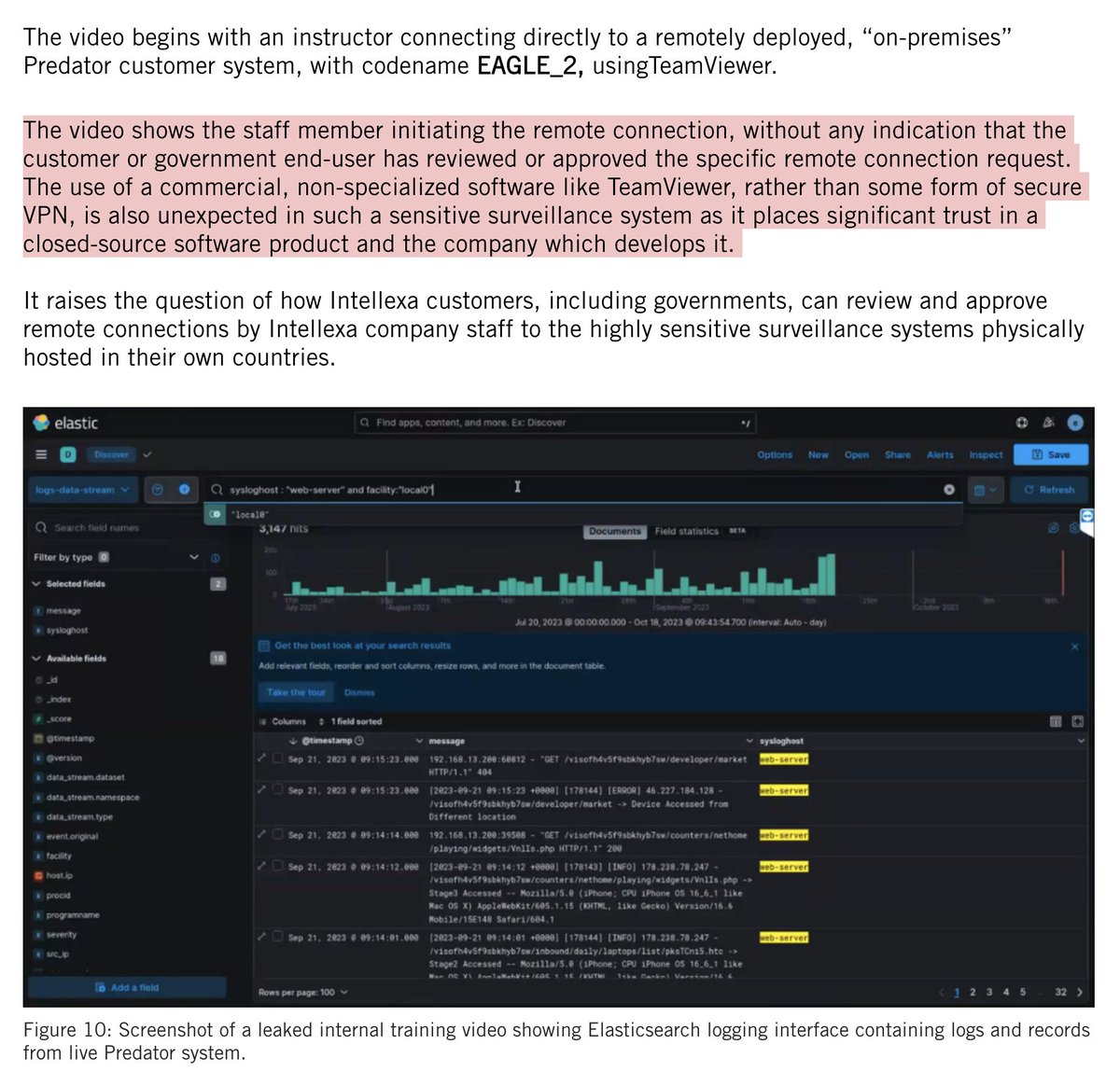
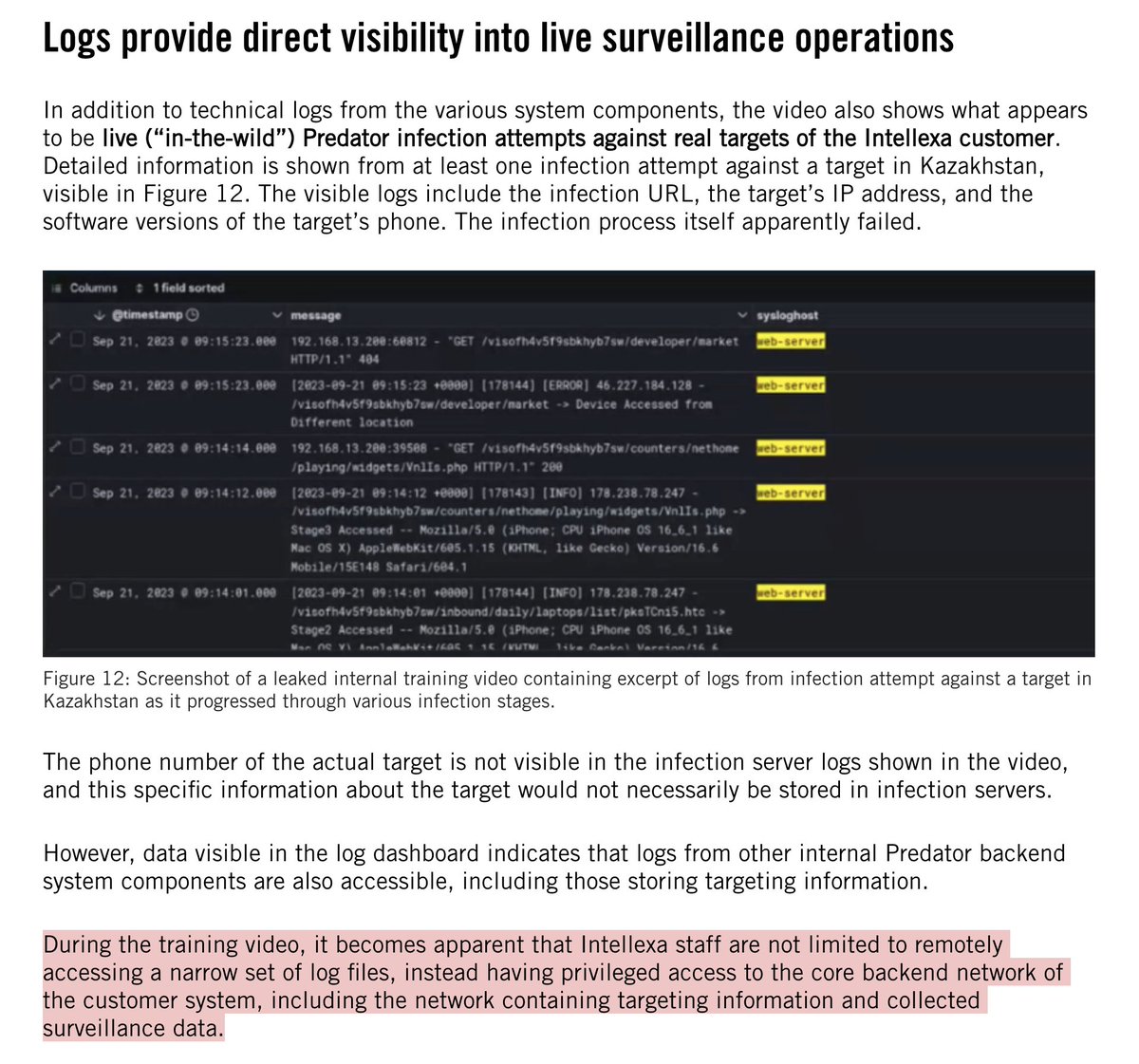
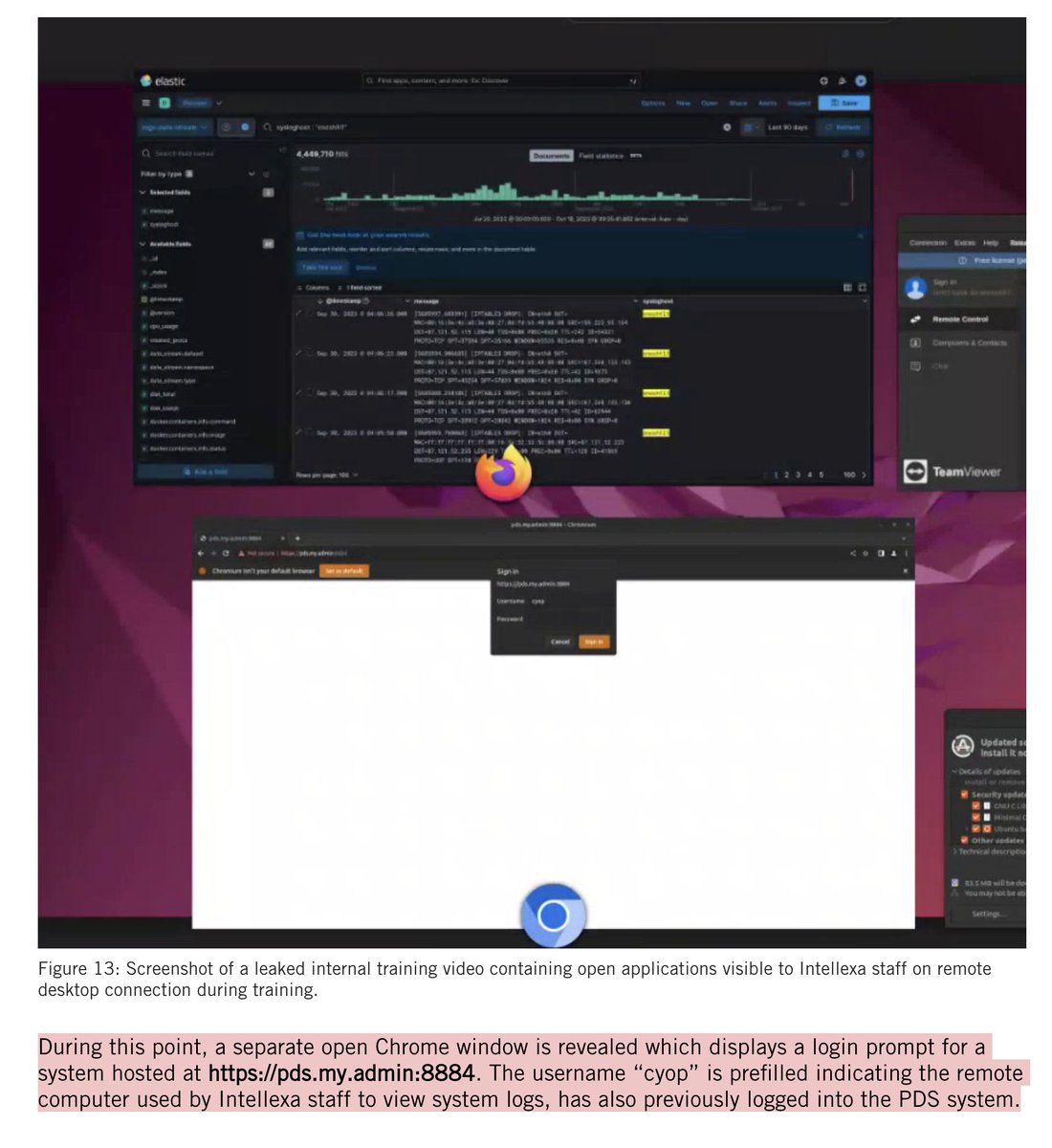
