Day 2️⃣0️⃣ of Your 30 Day SOC Analyst Journey
How to detect Windows Attacks - Kerberoasting:
How to detect Windows Attacks - Kerberoasting:
Kerberoasting is one of the quickest way for an attacker to get password hashes and try to crack them to get to the passwords
It is based on a “feature” that essentially allows anyone to request a ticket (TGS) from the domain controller without knowing the users password
It is based on a “feature” that essentially allows anyone to request a ticket (TGS) from the domain controller without knowing the users password
This only works for service accounts - those that have a Service Principal Name (SPN)
The received ticket/hash is encrypted with the users password and thus it can be used to brute-force passwords of so called service accounts
The received ticket/hash is encrypted with the users password and thus it can be used to brute-force passwords of so called service accounts
PHEEEEW thats a lot of words I dont understand yet mr maikroservice.
Gotcha - let’s make this clearer by first running the attack hands-on:
There are multiple tools that can run kerberoasting attacks - two of the more prominent one’s are rubeus & impacket-GetUserSPNs.py
Gotcha - let’s make this clearer by first running the attack hands-on:
There are multiple tools that can run kerberoasting attacks - two of the more prominent one’s are rubeus & impacket-GetUserSPNs.py
download rubeus here
This is kinda ok for the lab but DO NOT run any precompiled (malware) binary from the internet on company infrastructure! big NO NOgithub.com/r3motecontrol/…
This is kinda ok for the lab but DO NOT run any precompiled (malware) binary from the internet on company infrastructure! big NO NOgithub.com/r3motecontrol/…
💡 Always download the source code, check it and compile the binary yourself - I will share how to do that in the bootcamp.
Which bootcamp?
I will tell you at the end of the thread!
Which bootcamp?
I will tell you at the end of the thread!
Ok once, you have rubeus downloaded run the attack via
rubeus.exe kerberoast /nowrap
You should see something like this:
rubeus.exe kerberoast /nowrap
You should see something like this:

You can see the domain, the LDAP query that is used to check for service accounts and if all goes well also a hash at the bottom that you might be able to crack 😈
Ok great but what do we do with that?!
Ok great but what do we do with that?!
That my friends is the exact right question - you are a (future) SOC Analyst so you want to detect this attack.
How do you do that? You use your methodology
Well… I dont have one yet…
How do you do that? You use your methodology
Well… I dont have one yet…
Ok lets build it together - First, you look at available logs, your favorite data source in the whole wide world.
Which logs though?
Which Operating System are we talking about here?
Windows
Which logs though?
Which Operating System are we talking about here?
Windows
Great, remember the Windows Event Logs?
We talked about windows event logs and the availability of at least 4 different logs.
If you dont know where to start, go to what you know first.
We talked about windows event logs and the availability of at least 4 different logs.
If you dont know where to start, go to what you know first.

Open the event viewer and now you have a slight issue - there will probably be a lot of events in the logs already…
pheeew… Lucky for us, we are in a Lab environment, so we can just delete all the logs, run the attack again and see what happens.
Shall we?!
pheeew… Lucky for us, we are in a Lab environment, so we can just delete all the logs, run the attack again and see what happens.
Shall we?!

💡 Once you cleared all the logs you will see one event in the System log with ID 104 / 1102 in security logs - this is fired when someone deletes the logs! You might want to check for this with your SIEM as well ;) 

Ok done, now we fire up the attack again and refresh the logs (right section - middle of the screen) 

_umm… nothing? _
Well that depends on which computer you used for the attack. But yes, it could be empty.
_Which computer do we need to check the logs on? _
the domain controller.
Well that depends on which computer you used for the attack. But yes, it could be empty.
_Which computer do we need to check the logs on? _
the domain controller.
ohhhh, yes that makes sense because this attack needs a ticket and those are issued by the domain controller!
ok, lets clear the logs again and check for new information.
Once again DO NOT DO THIS IN PRODUCTION/at your company - ONLY in a lab environment!
ok, lets clear the logs again and check for new information.
Once again DO NOT DO THIS IN PRODUCTION/at your company - ONLY in a lab environment!
Go through the logs - you will see something interesting at some point, an Event with ID 4769.
If you remember we talked about 4768 (kerberos ticket requested) and 4769 (kerberos ticket issued) in the kerberos thread → kerberoasting attacks create a #4769 event
If you remember we talked about 4768 (kerberos ticket requested) and 4769 (kerberos ticket issued) in the kerberos thread → kerberoasting attacks create a #4769 event

Kerberos Blog post: maikroservice.com/how-does-kerbe…
Great, we can start writing a behavioral rule to detect this now!
Since you don’t (yet) know how to look for windows EventIDs you google for something along the lines of “Windows event logs wazuh” which leads you to this reddit post reddit.com/r/Wazuh/commen…
Since you don’t (yet) know how to look for windows EventIDs you google for something along the lines of “Windows event logs wazuh” which leads you to this reddit post reddit.com/r/Wazuh/commen…
and in it there is a section that states
Looking for that eventID, you can find the following rule
so you click on that link and see this: github.com/wazuh/wazuh-ru…

Looking for that eventID, you can find the following rule
so you click on that link and see this: github.com/wazuh/wazuh-ru…

here there is a field called “win.system.eventID” followed by some weird looking symbols e.g. ^20187$
Remember how all the field content thingies are regular expressions?
Remember how all the field content thingies are regular expressions?
If you know regular expressions you already know what the ^ (caret) and $ mean, but if not - you google again for:



