1/ The exploiter of the @WazirXIndia Multisig was able to drain it after changing the implementation of the Multisig, that couldn't have been done without compromising the signers EOA, but here's a closer look on the attack flow 🧵
2/ after the following tx of the Safe the attacker starts to drain, let's analyze the Msig tx params
* to - the to address is the address we want to call
* data - the data including the selector of the "to" we are calling
* operation - That's a very important one - Safe supports an Operation Enum which can be either 0 - Call or 1 - Delegatecall etherscan.io/tx/0x48164d3ad…
github.com/safe-global/sa…
* to - the to address is the address we want to call
* data - the data including the selector of the "to" we are calling
* operation - That's a very important one - Safe supports an Operation Enum which can be either 0 - Call or 1 - Delegatecall etherscan.io/tx/0x48164d3ad…
github.com/safe-global/sa…

3/ so in the attack tx the Attacker executes a delegate call from the msig (they were able to do it by compromising the signers keys) to a proprietary contract that was deployed 8 days ago etherscan.io/address/0xfbfF…
4/ The delegate call data to the contract as seen on (2) is
0x804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6
so delegating a call to the 0x804e1f0a function with 000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6 as param - an address?
0x804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6
so delegating a call to the 0x804e1f0a function with 000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6 as param - an address?
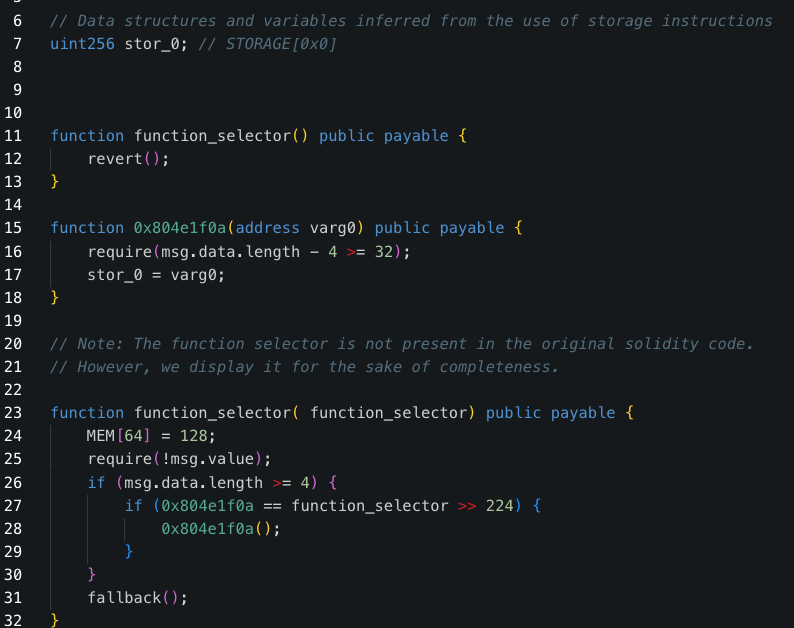
5/ in the Decompilation of the 0xfbfFEF83b1C172fE3BC86C1CCB036AB9F3efCAF2 - we can see that when calling 0x804e1f0a the slot0 is modified, with the input address. since the msig delegated a call to this contract it will modify to 0 slot of the multisig itself! because of the nature of delegate call
6/ Now let's check what was stored in the 0 slot of the Msig proxy before the malicious delegatecall using we can see that prior the attack tx it was the standard safe Impl and after it was a new proprietary deployed contract evm.storage




7/ Analyzing a tx that funds were stolen:
in this tx for example 95m worth of Shiba i nu were stolen, after the modification of the impl etherscan.io/tx/0x1e523051a…
in this tx for example 95m worth of Shiba i nu were stolen, after the modification of the impl etherscan.io/tx/0x1e523051a…
8/ Using you can see that from now on every tx to the Safe Multisig redirects a delegatecall to the new implementation address specified in (4) openchain.xyz


• • •
Missing some Tweet in this thread? You can try to
force a refresh





