NEW: @TheJusticeDept just disrupted a Russian-run AI-enabled Twitter disinformation bot farm.
Almost 1000 accounts on @X.
Masqueraded as Americans & promoted Russian government narratives.
Fascinating sleuthing behind this 1/
justice.gov/opa/pr/justice…




Almost 1000 accounts on @X.
Masqueraded as Americans & promoted Russian government narratives.
Fascinating sleuthing behind this 1/
justice.gov/opa/pr/justice…




2/ The investigation behind this Russian political interference takedown is interesting.
First, the @FBI got account registration info for a slice of fake accounts on @X
They found a lot of email accounts registered on the same server.
So they went to the registrar...


First, the @FBI got account registration info for a slice of fake accounts on @X
They found a lot of email accounts registered on the same server.
So they went to the registrar...


@FBI @X 3/ While the domain registrar (Namecheap) had a bunch of account registration information for the @FBI, the info was a fake name and some alias information.
Strike out? No. The FBI began a subpoena cascade, starting with the Google account used to register the domain.
Strike out? No. The FBI began a subpoena cascade, starting with the Google account used to register the domain.
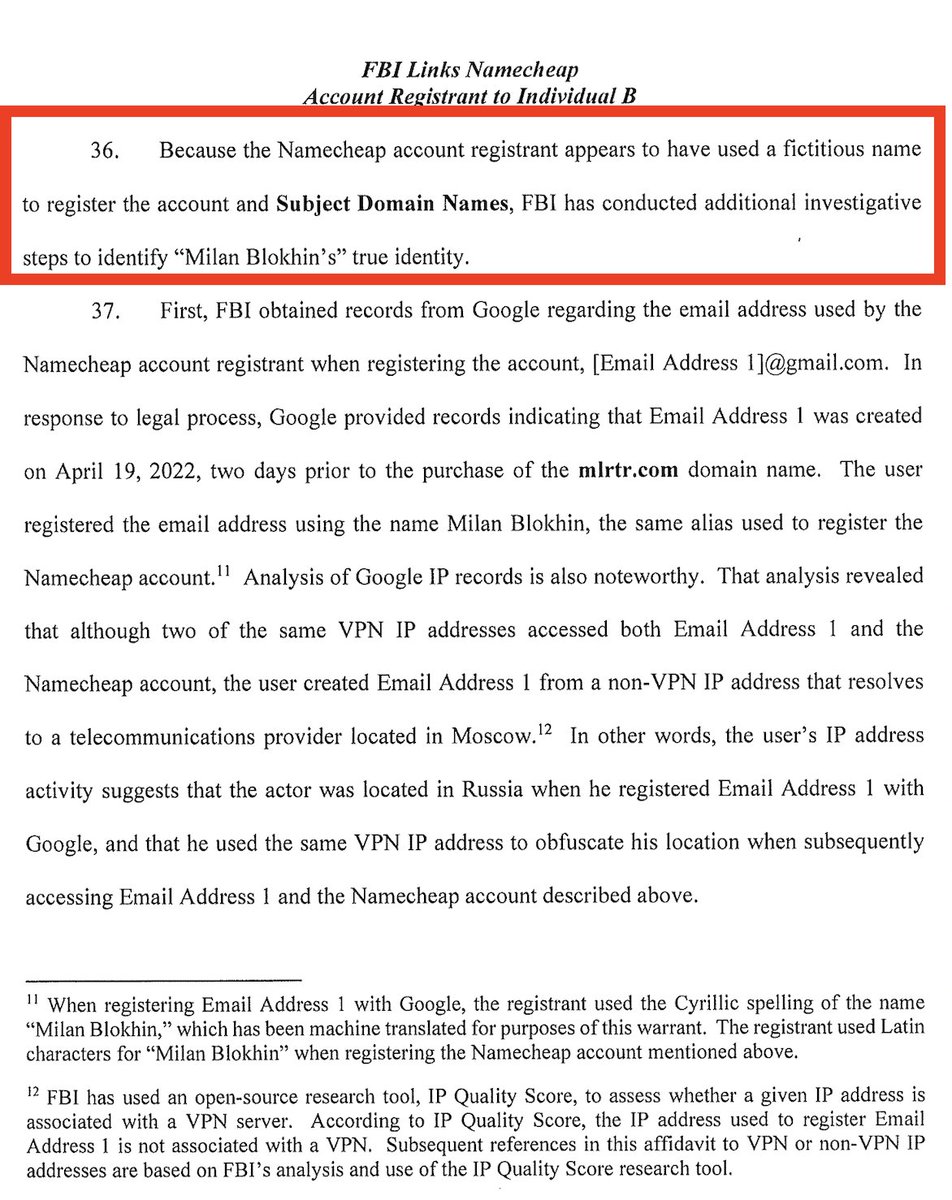
@FBI @X 4/ @FBI had a tasty find from first gmail subpoena: Moscow IP address.
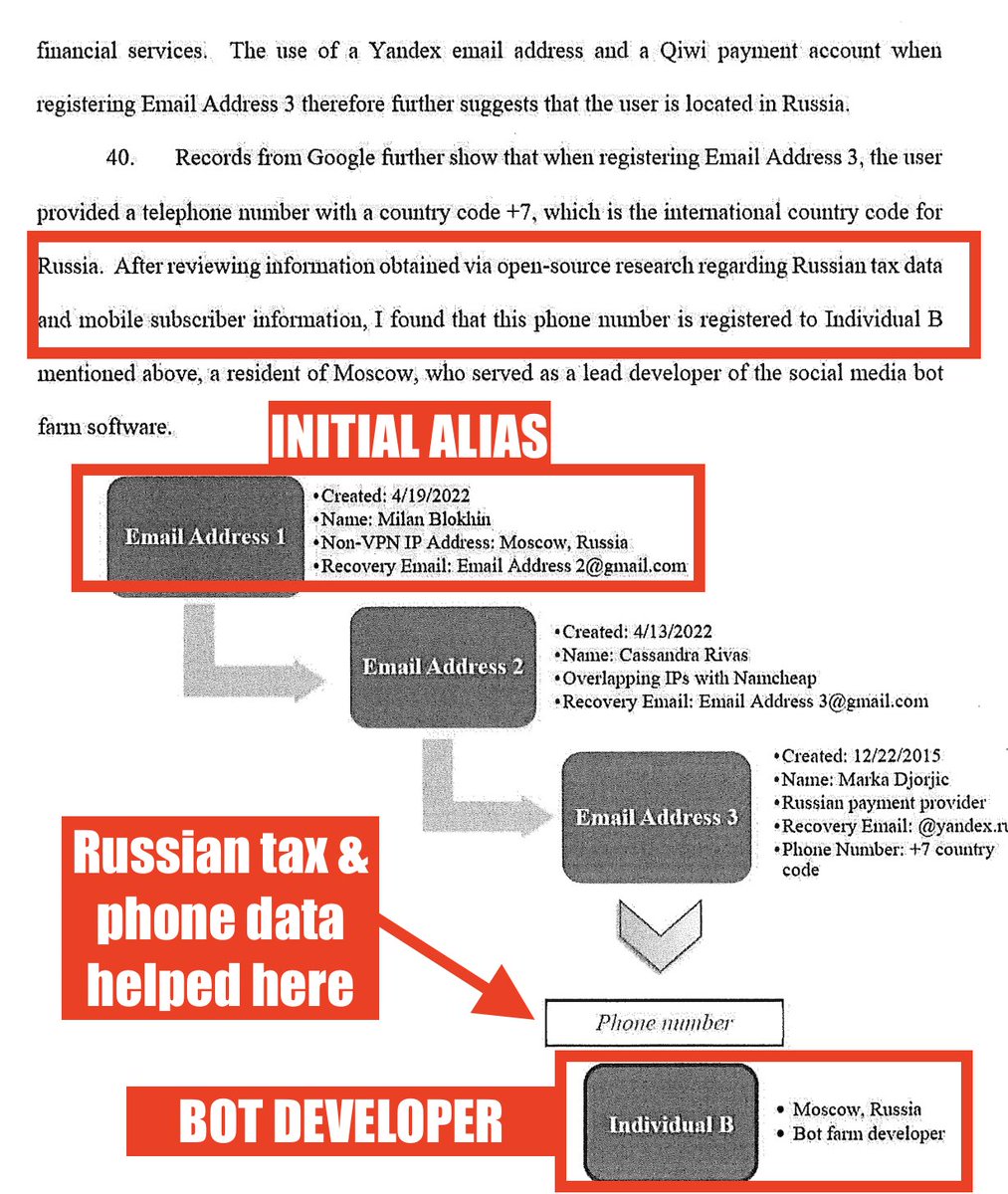
That was just the beginning: ubpoena cascade led through 2 more emails to a phone number.
Which they say they found in widely-leaked Russian tax & mobile subscriber information.
And got the operator.
That was just the beginning: ubpoena cascade led through 2 more emails to a phone number.
Which they say they found in widely-leaked Russian tax & mobile subscriber information.
And got the operator.
@FBI @X 5/ Simultaneously, a jointly issued* a technical advisory provided detail on identifying Russian AI-generated personas.
Likely reflects their conclusion that the Russians won't stop.
*🇺🇸@FBI @CNMF_CyberAlert 🇨🇦@cybercentre_ca 🇳🇱@AIVD @Defensie @Politie
ic3.gov/Media/News/202…