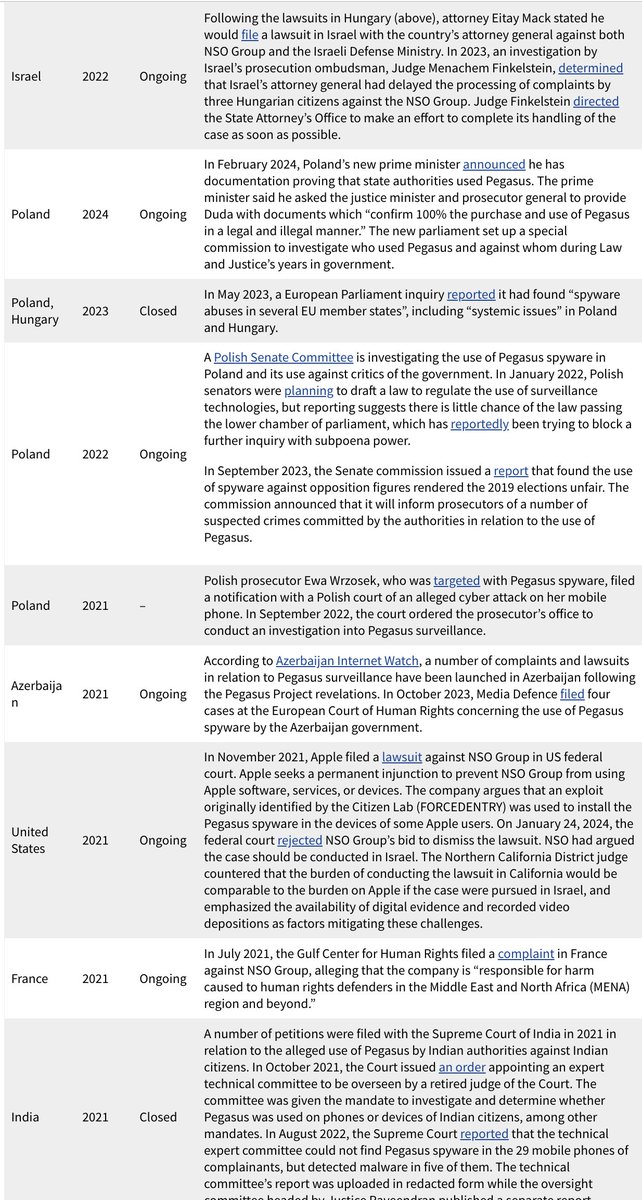
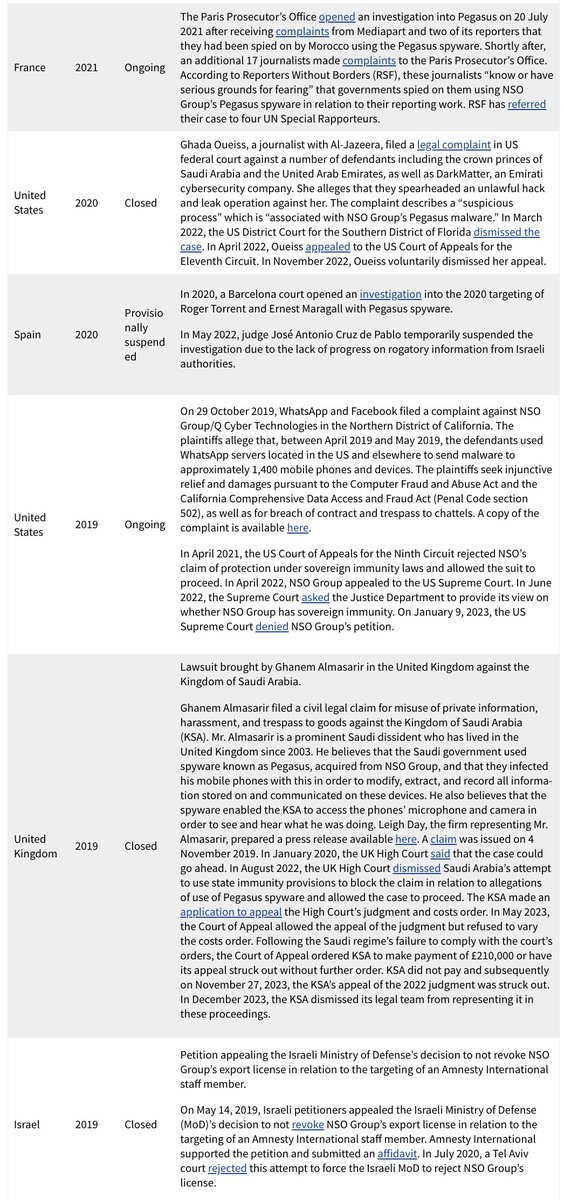
BREAKING: NSO Group liable for #Pegasus hacking of @WhatsApp users.
Big win for spyware victims.
Big loss for NSO.
Bad time to be a spyware company.
Landmark case. Huge implications. 1/ 🧵



Big win for spyware victims.
Big loss for NSO.
Bad time to be a spyware company.
Landmark case. Huge implications. 1/ 🧵




2/ In 2019, 1,400 @WhatsApp users were targeted with #Pegasus.
WhatsApp did the right thing & sued NSO Group.
NSO has spent 5 years trying to claim that they are above the law.
And engaged in all sorts of maneuvering.
With this order, the music stopped and NSO is now without a chair.

WhatsApp did the right thing & sued NSO Group.
NSO has spent 5 years trying to claim that they are above the law.
And engaged in all sorts of maneuvering.
With this order, the music stopped and NSO is now without a chair.


3/ Today, the court decided that enough was enough with NSO's gambits & efforts to hide source code.
Judge Hamilton granted @WhatsApp's motion for summary judgement against the #Pegasus spyware maker.
The judge finds NSO's hacking violated the federal Computer Fraud & Abuse Act (#CFAA), California state anti-fraud law #CDFA, and was a breach of contract.
What happens next? The trial proceeds only on the issue of resolving damages stemming from NSO's hacking.
Order: storage.courtlistener.com/recap/gov.usco…
Judge Hamilton granted @WhatsApp's motion for summary judgement against the #Pegasus spyware maker.
The judge finds NSO's hacking violated the federal Computer Fraud & Abuse Act (#CFAA), California state anti-fraud law #CDFA, and was a breach of contract.
What happens next? The trial proceeds only on the issue of resolving damages stemming from NSO's hacking.
Order: storage.courtlistener.com/recap/gov.usco…

4/@WhatsApp suing NSO Group was a huge deal at the time.
We at @citizenlab & our peers in civil society had been investigating & surfacing a pile of #Pegasus abuses since 2016. Journalists, dissidents, truth-tellers, scientists, lawyers..
But nobody was taking action & NSO was flying high.
The ultimate digitally-enabled playground bully.
citizenlab.ca/2016/08/millio…



We at @citizenlab & our peers in civil society had been investigating & surfacing a pile of #Pegasus abuses since 2016. Journalists, dissidents, truth-tellers, scientists, lawyers..
But nobody was taking action & NSO was flying high.
The ultimate digitally-enabled playground bully.
citizenlab.ca/2016/08/millio…



5/ For years, governments seemed content to let the mercenary spyware industry live in the shadows...
NSO's valuation & client list ballooned.
Meanwhile, NSO constantly misled reporters, nurtured disinformation about researchers & blamed spyware victims..
And then they got sued by a very big company that chose to stick up for its users & security.
Suddenly, NSO wasn't on such sure footing.
@WhatsApp had their own factual, technical analyses, and plenty of resources
Suddenly they couldn't just claim that a few researchers were out to get them.
By @MehulAtLarge
ft.com/content/67a5b4…

NSO's valuation & client list ballooned.
Meanwhile, NSO constantly misled reporters, nurtured disinformation about researchers & blamed spyware victims..
And then they got sued by a very big company that chose to stick up for its users & security.
Suddenly, NSO wasn't on such sure footing.
@WhatsApp had their own factual, technical analyses, and plenty of resources
Suddenly they couldn't just claim that a few researchers were out to get them.
By @MehulAtLarge
ft.com/content/67a5b4…


