im pirating Ableton Live suite 12
the .NFO has an interesting tidbit:
"does not modify any original binaries".
How does it work? lets find out. live reversing thread lets go
the .NFO has an interesting tidbit:
"does not modify any original binaries".
How does it work? lets find out. live reversing thread lets go
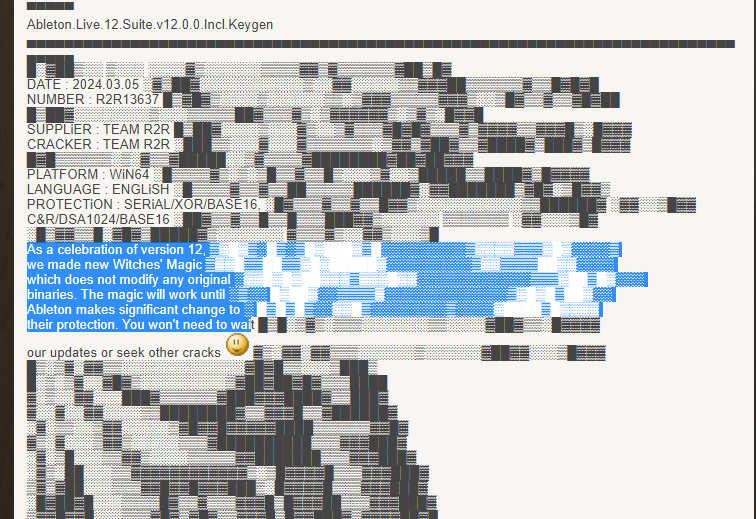
okay so extracting it we have the legit installer
all the files are signed by Ableton AG. also lmao overpriced code signing cert thats a pain in the ass to get


all the files are signed by Ableton AG. also lmao overpriced code signing cert thats a pain in the ass to get


the actual crack is cute
it's a keygen with a vcruntime dll
the keygen, we can run it in a VM later, so no need to reverse this for now. the msvcrt runtime dll is too small to be a real one. its probably just a shim
for reference here's also what size of real ones look like


it's a keygen with a vcruntime dll
the keygen, we can run it in a VM later, so no need to reverse this for now. the msvcrt runtime dll is too small to be a real one. its probably just a shim
for reference here's also what size of real ones look like


how does a dll shim work?
great tool for patching, cracking, game hacking etc.
you make a dll that pretends to be another dll thats referenced by the thing you're trying to patch
put the dll earlier in the search path so yours get loaded instead
great tool for patching, cracking, game hacking etc.
you make a dll that pretends to be another dll thats referenced by the thing you're trying to patch
put the dll earlier in the search path so yours get loaded instead

in your shim, provide all the same exports, but just delegate all the calls to the real dll's implementation (ie LoadLibraryA and GetProcAddress)
use the DllMain hooks to get code execution at load time. then use GetModuleHandleA to get pointers to various shit you wanna patch
use the DllMain hooks to get code execution at load time. then use GetModuleHandleA to get pointers to various shit you wanna patch
anyways enough background info. lets stop fucking around and actually look at the dll.
pretty standard pe header, not very fucked up (this is a good sign)
pretty standard pe header, not very fucked up (this is a good sign)

text section looks like normal x86_64 (starts with "H" = push. normal function epilogue. This is what we want to see!) code is low entropy from visual inspection 

...wait, that's it? that's a tiny text section. also a good sign. not much shit to reverse. so not a lot of places you can hide bad shit. 

ok lets look at the data section ig
rofl
i bet this is like a RSA public key or some shit.
theyre probably just patching the license signing key
rofl
i bet this is like a RSA public key or some shit.
theyre probably just patching the license signing key

okay its 376h long which is 886 bytes in decimal. but this is ascii hex so this is really 443 bytes encoded.
DSA1024 keys are 443 bytes long(thx stackoverflow)


DSA1024 keys are 443 bytes long(thx stackoverflow)


also lol if u read the NFO it tells u that this is in fact the protection used
1024 bit RSA is weak (~80 bits of security iirc), i feel like it may become factorable in this decade(?) with $$$ and some cloud compute?
1024 bit RSA is weak (~80 bits of security iirc), i feel like it may become factorable in this decade(?) with $$$ and some cloud compute?

!!!wowiee!! its the imports table. and it imports exactly all the shit a shim should import
GetsystemdirectoryW is probably for finding the real vcruntime140.dll
virtualprotect is probably for patching ableton. also i guess they're patching the main exe based on string earlier
GetsystemdirectoryW is probably for finding the real vcruntime140.dll
virtualprotect is probably for patching ableton. also i guess they're patching the main exe based on string earlier

ok lets acutally reverse the fucking thing in ida instead of fucking around in a hex editor
to make more obvious what is going on, here is the cff explorer of the real binary and the shim
its basically just going thru its own exports table and re-resolving the exports to the real functions


its basically just going thru its own exports table and re-resolving the exports to the real functions


i guess they chose this dll because it only has 3 exports so its easy and tiny. doesnt really matter tho u could shim whatever dll in theory
that look like ascii to me.
ok i guess they are parsing the pe header and finding where the rdata section starts? lol that is pretty gamer
ok i guess they are parsing the pe header and finding where the rdata section starts? lol that is pretty gamer

alright lets fuck around and add some structs
did u know l_efanew means logical file address for the New Executable header ? me neither.
its some shit like this, theres some incorrect shit like &ntHeader[1] because the struct doesnt include the section headers
did u know l_efanew means logical file address for the New Executable header ? me neither.
its some shit like this, theres some incorrect shit like &ntHeader[1] because the struct doesnt include the section headers

did u know ida pro has three types of comments
anterior posterior and inline?
insert, shift-insert, and / are the hotkeys
i dont give mac hotkeys because mac users arent real. mac users have a real ida license and thats just not real to me.
anterior posterior and inline?
insert, shift-insert, and / are the hotkeys
i dont give mac hotkeys because mac users arent real. mac users have a real ida license and thats just not real to me.

ok so it does the virtualprotect
did you know you can unfuck the flags in virtualprotect in ida using bitfield enums?? no one does this tho and that makes me sad.
did you know you can unfuck the flags in virtualprotect in ida using bitfield enums?? no one does this tho and that makes me sad.

btw the virtualprotect is to make the page writeable so u can patch the code. sorry i forgot to mention that. virtualprotect is windows mmap by the way for all u losers who learned C in college 👎👎👎👎
alright thats the whole thing. normally i wouldnt go so in detailed or rename all the shit. i figured i would do it here to show how something like this is done for educational purpose 

ok that about wraps it up im going to install ableton now bye
if you enjoyed this thread fun fact you can support me on of (there is a link to it in my youtube bio) 

Overall I give this crack a 9/10 rating
- NFO file explains what protections was bypassed
- Public key patch, only patching rdata. No code is written which makes it very easy to audit
- Sideloaded patcher in shim DLL makes it resilient to software updates
- Good NFO art
- NFO file explains what protections was bypassed
- Public key patch, only patching rdata. No code is written which makes it very easy to audit
- Sideloaded patcher in shim DLL makes it resilient to software updates
- Good NFO art
bonus points for only scanning .rdata and parsing the PE header. some truly above and beyond shit
SO!!!! is this dll safe?? probably! you cant be quite sure only looking at decompilation because sometimes there is bad shit like code execution hidden in exception handlers or imports or relocations or some bullshit.
if you liked this thread, I do live reverse engineering streams on youtube!
• • •
Missing some Tweet in this thread? You can try to
force a refresh






































