🚨 ledger library confirmed compromised and replaced with a drainer. wait out interacting with any dapps till things become clearer.
cdn.jsdelivr.net/npm/@ledgerhq/…

cdn.jsdelivr.net/npm/@ledgerhq/…
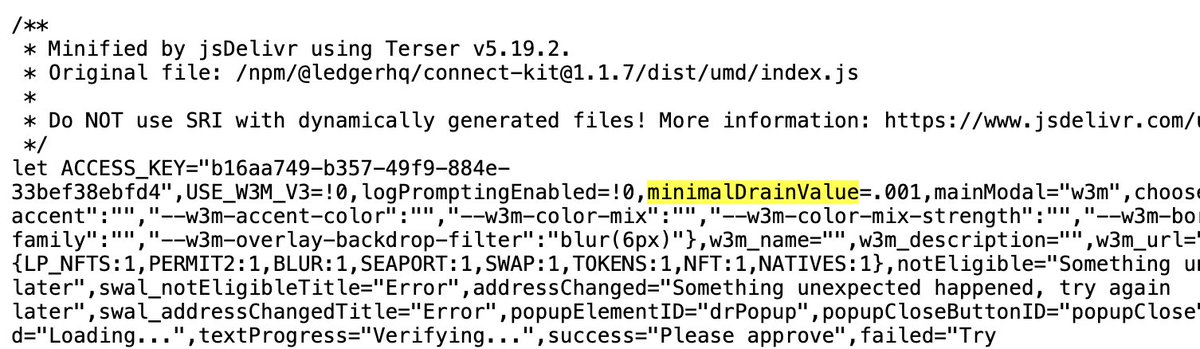
seems ledger connect-kit-loader is also vulnerable since it specified the dep loosely
possible list of affected parties
github.com/LedgerHQ/conne…
sourcegraph.com/search?q=conte…
possible list of affected parties
github.com/LedgerHQ/conne…
sourcegraph.com/search?q=conte…
ledger asks to use connect-kit loader to load connect-kit, but even if you follow the best practices and pin the version of the loader loader, it fetches the latest version of connect-kit >=1.0.0, <2.0.0.
this has allowed the attackers to infiltrate a shitton of libraries by compromising just the connect-kit. last known version coming from ledger is 1.1.4. three releases up to 1.1.7 were posted today, all should be considered compromised.
this has allowed the attackers to infiltrate a shitton of libraries by compromising just the connect-kit. last known version coming from ledger is 1.1.4. three releases up to 1.1.7 were posted today, all should be considered compromised.
ledger pushed a new version, @1 should match 1.1.8 now.
it still doesn't add strict version pinning, which is better addressed here.
the version is still not on npm yet though and it doesn't guarantee the fix if the attacker can still publish new packages.
github.com/LedgerHQ/conne…
github.com/LedgerHQ/conne…
npmjs.com/package/@ledge…
it still doesn't add strict version pinning, which is better addressed here.
the version is still not on npm yet though and it doesn't guarantee the fix if the attacker can still publish new packages.
github.com/LedgerHQ/conne…
github.com/LedgerHQ/conne…
npmjs.com/package/@ledge…
cdn code looks updated, the vulnerability is contained.
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter












