Last week, an expert told Congress we had spread "conspiracy theories" about censorship, but we hadn't. And now, yet another whistleblower has come forward with new files showing direct US Defense Department involvement in a mass censorship scheme. They're explosive. 

Pentagon Was Involved In Domestic Censorship Scheme, New CTIL Whistleblower Files Show
Slack messages show direct involvement of FBI, DOD, and DHS employees in a mass online censorship scheme deliberately misrepresented as “cybersecurity”
by @galexybrane
U.S. Defense Secretary Lloyd Austin testifes before the Senate on October 31, 2023 (Photo by Liu Jie/Xinhua via Getty Images)
Last week, Public and Racket published the first CTIL Files, which revealed the origins of the Censorship Industrial Complex in offensive tactics developed by US and UK military contractors.
Now, a second whistleblower has come forward with Slack messages showing far greater government and military involvement in the Cyber Threat Intelligence League (CTIL) than we had previously discovered.
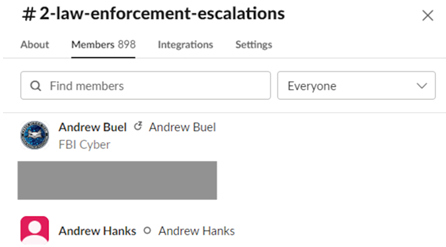
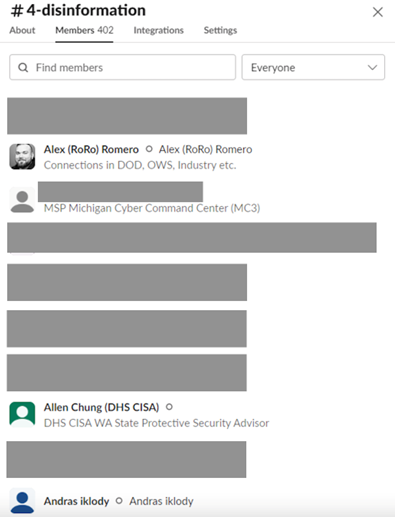
The CTIL Slack “disinformation” channel and the “law enforcement escalation” channel included current and former FBI employees, as well as personnel from the Michigan Cyber Command Center, the US Defense Digital Service (DDS), and at least one European government.
DDS is headquartered in the Pentagon and was founded by Secretary of Defense Ash Carter in November 2015. DDS’s website states, “The Department of Defense has a secret weapon.”
The Department of Defense told Public that it combined DDS with other agencies. “DDS merged with three other organizations to form the Chief Digital and Artificial Intelligence Office (CDAO) back in Feb 2022. CDAO is not currently involved with CTI and we do not have situational awareness on project participation which predated that merger,” a spokesperson said.
As for the CTI League, it claimed to serve an essential function, cybersecurity, protecting hospitals and healthcare systems from serious threats.
However, according to the new whistleblower, “The essential function of CTI League was largely duplicative of other free and paid threat services available to health care defenders.”
Justin Frappier, who worked for the Cybersecurity and Infrastructure Security Agency (CISA) of the Department of Homeland Security (DHS), wrote on his profile, “The opinions expressed here are my own as an analyst, and not those of CISA, or the US Government unless otherwise stated.”
But Frappier put the CISA seal as his profile image and was an eager participant in the CTI League. When he first joined CTIL, he asked if the group was “consolidating a list of disinformation resources to validate.” A CTIL member replied, “Yes, we are working on that. There is a whole Disinfo gathering [and] analysis operation happening in another group connected to CTI-League, which we’re working to incorporate as a threat stream.”
Responded Frappier, “That’s awesome, I think it’s amazing to see this happening at scale, long overdue but massive effort.”
Note: we redacted the files to protect identities of individuals who did not appear to play a leadership role.
These messages suggest that a government employee explicitly sought out a way to use the group for anti-disinformation activities and initiated access to these activities. Frappier contributed 573 messages to the “disinformation” channel of the Slack group.