OHHHH ok so the ^ is the start & the $ is the end + if both are there it matches everything in between
We can use that to write our own rule, right?!
When looking for this attack you need to make sure that each computer uses sysmon to forward logs to wazuh
We can use that to write our own rule, right?!
When looking for this attack you need to make sure that each computer uses sysmon to forward logs to wazuh
First we have the group that has to always be there
we have the rule with a unique ID (>100,000) and a level between 0 & 16 - higher = more ⚠️DANGER⚠️
Then we have our field that we are looking for - win.system.eventID and the value we are looking for ^4769$
we have the rule with a unique ID (>100,000) and a level between 0 & 16 - higher = more ⚠️DANGER⚠️
Then we have our field that we are looking for - win.system.eventID and the value we are looking for ^4769$
Wait! Why can we not just use 4769?
well… what happens if we have a rule 14769? or 24769?
oh… ok got it, so the ^ and $ make sure that only this specific ID triggers the rule
Yes exactly!
well… what happens if we have a rule 14769? or 24769?
oh… ok got it, so the ^ and $ make sure that only this specific ID triggers the rule
Yes exactly!
Now let’s test that rule, shall we?!
open wazuh - head to Management → Rules → Add new rules file
open wazuh - head to Management → Rules → Add new rules file
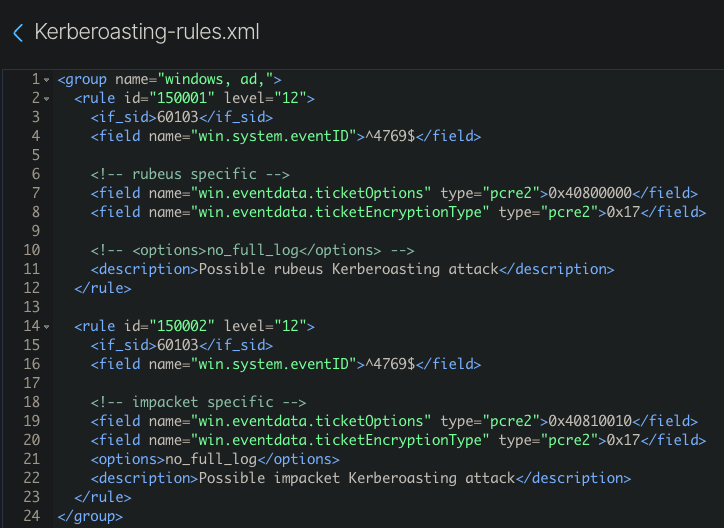
Let’s look closely into each one and see if we can find out differences between them → click on the small triangle next to the time and check the fields! 

What are the differences?!
- 0x12 vs. 0x17
.eventdata.ticketOptions - 0x40810000 vs. 0x40800000
.system.eventRecordID - 56148 vs. 56150
Ok great, but what is that?! data.win/eventdata.tick…
data.win
data.win

- 0x12 vs. 0x17
.eventdata.ticketOptions - 0x40810000 vs. 0x40800000
.system.eventRecordID - 56148 vs. 56150
Ok great, but what is that?! data.win/eventdata.tick…
data.win
data.win

Those fields are pretty interesting, except for the eventRecord - that one is “just” a number that counts up for each event.
The ticketEncryptionType of 12 vs 17 might throw you off - this is juicy! First off, the 0x means it is hexadecimal and the value is 12 (0x12) / 17 (0x17) respectively.
When you google for those values in combination with kerberoasting you will find the following blog post ()
In it is a nice table showing what the Encryption Types stand for - 0x12 = AES256 encryption, 0x17 = RC4 encryption adsecurity.org/?p=3458

In it is a nice table showing what the Encryption Types stand for - 0x12 = AES256 encryption, 0x17 = RC4 encryption adsecurity.org/?p=3458

Too much information - Why do I need to know this?!???
Windows Events will play a major role in your job and knowing what is normal and what NOT will save your company more than once in the future.
Windows Events will play a major role in your job and knowing what is normal and what NOT will save your company more than once in the future.

AES256 (0x12) is part of the new “normal” while RC4 (0x17) should be a RARE exception and in my experience very often is used by either attackers, their tools or legacy software.
That means, 0x17 as the encryptionType is a possible indicator of compromise, while 0x12 is “normal” (in quotes, because there can also be 0x11 and others depending on the environment you are in).
Remember how 4769 events are technically just Kerberos ticket events? Well, what happens every time you login with your domain account?
Correct, a 4769 event is triggered, BUT the encryption type is 0x12 (most likely) and the ticketOptions = 0x40810000
while for Rubeus-triggered Events it is 0x17 and 0x40800000
We can use that for a more specific RULE!
while for Rubeus-triggered Events it is 0x17 and 0x40800000
We can use that for a more specific RULE!
Here we use the pcre2 regular expression that is similar to the way the programming language Perl handles it - more information in the documentation - documentation.wazuh.com/current/user-m…


Ok great, but what if the attacker uses a different tool?!
Lets try with another one - impacket, shall we?!
Lets try with another one - impacket, shall we?!
When you check the Windows Event you will see that impacket has different ticketOptions - 0x40810010 compared to rubeus, but the same ticketEncryptionType - 0x17 

I hope you learned something today - if you did please consider following me @maikroservice for more content just like this.
and one last thing - if you loved this 🧵
and one last thing - if you loved this 🧵
You have 3 days left to buy my upcoming course the Practical SOC Analyst 101 for the low price of $50 - on January 1st the price will go up to $150 and it will NEVER be this low again.
Not convinced yet?
Not convinced yet?
What if I told you if you order until January 1st you will get a spot in the upcoming cohort-based bootcamp FOR FREE ($400 value)?!
GREAT WHERE CAN I SIGN UP
Glad you asked:
academy.maikroservice.com/l/soc101

GREAT WHERE CAN I SIGN UP
Glad you asked:
academy.maikroservice.com/l/soc101

@threadreaderapp unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh