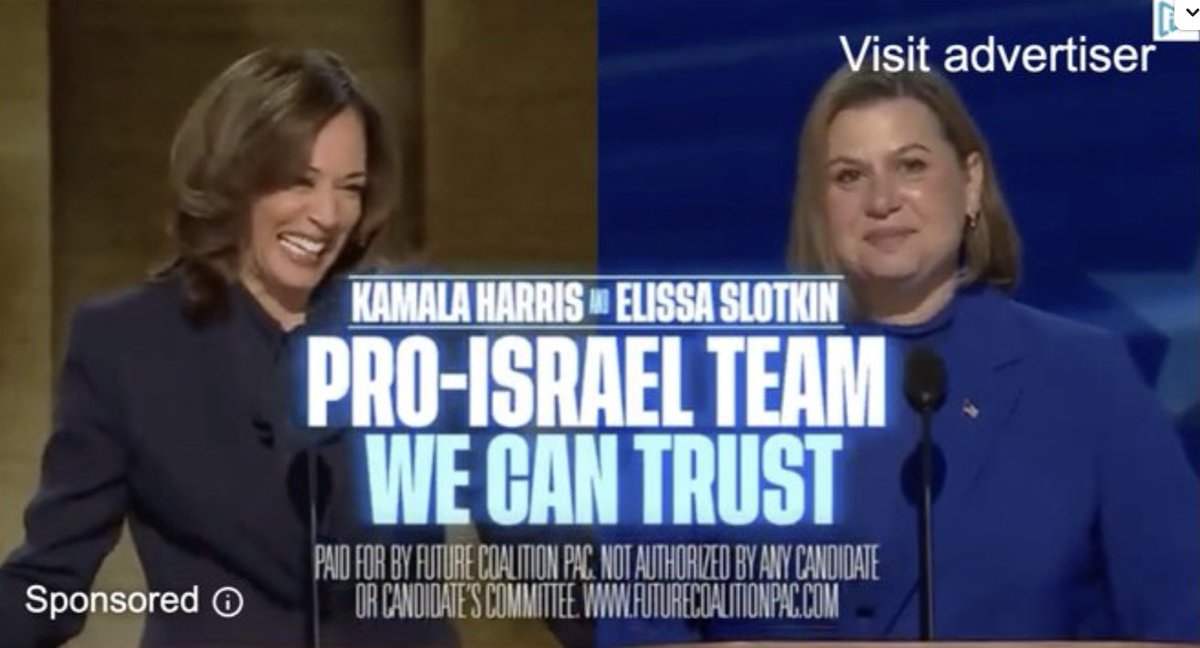
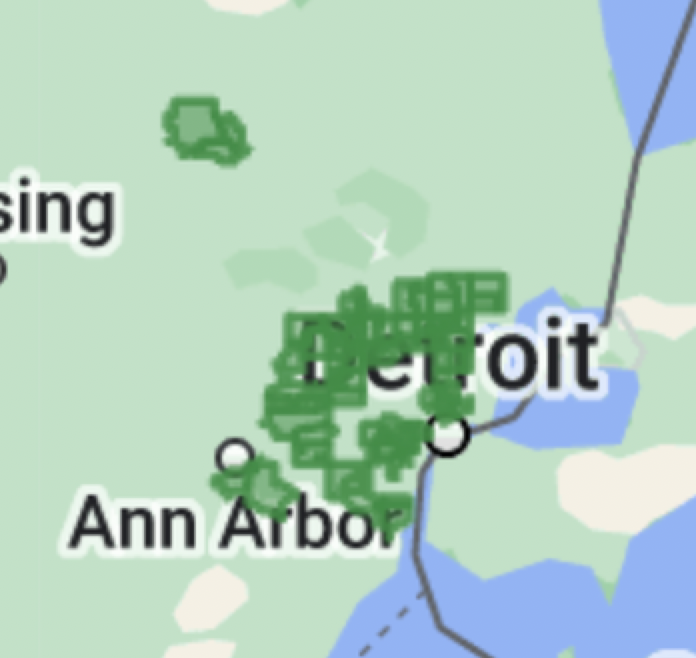
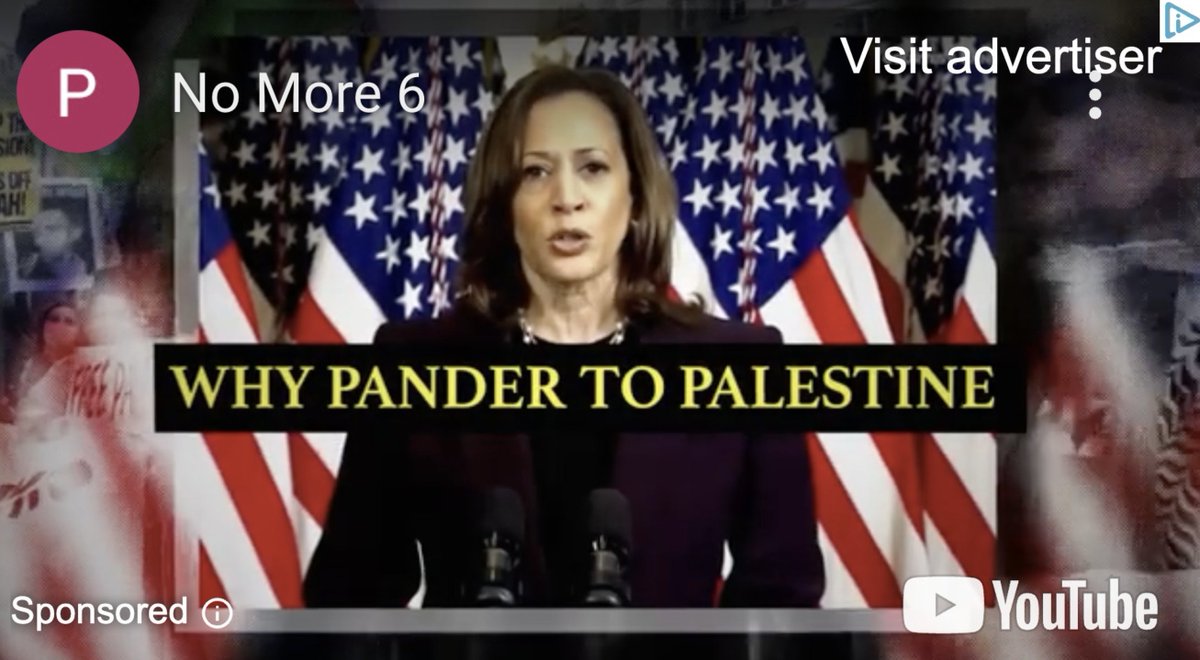
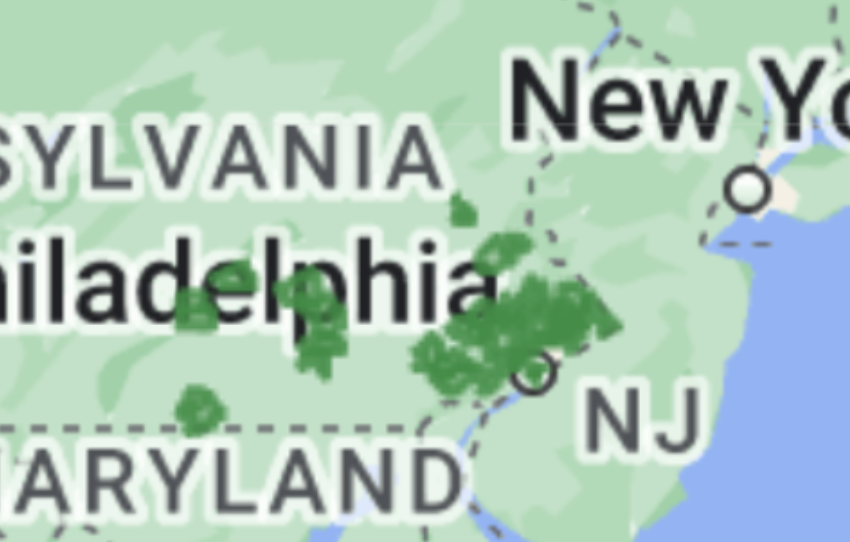
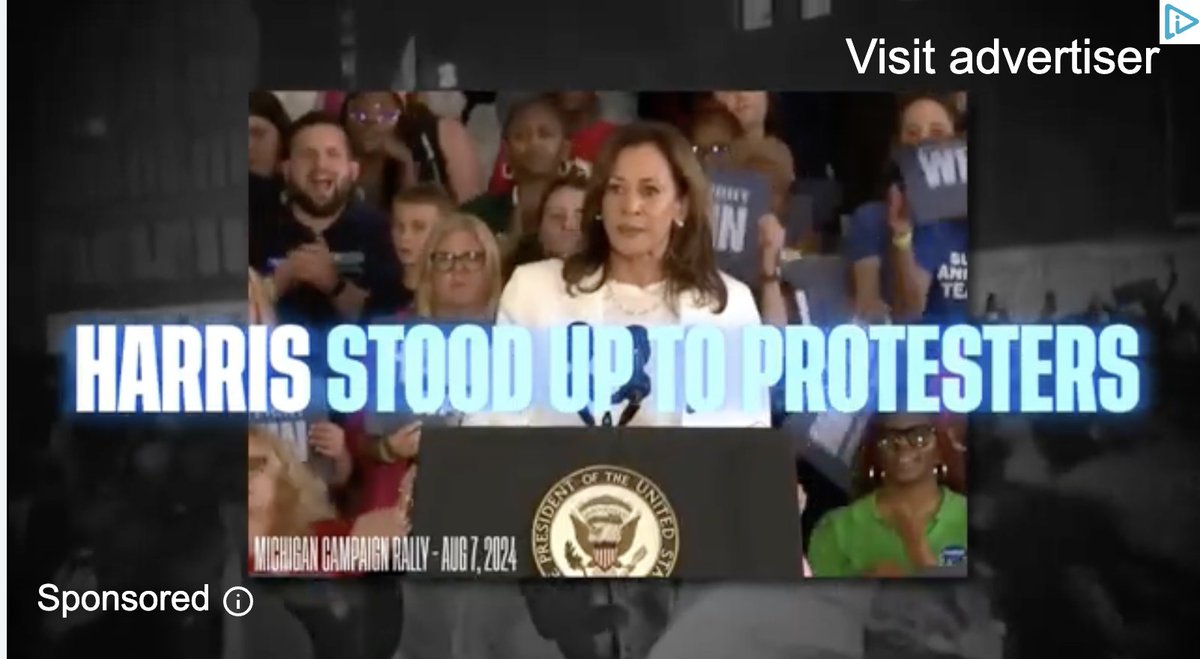
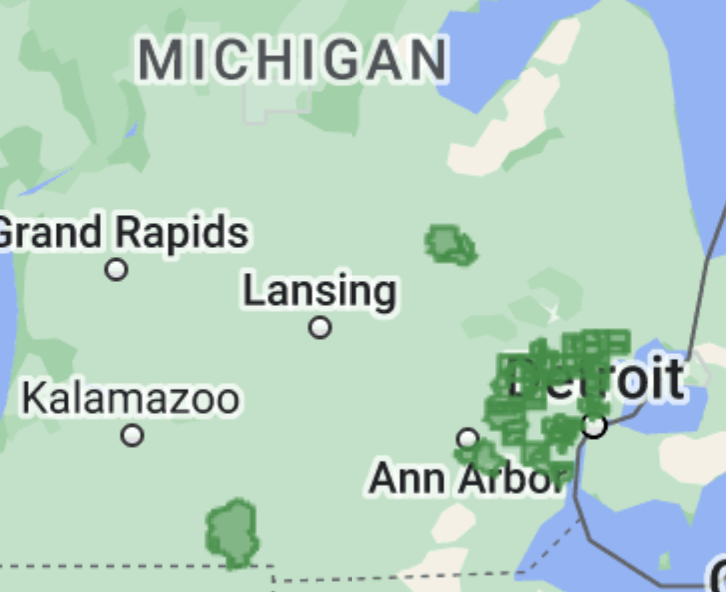
