views
RE: APEX / ALGS / EAC Remote Code Execution
👋 I wrote undectable cheats for online games for challenge and sport for many, many years. I know enough to know that no one has the answers, but I'd like to call out some things you may have glazed over, and put them in context. 🧵
👋 I wrote undectable cheats for online games for challenge and sport for many, many years. I know enough to know that no one has the answers, but I'd like to call out some things you may have glazed over, and put them in context. 🧵
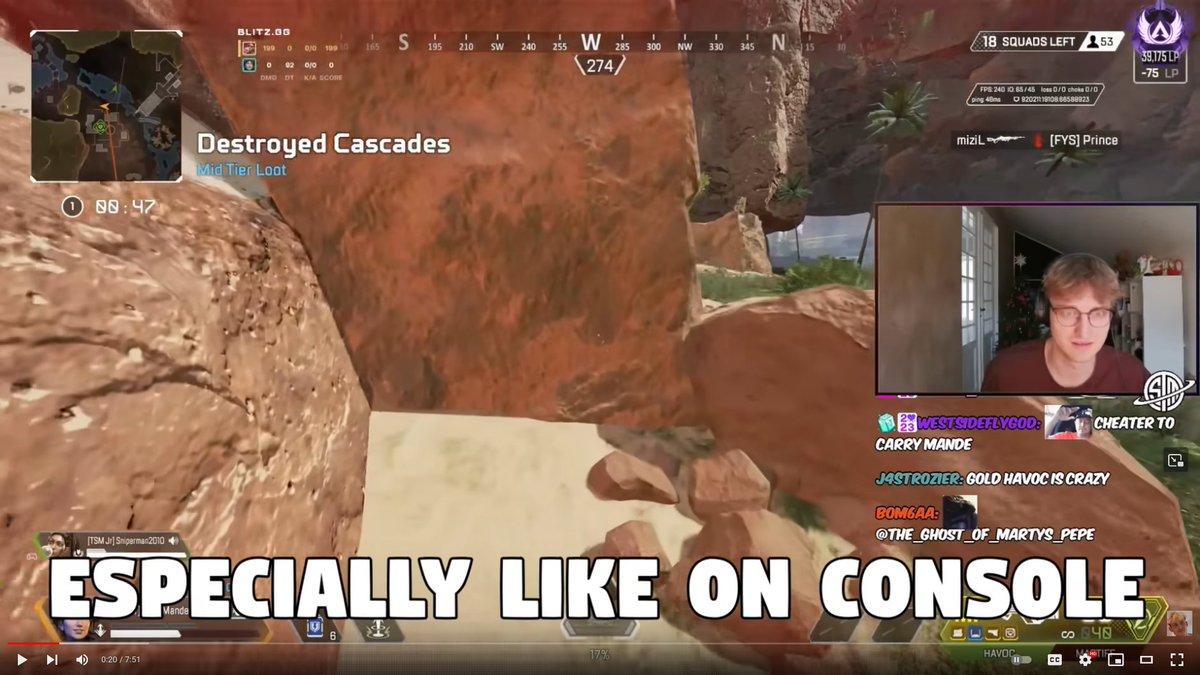
About a month ago, the suspected individual talked on stream about cheating and attempted to defer the accusation by saying "you can't cheat on console"
I am very familiar with this claim, and why it's important in context!
I am very familiar with this claim, and why it's important in context!
Online games that are cross-platform will often have heavy anti-cheat (in this case, EAC) on the desktop computer client, but little to none on consoles/mobile.
The absence of anti-cheat logs on a desktop may be a strong signal of a cheater, but not other platforms.
The absence of anti-cheat logs on a desktop may be a strong signal of a cheater, but not other platforms.
When implementing a cross-platform game, the client may change, but the network protocol will often remain the same.
A modified desktop client presenting as another platform, a console, allows you to operate outside of the purview of anti-cheat without being anomalous.
A modified desktop client presenting as another platform, a console, allows you to operate outside of the purview of anti-cheat without being anomalous.
This isn't to say they aren't using a modified console, but rather make clear that they don't need to. In fact, you don't even need to use a modified client at all!
Let's talk about protocol hacking!
Let's talk about protocol hacking!
Game clients and servers get regular updates and this often breaks cheats. Client modifications are easier, but toilsome to maintain. If you like challenges, you operate your cheat in the most stable and invisible way possible: on the network itself!
There's a long and very interesting history of protocol hacks on online games, I'll leave this here as a great example:
If you understand the game protocol, you can run the official game client with no modifications, and get updates, and pass anti-cheat.web.archive.org/web/2018021616…
If you understand the game protocol, you can run the official game client with no modifications, and get updates, and pass anti-cheat.web.archive.org/web/2018021616…
On-system anti-cheat can and will watch everything on the system. Between your game client and the game servers, there's many network devices, including your home router.
Anti-cheat cannot monitor your home router. That's *your* territory.
Anti-cheat cannot monitor your home router. That's *your* territory.
Modifying packets on-the-fly is fairly trivial if you know what you're doing, and you can largely operate with impunity unless other users report you. Neat!
The hard part is reverse engineering the protocol, but again, you've got the game client that speaks the protocol.
The hard part is reverse engineering the protocol, but again, you've got the game client that speaks the protocol.
Lots of cool things may be built in to game protocols, including but not limited to: acting as the server, pushing configurations to other users, and leveraging features that are useful for game QA (infinite health, etc...)
In the case of @Genburten we see a "cheat" dialog pop up, but take note of the font. Looks nearly identical to the font as used in the game itself, yeah?
Well, looking at the rest of the game screen, we can clearly see the game supports populating overlays via the game protocol.
Well, looking at the rest of the game screen, we can clearly see the game supports populating overlays via the game protocol.

@Genburten I'll wrap this up here. I see no indication of on-system RCE. I see no indication of EAC even being involved.
I do see something I've done many, many times: Speaking the game protocol to leverage builtin game configurations and tooling in such a way that is otherwise invisible.
I do see something I've done many, many times: Speaking the game protocol to leverage builtin game configurations and tooling in such a way that is otherwise invisible.
Anyways, blog post plug: remyhax.xyz/posts/golang-p…
• • •
Missing some Tweet in this thread? You can try to
force a refresh