Slack messages show direct involvement of FBI, DOD, and DHS employees in a mass online censorship scheme deliberately misrepresented as “cybersecurity”
by @galexybrane
U.S. Defense Secretary Lloyd Austin testifes before the Senate on October 31, 2023 (Photo by Liu Jie/Xinhua via Getty Images)
Last week, Public and Racket published the first CTIL Files, which revealed the origins of the Censorship Industrial Complex in offensive tactics developed by US and UK military contractors.
Now, a second whistleblower has come forward with Slack messages showing far greater government and military involvement in the Cyber Threat Intelligence League (CTIL) than we had previously discovered.
The CTIL Slack “disinformation” channel and the “law enforcement escalation” channel included current and former FBI employees, as well as personnel from the Michigan Cyber Command Center, the US Defense Digital Service (DDS), and at least one European government.
DDS is headquartered in the Pentagon and was founded by Secretary of Defense Ash Carter in November 2015. DDS’s website states, “The Department of Defense has a secret weapon.”
The Department of Defense told Public that it combined DDS with other agencies. “DDS merged with three other organizations to form the Chief Digital and Artificial Intelligence Office (CDAO) back in Feb 2022. CDAO is not currently involved with CTI and we do not have situational awareness on project participation which predated that merger,” a spokesperson said.
As for the CTI League, it claimed to serve an essential function, cybersecurity, protecting hospitals and healthcare systems from serious threats.
However, according to the new whistleblower, “The essential function of CTI League was largely duplicative of other free and paid threat services available to health care defenders.”
Justin Frappier, who worked for the Cybersecurity and Infrastructure Security Agency (CISA) of the Department of Homeland Security (DHS), wrote on his profile, “The opinions expressed here are my own as an analyst, and not those of CISA, or the US Government unless otherwise stated.”
But Frappier put the CISA seal as his profile image and was an eager participant in the CTI League. When he first joined CTIL, he asked if the group was “consolidating a list of disinformation resources to validate.” A CTIL member replied, “Yes, we are working on that. There is a whole Disinfo gathering [and] analysis operation happening in another group connected to CTI-League, which we’re working to incorporate as a threat stream.”
Responded Frappier, “That’s awesome, I think it’s amazing to see this happening at scale, long overdue but massive effort.”
Note: we redacted the files to protect identities of individuals who did not appear to play a leadership role.
These messages suggest that a government employee explicitly sought out a way to use the group for anti-disinformation activities and initiated access to these activities. Frappier contributed 573 messages to the “disinformation” channel of the Slack group.




CTIL’s disinformation team referred to using the “law enforcement escalation” channel. This channel had an FBI Cyber Crime employee and Montana’s Chief Information Security Officer (who now works as a Director at the Center for Internet Security, a CISA-funded non-profit that manages information sharing for DHS). It is unclear how often CTIL’s disinformation league sent escalations to this channel.
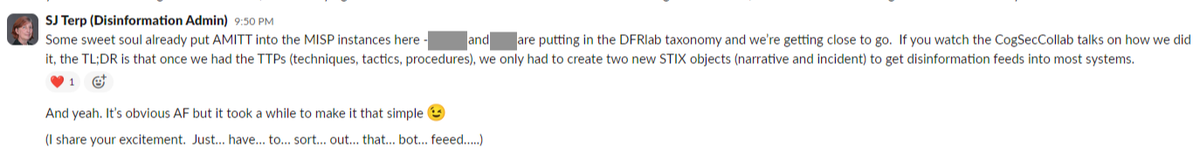
One member of the disinformation team, Andras Iklody, worked for a Luxembourg government computer security initiative at the time of CTIL’s activities, according to his LinkedIn. Iklody previously worked for NATO. Iklody appears to have set up a disinformation channel for CTIL in the Malware Information Sharing Platform (MISP) that he helped develop.
MISP is funded and sponsored by the European Union, and the Covid disinformation channel CTIL used was vetted by MISP. According to Sara-Jayne Terp, a leader of CTIL’s disinformation team, the Adversarial Misinformation and Influence Tactics and Techniques (AMITT) framework was added to MISP. The group, Terp said, was also inputting the Atlantic Council Digital Forensic Lab’s disinformation taxonomy.
When Terp explained that the group would be using MISP, Frappier responded, “I can’t tell you how exited [sic] I am that we got this up and running. I am really looking forward to what this is going to be. I think it has been long over due, and many as you said are working on similar issues, however tying it into MISP is INGENIOUS. I can’t believe I never thought of it before, and have been working with MISP for like 5 years.”
The new whistleblower’s files provide insight into the group’s inner workings, which Terp described as a “parallel effort.” Neither we nor the whistleblower know what the “parallel effort” refers to.




