Since I'm 6 drinks in for 20 bucks, let me tell you all about the story of how the first Microsoft Office 2007 vulnerability was discovered, or how it wasn't.
This was a story I was gonna save for a book but fuck it, I ain't gonna write it anyways.
This was a story I was gonna save for a book but fuck it, I ain't gonna write it anyways.
So my first month at working at eEye in late 2006 good ol Microsoft announced Office 2007.
They said they added a shit ton of security including safe int, sandboxing, code analysis, and malformed doc detection.
I told my boss I was gonna break it.
So I started fuzzing by hand
They said they added a shit ton of security including safe int, sandboxing, code analysis, and malformed doc detection.
I told my boss I was gonna break it.
So I started fuzzing by hand
I'm the kind of sicko who can open a Microsoft office document in a hex editor and start telling you what it is all about just by scrolling down.
I have spent an embarrassing amount of time looking at BIFF format in a hex editor, trust me it's nothing special
I have spent an embarrassing amount of time looking at BIFF format in a hex editor, trust me it's nothing special
So I start manually fuzzing legacy word documents, I literally bring up office 6.0 documents and start manually fuzzing the legacy controls in them the day office 2007 drops.
After about 36 hours I get a promising crash in good ol Word . Exe
After about 36 hours I get a promising crash in good ol Word . Exe
So I start digging in and it is from a legacy conversation function converting an ancient word art structure into a modern structure and it incorrectly trusts a user calculation to control a pointer
Game over
Game over
Sorry I keep getting served drinks because I dropped a 50 dollars
This is literally dumb amount of drinks
This is literally dumb amount of drinks
Game over - or so I thought
So at eEye we have a senior review every bug we report and my boss looks over this issue and gives it the green light.
I take it to @marcmaiffret and he sends it right over to Microsoft and starts a press release as one does
So at eEye we have a senior review every bug we report and my boss looks over this issue and gives it the green light.
I take it to @marcmaiffret and he sends it right over to Microsoft and starts a press release as one does
So MSRC starts reviewing this cluster fuck and as your can imagine since it's a brand new product they call in their A Team to review it, including none other than David LeBlanc, the Creator of Safe Int and a huge component of the safety of office 2007
(I'm sorry David for this)
(I'm sorry David for this)
Anyways David and his team look over our crash
Meanwhile we are pumping press releases left and right because we got an 0day in office 2007 in 2 days after release
We are high fiving each other in the office, literally strutting around like Rockstars
Meanwhile we are pumping press releases left and right because we got an 0day in office 2007 in 2 days after release
We are high fiving each other in the office, literally strutting around like Rockstars
Except Le Blanc comes back & says
"So. About that crash.. It's only exploitable when a debugger is attached."
...
So we look it over.. there's a fucking 0xCC op code there that we blew past in our code path.
We tested and replicated with a full exploit only with a debugger
"So. About that crash.. It's only exploitable when a debugger is attached."
...
So we look it over.. there's a fucking 0xCC op code there that we blew past in our code path.
We tested and replicated with a full exploit only with a debugger
Anyways so review the bug and holy shit he's right
We submitted an exploitable condition only under a debugged process and we literally contacted every press release
Every single one
There's like 8 major news articles saying we have an exploit in office 2007 in under 48 hours
We submitted an exploitable condition only under a debugged process and we literally contacted every press release
Every single one
There's like 8 major news articles saying we have an exploit in office 2007 in under 48 hours
So Marc calls us in our office and sits on us down and tells us the news
I have literally been on the team for less than 2 months
I feel fucking awful
I feel fucking dumb AF
I have let down this incredible team
I am utterly devastated
I have literally been on the team for less than 2 months
I feel fucking awful
I feel fucking dumb AF
I have let down this incredible team
I am utterly devastated
Marc says well, I am not retracting the press release, so you all better give me an 0day
We will tell MSRC we sent the wrong file, in the meantime find me an 0day
We will tell MSRC we sent the wrong file, in the meantime find me an 0day
So me, feeling awful I start manually fuzzing again, by myself terrified for my life. I have to find an 0day ASAP to save face. Like yesterday. I'm over my head but I go
And then to my dismay the entire research team comes over and goes "we are in this together. Let's do this"
And then to my dismay the entire research team comes over and goes "we are in this together. Let's do this"
And I don't mean just like let's research this and get a bug
We are all in the office for days, 24 hours, ordering pizza, ordering mountain dew, reversing, making fuzzers, we are all in this together.
Every single researcher
We are all in the office for days, 24 hours, ordering pizza, ordering mountain dew, reversing, making fuzzers, we are all in this together.
