In today's 🧵, I'm going to demonstrate how easy it is to identify and compromise industrial control systems, for educational purposes ONLY. No actual compromise will take place, and I've intentionally chosen an example that is no longer valid.
On with the learning.
On with the learning.
First, there's a US Government organization called CISA. The acronym's expansion is unimportant; what is important is knowing that they're tasked with our nation's cybersecurity.
CISA will occasionally issue alerts and bulletins about security problems, including with
CISA will occasionally issue alerts and bulletins about security problems, including with
industrial control systems (ICS) for our nation's critical infrastructure. Here's an example from 2013:
The advisory states that Siemens Synco OZW web server devices for building automation systems have a default password. Interesting! Let's find outcisa.gov/news-events/ic…
The advisory states that Siemens Synco OZW web server devices for building automation systems have a default password. Interesting! Let's find outcisa.gov/news-events/ic…
what that is.
Pop over to a search engine, and search for "Siemens Synco OZW default password". I'm using Bing, for reasons.
We're looking for an installation/configuration manual for the Siemens OZW products. In this instance, the first result works:
Pop over to a search engine, and search for "Siemens Synco OZW default password". I'm using Bing, for reasons.
We're looking for an installation/configuration manual for the Siemens OZW products. In this instance, the first result works:

Let's look at it. Go to the Table of Contents, and look for the first thing that looks like logging into the device. Here we go: 
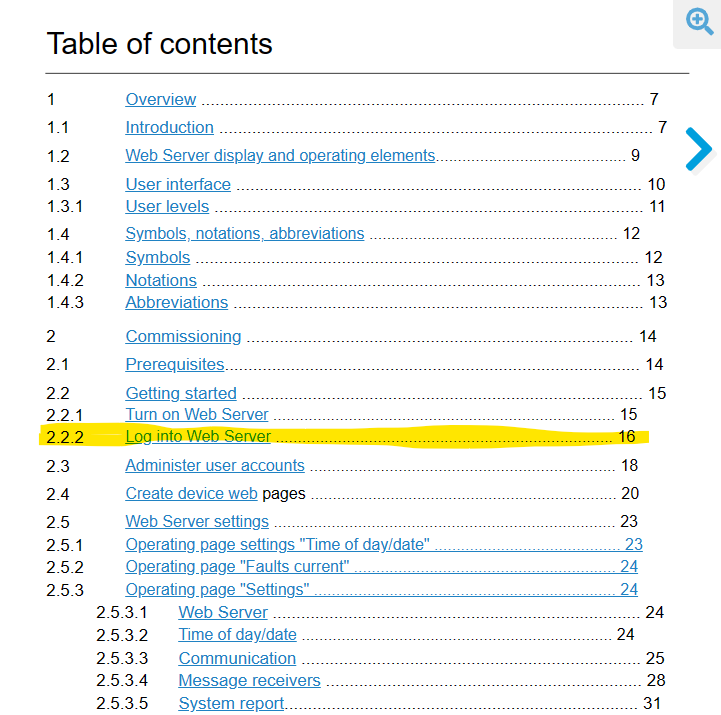
So, we go to page 16. It helpfully shows the default administrator username, and the default password (in this case, two of them depending on firmware version). It even helpfully shows what the login screen will look like: 
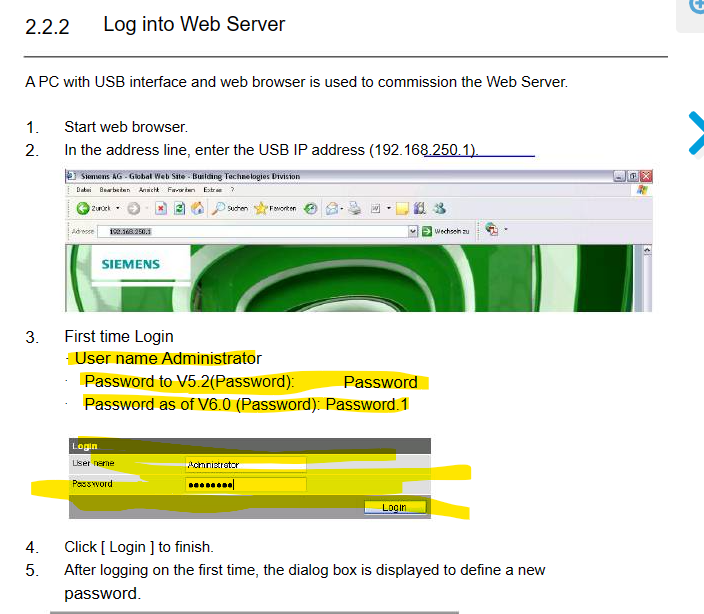
You'd be disgusted to know how many critical control systems get connected to the internet and no one ever bothers to change the default password, or disable the default accounts. They're usually so simple that, with practice, you can generally guess correctly without having to
look it up, sometimes.
