers explained that there may be an explosion in a market in the capital, N'Djamena, to justify the postponement. That did not deter Jorge, who asked for 6 million euros ($6.4 million) to see the campaign through."

The list really does go on and on. There isn't a job too big or too small for these companies... as long as the price is right. And it isn't limited to online activity or just social media. It oftentimes bleeds into reality.
By the way, in case you are wondering, the cost to delay an election in a small country is $6.4 million.
"In one of the meetings, Meidan [from Team Jorge] suggested destabilizing Chad as a means to delay the elections. In another meeting, the advisers explained that there may be an explosion in a market in the capital, N'Djamena, to justify the postponement. That did not deter Jorge, who asked for 6 million euros ($6.4 million) to see the campaign through."

The Methods and Tools Used
"The broader notion of deception and influence operations has been around for some time, but over the past several years, we have seen [...] companies grow up that basically build their business model around deception."
Source:
buzzfeednews.com/article/craigs…
"The broader notion of deception and influence operations has been around for some time, but over the past several years, we have seen [...] companies grow up that basically build their business model around deception."
Source:
buzzfeednews.com/article/craigs…
Quote:
"Thank you my love. It was a wonderful night. Waiting for you whenever you come back,” read the note attached to the sex toy hidden inside the Amazon delivery box. It was allegedly sent by Shannon Aiken, a 38-year-old Washington woman, to the home of a politician at the height of an election campaign. His wife received the package. The politician slept in his office for two days. A crew was secretly sent to film him there, and the embarrassing footage leaked online.
Aiken appears real. She is active on Facebook and Twitter, has a real Gmail account and an active WhatsApp, both linked to a real phone number. Her Amazon is connected to a credit card, while real funds from her digital wallet paid for the package purportedly containing a dildo, condoms and lubricants.
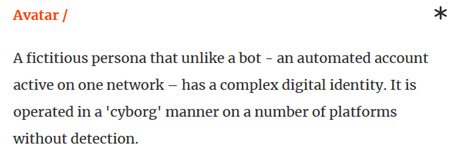
However, despite her impressive digital footprint, Aiken is not real. She is an avatar: a complex, fake digital persona built to mimic human behavior and avoid detection – not a bot, but a “cyborg.”
"Thank you my love. It was a wonderful night. Waiting for you whenever you come back,” read the note attached to the sex toy hidden inside the Amazon delivery box. It was allegedly sent by Shannon Aiken, a 38-year-old Washington woman, to the home of a politician at the height of an election campaign. His wife received the package. The politician slept in his office for two days. A crew was secretly sent to film him there, and the embarrassing footage leaked online.
Aiken appears real. She is active on Facebook and Twitter, has a real Gmail account and an active WhatsApp, both linked to a real phone number. Her Amazon is connected to a credit card, while real funds from her digital wallet paid for the package purportedly containing a dildo, condoms and lubricants.
However, despite her impressive digital footprint, Aiken is not real. She is an avatar: a complex, fake digital persona built to mimic human behavior and avoid detection – not a bot, but a “cyborg.”
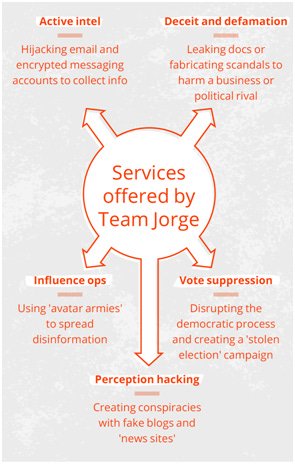
Team Jorge's services include:
- Hacking messaging apps and email accounts
- Planting materials in compromised accounts
- Hack-and-leak of real or forged material
- Army of online avatars (fake accounts) for social media manipulation
- Voter suppression and election disruption
- Undermining election results with 'stop the steal' style campaigns
"Every influence operation... has three stages: gathering intelligence, constructing a narrative, and deploying for maximum impact."
- Hacking messaging apps and email accounts
- Planting materials in compromised accounts
- Hack-and-leak of real or forged material
- Army of online avatars (fake accounts) for social media manipulation
- Voter suppression and election disruption
- Undermining election results with 'stop the steal' style campaigns
"Every influence operation... has three stages: gathering intelligence, constructing a narrative, and deploying for maximum impact."
Some of these companies use software, sophisticated AI, and cyborgs (which is a cross between AI and human interaction). Others use cheap human labor.
One thing is for certain, they build profiles on their targets, identify who to attack, come up with a game plan to attack, and deploy it. Sometimes this looks like simple harassment and smear campaigns. Other times these forms of attacks are much more sophisticated.
"The aim is to get an emotional reaction from a person," Bidun said in an interview. "If they read a comment, even [if they understand] that it was written by a bot, it could have affected them emotionally and it becomes more difficult for them to control themselves."

One thing is for certain, they build profiles on their targets, identify who to attack, come up with a game plan to attack, and deploy it. Sometimes this looks like simple harassment and smear campaigns. Other times these forms of attacks are much more sophisticated.
"The aim is to get an emotional reaction from a person," Bidun said in an interview. "If they read a comment, even [if they understand] that it was written by a bot, it could have affected them emotionally and it becomes more difficult for them to control themselves."
These actions don't always stay online. Sometimes agents were hired to go undercover. Other times crowds were hired to stage a protest or create the illusion of one. Actors were often employed. Anything that could be faked to create the illusion of the new reality would be.
"We also identified real-world events that appeared to have been staged to provide ammunition that could be leveraged in social media campaigns. One case involved a fake protest staged outside a company headquarters on Regent Street, central London.
"Three masked activists in baseball caps, sunglasses and masks filmed themselves waving placards. A similar leafleting campaign was staged near the Eiffel Tower in Paris, before being circulated on social media by Aims bots. It is not possible to know who the clients were in any of the campaigns, or even what their objective was.
"However, what seems clear is that the avatars peddling propaganda are doing so with the help of stolen photographs of real people."
It wasn't always to create a false narrative either. Sometimes these tactics were deployed to destroy real reactions.
How do you destroy an authentic movement? What if our efforts were being actively sabotaged?
"We also identified real-world events that appeared to have been staged to provide ammunition that could be leveraged in social media campaigns. One case involved a fake protest staged outside a company headquarters on Regent Street, central London.
"Three masked activists in baseball caps, sunglasses and masks filmed themselves waving placards. A similar leafleting campaign was staged near the Eiffel Tower in Paris, before being circulated on social media by Aims bots. It is not possible to know who the clients were in any of the campaigns, or even what their objective was.
"However, what seems clear is that the avatars peddling propaganda are doing so with the help of stolen photographs of real people."
It wasn't always to create a false narrative either. Sometimes these tactics were deployed to destroy real reactions.
How do you destroy an authentic movement? What if our efforts were being actively sabotaged?
New Tools For An Old Playbook
Could there have been a concerted effort to keep election integrity from happening, to keep conservatives for organizing effectively, and to stop efforts to fix our country from succeeding? What if there was a playbook that already spelled out how to do this? What if these tactics weren't anything new? What if they were in fact actually from another era and used against another political group?
Quote:
After the East German popular uprising of June 1953 (suppressed by Soviet troops) the government gave the Stasi the task of systematic surveillance and prevention of unrest in the population. Initially this took the form of brutal physical repression: imprisonment and physical abuse (including torture) by police and secret police. But this changed during the 1970s when the GDR became more interested in gaining a positive international image, and the repression of activists became more subtle. The Stasi redefined the military term Zersetzung (attrition or corrosion) to name their harassment tactics: the aim was to disrupt the working of groups and the lives of individuals to such a degree that their activism became ineffective, or more preferably, ceased altogether.
The aim of the Zersetzung was to ‘switch off’ the group by rendering it ineffective, with an interim goal of hindering any positive media or public exposure. The usual ways to switch groups off were to:
- Create conflict between members – particularly useful subjects for sowing discord were those of a philosophical or political nature, money and personal (sexual) relations;
- Hinder and sabotage activities by the use of one or more infiltrators, who would agree to do tasks, but not get round to doing them, lose materials and equipment, repeatedly request changes and further edits of materials to slow down production, attempt to divert the group into more harmless activities etc;
- Isolate the groups from other activists, example by spreading rumors regarding unacceptable behavior and political views etc.
The choice of tactics in any particular case was based on extensive psychological profiling and intelligence on the group members, particularly: who plays what role, who fulfills what kind of task; what are relationships within the group like, who hangs out with whom.
Could there have been a concerted effort to keep election integrity from happening, to keep conservatives for organizing effectively, and to stop efforts to fix our country from succeeding? What if there was a playbook that already spelled out how to do this? What if these tactics weren't anything new? What if they were in fact actually from another era and used against another political group?
Quote:
After the East German popular uprising of June 1953 (suppressed by Soviet troops) the government gave the Stasi the task of systematic surveillance and prevention of unrest in the population. Initially this took the form of brutal physical repression: imprisonment and physical abuse (including torture) by police and secret police. But this changed during the 1970s when the GDR became more interested in gaining a positive international image, and the repression of activists became more subtle. The Stasi redefined the military term Zersetzung (attrition or corrosion) to name their harassment tactics: the aim was to disrupt the working of groups and the lives of individuals to such a degree that their activism became ineffective, or more preferably, ceased altogether.
The aim of the Zersetzung was to ‘switch off’ the group by rendering it ineffective, with an interim goal of hindering any positive media or public exposure. The usual ways to switch groups off were to:
- Create conflict between members – particularly useful subjects for sowing discord were those of a philosophical or political nature, money and personal (sexual) relations;
- Hinder and sabotage activities by the use of one or more infiltrators, who would agree to do tasks, but not get round to doing them, lose materials and equipment, repeatedly request changes and further edits of materials to slow down production, attempt to divert the group into more harmless activities etc;
- Isolate the groups from other activists, example by spreading rumors regarding unacceptable behavior and political views etc.
The choice of tactics in any particular case was based on extensive psychological profiling and intelligence on the group members, particularly: who plays what role, who fulfills what kind of task; what are relationships within the group like, who hangs out with whom.
Does any of this feel familiar to anyone? Have you noticed these patterns within the MAGA movement?
"The Stasi used operational psychology and its extensive network of between 170,000 and over 500,000 informal collaborators to launch personalized psychological attacks against targets to damage their mental health and lower chances of a "hostile action" against the state. Among the collaborators were youths as young as 14 years of age."
"The Stasi used operational psychology and its extensive network of between 170,000 and over 500,000 informal collaborators to launch personalized psychological attacks against targets to damage their mental health and lower chances of a "hostile action" against the state. Among the collaborators were youths as young as 14 years of age."
A Mixture of Tools
And then we have the useful idiot...
"In political jargon, a useful idiot is a term currently used to reference a person perceived as propagandizing for a cause — particularly a bad cause originating from a devious, ruthless source — without fully comprehending the cause's goals, and who is cynically being used by the cause's leaders. The term was often used during the Cold War to describe non-communists regarded as susceptible to communist propaganda and manipulation."
If the election was stolen, would it make sense for plans to be made to keep that from being discovered and effectively reversed? Do you honestly think their plans stopped at just stealing an election? It wouldn't be enough just to steal it. They had to keep it after it was stolen.
How far do you think the powers that be would take this? How far do you think this rabbit hole could go?
Part 2 of Con Inc and the Red Pilled Antifa thread coming soon!
And then we have the useful idiot...
"In political jargon, a useful idiot is a term currently used to reference a person perceived as propagandizing for a cause — particularly a bad cause originating from a devious, ruthless source — without fully comprehending the cause's goals, and who is cynically being used by the cause's leaders. The term was often used during the Cold War to describe non-communists regarded as susceptible to communist propaganda and manipulation."
If the election was stolen, would it make sense for plans to be made to keep that from being discovered and effectively reversed? Do you honestly think their plans stopped at just stealing an election? It wouldn't be enough just to steal it. They had to keep it after it was stolen.
How far do you think the powers that be would take this? How far do you think this rabbit hole could go?
Part 2 of Con Inc and the Red Pilled Antifa thread coming soon!
This was research I did back in February and March of this year. I originally published it to substack (No subscription required. Not behind a paywall).
If you want to read this or read ahead in this 6 part (so far) series, you can find them here.
Given recent events, I thought it was a good time to revisit this topic.
Sources and Further Reading:
Note: Forbidden Stories is a consortium of reporters and journalists. It was formed due to some journalists being imprisoned and/or killed bringing you the types of stories I have outlined above. They are the experts on reporting regarding disinformation campaigns and private intelligence organizations/Mossad for hire.
End of thread 🧵elizabeththepunisherdove.substack.com/p/con-inc-and-…
If you want to read this or read ahead in this 6 part (so far) series, you can find them here.
Given recent events, I thought it was a good time to revisit this topic.
Sources and Further Reading:
Note: Forbidden Stories is a consortium of reporters and journalists. It was formed due to some journalists being imprisoned and/or killed bringing you the types of stories I have outlined above. They are the experts on reporting regarding disinformation campaigns and private intelligence organizations/Mossad for hire.
End of thread 🧵elizabeththepunisherdove.substack.com/p/con-inc-and-…
• • •
Missing some Tweet in this thread? You can try to
force a refresh