6/ In the years after @WhatsApp sued NSO, much happened.
More court cases were filed against the #Pegasus spyware maker.
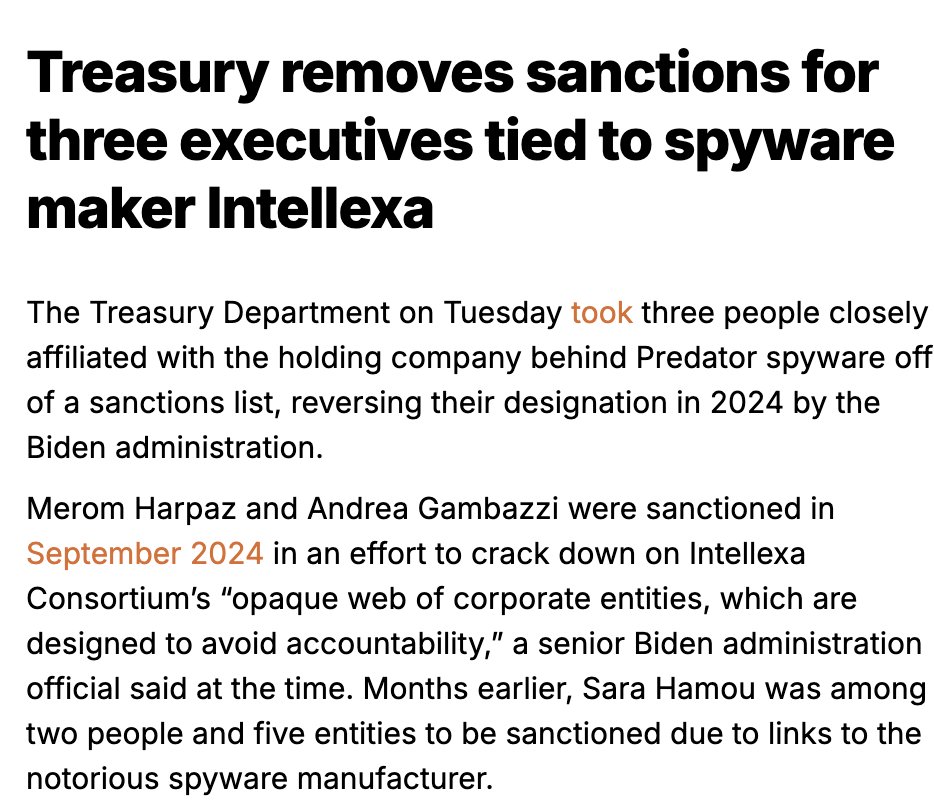
And in November 2021 NSO got hit with US sanctions.
But thankfully, WhatsApp stuck to the case for five years even as NSO seems to have tried every-available-trick to slow-roll & delay.
To some, it looked a lot NSO was being arrogant.
To others, like a company that truly held itself above any law...
Ultimately NSO's legal tactics seem to have gone over badly with the judge, resulting in today's summary judgement.
More court cases were filed against the #Pegasus spyware maker.
And in November 2021 NSO got hit with US sanctions.
But thankfully, WhatsApp stuck to the case for five years even as NSO seems to have tried every-available-trick to slow-roll & delay.
To some, it looked a lot NSO was being arrogant.
To others, like a company that truly held itself above any law...
Ultimately NSO's legal tactics seem to have gone over badly with the judge, resulting in today's summary judgement.
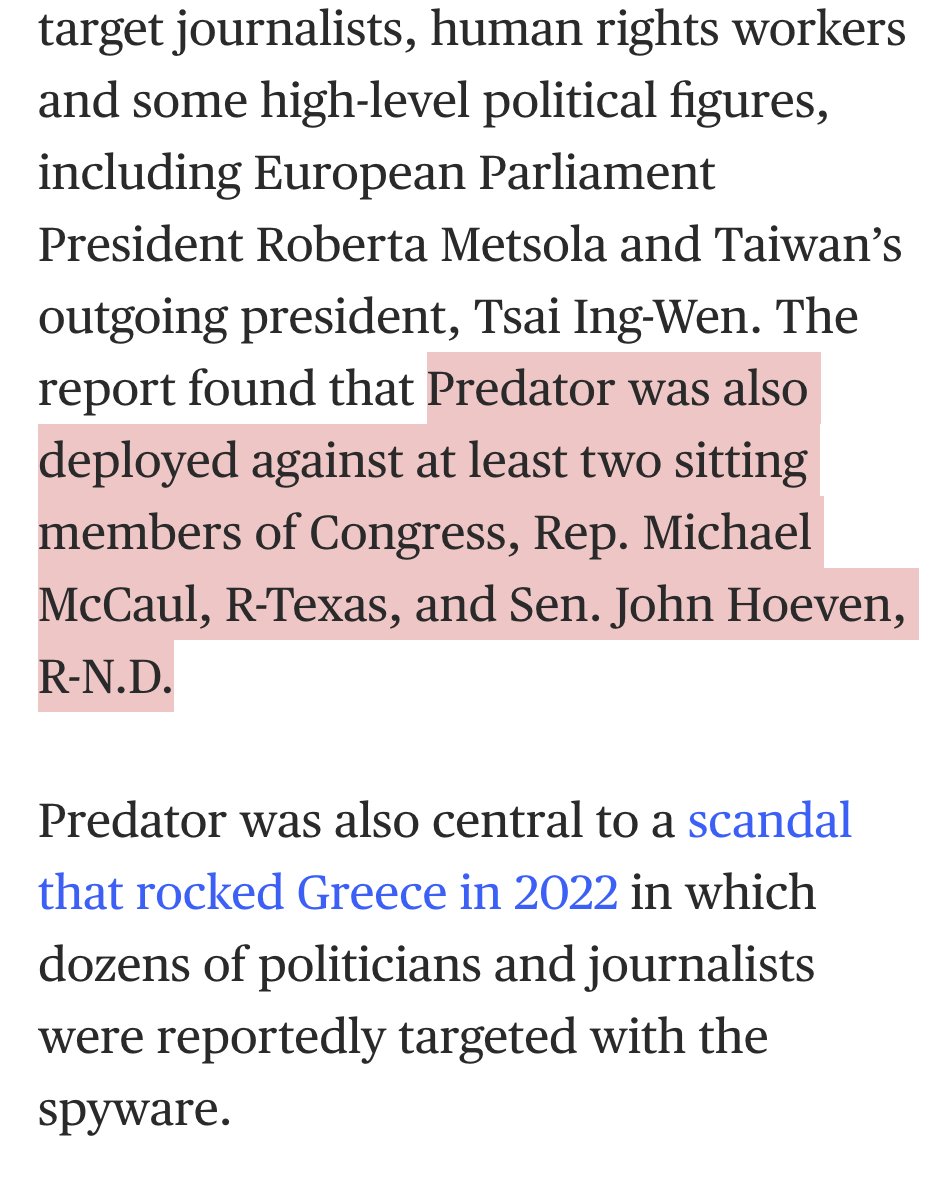
7/ The victims in the 2019 hack had been targeted with a simple missed video call exploit.
No action required, and once-infected, the call log would typically be deleted.
We @citizenlab volunteered help investigate the target list and try find journalists, dissidents, and human rights defenders.
We found a lot.
And plenty of unexpected pockets of repression. Like the targeting dissident members of the clergy in Togo.
citizenlab.ca/2020/08/nothin…