Anyway, now we know that these things have a default password, and we know what the credentials are. How do we find the devices online?
There are multiple ways, but one of the easiest is a free service called Shodan.
Go to ,shodan.io
Anyway, now we know that these things have a default password, and we know what the credentials are. How do we find the devices online?
There are multiple ways, but one of the easiest is a free service called Shodan.
Go to ,shodan.io
and type in "siemens port:80". Sometimes it's just that simple. A lot of results will come back. In this case, most of them are these devices. We specified "port:80" because, of course, many of these ICS systems don't even bother with HTTPS. 
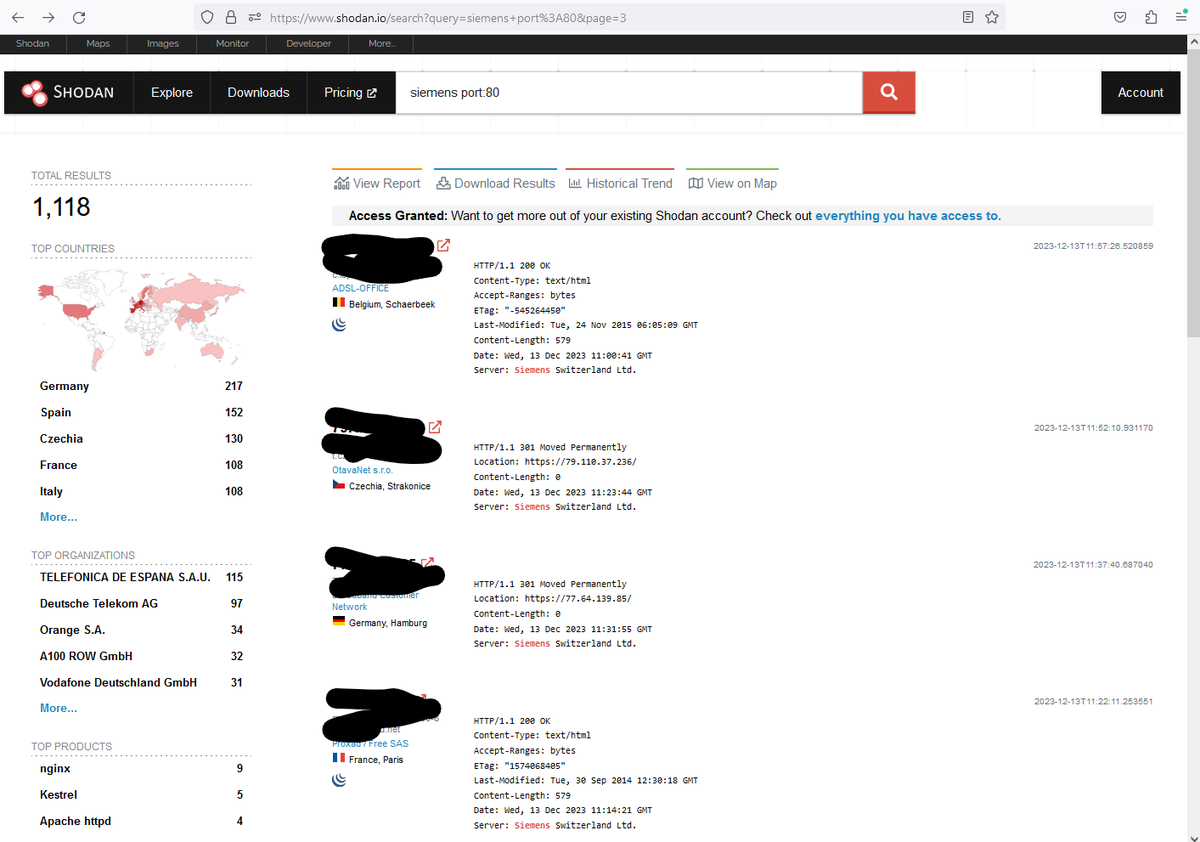
Visiting one of them would yield confirmation that these are the devices in question. We won't do that, because that's crossing from passive to active reconnaissance, and that's starting to tread into territory we want to avoid. This is just educational.
