🚨NEW - iSoon & the Chinese cyber mercenary ecosystem 🚨
Going back to my roots with some good old fashioned China cyber analysis @Margin_Research. How is iSoon related to cyber mercenaries, and the Chinese offensive ecosystem? 🧵/ 5 findings:
margin.re/2024/02/same-s…
Going back to my roots with some good old fashioned China cyber analysis @Margin_Research. How is iSoon related to cyber mercenaries, and the Chinese offensive ecosystem? 🧵/ 5 findings:
margin.re/2024/02/same-s…
1️⃣ Tianfu Cup confirmed to be exploit feeder system for the Chinese Ministry of Public Security (MPS). If the stuff isn’t fullchain ⛓️(ready to use), the MPS disseminates the proof-of-concept code to private firms to further exploit. 

This is absolutely the precursor to the wider CN vulnerability disclosure laws - tagging great reporting by @DakotaInDC @kristindelrosso atlanticcouncil.org/in-depth-resea…
@ anyone interested in curbing proliferation of these capabilities, look at the last line of the chat 💀 
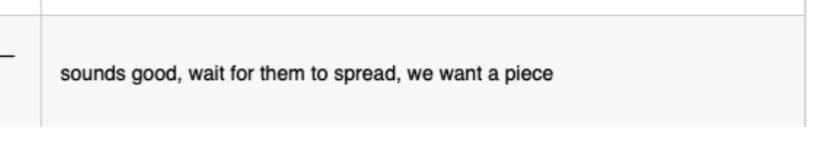
Also confirmation of @HowellONeill’s great reporting here: technologyreview.com/2021/05/06/102…
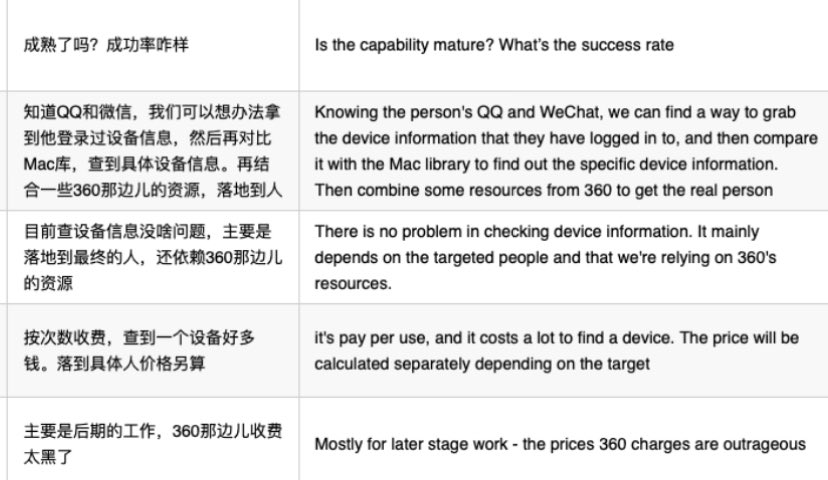
2️⃣ Qihoo360 invests in cyber mercenaries and may have even sold user PII? 360 is a series A investor in iSoon AND chatlogs suggest iSoon is being sold 360 PII… 😱 that’s the equivalent of Symantec selling data to Palantir… 
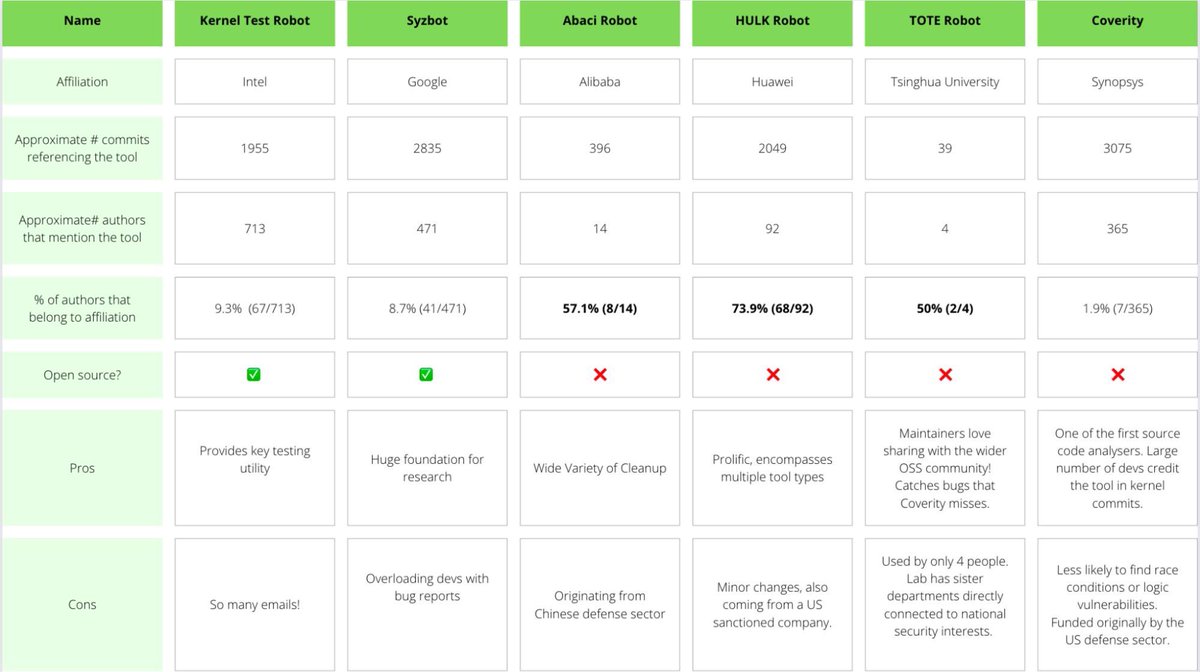
3️⃣ this is a well-funded, prime/sub-contracting ecosystem, like NSO/Intellexa.
🇨🇳 offensive capabilities firms are large, sometimes venture-backed firms in a dense ecosystem of players. Some firms directly bid for contracts, some work with large primes, and some join forces.
🇨🇳 offensive capabilities firms are large, sometimes venture-backed firms in a dense ecosystem of players. Some firms directly bid for contracts, some work with large primes, and some join forces.
5️⃣ ofc, CN firms have a well established Capture-the-Flag (CTF) to hiring pipeline for offensive talent: something many people who play CTF have known for years. ctftime.org/stats/2021/CN
Why should you care?
Yes, NSO is well known but this is a global market for capabilities, and China is key player. Prior to this leak, little has been made public about the Chinese offensive cyber capability marketplace!
Yes, NSO is well known but this is a global market for capabilities, and China is key player. Prior to this leak, little has been made public about the Chinese offensive cyber capability marketplace!
What can we do? 1) use these leaks against China’s diplomatic efforts. It’s bad form for them to be relying on companies like these and to hoard vulns/create “buggy banks” - (term stolen from @k8em0 she deserves all credit).
Also, follow the people! Plenty of actors in this leak are known entities - and when they close shop in one place they go to another. I mention this in my
Lawfare piece here: lawfaremedia.org/article/export…
Lawfare piece here: lawfaremedia.org/article/export…
Suing companies is also a great option. Yes, US courts may not have jurisdiction if they don’t have a branch here, but you might get it in the UK or elsewhere!
Anyway okay, I’ve been pulling too many all nighters this week to get this out, mostly to show to myself I’ve still got my China analysis chops while in law school. Time for a well deserved nap 👋
• • •
Missing some Tweet in this thread? You can try to
force a refresh