One member of the disinformation team, Andras Iklody, worked for a Luxembourg government computer security initiative at the time of CTIL’s activities, according to his LinkedIn. Iklody previously worked for NATO. Iklody appears to have set up a disinformation channel for CTIL in the Malware Information Sharing Platform (MISP) that he helped develop.
MISP is funded and sponsored by the European Union, and the Covid disinformation channel CTIL used was vetted by MISP. According to Sara-Jayne Terp, a leader of CTIL’s disinformation team, the Adversarial Misinformation and Influence Tactics and Techniques (AMITT) framework was added to MISP. The group, Terp said, was also inputting the Atlantic Council Digital Forensic Lab’s disinformation taxonomy.
When Terp explained that the group would be using MISP, Frappier responded, “I can’t tell you how exited [sic] I am that we got this up and running. I am really looking forward to what this is going to be. I think it has been long over due, and many as you said are working on similar issues, however tying it into MISP is INGENIOUS. I can’t believe I never thought of it before, and have been working with MISP for like 5 years.”
The new whistleblower’s files provide insight into the group’s inner workings, which Terp described as a “parallel effort.” Neither we nor the whistleblower know what the “parallel effort” refers to.


In these new files, Eric Brogdon, a cybersecurity director for a private firm, and others appear to have attempted to interfere with physical gatherings, with Brogdon implying that he had the ability to get social media users suspended.
When one member shared news about a call for anti-lockdown protests, Brogdon responded, “Let me see if I can get the Facebook user suspended.”
When asked about the incident, Brogdon sent to Public an XKCD comic strip, which argues that the First Amendment does not prevent private Internet companies from censoring speech.
But if Facebook took action on this post, it could have been a direct violation of the user’s free speech rights, and perhaps even right to assembly, given the involvement of government officials in CTIL.
Other files previously obtained by Public showed that Tom Sear of the Australian Defence Force Academy and the Joint Special Operations University was also a member of the disinformation team.


When one member shared news about a call for anti-lockdown protests, Brogdon responded, “Let me see if I can get the Facebook user suspended.”
When asked about the incident, Brogdon sent to Public an XKCD comic strip, which argues that the First Amendment does not prevent private Internet companies from censoring speech.
But if Facebook took action on this post, it could have been a direct violation of the user’s free speech rights, and perhaps even right to assembly, given the involvement of government officials in CTIL.
Other files previously obtained by Public showed that Tom Sear of the Australian Defence Force Academy and the Joint Special Operations University was also a member of the disinformation team.

No other leading participants in the CTIL responded to our requests for comment.
Once again, we are confronted with the question: what was really going on with CTIL?
Why were individuals associated with foreign governments, Special Operations, NATO, and DOD all participating in an operation to censor and influence US citizens?
Please subscribe now to support our award-winning investigative reporting and to find out!


Once again, we are confronted with the question: what was really going on with CTIL?
Why were individuals associated with foreign governments, Special Operations, NATO, and DOD all participating in an operation to censor and influence US citizens?
Please subscribe now to support our award-winning investigative reporting and to find out!


• • •
Missing some Tweet in this thread? You can try to
force a refresh