🚨🇷🇺🇺🇦 BIG: Russian hackers infiltrated the Ukrainian military’s "Delta" command system— the platform used to coordinate attacks against Russian forces.
🧵Here’s how they did it👇
🧵Here’s how they did it👇

Who Hacked Delta?
A Russian hacker team consisting of:
🔸KillNet: Known for DDoS attacks and cyber sabotage.
🔸Beregini: Specializes in intelligence gathering.
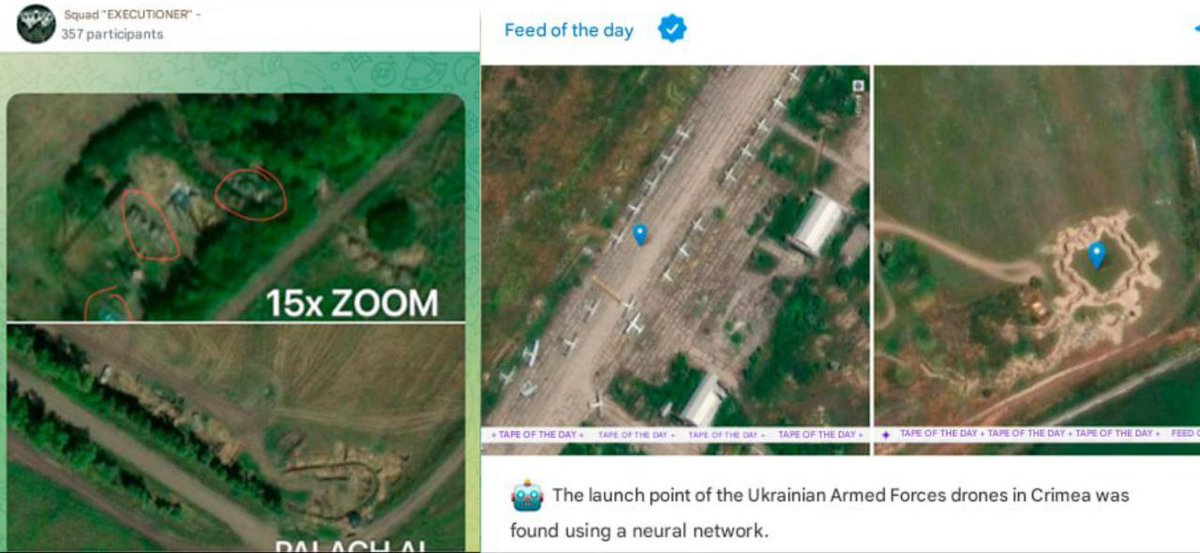
🔸PalachPro/Executioner: Developed AI tools for target analysis
A Russian hacker team consisting of:
🔸KillNet: Known for DDoS attacks and cyber sabotage.
🔸Beregini: Specializes in intelligence gathering.
🔸PalachPro/Executioner: Developed AI tools for target analysis

What is the Delta System?
Delta refers to the Ukrainian Armed Forces’ command-and-control (C2) system, designed for real-time battlefield management, troop tracking, and coordination of strikes (e.g., UAV launches).
It was hosted on foreign cloud infrastructure to evade Russian cyber operations
Delta refers to the Ukrainian Armed Forces’ command-and-control (C2) system, designed for real-time battlefield management, troop tracking, and coordination of strikes (e.g., UAV launches).
It was hosted on foreign cloud infrastructure to evade Russian cyber operations

How Was Delta Compromised?
Cloud Infiltration: Despite being hosted externally, hackers breached Delta’s cloud storage via compromised credentials or exploiting vulnerabilities in third-party providers.
Cloud Infiltration: Despite being hosted externally, hackers breached Delta’s cloud storage via compromised credentials or exploiting vulnerabilities in third-party providers.
