#OpenProbe🧵| Israeli spyware is targeting Arab smartphone users through deceptive sponsored advertisements on social media. Eekad’s investigation uncovers tens of thousands of such ads, systematically disseminated by pages operated from within Israel as part of a coordinated cyber campaign.
✔️Although these ads appear to be routine promotional content, they are, in fact, engineered to covertly compromise mobile devices and extract sensitive personal data, often without any user interaction or visible trace.
✔️This probe delves into the technical infrastructure behind the campaign, revealing the tactics used in its execution with such precision and widespread reach, targeting Arabs across social media.
✔️Although these ads appear to be routine promotional content, they are, in fact, engineered to covertly compromise mobile devices and extract sensitive personal data, often without any user interaction or visible trace.
✔️This probe delves into the technical infrastructure behind the campaign, revealing the tactics used in its execution with such precision and widespread reach, targeting Arabs across social media.

✔️Since 2022, several investigative reports have highlighted Israel’s use of spyware delivered through paid social media ads to target internet users.
✔️In April 2024, the Israeli newspaper Haaretz revealed that Israel had developed a hacking system known as "Aladdin," designed to push deceptive ads, including fake job listings, across social media platforms. These ads can breach users’ devices and extract sensitive data.
✔️Although Israeli authorities have attempted to downplay the system’s capabilities, cybersecurity experts warn that Aladdin can infect devices merely by displaying the ad, without requiring users to click on it.

✔️In April 2024, the Israeli newspaper Haaretz revealed that Israel had developed a hacking system known as "Aladdin," designed to push deceptive ads, including fake job listings, across social media platforms. These ads can breach users’ devices and extract sensitive data.
✔️Although Israeli authorities have attempted to downplay the system’s capabilities, cybersecurity experts warn that Aladdin can infect devices merely by displaying the ad, without requiring users to click on it.


✔️According to various media reports, Israel used this tactic, which cybersecurity experts refer to as malvertising—the practice of using seemingly legitimate online ads to deliver malicious software.
✔️These ads often appear harmless but contain hidden malware and malicious code that silently infect users’ devices without their knowledge or consent.
✔️Since 2023, malvertising has experienced significant growth, driven by advancements in AI and increasingly precise ad-targeting technologies.
✔️In many instances, such ads have functioned as sophisticated surveillance tools engineered to identify and extract data from selected users—a tactic commonly referred to in the cyber domain as Ad Intelligence (AdInt).



✔️These ads often appear harmless but contain hidden malware and malicious code that silently infect users’ devices without their knowledge or consent.
✔️Since 2023, malvertising has experienced significant growth, driven by advancements in AI and increasingly precise ad-targeting technologies.
✔️In many instances, such ads have functioned as sophisticated surveillance tools engineered to identify and extract data from selected users—a tactic commonly referred to in the cyber domain as Ad Intelligence (AdInt).