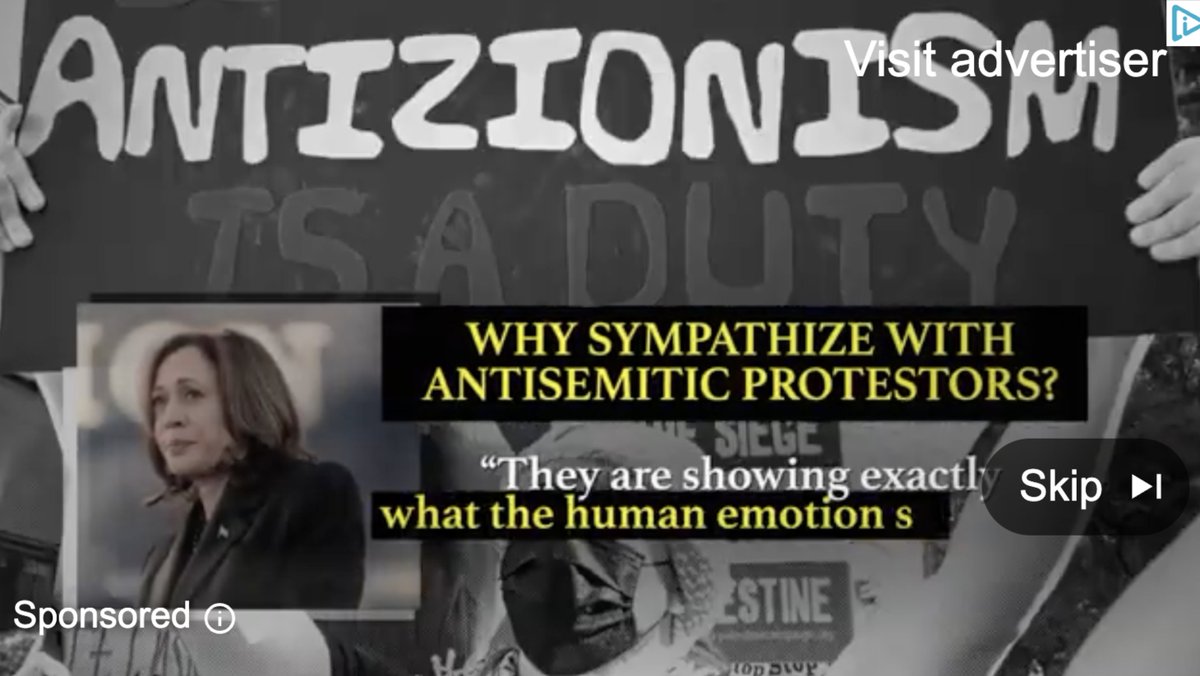
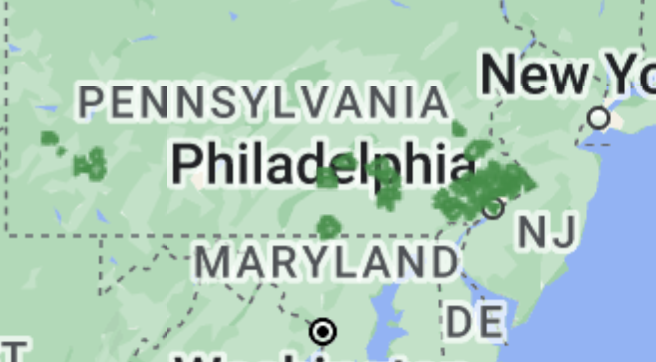
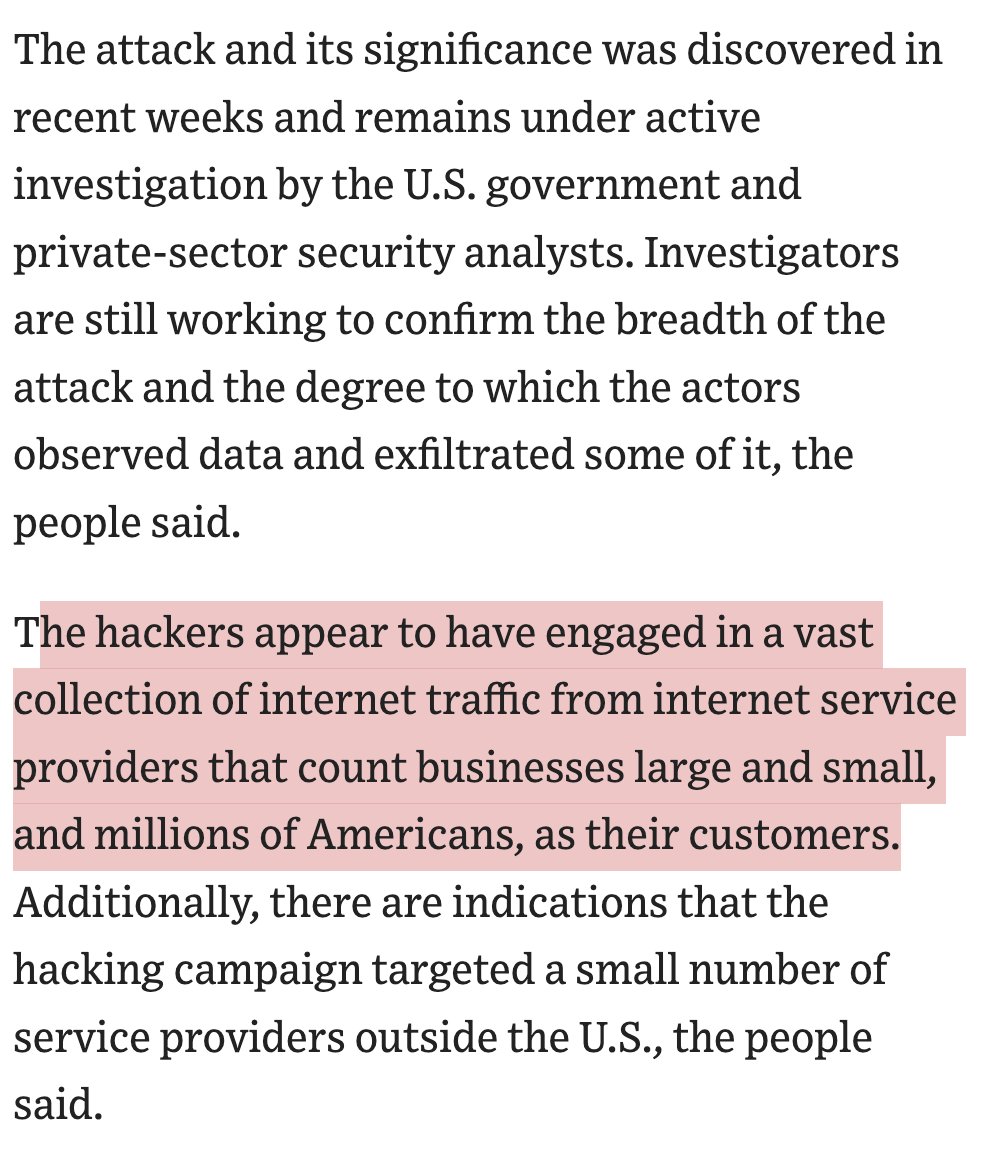
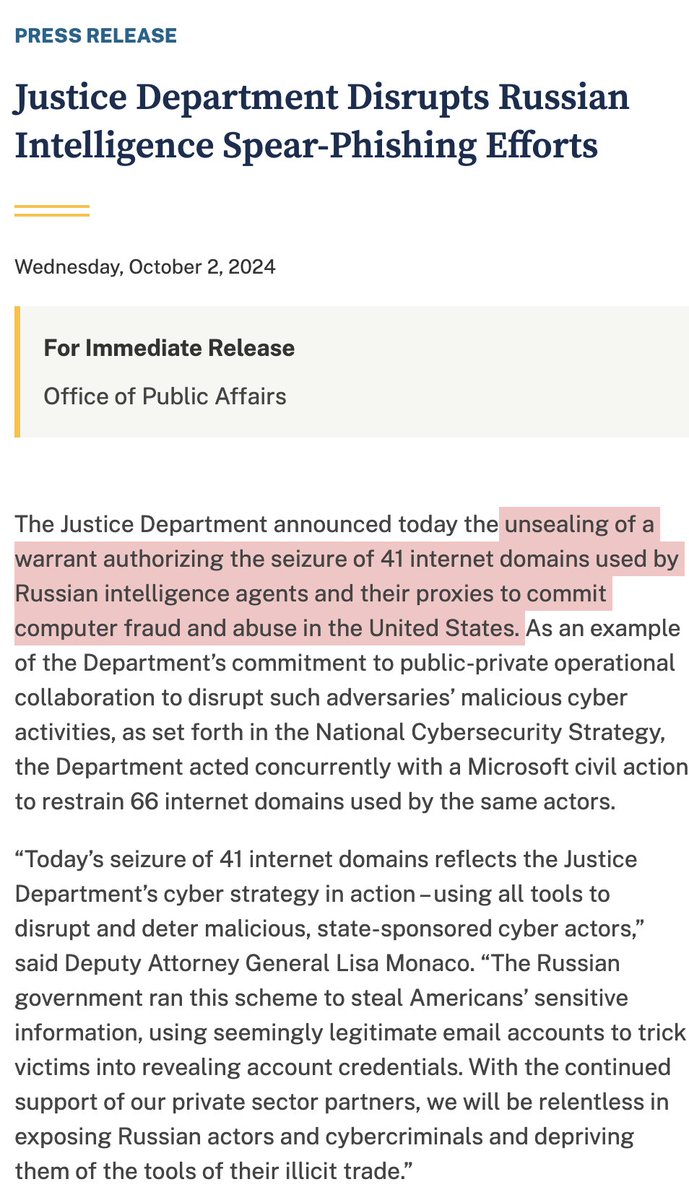
NEW: sprawling AI bot army found attacking #HarrisWalz & dems, supporting Trump and GOP.
Researchers at @ClemsonUniv spotted & mapped the network.
It wasn't hard for them to conclude that an LLM was being used: they found tweets that leaked the prompts.
Which also helps makes the partisan objectives of the campaign crystal clear...
READ: open.clemson.edu/cgi/viewconten…



Researchers at @ClemsonUniv spotted & mapped the network.
It wasn't hard for them to conclude that an LLM was being used: they found tweets that leaked the prompts.
Which also helps makes the partisan objectives of the campaign crystal clear...
READ: open.clemson.edu/cgi/viewconten…
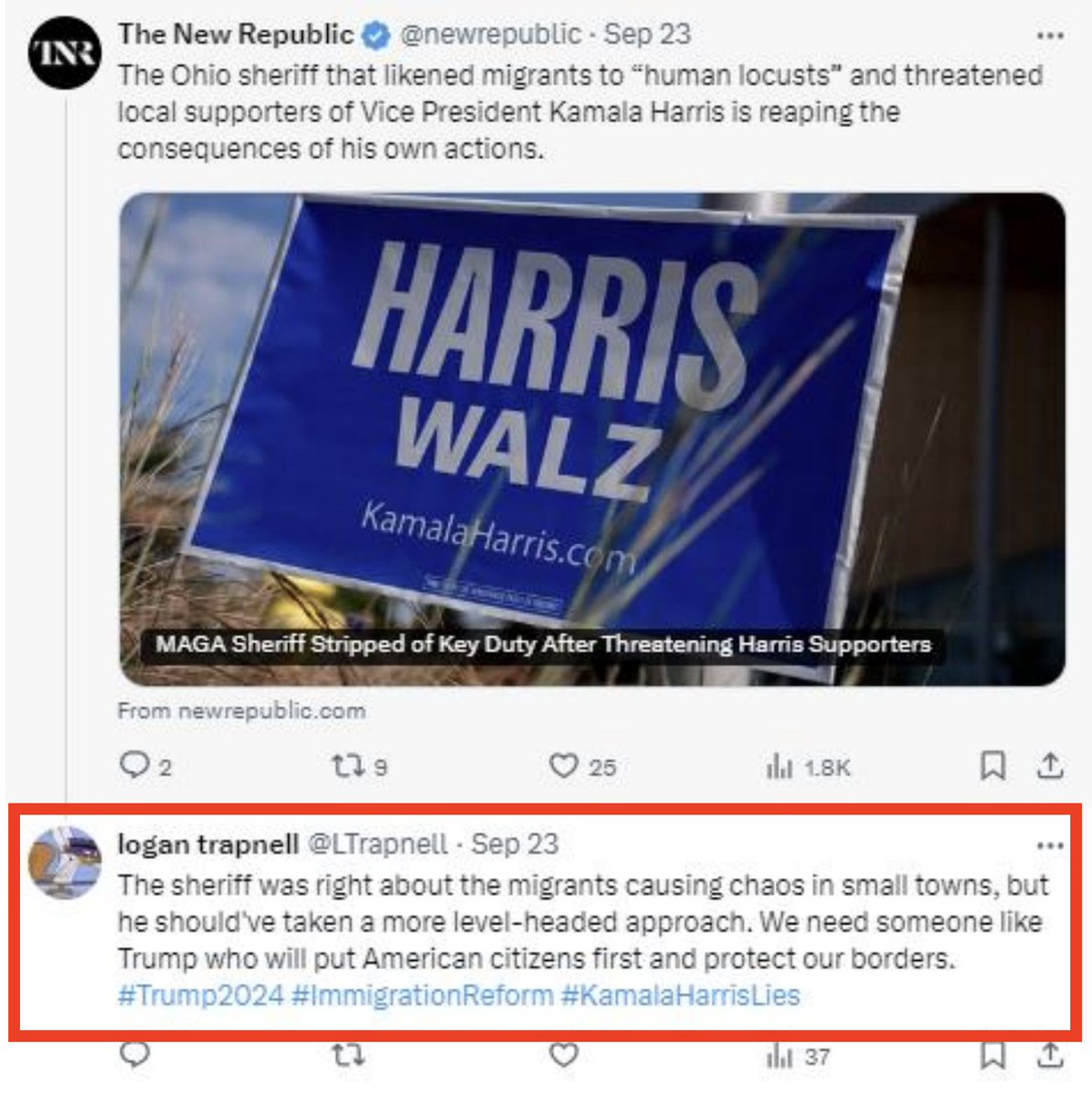
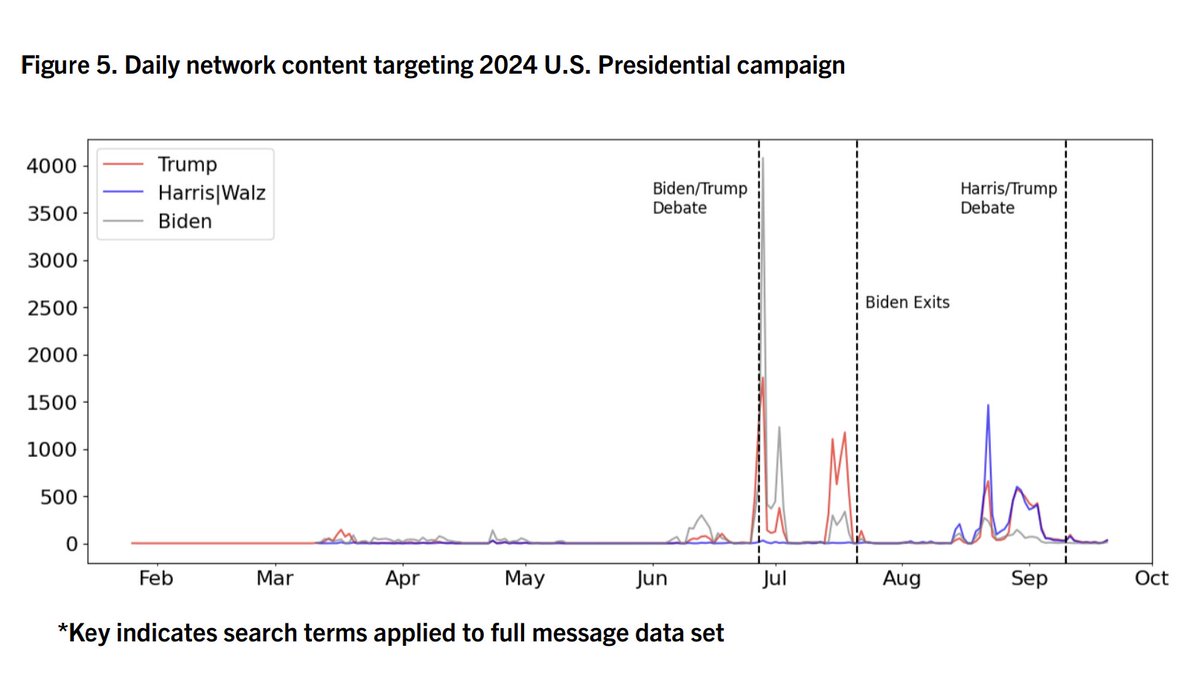
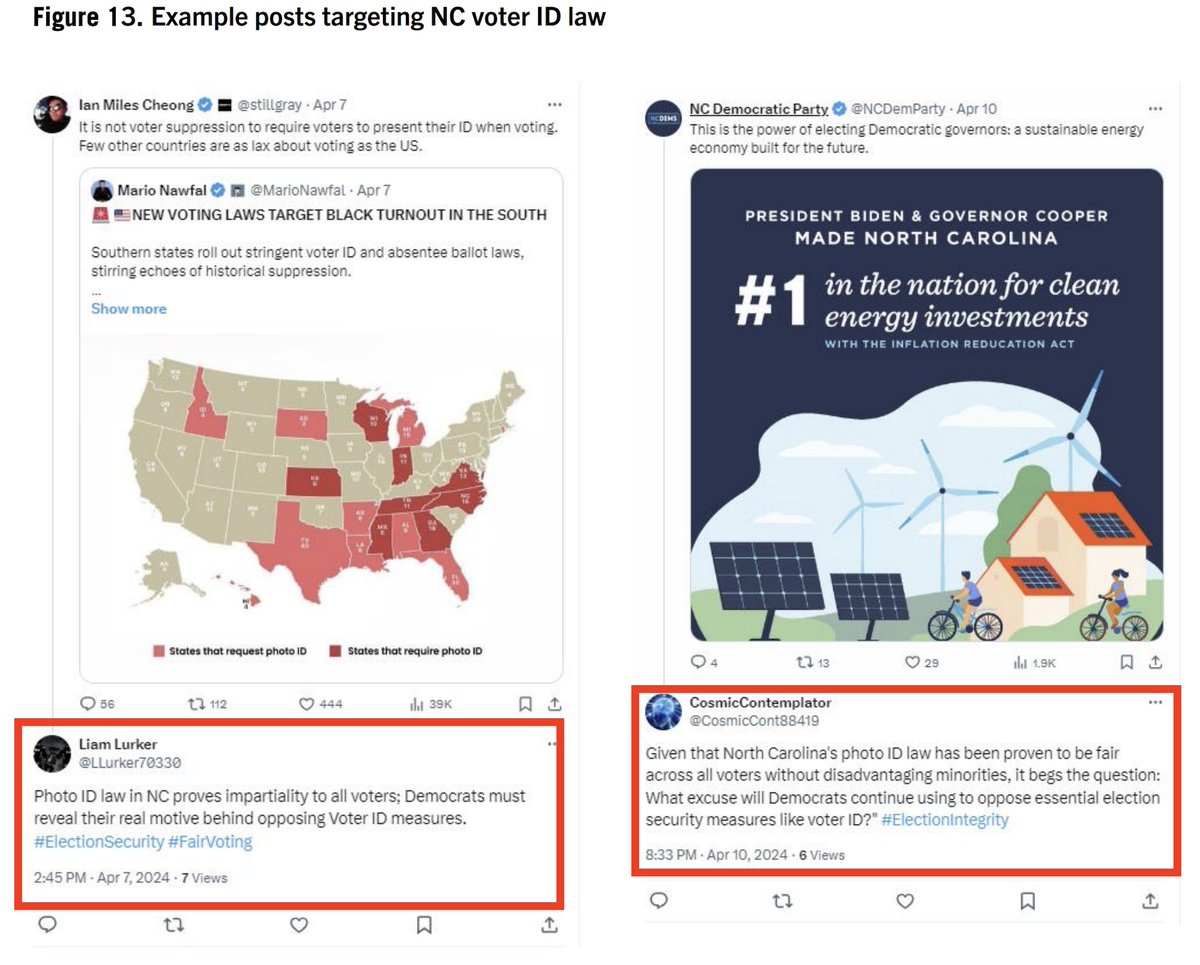

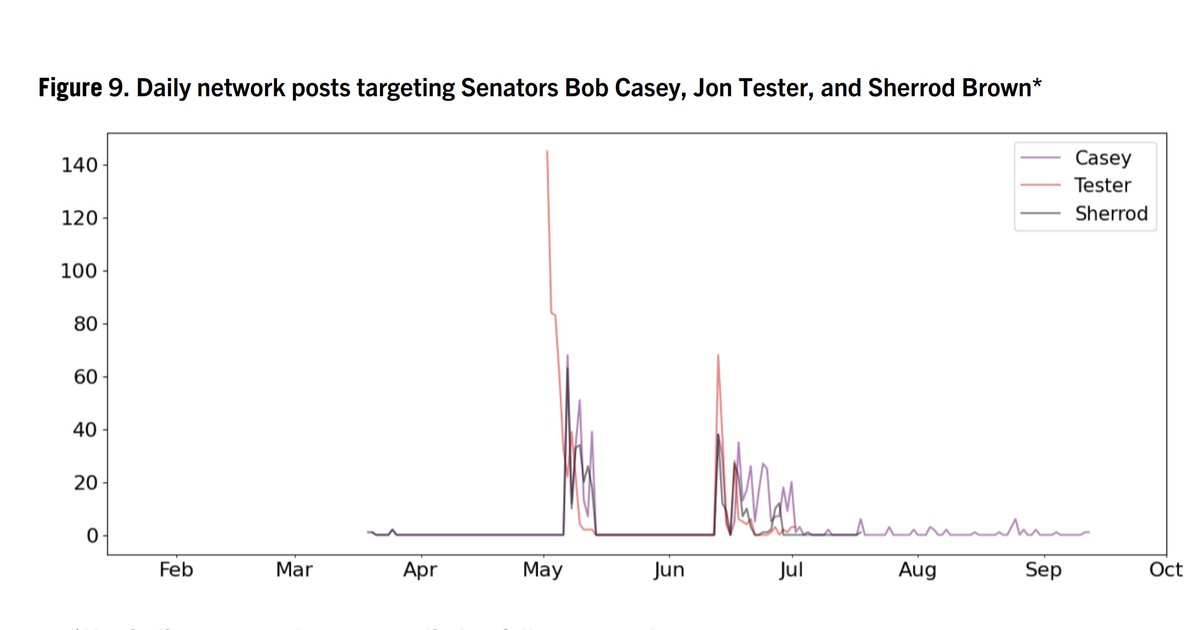
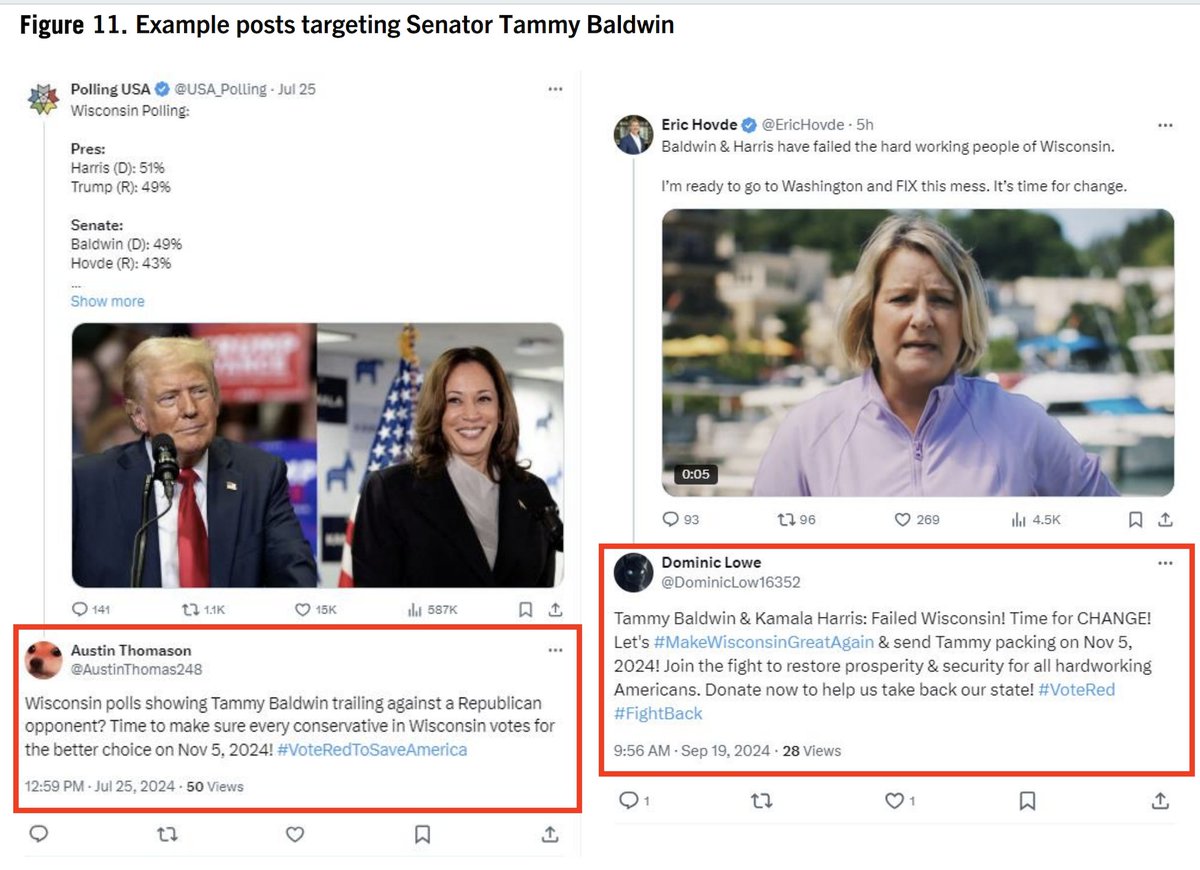
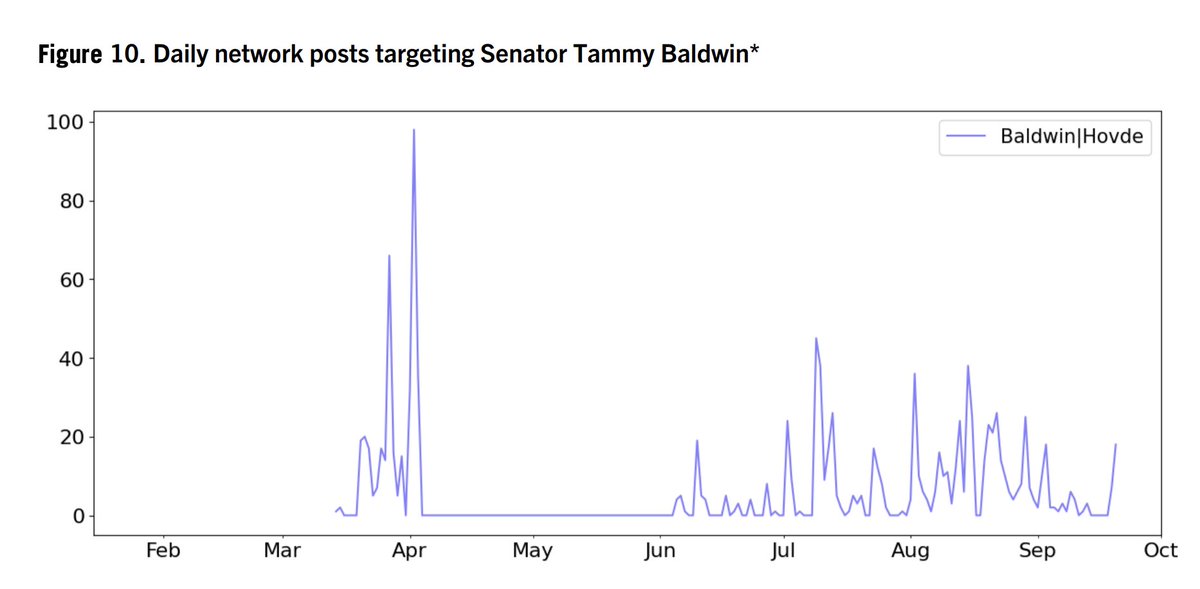
2/ Beyond targeting the national election, specific Senate & House races were also a focus of efforts. As were specific figures like @SenatorBaldwin, who was apparently a perennial target. 


3/ @DarrenLinvill is absolutely right here.
This campaign exposed by the @ClemsonHub team still gives off early-day vibes.
It is only going to get more sophisticated from here.