No action required, and once-infected, the call log would typically be deleted.
We @citizenlab volunteered help investigate the target list and try find journalists, dissidents, and human rights defenders.
We found a lot.
And plenty of unexpected pockets of repression. Like the targeting dissident members of the clergy in Togo.
citizenlab.ca/2020/08/nothin…




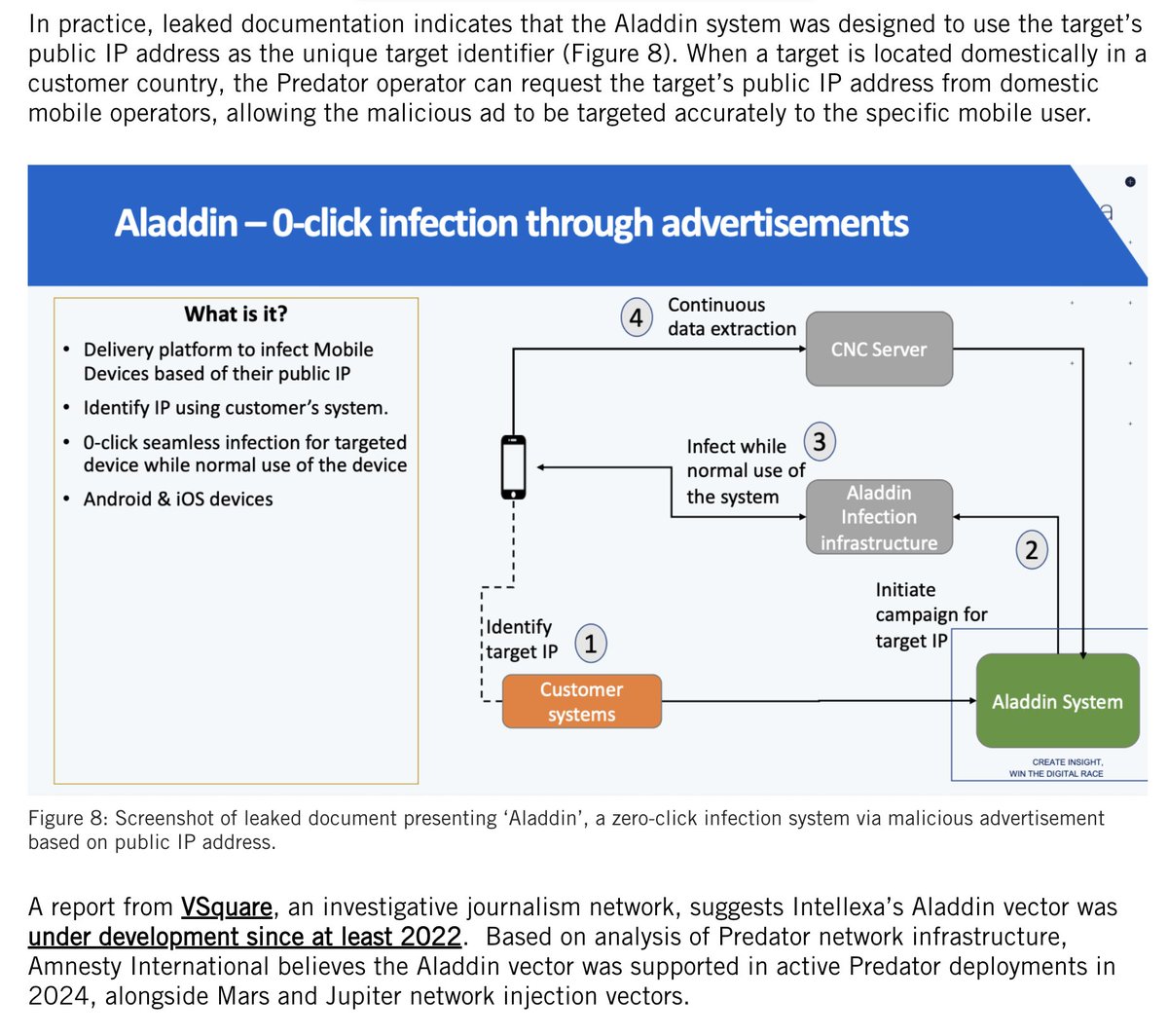
8/ In the years after the @WhatsApp case was filed, thanks to a lot of investigations including the #PegasusProject know hundreds of abuses.
It's just so. much. harm. So many lives surveilled & disrupted. So much repression.
There have been a lot court challenges, litigations & investigations /hearings over NSO in the ensuing years brought by victims.
For those cases still active, it's not hard to see how today's ruling in federal court will help many of them along.
citizenlab.ca/2018/12/litiga…



It's just so. much. harm. So many lives surveilled & disrupted. So much repression.
There have been a lot court challenges, litigations & investigations /hearings over NSO in the ensuing years brought by victims.
For those cases still active, it's not hard to see how today's ruling in federal court will help many of them along.
citizenlab.ca/2018/12/litiga…


9/ Take a minute & think about all the victims of #Pegasus.
Many bravely come forward & speak out.
Others make the difficult decision to remain private, often because of serious danger.
Today's order is a powerful sign for them: accountability can happen for companies like NSO.



