Over a decade in the making: Sandworm is now APT44.
Below is a thread with some major takeaways and insights from our new report:
cloud.google.com/blog/topics/th…
Below is a thread with some major takeaways and insights from our new report:
cloud.google.com/blog/topics/th…
Also known commonly as the GRU’s Main Centre for Special Technologies (GTsST) or Unit 74455 - APT44 has been at it for the better part of 15 years. Publicly available images of its anniversary insignia place the unit’s formation in 2009. 

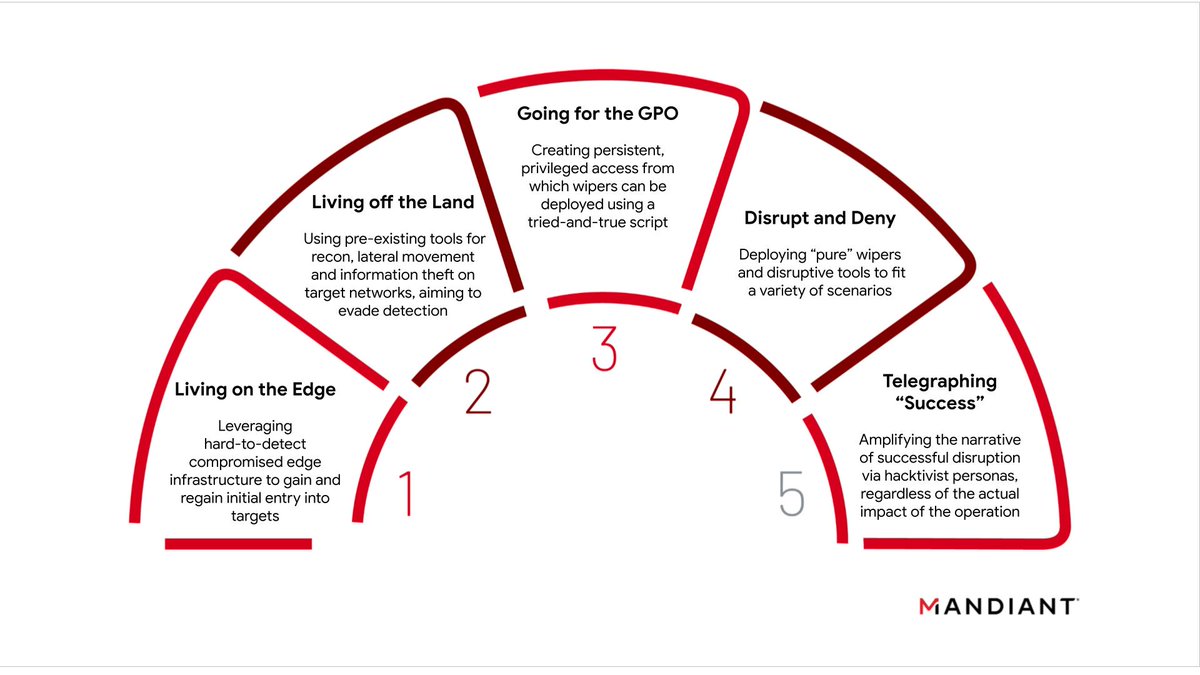
This tenure has involved a series of the most brazen cyber operations known to date - a series of firsts that have set precedents for future network attack activity and that continue to carry significant proliferation risk. 

But everyone knows the history here, so let's focus in on what we're seeing today:
With Russia's full-scale invasion in its third year, APT44 remains the preeminent threat to Ukraine. To date, no other Russian government-backed cyber group has played a more central role in shaping and supporting Russia’s military campaign.
APT44’s approach to supporting Russia’s war has evolved significantly over the two years. Specifically, we have seen the group's posture shift away from disruption as its primary focus toward espionage to provide battlefield advantage to Russia’s conventional forces.
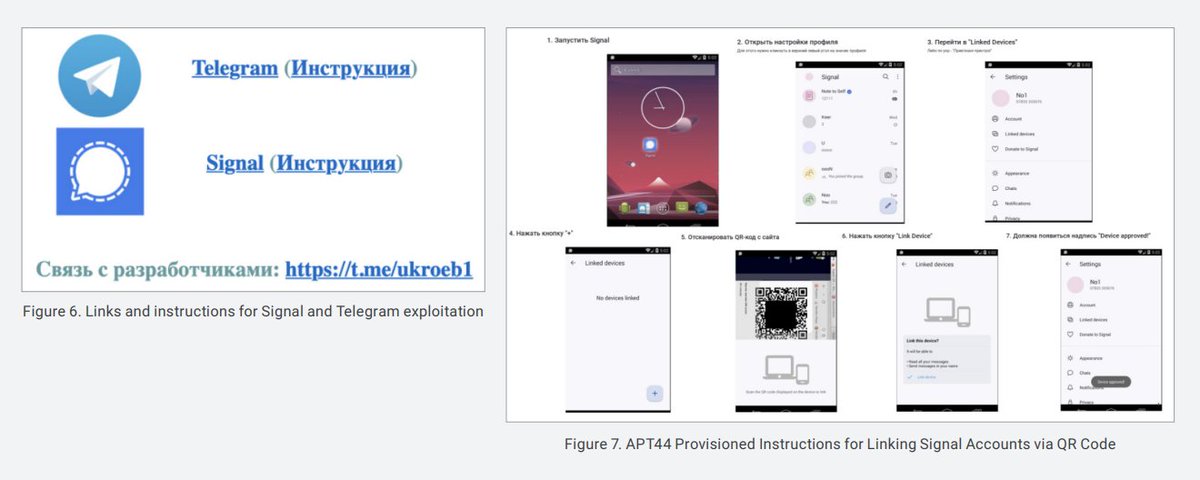
For example, one long-running APT44 campaign has assisted forward-deployed Russian ground forces to exfiltrate communications from captured mobile devices, ultimately to be fed into Russia’s reconnaissance-strike complex. They even provide troubleshooting support on Telegram! 
This pivot in focus has also resulted in a deeper focus on drones and their enabling systems and technologies (a pattern we see across multiple Russian intrusion sets). A glimpse of that activity from our TAG colleagues here:
blog.google/threat-analysi…
blog.google/threat-analysi…
This is not to say sabotage is off the table, but that APT44 is more calculated about its targets and the capabilities it uses. This is a highly adaptive adversary that is absorbing lessons on how cyber operations can best support a long war and has adjusted accordingly.
APT44 has also retained its interest in supply chain-enabled sabotage. In a recent case, access to a software developer resulted in downstream compromise of critical infrastructure networks in Eastern Europe and Central Asia, followed by selective deployment of wiper malware.
To emphasize: a lot has changed over the past two years. The APT44 of 2022 is not the APT44 of 2023, and it won’t be the APT44 of 2024 as Russia goes on the offensive. Each phase of the war has brought new adaptations and innovations. The learning curve is visible.
Zooming out: Beyond Ukraine, APT44 continues to operate globally. For example, APT44 is responsible for the recent targeting of @Bellingcat.
Others investigating Russia’s transgressions in Ukraine should be hyper aware of this threat.
Others investigating Russia’s transgressions in Ukraine should be hyper aware of this threat.
https://twitter.com/bellingcat/status/1738173672043450532
Given what we know about the group’s historical targeting patterns, and the number of significant events on the horizon, we expect APT44 to continue to be active outside of Ukraine in 2024. In particular…
2024 is a record year for elections globally, and APT44’s history of attempting to interfere in democratic processes means vigilance around this group is of utmost importance. APT44 is a multifaceted threat to elections / their underlying infrastructure.
cloud.google.com/blog/topics/th…
cloud.google.com/blog/topics/th…
There is also an upcoming Olympics Games in France, which has historically been a target of disruptive cyber operations. Russia still can’t compete under its national flag – a grievance that drove APT44’s targeting of the South Korea and Japan games.
gov.uk/government/new…
gov.uk/government/new…
And we can’t discount the unknown. APT44’s bias for action in service of the Kremlin’s whims means organizations around the world are at risk of falling into the group's sights on short notice.
Take for instance how significantly degraded Russia’s spy networks in Europe have become. With fewer options to lean on, the Kremlin may be forced to rely more heavily upon cyber units like APT44 for its “special activities” abroad.
washingtonpost.com/world/2023/02/…
washingtonpost.com/world/2023/02/…
APT44 is incredibly brazen, amidst the most intense campaign of cyber activity ever seen, in full-blown support of a war of territorial aggression. And the threat posed does not end at Kyiv’s borders.
As other storms (Typhoons) emerge, it's critical we keep an eye on this one.
As other storms (Typhoons) emerge, it's critical we keep an eye on this one.
• • •
Missing some Tweet in this thread? You can try to
force a refresh