We're naming names 🔥 because the harm is not hypothetical.
Today we share "Buying Spying", our new report diving into the commercial surveillance/spyware industry. We dive into the players, the campaigns, the spyware, & the harm it perpetuates.
blog.google/threat-analysi…

Today we share "Buying Spying", our new report diving into the commercial surveillance/spyware industry. We dive into the players, the campaigns, the spyware, & the harm it perpetuates.
blog.google/threat-analysi…

There's also lots of goodies that we've never released before like:
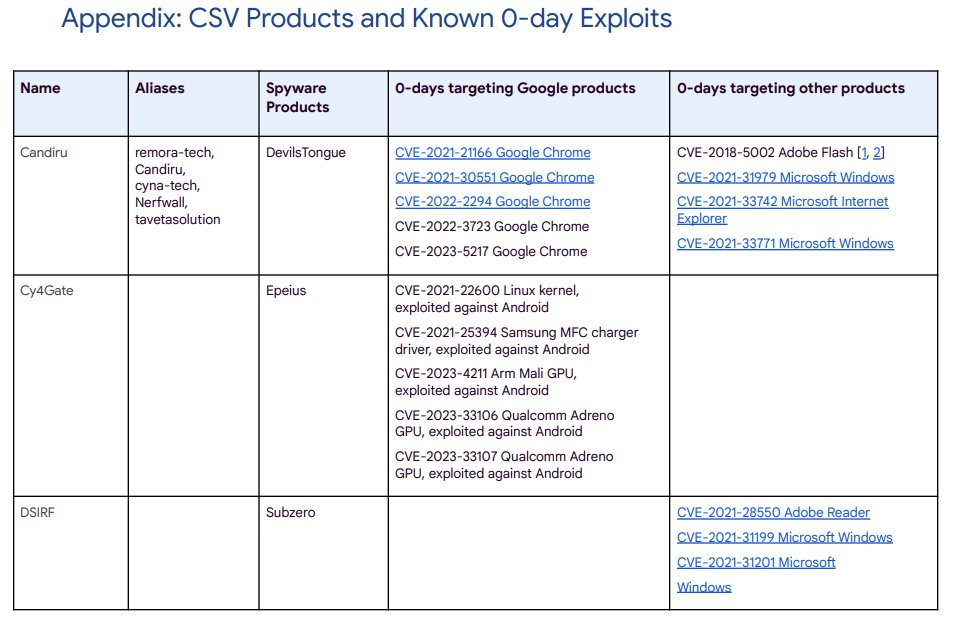
👀 That Chrome 0-day (CVE-2023-7024) @_clem1 discovered in Dec? NSO Group
🤔 Which vendor gets caught the most
🕐 In April, it took Intellexa 45 days to come back after their Chrome 0days were caught & patched
👀 That Chrome 0-day (CVE-2023-7024) @_clem1 discovered in Dec? NSO Group
🤔 Which vendor gets caught the most
🕐 In April, it took Intellexa 45 days to come back after their Chrome 0days were caught & patched
While most are not at risk of being personally targeted with these capabilities, the impacts affect us all. When the most at-risk in our society: human rights defenders, journalists, opposition politicians, etc are targeted, that threatens & harms our free societies as a whole.
I'm so thrilled that we're getting this out to share and so thankful that I got to work with some incredible people on this: @auroracath @k_dennesen @az_matazz @charley_snyder_ @Kimberly_Samra @_clem1
Go check out the full 50 page report:
storage.googleapis.com/gweb-uniblog-p…

Go check out the full 50 page report:
storage.googleapis.com/gweb-uniblog-p…

• • •
Missing some Tweet in this thread? You can try to
force a refresh