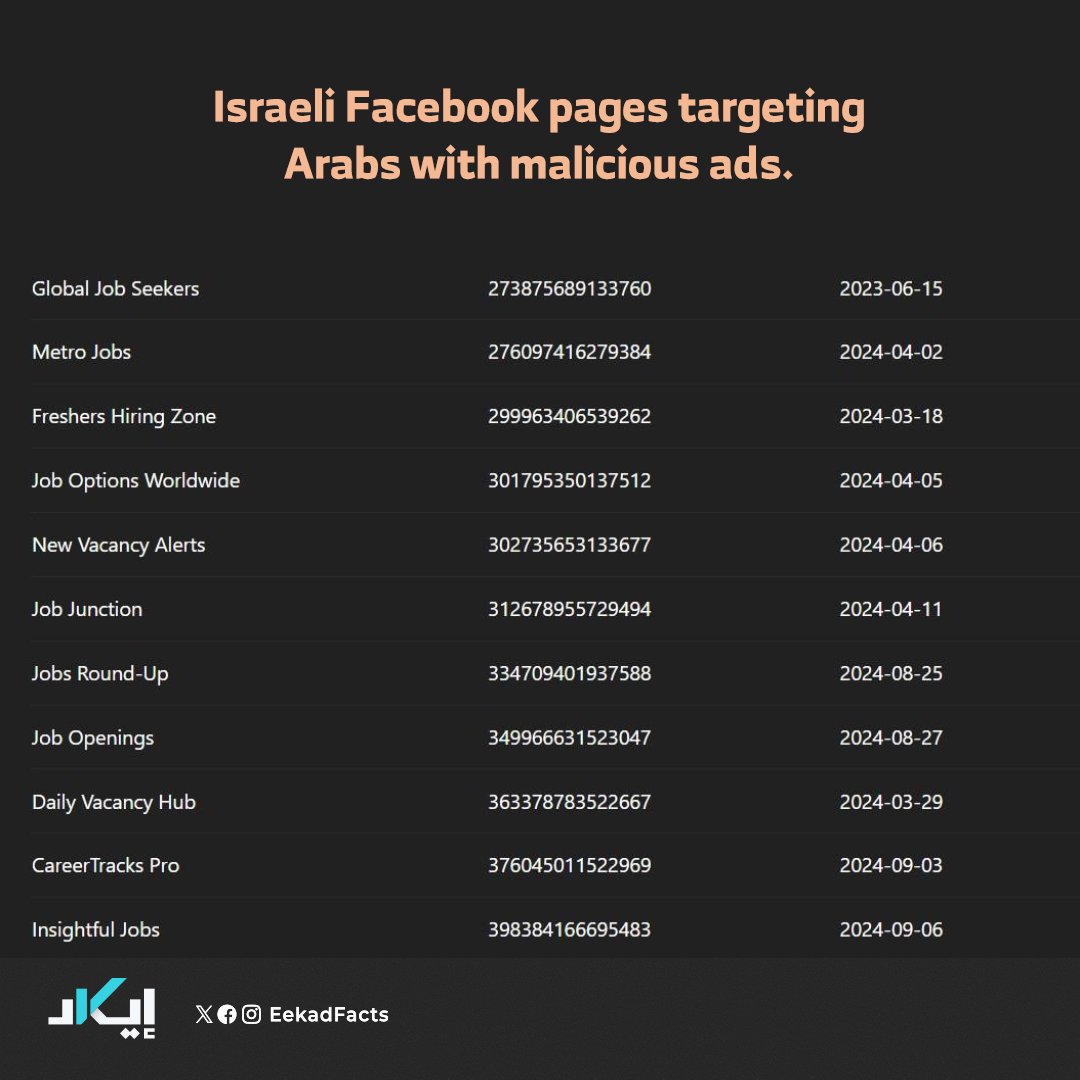

✔️Our investigation revealed that these pages and ads were widely disseminated across the Arab world. While some were tailored to target specific countries, others were designed to reach users across multiple Arab nations simultaneously, such as Egypt, Jordan, Lebanon, and Iraq. 
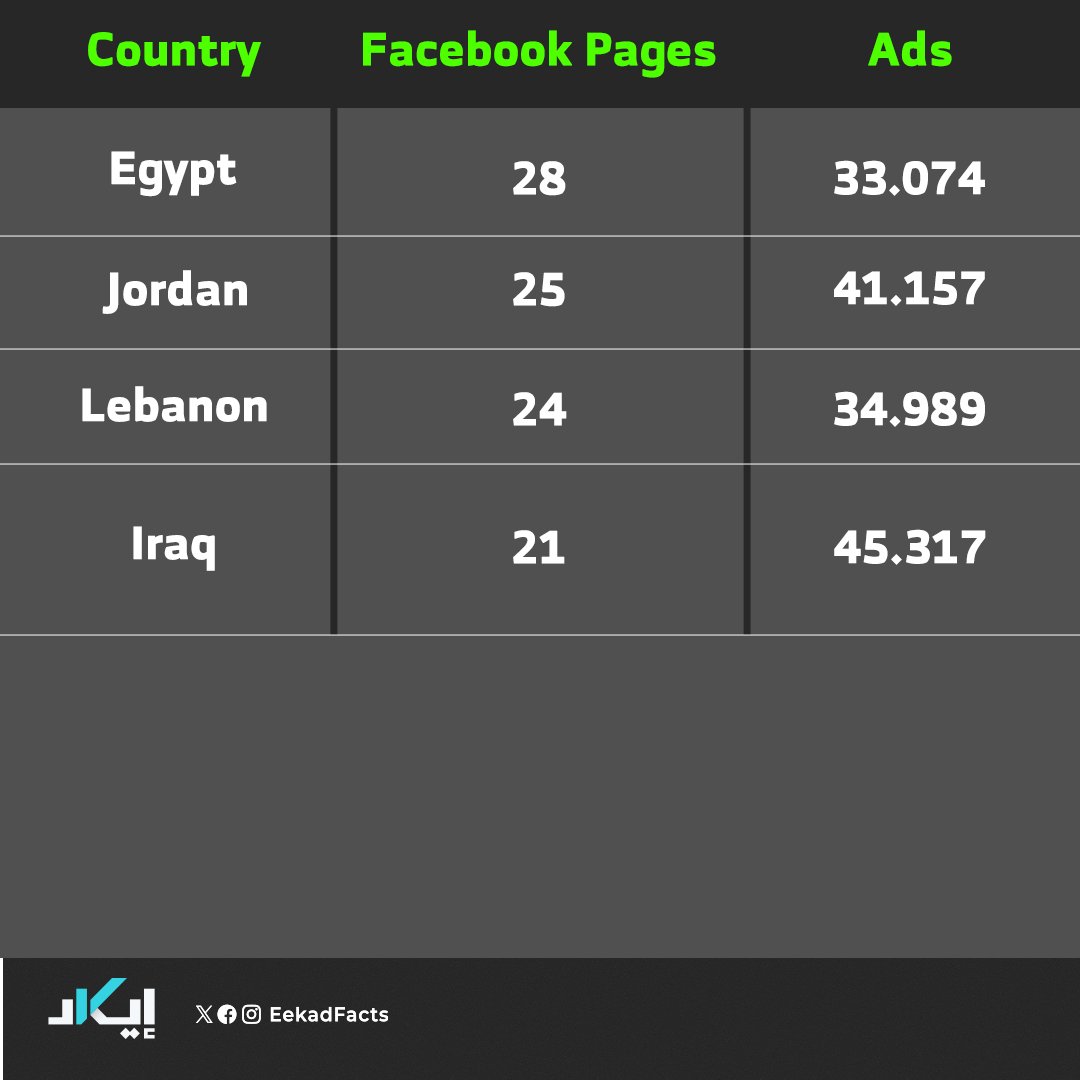
📌Our analysis of these pages and their associated ads uncovered several consistent patterns:
➡️All of the pages were operated from within Israel, with most created between 2024 and 2025 using fake identities.
➡️They shared a unified visual identity, featuring similar colors, logos, fonts, and overall design, which strongly suggested they originated from a single source and served a common purpose.
➡️Even the page names followed predictable patterns, often repeating specific keywords or adhering to similar naming structures.


➡️All of the pages were operated from within Israel, with most created between 2024 and 2025 using fake identities.
➡️They shared a unified visual identity, featuring similar colors, logos, fonts, and overall design, which strongly suggested they originated from a single source and served a common purpose.
➡️Even the page names followed predictable patterns, often repeating specific keywords or adhering to similar naming structures.



📌These similarities extended to the ad content, which consistently targeted financially vulnerable Arab users with enticing but deceptive offers, including:
➡️Job opportunities in Europe, the U.S., Japan, and Qatar.
➡️Openings in the military and immigration sectors.
➡️Fake online training programs.
➡️Large loans with no collateral required.


➡️Job opportunities in Europe, the U.S., Japan, and Qatar.
➡️Openings in the military and immigration sectors.
➡️Fake online training programs.
➡️Large loans with no collateral required.



✔️In addition to the previous similarities, specialized analysis software further confirmed that these pages were interconnected.
✔️These consistent patterns strongly suggest that they all originate from a single source and were created for a specific objective, prompting us to examine the ads and their associated links more closely.
❓So, what did our technical analysis of these Israeli-run ads and their associated domains unearth?
✔️These consistent patterns strongly suggest that they all originate from a single source and were created for a specific objective, prompting us to examine the ads and their associated links more closely.
❓So, what did our technical analysis of these Israeli-run ads and their associated domains unearth?

✔️Our technical analysis also showed that the links accessed after users clicked on the ads operate within groups that share the same name servers, which are systems that route web traffic to the intended site.
✔️For instance, many links shared the name servers mark.ns.cloudflare.com and dns1.p01.nsone.net.


✔️For instance, many links shared the name servers mark.ns.cloudflare.com and dns1.p01.nsone.net.



✔️The repeated use of the same name servers strongly indicates that the websites linked through these ads share key structural traits. First, they appear to be centrally managed—likely owned or operated by a single entity or a tightly connected network.
✔️Second, they rely on a uniform infrastructure, allowing the operators to easily control, scale, and update campaigns by swapping out links quickly and redeploying content without the need to redesign or reconfigure servers.