Every single researcher
We made 4 different fuzzers, an analysis tool kit, and a binary decompiler of the BIFF format
Drew Copley (RIP) makes an HTML fuzzer for Web objects
Yuki Ukai and Derek Soeder start reversing every crash we come up with.
Me and Andre are fuzzing like no one has ever fuzzed
Drew Copley (RIP) makes an HTML fuzzer for Web objects
Yuki Ukai and Derek Soeder start reversing every crash we come up with.
Me and Andre are fuzzing like no one has ever fuzzed
3 days go by, we all haven't left the office
Girl friends and wives have called and yelled, pleaded and begged for each of us to come home
Every single member of the team stays
I feel guilty AF and keep at it
Girl friends and wives have called and yelled, pleaded and begged for each of us to come home
Every single member of the team stays
I feel guilty AF and keep at it
Day 4, I'm in a state of delirium
The office smells of dirty researcher but we all have found so many close AF vulns but nothing serious
I write a new fuzzer
There's a stack of pizzas ordered to the office that comes up to my chest
The office smells of dirty researcher but we all have found so many close AF vulns but nothing serious
I write a new fuzzer
There's a stack of pizzas ordered to the office that comes up to my chest
Im in a half passed out state, filled with delirium, pizza half in my hand barely conscious when I hear a fuzzer really hit
I spill a mountain dew code red while I come back into consciousness
I spill a mountain dew code red while I come back into consciousness
The crash has a a full EIP overwrite
0x4141414141
Yuji looks over and goes "oh shit"
Derek awakens and runs over and he's like ... Oh really?!!!
And my boss Andre is like
Remove the Debugger and run it again
0x4141414141
Yuji looks over and goes "oh shit"
Derek awakens and runs over and he's like ... Oh really?!!!
And my boss Andre is like
Remove the Debugger and run it again
I'm 14 drinks in everyone
The bartender has given me the eye as in "sir what are you doing standing"
So I'm doing what every drunk AF person would do
Switching to Scotch
The bartender has given me the eye as in "sir what are you doing standing"
So I'm doing what every drunk AF person would do
Switching to Scotch
Update: I just got an 18 year old scotch for $15 dollars.... This is so dumb
So yuji and Derek start reversing this crash.
It's in publisher.
Fucking publisher, the web site developing tool in office that no one uses.
What the actual fuck.
We don't care we are all exhausted at this point, we just want something, literally anything.
It's in publisher.
Fucking publisher, the web site developing tool in office that no one uses.
What the actual fuck.
We don't care we are all exhausted at this point, we just want something, literally anything.
Derek and Yuki start reversing the shit out of this bug. They are literally going so hard core, reconstructing structures and white boarding this and the adjacent functions.
This is before office had symbols and these 2 bad asses to are literally making symbols on the fly
This is before office had symbols and these 2 bad asses to are literally making symbols on the fly
God fuck I'm so fucking drunk
So these 2 bad asses are literally IDAing this shit out of their heads
And I remember and they look at me and go "Greg! This crash is good, is a pointer overwrite because of an integer overflow"
We retest without a debugger... Hell we retest on a fresh os install
And I remember and they look at me and go "Greg! This crash is good, is a pointer overwrite because of an integer overflow"
We retest without a debugger... Hell we retest on a fresh os install
It
Fucking
Crashes
At
The
Same
Spot
0x4141414141
Fucking
Crashes
At
The
Same
Spot
0x4141414141
The entire research office explodes
We fucking did it
News articles have been asking us for updates
Microsoft has been asking us for further clarification
We have found a legit vulnerability and it bypasses safe int
We fucking did it
News articles have been asking us for updates
Microsoft has been asking us for further clarification
We have found a legit vulnerability and it bypasses safe int
So we are crying, screaming, throwing up, shitting, rolling on the floor, options eruptions, parties
The entire research team is screaming
I am literally crying because this is my first professional job and I had fucked up so bad, but every single researcher there stayed
The entire research team is screaming
I am literally crying because this is my first professional job and I had fucked up so bad, but every single researcher there stayed
Derek, Daniel, drew, Andre, Yuki, Marc, Matt, Permeh, Chris, Laurentiu
Guys I love you so much
Not a month goes by where I don't think about how much of bad asses each an every one of you are
Guys I love you so much
Not a month goes by where I don't think about how much of bad asses each an every one of you are
I just got handed a mojito??????????????!!!??????
Fuck it I'm drinking it
Fuck it I'm drinking it
Anyways
So crying shitting partying researchers at eEye
We write a report and slam that right over to MSRC, high fiving and partying with pizza we all finally go home for the first time in days
So crying shitting partying researchers at eEye
We write a report and slam that right over to MSRC, high fiving and partying with pizza we all finally go home for the first time in days
Wait I'm so drunk I fucked up this thread
Fuck I'm trashed
Anyways we wrap that bug and slam that at MSRC
Anyways we wrap that bug and slam that at MSRC
mSRC replies and they are like "oh this looks like it might be something"
Meanwhile, David LeBlanc is on horseback 100 miles out of Seattle on vacation enjoying his time off according to his blog
But the bug is in SafeInt, his baby
Meanwhile, David LeBlanc is on horseback 100 miles out of Seattle on vacation enjoying his time off according to his blog
But the bug is in SafeInt, his baby
So guess fucking what
Microsoft recalls his vacation
David LeBlanc literally blogs about his vacation being cut
This man was enjoying touching grass out in the world
And we fucking broke something so bad they recalled him vacation
On horseback
In the wilderness
Microsoft recalls his vacation
David LeBlanc literally blogs about his vacation being cut
This man was enjoying touching grass out in the world
And we fucking broke something so bad they recalled him vacation
On horseback
In the wilderness
David, man, I'm really sorry.
I've been wanting to tell you I'm sorry for like nearly 20 years about this
I
Am
So
Fucking
Sorry
To
Have
You
Come
Back
On
Vacation
I've been wanting to tell you I'm sorry for like nearly 20 years about this
I
Am
So
Fucking
Sorry
To
Have
You
Come
Back
On
Vacation
So we get a receipt from Microsoft.
They called back LeBlanc, Marc is tossing even more news interviews
Meanwhile Derek Soeder has written a full sexy RCE with kernel privilege exploit that he combined with his CSRSS Windows 7 LPE in a chain with us.
He even added C2 via ICMP
They called back LeBlanc, Marc is tossing even more news interviews
Meanwhile Derek Soeder has written a full sexy RCE with kernel privilege exploit that he combined with his CSRSS Windows 7 LPE in a chain with us.
He even added C2 via ICMP
So what does eEye do now?
We blast the press, we show off full demos, we write a core exploit module, we write a custom office to kennel c2 exploit chain (rare AF in 2007)
We own this exploit, we work it
We make that fur coat fucking pur
We blast the press, we show off full demos, we write a core exploit module, we write a custom office to kennel c2 exploit chain (rare AF in 2007)
We own this exploit, we work it
We make that fur coat fucking pur
Guys I just got handed another drink??? Wtaf I won't even know what it is
Ok crushed that mojito so I ordered another cuz why the fuck not
So MSRC responds with an email
Marc gathers all of us around to open it together
We, delirious, gather around open the email
.......
Marc gathers all of us around to open it together
We, delirious, gather around open the email
.......
Fucking confirmed the vulnerability
SafeInt wasn't applied to the structure we found
Get
Fucked
SafeInt wasn't applied to the structure we found
Get
Fucked
We did it
We found a legit zero day in a major product, office 2007, within the first week of release
Everyone is relieved
Everyone hugs
Everyone goes home finally
We found a legit zero day in a major product, office 2007, within the first week of release
Everyone is relieved
Everyone hugs
Everyone goes home finally
So after MSRC confirms, we write up the blog post, we write up the advisory, we get a CVE, we write a sexy write up
Here it is in jpeg form




Here it is in jpeg form

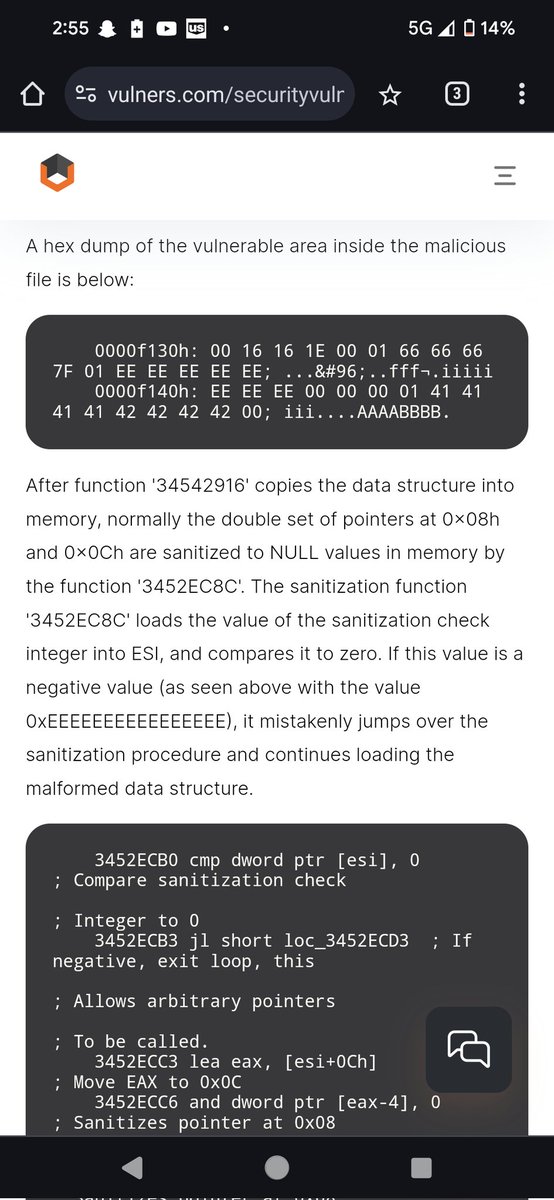


It gets patched in MS07-037 and assigned CVE-2007-1754
But that's not all....
Since we are eEye we always have greetz in our advisory, just like the old school VX authors in their zines
But that's not all....
Since we are eEye we always have greetz in our advisory, just like the old school VX authors in their zines
So what do I as the founder add into the greetz????
100 miles rides is absolutely David LeBlanc. 💀💀💀💀💀💀💀💀💀
100 miles rides is absolutely David LeBlanc. 💀💀💀💀💀💀💀💀💀
David. LeBlanc
I will happily buy you a drink any time, any where
I have felt guilty about this for nearly 20 years.
I am so so so so so sorry
I will happily buy you a drink any time, any where
I have felt guilty about this for nearly 20 years.
I am so so so so so sorry
David sent us an email intricately detailing how bad ass safeint was and how it protects against integer overflows and how insanely cool it is
He's right
It's is
But we found the section of code it somehow didn't get applied too
He's right
It's is
But we found the section of code it somehow didn't get applied too
And that's all it took
Office 2007 wrecked, destroyed, defeated
You can probably find some live demo of Derek Soeders ICMP C2 root kit that he demoed live on some news using this
Office 2007 wrecked, destroyed, defeated
You can probably find some live demo of Derek Soeders ICMP C2 root kit that he demoed live on some news using this
In the end the full write up goes here
It's my first big exploit at eEye
I honestly have the entire research crew to thank for the fuck up turned success.vulners.com/securityvulns/…
It's my first big exploit at eEye
I honestly have the entire research crew to thank for the fuck up turned success.vulners.com/securityvulns/…
And I just wanna say 2 things about this thread
Fucking up is hard, it sucks, we all do it, it's what you do immediately after is what matters. Roll with the punches, get up, fight back. You got this. It is ok to fuck up, we all do it. We don't talk about it. But we do it
Fucking up is hard, it sucks, we all do it, it's what you do immediately after is what matters. Roll with the punches, get up, fight back. You got this. It is ok to fuck up, we all do it. We don't talk about it. But we do it
And the second thing:
Your team makes a difference.
I was lucky enough to be one of the last researchers hired at eEye
It was a legendary period.
I was the dumbest person in the room and they rallied every time as a team
Your team makes a difference.
I was lucky enough to be one of the last researchers hired at eEye
It was a legendary period.
I was the dumbest person in the room and they rallied every time as a team
I have never been on a team like this except currently at @HuntressLabs
This team stands by and has every single aspect the same as back in 2007 eEye
Having a team that has your back like this makes a world of a difference
This team stands by and has every single aspect the same as back in 2007 eEye
Having a team that has your back like this makes a world of a difference
@HuntressLabs Being on the shoulder of giants makes me truly appreciate the 20+ years I have been in this industry.
Thank you for reading thru this drunk thread
This industry is crazy, and the fails we have aren't talked about
Please help normalize fucking up but owning it
Thank you for reading thru this drunk thread
This industry is crazy, and the fails we have aren't talked about
Please help normalize fucking up but owning it
I just wanna end this thread with one last thing
I love this community
I am not perfect, no one is
I have fucked up so times in my career
We all do and it happens
What matters is how we get back up, do it all over again, and help others learn from our mistakes.
Love you all
I love this community
I am not perfect, no one is
I have fucked up so times in my career
We all do and it happens
What matters is how we get back up, do it all over again, and help others learn from our mistakes.
Love you all
• • •
Missing some Tweet in this thread? You can try to
force a refresh