Likely reflects their conclusion that the Russians won't stop.
*🇺🇸@FBI @CNMF_CyberAlert 🇨🇦@cybercentre_ca 🇳🇱@AIVD @Defensie @Politie
ic3.gov/Media/News/202…




6/ The Russian Bot takedown, some notes:
☑️ Foreign efforts to shape Americans' perceptions via bots continue on @X despite Musk claims.
☑️AI is now a key disinformation op. tool.
☑️ Total # of accounts is small vs. @X universe, BUT doesn't rule out outside impact when well targeted.
☑️ Foreign efforts to shape Americans' perceptions via bots continue on @X despite Musk claims.
☑️AI is now a key disinformation op. tool.
☑️ Total # of accounts is small vs. @X universe, BUT doesn't rule out outside impact when well targeted.
7/ Cont'd:
☑️Takedowns & accompanying advisory suggest that US & allies are trying various techniques like these disruptions and seizures... because the operators are currently beyond their direct reach.
Expect the operators to learn, evolve & come right back targeting the US.
☑️Takedowns & accompanying advisory suggest that US & allies are trying various techniques like these disruptions and seizures... because the operators are currently beyond their direct reach.
Expect the operators to learn, evolve & come right back targeting the US.
8/ Russia is one of many countries now swamping @X with AI-driven bots to shape perceptions.
Even smaller countries operations flourish & aren't taken down after being identified.
Want proof? Check the accounts in this campaign for yourself.👇
Even smaller countries operations flourish & aren't taken down after being identified.
Want proof? Check the accounts in this campaign for yourself.👇
https://x.com/jsrailton/status/1804547853643317529
9/ Oh, and in case you missed it, Russia Today @RT_com involvement is alleged all over this bot farm, from origins to cover stories.
Source: justice.gov/d9/2024-07/aff…



Source: justice.gov/d9/2024-07/aff…



10. The "another US government agency" is an interesting element to the affidavit. So is framing of credibility & reliability.
Speculating wildly that it isn't @USFWS
Further speculating: this suggests a high level effort to break silos & get key information out quickly.
Speculating wildly that it isn't @USFWS
Further speculating: this suggests a high level effort to break silos & get key information out quickly.

• • •
Missing some Tweet in this thread? You can try to
force a refresh



