Many bravely come forward & speak out.
Others make the difficult decision to remain private, often because of serious danger.
Today's order is a powerful sign for them: accountability can happen for companies like NSO.




10/ Since I'm not one, and this is a consequential decision, here's a lawyer breaking down today's landmark ruling in WhatsApp v NSO.👇
https://x.com/natynettle/status/1870274028331553237
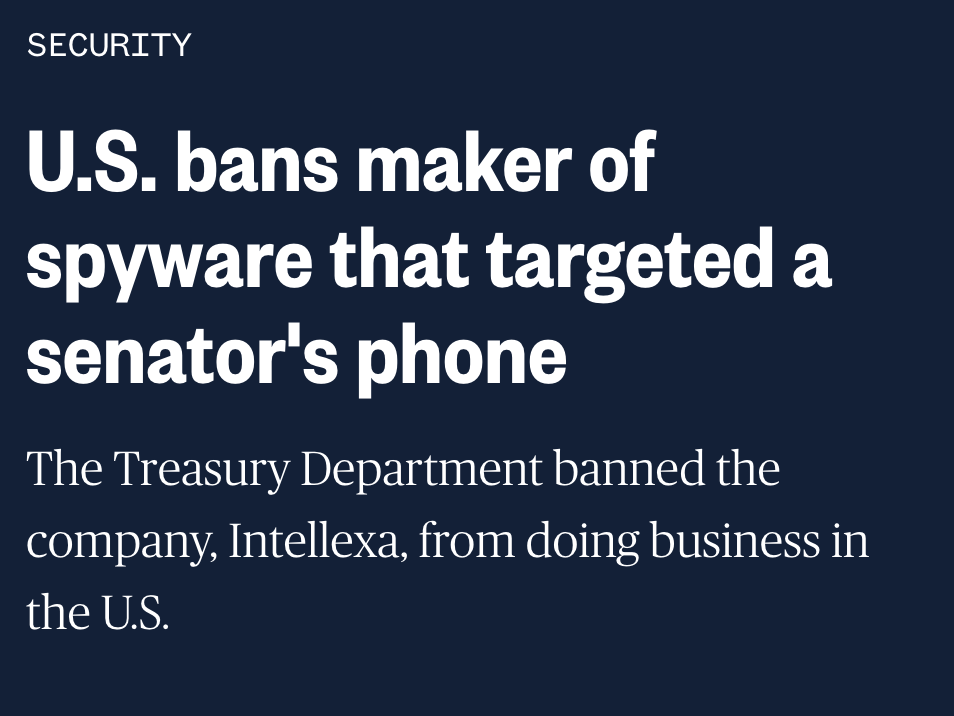
11/ Even as NSO has a bad time, other spyware companies like #Paragon present themselves as 'different' & 'approved' to try and break into the US market & grab market share.
I think their goal is to get enough contracts with countries like the US that it's hard to regulate them.
Be skeptical of their claims.
Seems like some are already falling apart.
They want to put secret hacking tools in the hands of American cops & police forces around the world.
You should demand oversight & action from Congress to stop this toxic industry from nesting in the US.
Today's ruling also raises questions about how legally safe it is for a company to sell & run hacking services targeting US-based platforms & their users.
By @razhael & @AJVicens
reuters.com/technology/cyb…



I think their goal is to get enough contracts with countries like the US that it's hard to regulate them.
Be skeptical of their claims.
Seems like some are already falling apart.
They want to put secret hacking tools in the hands of American cops & police forces around the world.
You should demand oversight & action from Congress to stop this toxic industry from nesting in the US.
Today's ruling also raises questions about how legally safe it is for a company to sell & run hacking services targeting US-based platforms & their users.
By @razhael & @AJVicens
reuters.com/technology/cyb…




12/ Let's close by hearing from some of NSO Group's #Pegasus victims in this case.
These testimonies were gathered by @accessnow which led an amicus brief in the case.
accessnow.org/nso-whatsapp-h…



These testimonies were gathered by @accessnow which led an amicus brief in the case.
accessnow.org/nso-whatsapp-h…




• • •
Missing some Tweet in this thread? You can try to
force a refresh