If one were to do that, however, you'd see something like this, confirming you've found a relevant device. From there, if you were a hardened criminal and did not care about the law, you could begin trying the default credentials to see if they work. 

As I mentioned earlier, there are all manner of devices accessible from the internet, many of which have multiple vulnerabilities, including default credentials. And our government (and multiple cybersecurity companies, along with cybersecurity researchers) are quick to
publicly announce these vulnerabilities as soon as they find them, often with enough information to create an exploit for the vulnerability. Sometimes, they even provide the exploit, too!
And there are much more serious devices that building automation (not that one couldn't
And there are much more serious devices that building automation (not that one couldn't
cause some serious shenanigans with a building automation system). For example, the US Emergency Alert System (the thing that controls the loud emergency alerts you get on radio, TV, and phones nationwide). The system runs on a series of authenticated devices distributed
to carriers and broadcasters nationwide. These devices have the ability to not just receive, but create and send alerts as well. Pretty much the only thing protecting them is that most people don't know what they're called.
They're called DASDECs. Once you know that, you can
They're called DASDECs. Once you know that, you can
just search for "DASDEC", and sure enough, you'll find them.
They also have default credentials, discoverable via the same method I described above.
This is absolutely not my image; I found it online. However, were one to access one of these devices (DO NOT DO THIS),
They also have default credentials, discoverable via the same method I described above.
This is absolutely not my image; I found it online. However, were one to access one of these devices (DO NOT DO THIS),
one might see a screen similar to this, allowing a person to inject an alert into the Emergency Alert System and specify its delivery date, time, and area: 
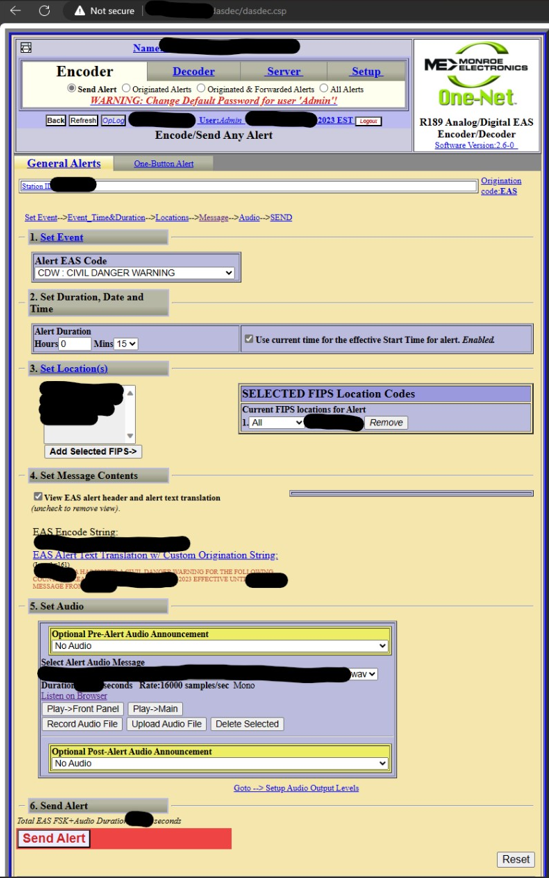
As you can see, all it takes to cripple critical infrastructure is a search engine, a manual, a service like Shodan, and knowledge of a vendor and/or product make/model, and knowledge of a vulnerability and the ability to exploit it. And yes, default credentials are very much
a vulnerability. So much so, they're classified in a vulnerability taxonomy put together by MITRE, an FFRDC: cwe.mitre.org/data/definitio…
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter



