#threatintel
someone just leaked a bunch of internal Chinese government documents on GitHub
github.com/I-S00N/I-S00N/
someone just leaked a bunch of internal Chinese government documents on GitHub
github.com/I-S00N/I-S00N/
From the looks of it, it looks like a bunch of spyware developed by the company 安洵信息
Some of these software features includes obtaining the user's Twitter email and phone number, realtime monitoring, publishing tweets on their behalf, reading DMs. 

Custom RAT built for Windows x64/x86 with features such as process/service/registry management, remote shell, keylogging, file access logging, obtaining system info, disconnect, uninstallation.




A Mac version also exists, with features such as remote shell, file management, screenshot and keylogging.






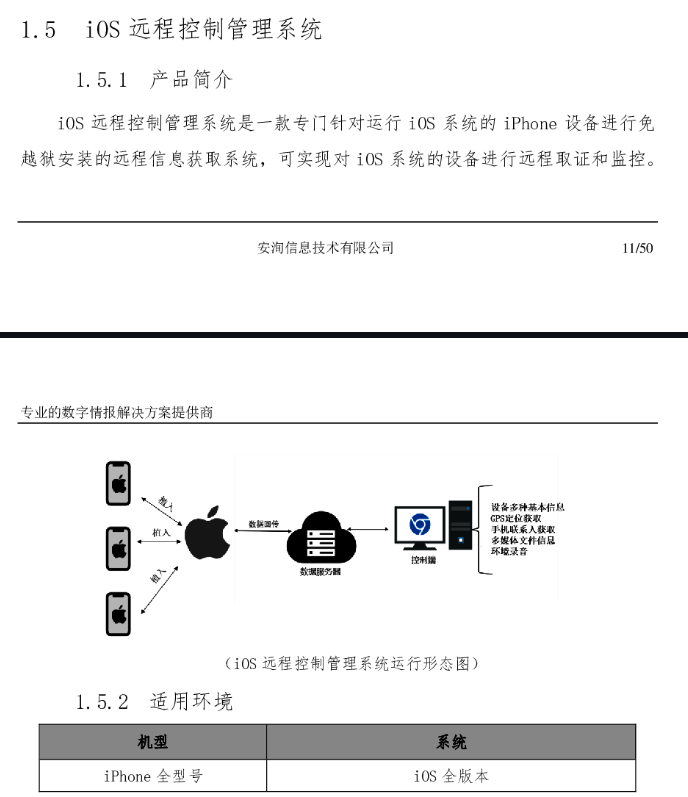
An iOS version also... exists somehow, and they claim that this supports all iOS versions. Includes features such as gathering hardware information, GPS data, contacts, media files, and real-time audio record.
No jailbreak required.



No jailbreak required.


Android version also exists, supporting Android 6.0 and above. Features include obtaining system information, GPS, contacts, SMS, call logs, browser history, app list, real-time audio recording, process list, camera, WiFi list, screenshot, keylogging, and system info. 

Few interesting tidbits for the Android one
- Ability to dump messages from QQ, WeChat, and MoMo - all popular Chinese IM apps (requires root)
- Ability to keylog specifically QQ, WeChat, Momo *AND* Telegram.
- Ability to elevate as system app for persistence (requires root)



- Ability to dump messages from QQ, WeChat, and MoMo - all popular Chinese IM apps (requires root)
- Ability to keylog specifically QQ, WeChat, Momo *AND* Telegram.
- Ability to elevate as system app for persistence (requires root)



Linux version also exists that specifically supports CentOS 5/6/7 & Ubuntu 12/14. Oddly old versions of these distros. Features include remote shell, file management, Socks5 proxy via SocksCap64, port reuse. Controller appears to be named "TracedStone"




This is the weirdest of them all - a WiFi-capable device that can inject into the targeted... Android devices via WiFi? The device is said to be portable, plug and play, supports 3G and 4G. After a successful injection, it can get device info, GPS, SMS, contacts, call log, files




Another one: "WiFi Near Field Attack System," with a Standard and Mini edition. The standard version can be installed on a specifically crafted device and be used to infiltrate the internet network... somehow. It doesn't explain. 

