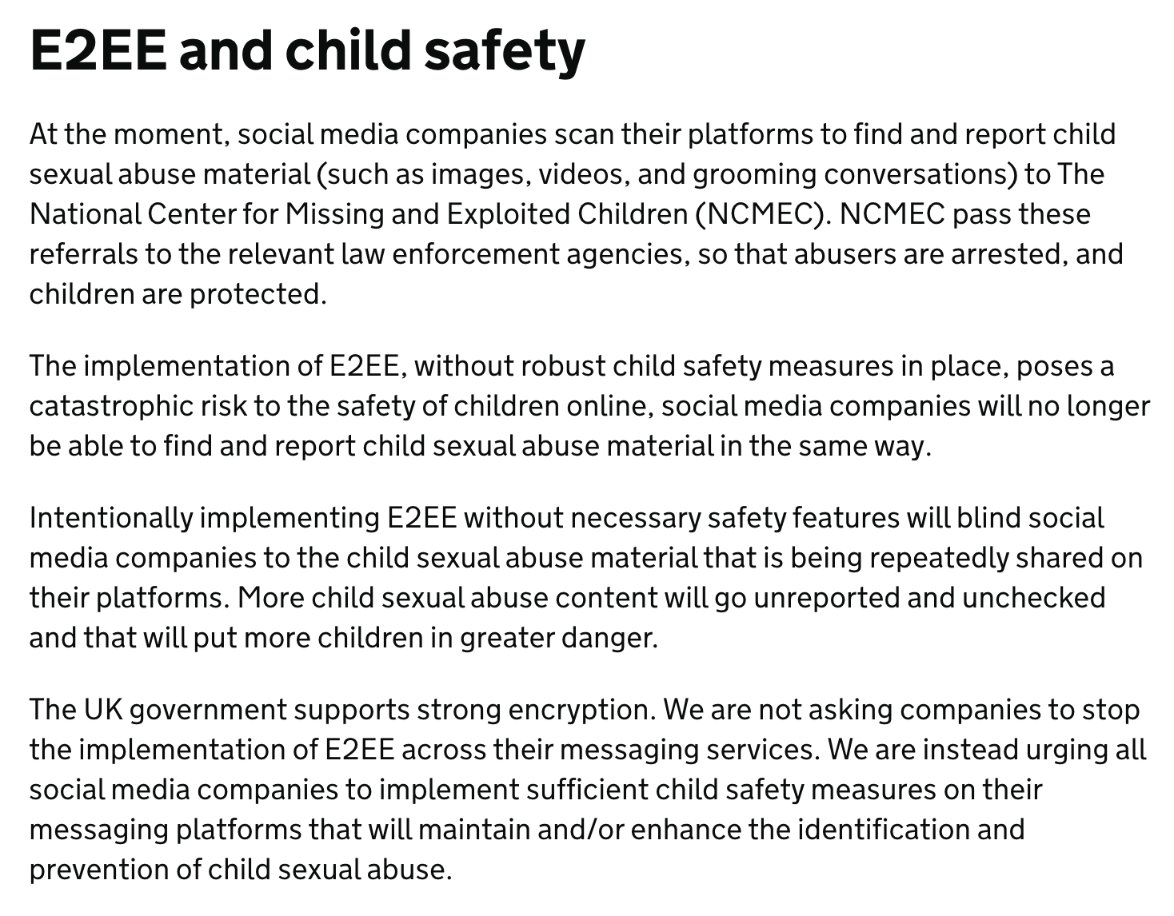
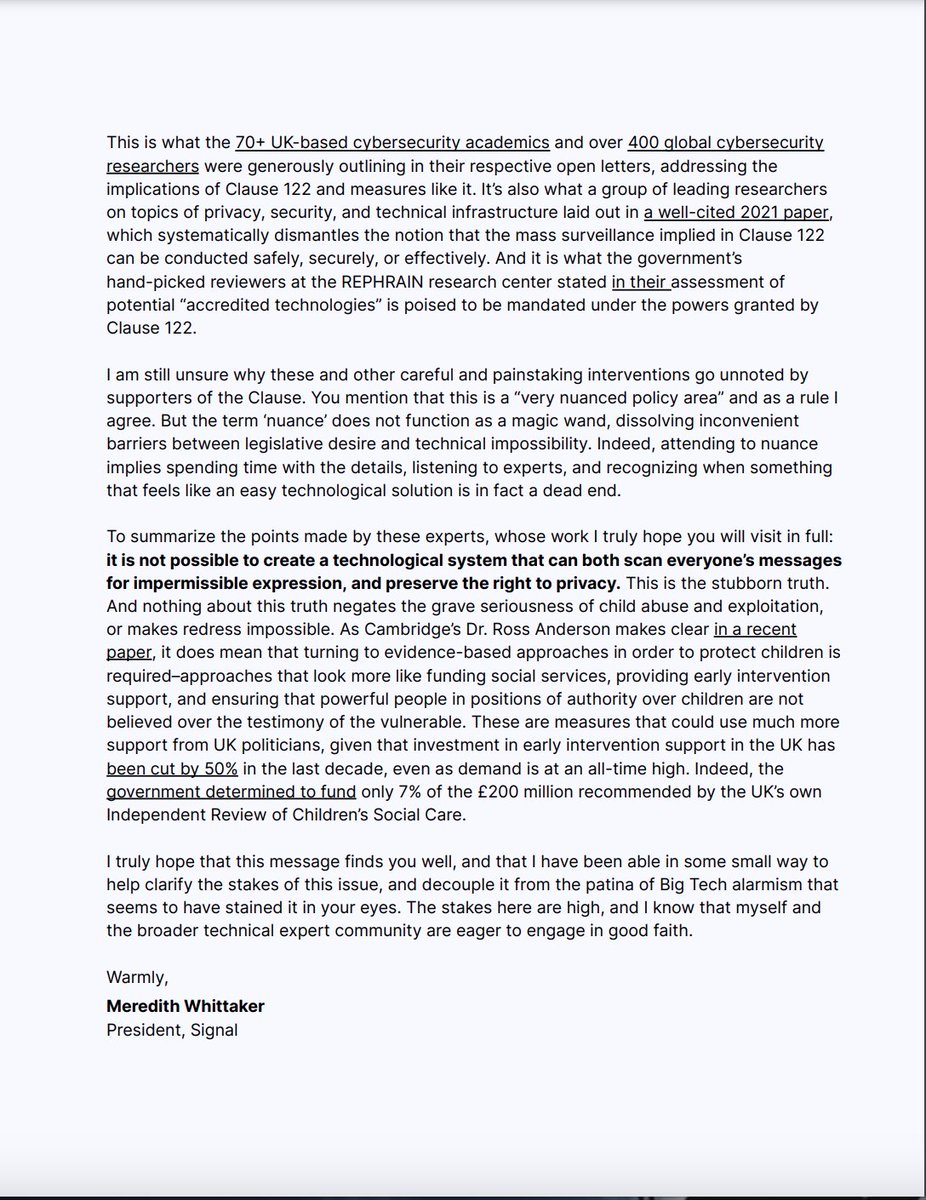
PSA: We've received questions about push notifications. First: push notifications for Signal NEVER contain sensitive unencrypted data & do not reveal the contents of any Signal messages or calls–not to Apple, not to Google, not to anyone but you & the people you're talking to. 1/
In Signal, push notifications simply act as a ping that tells the app to wake up. They don't reveal who sent the message or who is calling (not to Apple, Google, or anyone). Notifications are processed entirely on your device. This is different from many other apps. 2/
What's the background here? Currently, in order to enable push notifications on the dominant mobile operating systems (iOS and Android) those building and maintaining apps like Signal need to use services offered by Apple and Google. 3/
Apple simply doesn’t let you do it another way. And Google, well you could (and we've tried), but the cost to battery life is devastating for performance, rendering this a false option if you want to build a usable, practical, dependable app for people all over the world.* 4/
So, while we do not love Big Tech choke points and the control that a handful of companies wield over the tech ecosystem, we do everything we can to ensure that in spite of this dynamic, if you use Signal your privacy is preserved. 5/
*(Note, if you are among the small number of people that run alt Android-based operating systems that don't include Google libraries, we implement the battery-destroying push option, and hope you have ways to navigate.) 6/
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter