1/8 🚨 SECURITY ALERT: A victim lost 143.45 ETH ($460,895) through transaction simulation spoofing 1 day ago.
Here's how these attacks work... 🧵
Here's how these attacks work... 🧵

2/8 📱 Transaction simulation is a feature in modern Web3 wallets that shows users the expected outcome of their transactions before signing.
This feature aims to improve transparency and user experience. 🔍
This feature aims to improve transparency and user experience. 🔍

3/8 ⚠️ However, attackers exploit the delay between simulation and execution.
They create phishing sites that manipulate on-chain states immediately after transaction submission. 🕒
They create phishing sites that manipulate on-chain states immediately after transaction submission. 🕒

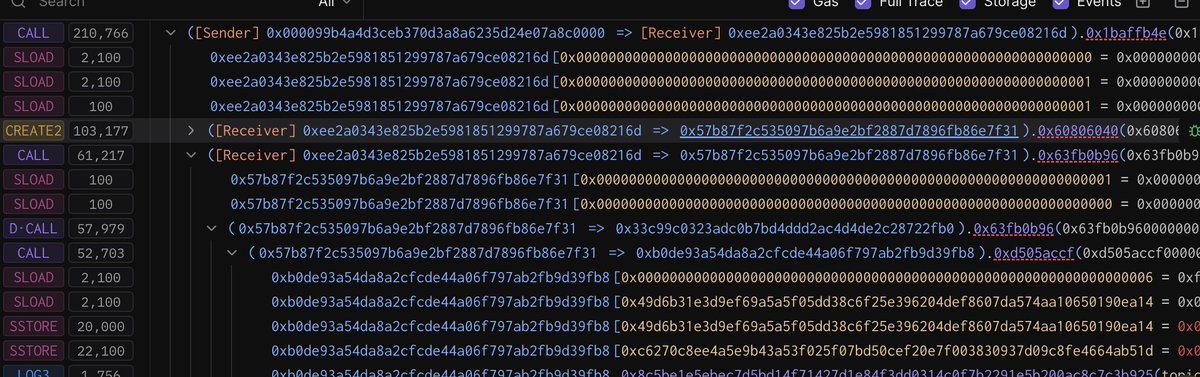
4/8 💻 The attack sequence:
• Phishing site initiates a "Claim" ETH transfer
• Wallet simulates tiny ETH receipt (0.000...0001 ETH)
• Backend modifies contract state
• Actual transaction drains wallet
• Phishing site initiates a "Claim" ETH transfer
• Wallet simulates tiny ETH receipt (0.000...0001 ETH)
• Backend modifies contract state
• Actual transaction drains wallet
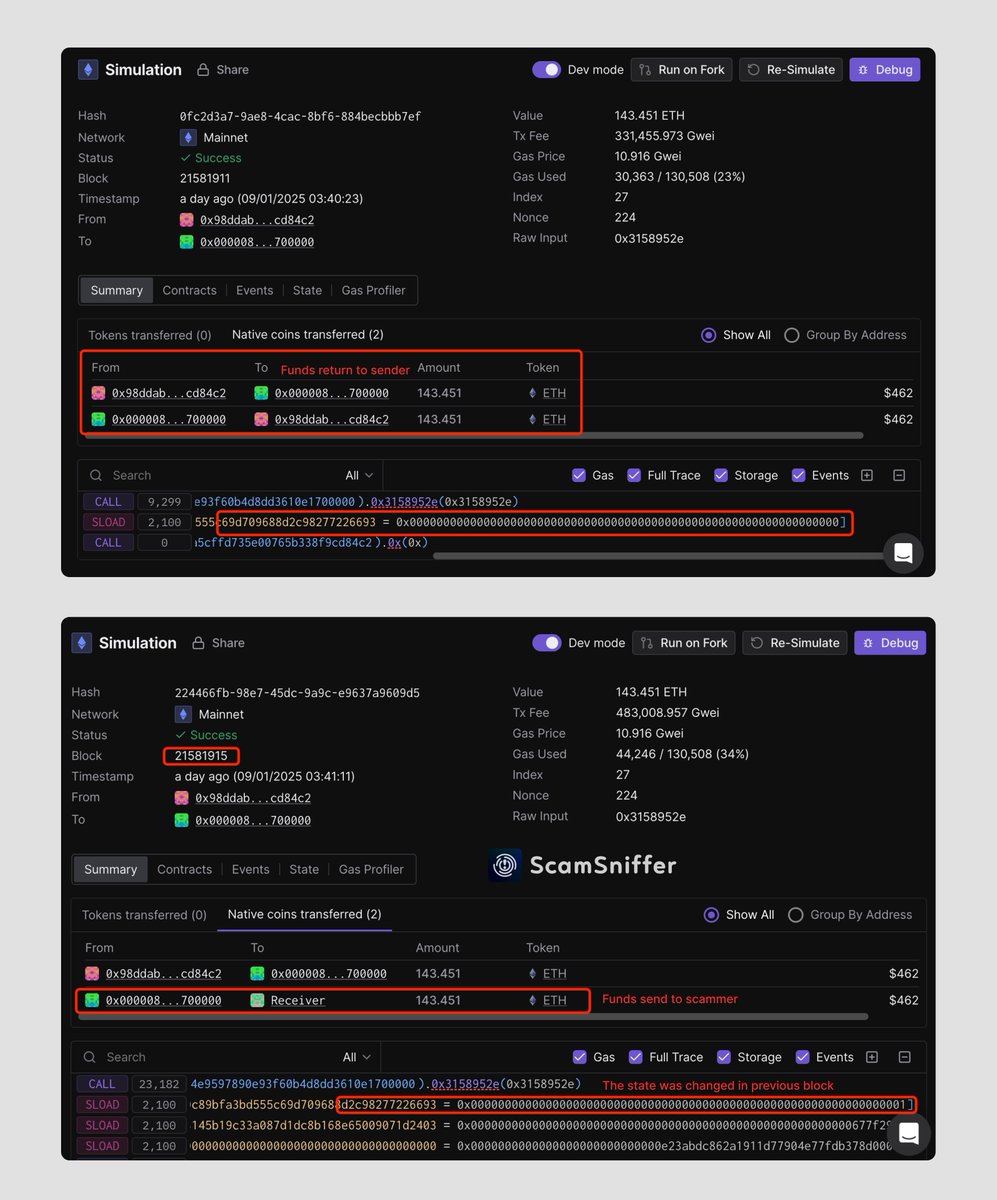
5/8 ⚡ Recent example analysis:
• Phishing site modified contract state
• Victim signed transaction ~30 seconds after state change
• Claim function executed
• Resulted in complete wallet drain
All appearing legitimate in simulation ⛓️
etherscan.io/tx/0x014321fba…
• Phishing site modified contract state
• Victim signed transaction ~30 seconds after state change
• Claim function executed
• Resulted in complete wallet drain
All appearing legitimate in simulation ⛓️
etherscan.io/tx/0x014321fba…
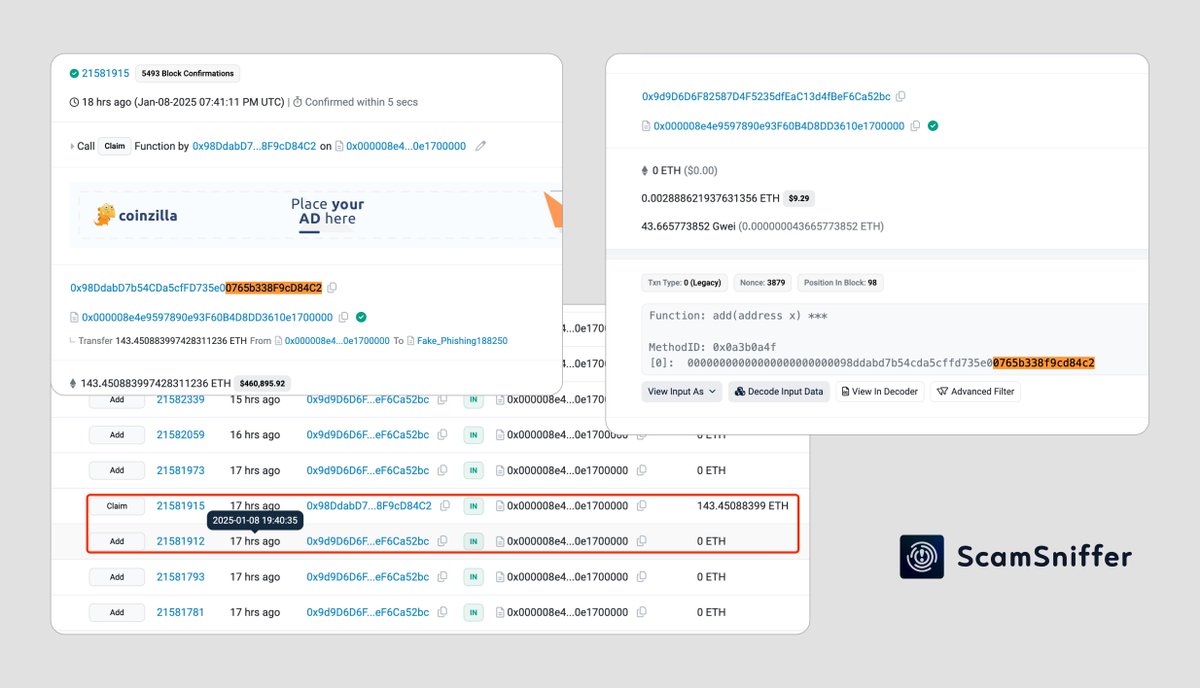
6/8 🛡️ Protection tips:
• Double-check transaction details
• Verify contract interactions
• Be suspicious of "free claim" offers
• Use trusted dApps only
🛡️ Protect your assets with ScamSniffer extension 🔒
• Double-check transaction details
• Verify contract interactions
• Be suspicious of "free claim" offers
• Use trusted dApps only
🛡️ Protect your assets with ScamSniffer extension 🔒
https://x.com/realScamSniffer/status/1875129987604644035
7/8 🔧 Wallet Optimization Suggestions:
• Dynamic refresh based on block time
• Force simulation refresh before signing
• Show simulation timestamps & block heights
• Integrate phishing contract blocklist
• Alert for outdated simulation results
• Dynamic refresh based on block time
• Force simulation refresh before signing
• Show simulation timestamps & block heights
• Integrate phishing contract blocklist
• Alert for outdated simulation results
8/8 ⚔️ This represents an advanced evolution in phishing attacks, exploiting trusted wallet features.
Always verify transactions through multiple sources and remain vigilant. 🔐
Read more 👇
drops.scamsniffer.io/transaction-si…
Always verify transactions through multiple sources and remain vigilant. 🔐
Read more 👇
drops.scamsniffer.io/transaction-si…
• • •
Missing some Tweet in this thread? You can try to
force a refresh