The Mini version is said to be able to disguise as a power strip, power adapter etc. and can be set up to connect to target WiFi and establish a SOCKS tunnel with the internal network. 

The standard version comes with 4G ability, 8GB eMMC, dual core 1.2GHz ARM processor, 10000 mAh battery, whilst the mini version runs on MIPS with 128MB of DDR2(?) and does not contain a battery. 

The standard version is disguised as a Xiaomi battery, whilst the mini version is just a plain PCB that can be inside anything. 

The Standard edition can be used to crack WiFi passwords, LAN port sniffing, SOCKS tunnel, port projection, remote shell, file management, and remote detonation (self-destruct). 

Correction: technically not Chinese government data, but a spyware vendor contractor's internal data.
Next chapter, they also have a DDoS system. The botnet client is 29kb sized and can be deployed on to Windows, Linux, or generic IoT devices with the total throughput of 10~100Gbps (or GBps? not specified).




Automatic pentesting system that supports Windows, Linux, web services, and networking equipment with support for various pentesting frameworks.




It also supports specialized APT attack scenarios, including generating email templates, browser-based attacks, exploited Office document generator and more. 

There's also specialized hardware for tracking down WiFi devices (i.e. alert when device with WiFi's MAC address is in range) and disrupt WiFi signals and can be controlled with a dedicated smartphone.






A dedicated Tor-like device for hopping between endpoints. Designed specifically for agents working overseas.






Product stack designed for spying on users using Chinese social media, including Weibo user details lookup (email/phone), historic IP address lookup, user detail lookup via the uploaded image (i.e. Alice uploads food pic to Weibo, Alice's details can be pulled up). 

Features designed specifically for forums:
- Emote beacon: Effectively IP grabber when opened: the user's IP address, portt, time, browser details are returned.
- Link beacon: Same thing as above but URL-based.
- Emote beacon: Effectively IP grabber when opened: the user's IP address, portt, time, browser details are returned.
- Link beacon: Same thing as above but URL-based.

Platform designed specifically for cracking down gambling cases, can be used to look up username, email, password, home address, IP address, etc. Notably, an email address of admin@webside.com can be seen. Not sure if this is a typo of "website"




"Skywalker" data research platform. Used to look up information related to the keyword, such as phone address, email, username, which would then bring up their IRL details. 

This information can then be fed into an "in-development" feature of looking up user details on various social media, including QQ, WeChat, Weibo, Facebook, and Twitter. 

Email text search platform. The emails can be automatically imported via SMTP, POP3, iMAP, and most importantly, Exchange. Exchange server can be configure to add "non-plaintext" transfer during transport. 

