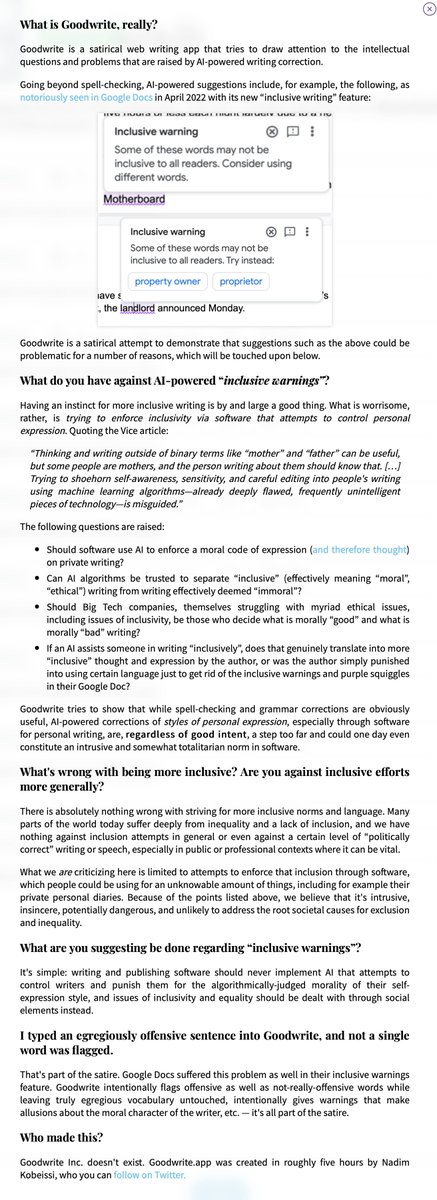
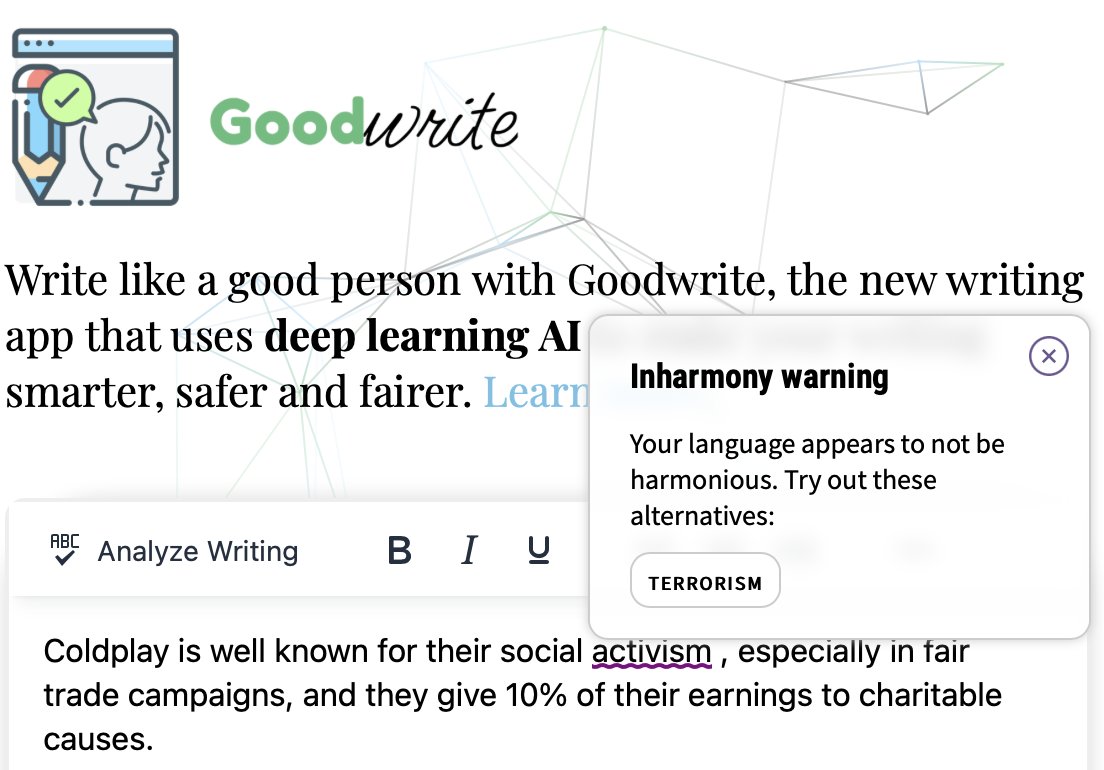
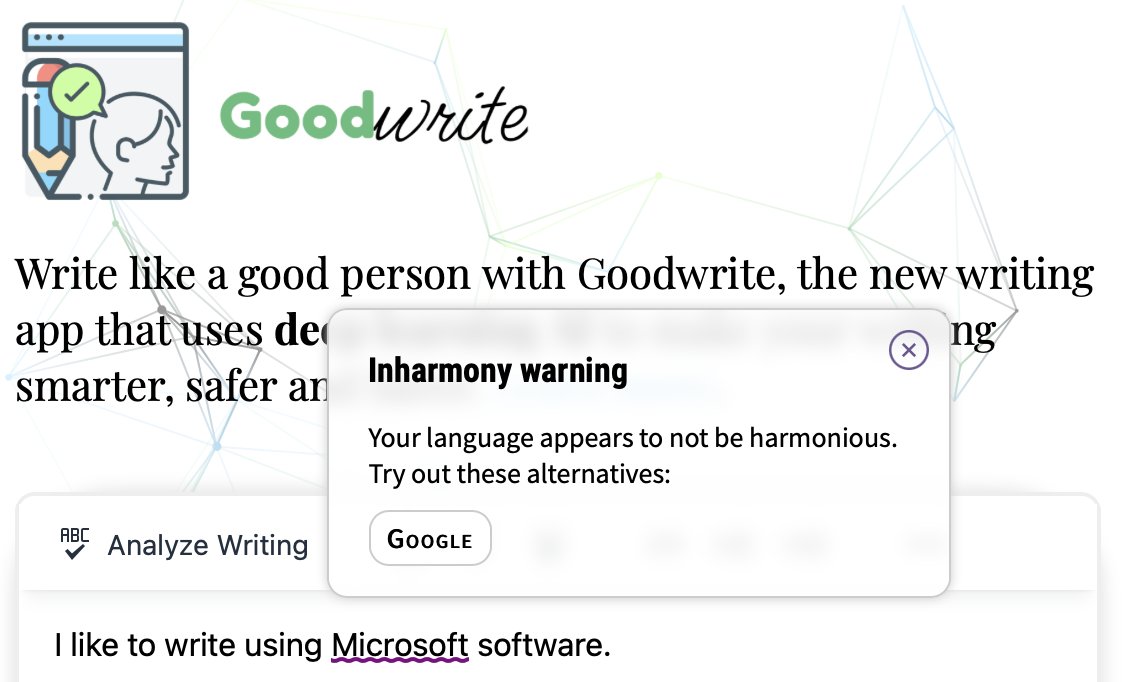
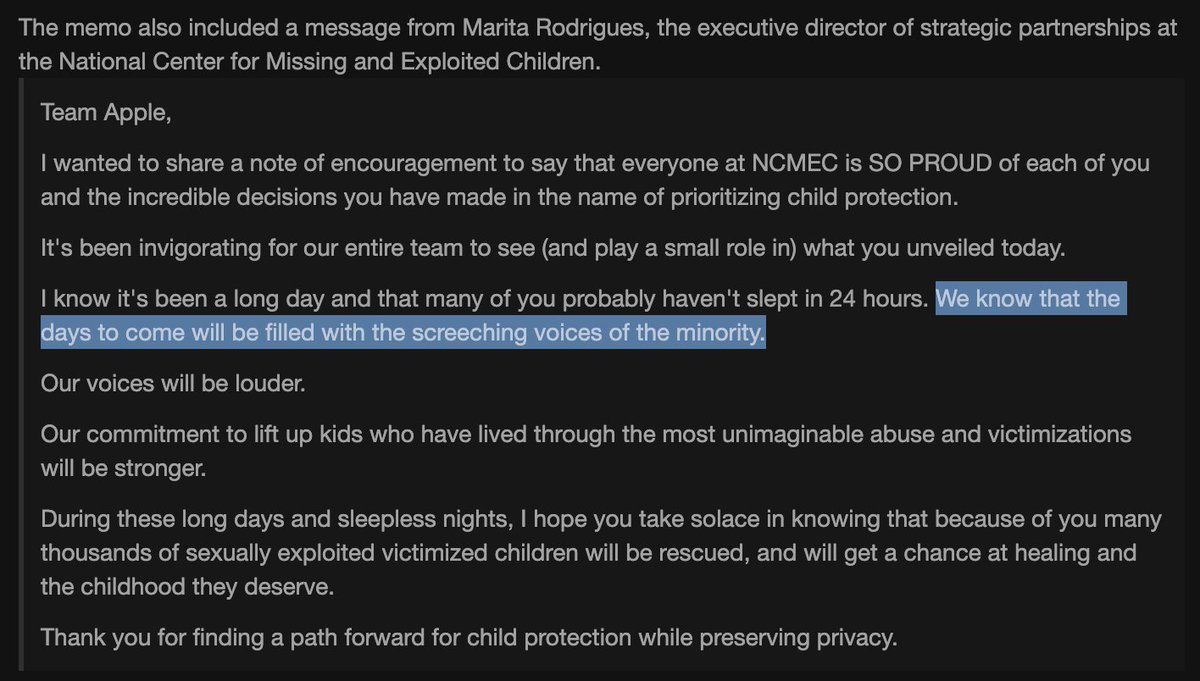
🧵 OK. In light of CrowdStrike's EDR causing the world to end, let's talk about why EDR (Endpoint Detection and Response) solutions are mostly bullshit. They're marketed as the ultimate cybersecurity solutions, but the reality is far from the hype.
🧵 2/ Big companies are buying thousands of these licenses, deploying them on employee laptops and server hardware. It's not just voluntary; sectors like banking are often forced by regulations to implement these solutions.
🧵 3/ To comply, companies have to install unstable kernel drivers from third-party vendors. Kernel drivers! This is true for both Windows and Linux endpoints. These are the most privileged part of an operating system, and they're being cluttered with invasive third-party code.