✔️Second, they rely on a uniform infrastructure, allowing the operators to easily control, scale, and update campaigns by swapping out links quickly and redeploying content without the need to redesign or reconfigure servers.


✔️However, Eekad’s investigation uncovered even more concerning insights. Upon examining hundreds of links embedded in the ads, it became evident that many directed users to a coordinated network of malicious websites.
✔️These domains appeared to have been specifically designed to entice users and compromise their devices with harmful software immediately upon access, without requiring any further interaction.
✔️Notable examples of such domains include morehackz.com, frantip.com, and wysing.com, among others.



✔️These domains appeared to have been specifically designed to entice users and compromise their devices with harmful software immediately upon access, without requiring any further interaction.
✔️Notable examples of such domains include morehackz.com, frantip.com, and wysing.com, among others.




📌Further investigation revealed that these websites and their associated links consistently used well-established cyberattack tactics, including:
1️⃣Short-term SSL certificates: These create the illusion of a secure website, tricking users into trusting the malicious domain.
2️⃣Obfuscation techniques: Designed to evade antivirus software and other security tools.
3️⃣Cloaked redirection: Users clicking on seemingly harmless buttons like “Continue” or “View Details” unknowingly triggered the download of malware-infected files.

1️⃣Short-term SSL certificates: These create the illusion of a secure website, tricking users into trusting the malicious domain.
2️⃣Obfuscation techniques: Designed to evade antivirus software and other security tools.
3️⃣Cloaked redirection: Users clicking on seemingly harmless buttons like “Continue” or “View Details” unknowingly triggered the download of malware-infected files.


✔️Moreover, our analysis found that these malicious links typically follow a structured six-stage sequence, closely aligned with the internationally recognized MITRE ATT&CK framework.
✔️This framework maps the tactics and techniques used by threat actors throughout the entire cyberattack lifecycle—from initial intrusion to final payload delivery.

✔️This framework maps the tactics and techniques used by threat actors throughout the entire cyberattack lifecycle—from initial intrusion to final payload delivery.


📌In summary, the six stages aim to:
➡️Attract the target and bypass security defenses.
➡️Remain hidden and maintain access, even if a domain or IP address is blocked.
➡️Silently install additional tools and extract data from the device without the user's awareness.

➡️Attract the target and bypass security defenses.
➡️Remain hidden and maintain access, even if a domain or IP address is blocked.
➡️Silently install additional tools and extract data from the device without the user's awareness.


📌Key Takeaways from Eekad’s Investigation:
➡️Eekad uncovered 61 fake Facebook pages operated from within Israel, which collectively deployed over 140,000 malicious ads targeting Meta users across the Arab world.
➡️These ads and pages shared a consistent visual identity and repeatedly used familiar lures, such as job offers, loan promotions, and fake online courses, to entice users into clicking malicious links.
➡️Our analysis revealed that these links operated within a centralized infrastructure, relying on shared name servers and a system designed for rapid link replacement, enabling large-scale, coordinated cyberattacks.
➡️The ads led users to malicious websites capable of bypassing security systems, extracting data, and installing harmful files, often without the user’s knowledge.
📌These findings point to a highly coordinated malvertising campaign targeting Meta platform users in the Arab region. The campaign operates through a structured technical network designed to infect as many devices as possible, at minimal cost and maximum efficiency.
➡️Eekad uncovered 61 fake Facebook pages operated from within Israel, which collectively deployed over 140,000 malicious ads targeting Meta users across the Arab world.
➡️These ads and pages shared a consistent visual identity and repeatedly used familiar lures, such as job offers, loan promotions, and fake online courses, to entice users into clicking malicious links.
➡️Our analysis revealed that these links operated within a centralized infrastructure, relying on shared name servers and a system designed for rapid link replacement, enabling large-scale, coordinated cyberattacks.
➡️The ads led users to malicious websites capable of bypassing security systems, extracting data, and installing harmful files, often without the user’s knowledge.
📌These findings point to a highly coordinated malvertising campaign targeting Meta platform users in the Arab region. The campaign operates through a structured technical network designed to infect as many devices as possible, at minimal cost and maximum efficiency.
• • •
Missing some Tweet in this thread? You can try to
force a refresh