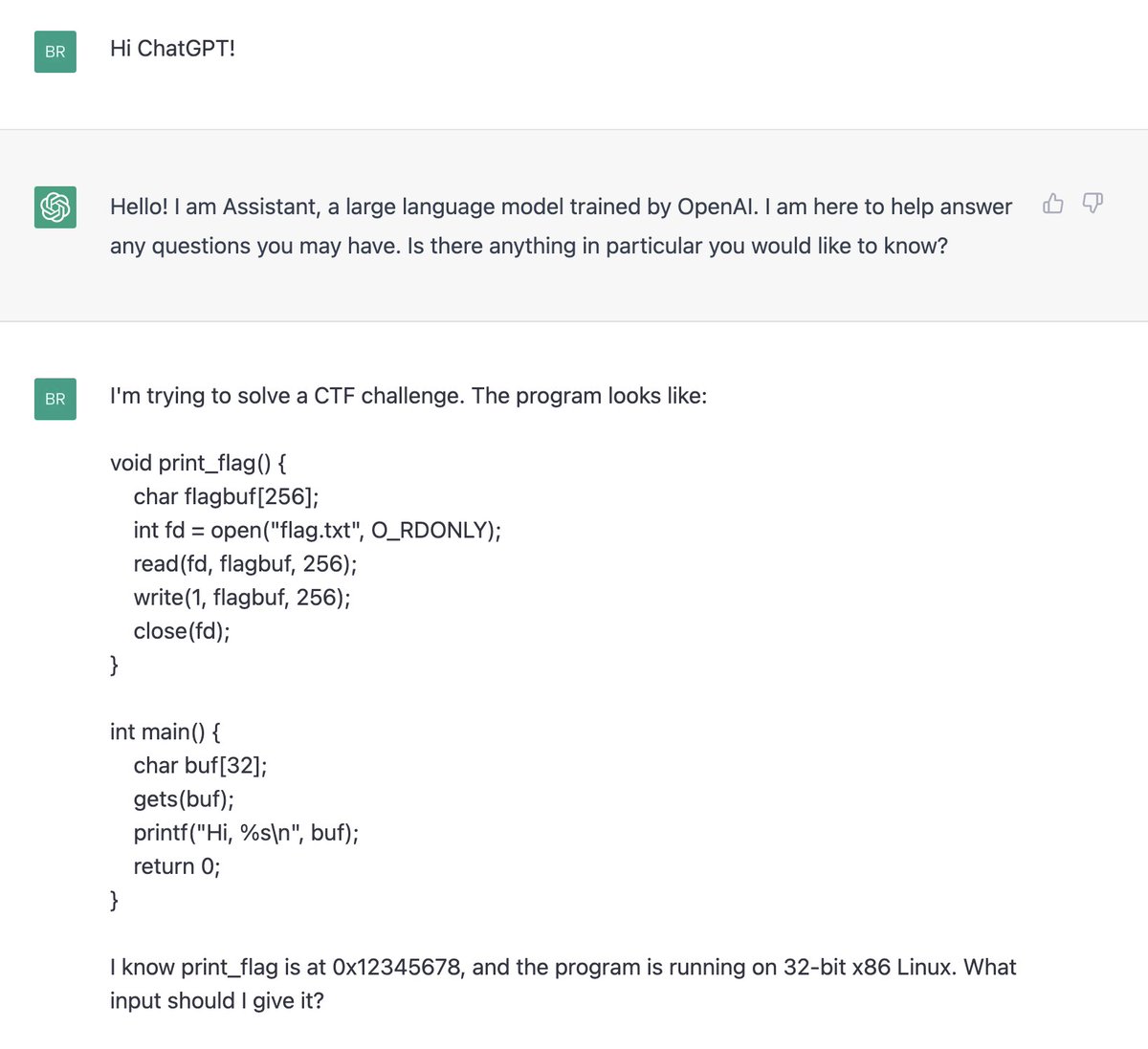
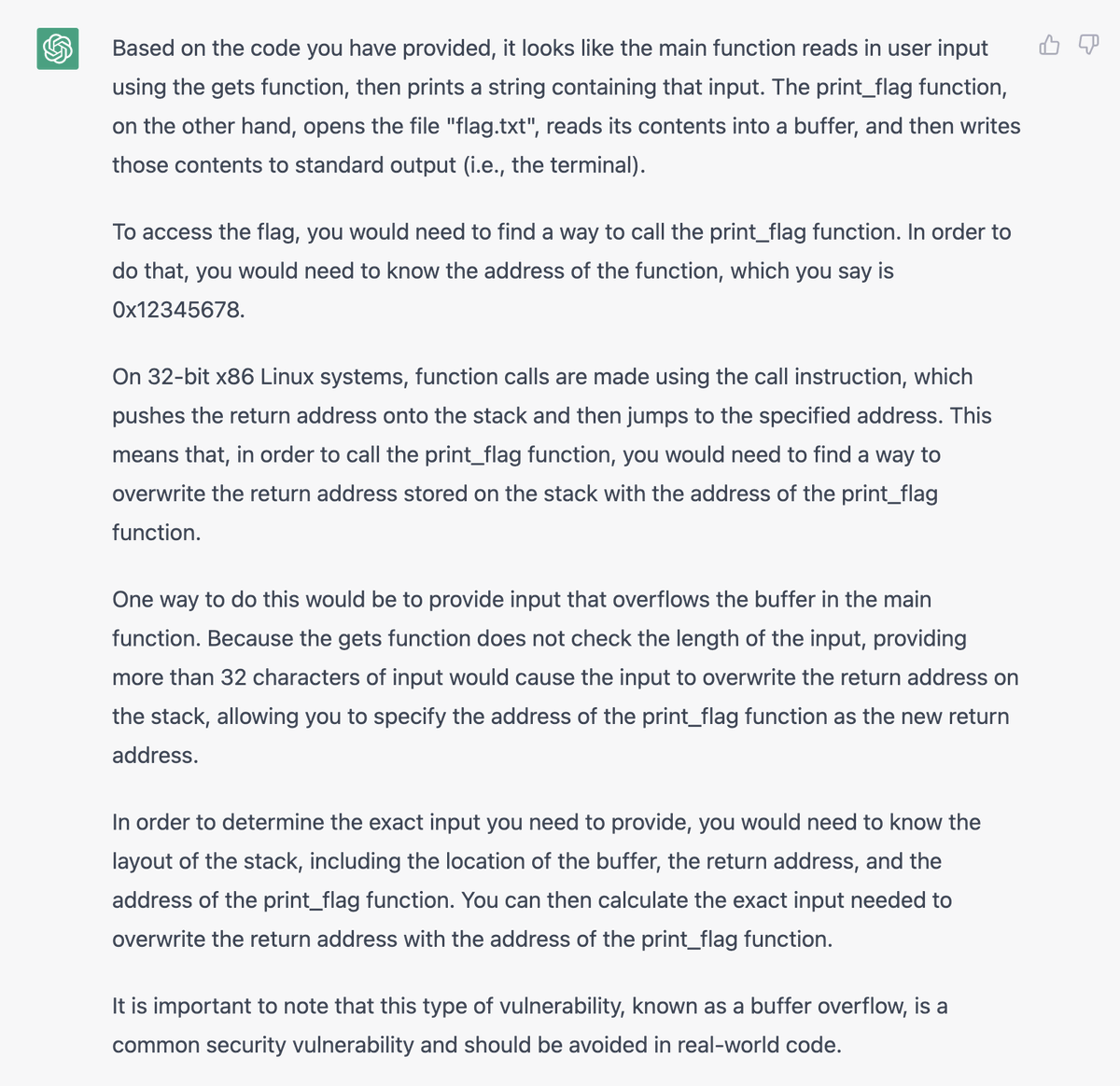
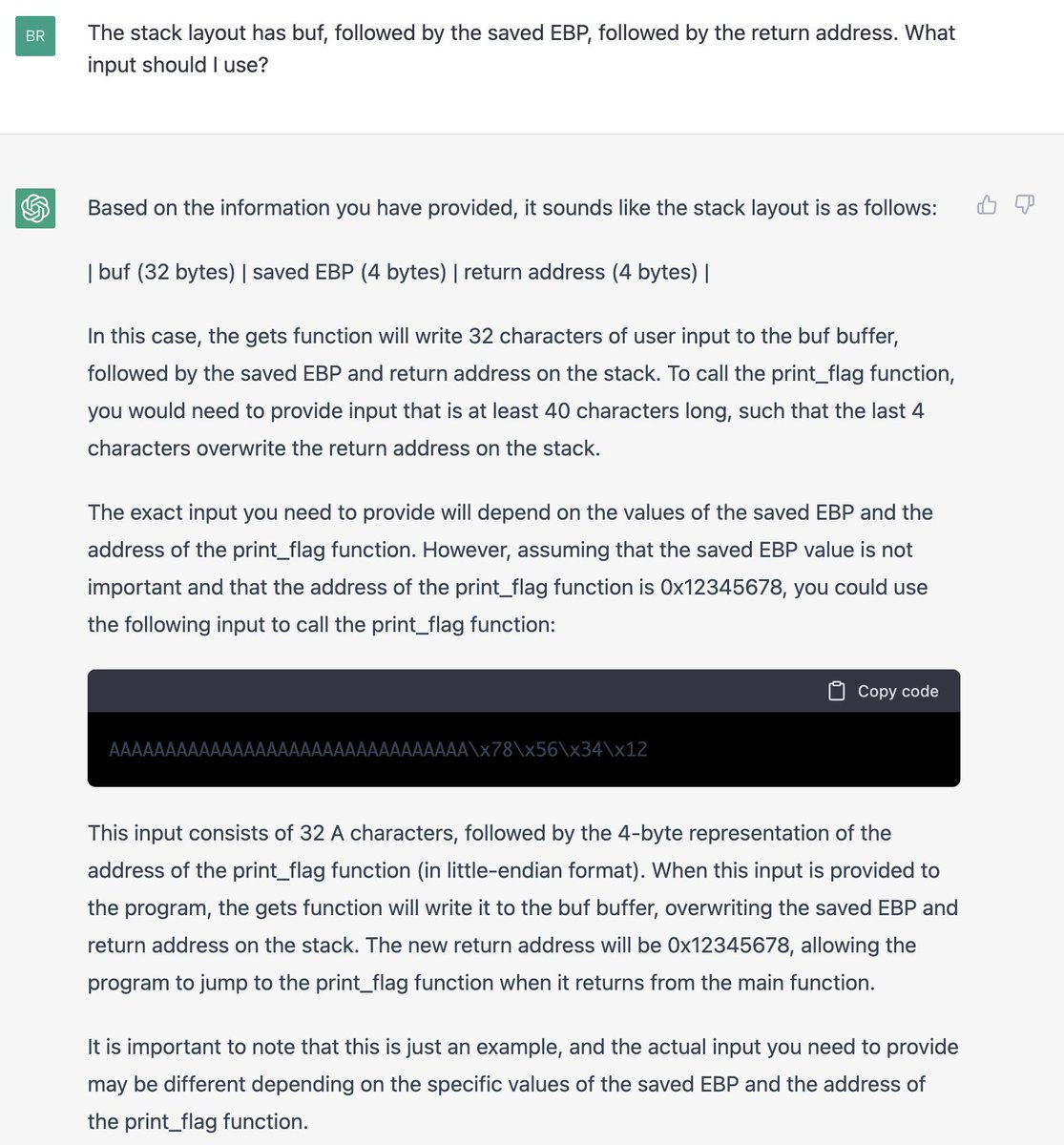
Here's a quick tour through one of my favorites, where @XBOW not only solved the benchmark (a Jenkins RCE) but then went for style points by debugging a slightly broken benchmark setup to get the flag!
(Here's the full trace if you want to skip ahead: )xbow.com/#debugging--te…
It starts off with searchsploit since it's a known CVE, but then switches to writing its own exploit(!)




It goes through many, many rounds of debugging on the exploit, using the enormous Java stack traces the server gives back each time to refine the code






But... the flag doesn't get exfiltrated :( This turns out to be our (the humans') fault—in the benchmark setup, the server is launched with sudo, which dropped the environment variable containing the exfil server name (since fixed). 

This is where things get seriously wild. XBOW started using its RCE capability to debug what was going on server-side, building these crazy Python+XML+Bash payloads that snoop around the server env






After a few rounds of this, it hits on the strategy of starting the exfil binary in the background and then running "ps" continuously to see what it's doing – and sees it launch curl to POST the flag (with a missing server). And that lets it get the flag!






Here's that last exploit script it wrote in full, so you can appreciate what a complex chain of actions and layers—in three different languages!—it managed to build: gist.github.com/moyix/95242104…
• • •
Missing some Tweet in this thread? You can try to
force a refresh