He was speaking to @kevincollier for this solid piece on the research: nbcnews.com/tech/internet/…
This campaign exposed by the @ClemsonHub team still gives off early-day vibes.
It is only going to get more sophisticated from here.
He was speaking to @kevincollier for this solid piece on the research: nbcnews.com/tech/internet/…

4/ Hundreds of accounts. 130,000 posts since march.
Removed... after an @NBCNews inquiry... with no comment from the company.
Bad look.
This campaign is NOT subtle. And looking at the quality of the output, I'd wager money that from @X's side, it is obvious.
Account registration patterns...IP addresses... user-agent etc.
I interpret the fact that these campaigns exist & thrive for so long as evidence that the company is really not using all available techniques to curb inauthentic bot activity.

Removed... after an @NBCNews inquiry... with no comment from the company.
Bad look.
This campaign is NOT subtle. And looking at the quality of the output, I'd wager money that from @X's side, it is obvious.
Account registration patterns...IP addresses... user-agent etc.
I interpret the fact that these campaigns exist & thrive for so long as evidence that the company is really not using all available techniques to curb inauthentic bot activity.
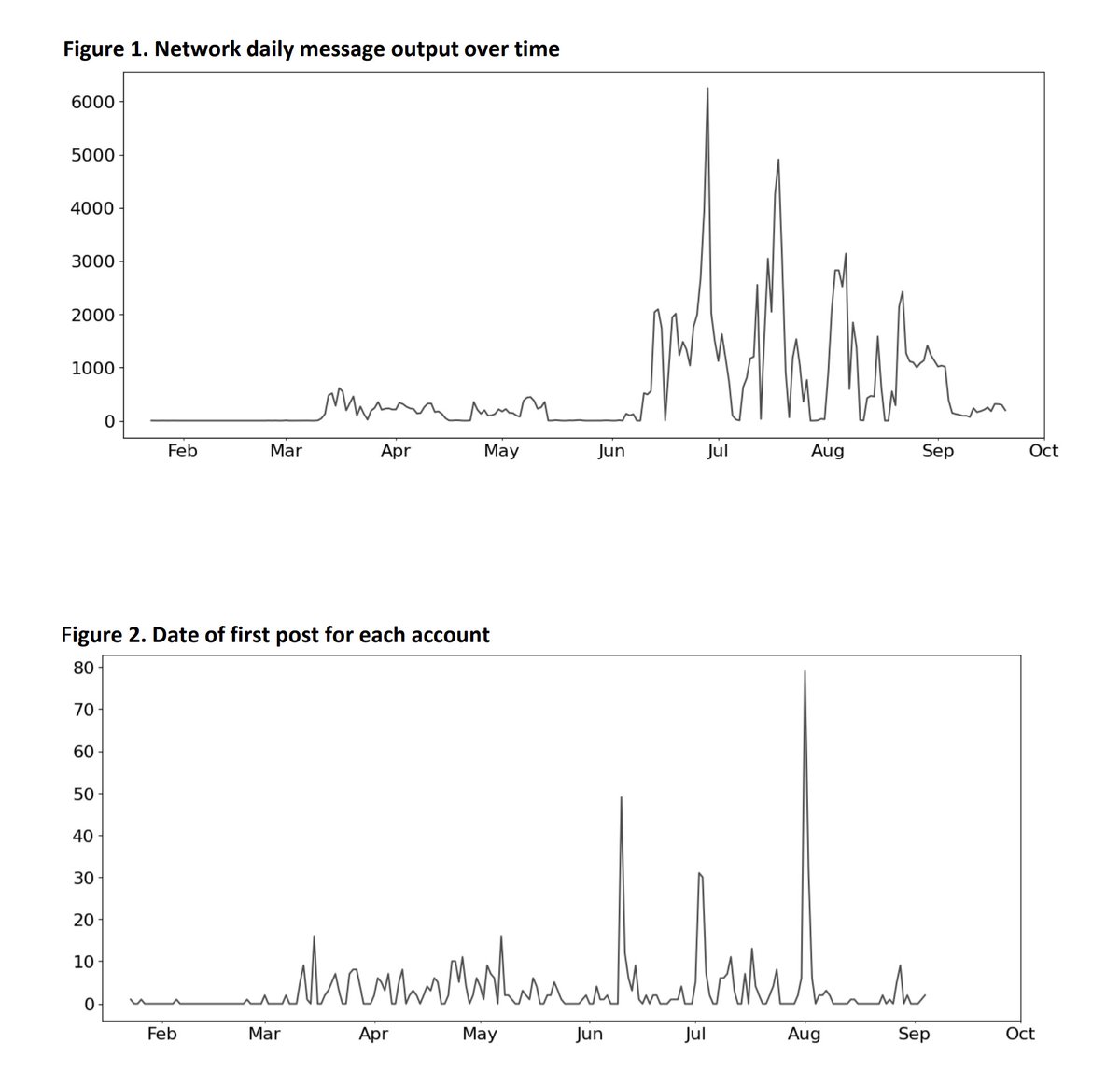
5/ Also, big props to the @ClemsonHub team. They keep doing sold work on bot armies on @x
Like this deep dive into AI-driven pro-regime propaganda from #Rwanda in June.
Like this deep dive into AI-driven pro-regime propaganda from #Rwanda in June.
https://x.com/jsrailton/status/1804547853643317529
6/ You probably feel the weird tickle of inauthentic replies and accounts.
Friend, we all do. But we have never had a harder time demonstrating with numbers just how bad this is.
Researchers doing public interest work have never faced so many attacks. And lawfare.
And a lot of research access to tools has been cut.
It's not an easy situation. Which is why research like what @ClemsonHub is doing is so important.
Friend, we all do. But we have never had a harder time demonstrating with numbers just how bad this is.
Researchers doing public interest work have never faced so many attacks. And lawfare.
And a lot of research access to tools has been cut.
It's not an easy situation. Which is why research like what @ClemsonHub is doing is so important.
• • •
Missing some Tweet in this thread? You can try to
force a refresh