First, I want to compliment @Microsoft for being forthright with details. Some of the problems I see in this report, I SEE EVERYWHERE due to VULNERABLE DEFAULTS.
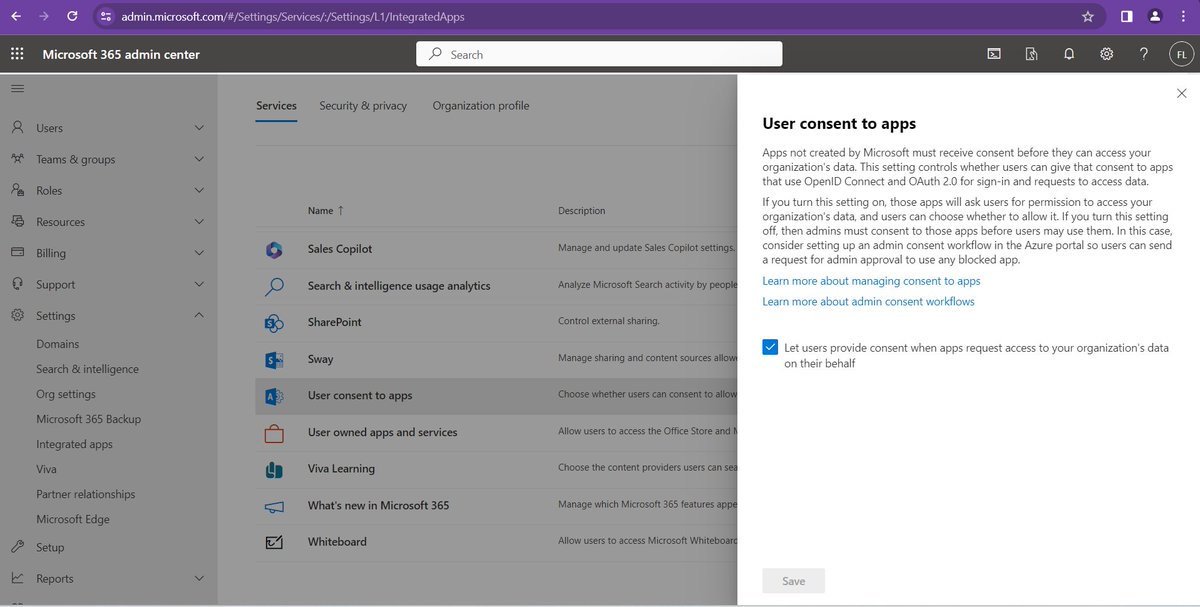
Let's start with creating malicious OAuth applications. By default, ANY USER can create app registrations and consent to Graph permissions as well as sharing 3rd party company data. In tenants where this is hardened, ability to create app registrations require Application Administrator or Cloud-Application Administrator and admins must consent to permissions used by the application whether local or from another tenant.
Let's start with creating malicious OAuth applications. By default, ANY USER can create app registrations and consent to Graph permissions as well as sharing 3rd party company data. In tenants where this is hardened, ability to create app registrations require Application Administrator or Cloud-Application Administrator and admins must consent to permissions used by the application whether local or from another tenant.

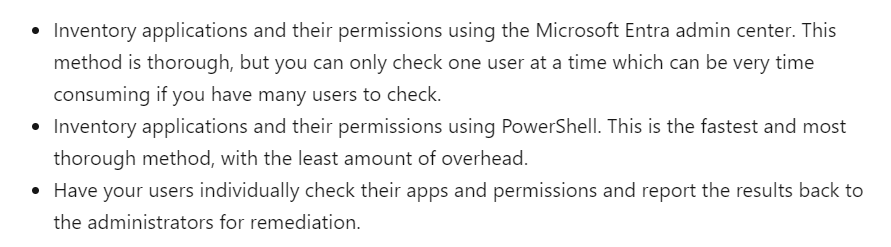
Go here and check ALL your app registrations and associated permissions. Make sure you know what they are! 

And FFS, ALL ADMINS SHOULD HAVE PHISHING RESISTANT MFA!
Also, stop signing in from unmanaged devices with privileged accounts! You check private email or browse to a sight and get hacked, attacker gains access to your admin tokens and tenant! Use a dedicated secured device to access your MS Cloud as an admin.
Also, stop signing in from unmanaged devices with privileged accounts! You check private email or browse to a sight and get hacked, attacker gains access to your admin tokens and tenant! Use a dedicated secured device to access your MS Cloud as an admin.
And start doing governance! Yes, I'm talking to you @Microsoft - who has a governance product line. Use the software you create!
And if you don't believe me that these attacks are common and not just Cozy Bear, you really should check out @AlteredSecurity 's CARTP and CARTE classes.
@cnotin @Microsoft There's too many different configurations and ways that could have happened that I dint want to make anymore assumptions. That's why I chose to talk about creating an OAuth app.
@NickCerny @inversecos Mostly.
@cnotin @Microsoft I don't need to 'spalined over and over and over again. Sigh
@cnotin @Microsoft I'm talking about a persistence mechanism is see on almost all IR engagements
@cnotin @Microsoft Maybe people should open their minds more instead of always "correcting me" and maybe they will learn more.
@cnotin @Microsoft This is ALSO why I highlighted EXACTLY WHAT I'M TALKING ABOUT so when the 'splainers showed up, they can reference the VERY FIRST PIC on the thread
@cnotin @Microsoft This thread is not a post-mortum. It's simply to supply quick tips to mitigate app registrations by low privileged users for persistence. That is all. The Graph permissions I'm discussing are clearly delegated but here is a screen shot for hthose not familiar: 

• • •
Missing some Tweet in this thread? You can try to
force a refresh