🧵In China, where the military-civilian divide is blurred, hacking contests and bug bounty programs help assess the strength and robustness of its offensive cyber ecosystem
This graph I've compiled shows my understanding based on my research (yellow) and other sources
Insights:
This graph I've compiled shows my understanding based on my research (yellow) and other sources
Insights:

Within China's cyber ecosystem, we can broadly divide hackers into two distinct groups. Group 1: prominent hacking teams/researchers who excel in top exploit hacking competitions (like Pwn2Own and the Tianfu Cup) and bug bounty programs. They mostly target Western products.
Group 2 consists of non-public, government-contracted hackers, such as those identified by i-SOON leaks, @intrusion_truth, and U.S. indictments. Unlike their competition-participating counterparts, they typically don't engage in prominent contests or bug bounty programs.
Contracted hackers directly carry out cyber operations, while elite hacking teams focus on vulnerability research and founding cybersecurity startups. This supports the contracted hackers' missions and sustains China's broader offensive cyber ecosystem in the long term.
Group 1/contest-winning hacking teams are often affiliated with Chinese companies that contribute the most 0-day vulnerabilities to China's premiere intelligence agency (MSS), as identified by @DakotaInDC and @kristindelrosso's Sleight of Hand report (image from their report). 

The hacking teams from the following companies particularly stood out for their performance at hacking contests and contributions to prominent bug bounty programs: Qihoo 360, Tencent, Chaitin Tech, Ant Group, Cyber Kunlun, Sangfor, OPPO, among others.
More specifically:
More specifically:
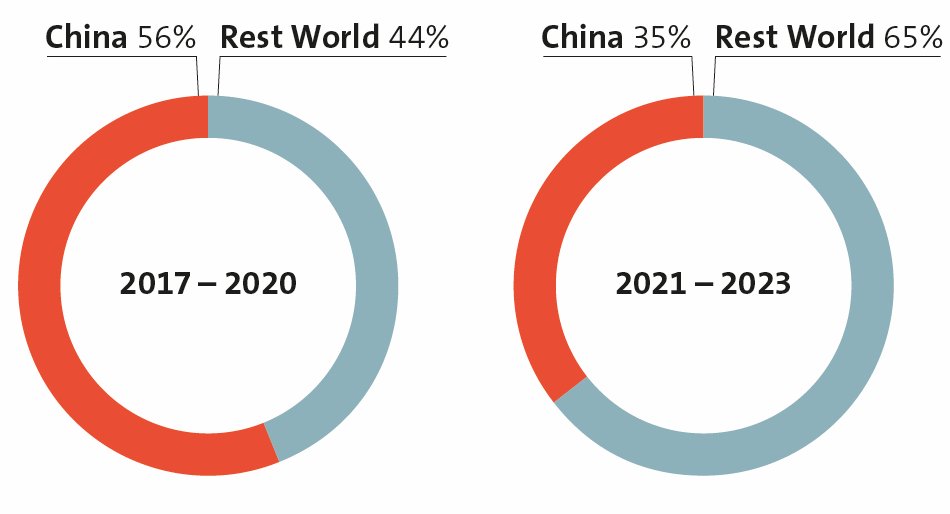
I analyzed Chinese winnings at the international hacking competition Pwn2Own (Vancouver, Canada), which surged from 13% of the entire prize pool in 2014 to 79% in 2017. Qihoo 360 and Tencent teams/labs dominated the competition. 

(The absence of Chinese hackers at Pwn2Own since 2018 has altered the contest’s landscape. In 2022 and 2023, no attempts were made to breach iPhone or Google Pixel devices, ending a 15-year streak of targeting Apple products.)
Unlike Pwn2Own, at the Tianfu Cup (Chengdu, China) almost all participants are from China-based teams/companies. Winning teams (2018-2023) include Qihoo 360, Tencent (initially), Cyber Kunlun, Sangfor, and Ant Group (in recent years).
Chinese hacking teams at these competitions target a wide range of products that offer interesting insights into which Chinese teams target which major Western products and systems, such as Apple, Google, and Microsoft. However...
To better understand their long-term research focus, I analyzed Chinese teams/labs' contributions to Apple, Google Android, and Microsoft's bug bounty programs. The volume of vulnerabilities submitted to the three programs combined looks as follows: 

Main contributing teams/labs: Ant Lightyear Lab (Ant Group), 360 Nirvan, 360 Vulcan (Qihoo 360), and Xuanwu Lab (Tencent) 

Main contributing teams/labs: 360 SRC, 360 Alpha, 360 IceSword, 360 C0RE (Qihoo 360), Alibaba Labs (Alibaba), Oppo Amber Labs (OPPO), Baidu Labs (Baidu). 

Main contributing teams/labs: 360 Vulcan, 360 IceSword, 360 C0RE (Qihoo 360), Xuanwu Lab, Keen Lab, Zhanlu Lab (Tencent), Kunlun Lab (Cyber Kunlun), Sangfor Lights Lab (Sangfor). 

Across all three platforms, the success of the Chinese teams is often credited to a small number of individuals. Fluctuations in a team’s contributions can often be traced back to a single individual transition between companies. This has been particularly true since 2020.
The number of research labs/teams vary across companies, in size, quantity, and research focus. Qihoo 360 boasts over 19 teams while Tencent operates 7/10 labs. In general, the higher the number of teams and labs, the larger the financial capital, HR, and areas of specialization.
What about Capture the Flag (CTF) competitions? I've looked at DEFCON CTF results and compiled the graph below (red: US teams, blue: Chinese, yellow: Taiwan). Chinese teams consistently reached the finals from 2013 to 2023, posing a significant challenge to U.S. dominance. 

Unlike at Pwn2Own and the Tianfu Cup, Chinese participants at DEFCON are mostly students. Their success prompted major tech companies (Tencent, Qihoo 360, etc.) to get involved, providing sponsorships, acquiring winning teams, organizing CTF events and recruiting members.
Some university deptments that host these teams have been (a) linked to Chinese state-sponsored cyber operations, (b) conducted vulnerability research with Chinese companies linked to state-sponsored cyber operations, (c) serve as recruitment centers for China security agencies.
Retired team members often either joined tech giants, such as Qihoo, Alibaba, Tencent, Huawei, or created their own cyber security startups. Some of the winning CTF teams have set up their own China-based hacking competitions. Or more of the above options combined, as shown below 

The 2023 WMCTF edition (bottom) was supported by i-SOON as the primary sponsor, the government-contracted firm whose extensive espionage activities were ex-posed in early 2024. 

More insights and detailed information available in the full report "From Vegas to Chengdu: Hacking Contests, Bug Bounties, and China’s Offensive Cyber Ecosystem" (page 11) here: css.ethz.ch/content/dam/et…
• • •
Missing some Tweet in this thread? You can try to
force a refresh