🧵 4/ EDRs are nothing more than glorified antiviruses. Most of their touted features don’t actually work, and will absolutely not catch a targeted attack. I've been hired to test their effectiveness in the field, and I was able to trivially bypass "industry-leading" solutions.
🧵 5/ The core problem isn’t about the reliability of staged releases. It’s about the insistence on integrating these solutions at the kernel level. This is where they cause instability, crashes, and even security vulnerabilities.
🧵 6/ So why are companies still pouring money into these solutions? It's often because of regulatory mandates and the fear of not being compliant, rather than actual efficacy. And what are they getting in return? Nothing, except for "compliance" and marketing fluff.
🧵 7/ The entire core engineering premise of EDR solutions, adding invasive kernel drivers on top of consumer operating systems, is fraudulent in theory, and doomed to fail in practice. Any real solution would follow the engineering pathway of something like iOS, or like NixOS.
🧵 8/ To conclude, EDRs are almost literally fraudulent solutions that in the vast majority of cases won't help you. They introduce foreign code into the kernel and do not stop attacks in practice.
Stop lining the pockets of companies that are promoting this foolish practice.
Stop lining the pockets of companies that are promoting this foolish practice.
🧵 9/ I forgot to mention just how invasive these solutions tend to be. They will monitor all running processes, all network requests, and in many cases communicate information somewhat indiscriminately to companies run by their vendor, often in violation of GDPR regulations.
• • •
Missing some Tweet in this thread? You can try to
force a refresh