That was *most* of the data in just ONE PDF file that is leaked from this repository. There's presumably a lot more to dig through.
The rest of the repo seems to be mostly low-res screenshots (presumably thumbnails?) of various WeChat logs, and random camera shots of random notes.
I'll be posting the rest of the updates back in the Mastodon thread.
infosec.exchange
infosec.exchange/@still/1119545…
infosec.exchange
infosec.exchange/@still/1119545…
This blew up so instead of plugging something I'm gonna tell you to go read the chat log analysis I'm doing over at .
infosec.exchange
infosec.exchange/@still/1119545…
infosec.exchange
infosec.exchange/@still/1119545…
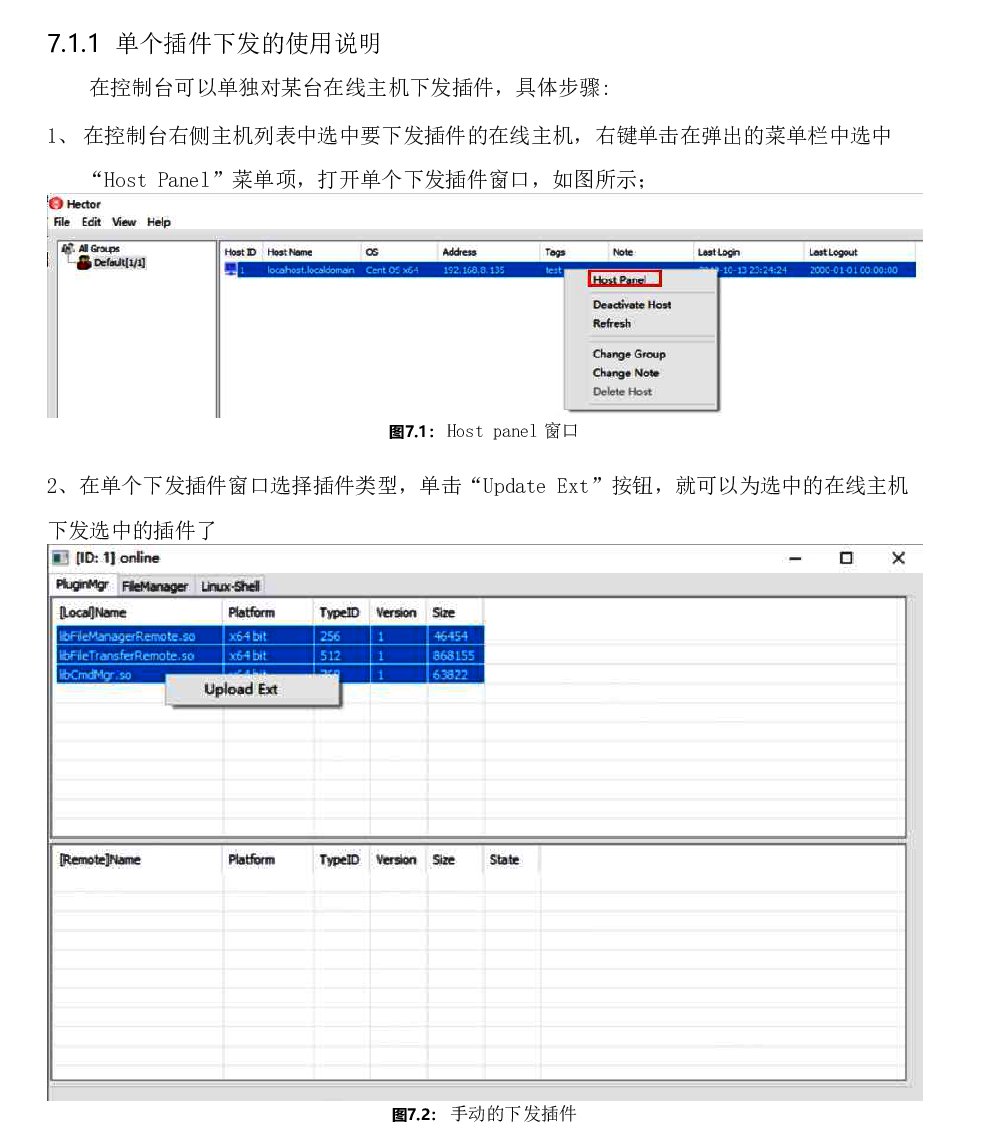
There's also a RAT called Hector.
"Hector is an active RAT that supports HTTP/WebSocket and HTTPS/WS over TLS."
"Hector supports interactive remote shell, file directory viewing, file management."



"Hector is an active RAT that supports HTTP/WebSocket and HTTPS/WS over TLS."
"Hector supports interactive remote shell, file directory viewing, file management."



The chatlogs are extremely fascinating as they provide a much broader view of how people are making money off of attacking critical government agencies. I'm seeing quotes and prices all in these chatlogs over intel/data from these hacked institutions.




The point I want to make is it's not *just* government hired actor, but companies are profiting off of these contracted attacks.
someone from the chatlog also claimed that they have data from Jens Stoltenberg (Secretary General of NATO) they've been wanting to sell 

uhhh I'm gonna be muting this thread because it's nuking my notification
• • •
Missing some Tweet in this thread? You can try to
force a refresh