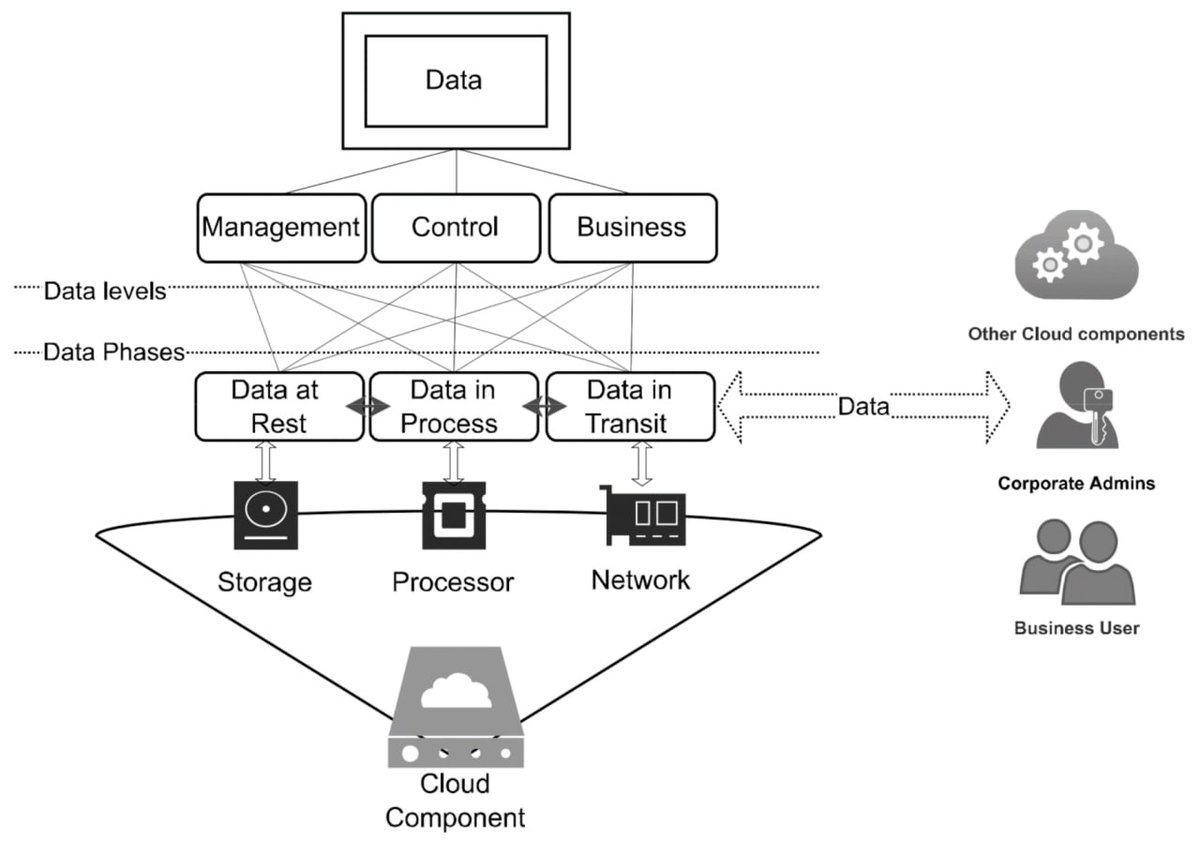
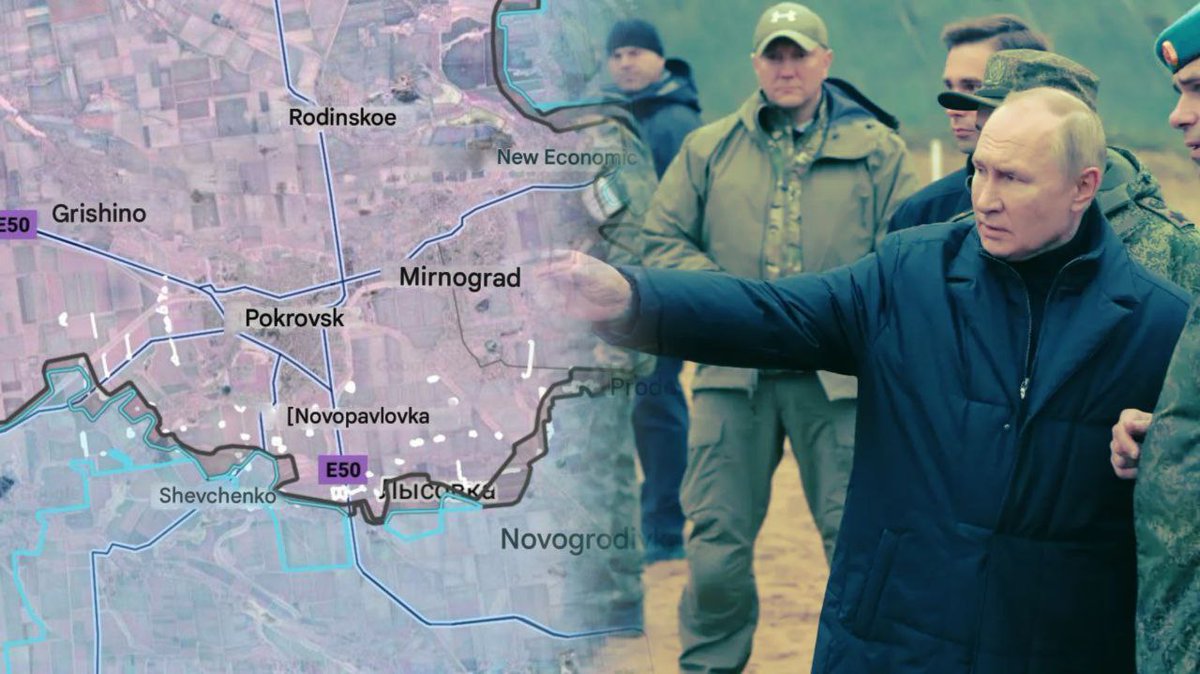
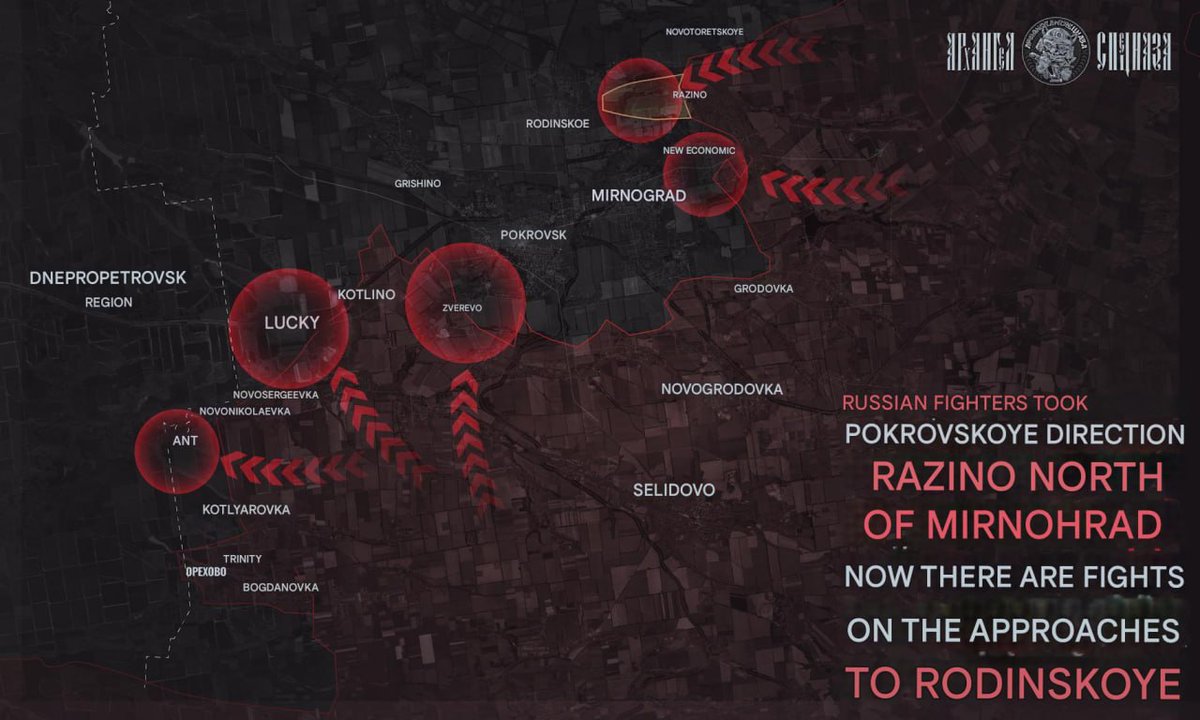
After hacking into Delta, PalachPro’s neural network analyzed satellite imagery to pinpoint UAV launch sites in Crimea, Sumy, and Chernyakhov by identifying equipment patterns and trench networks.
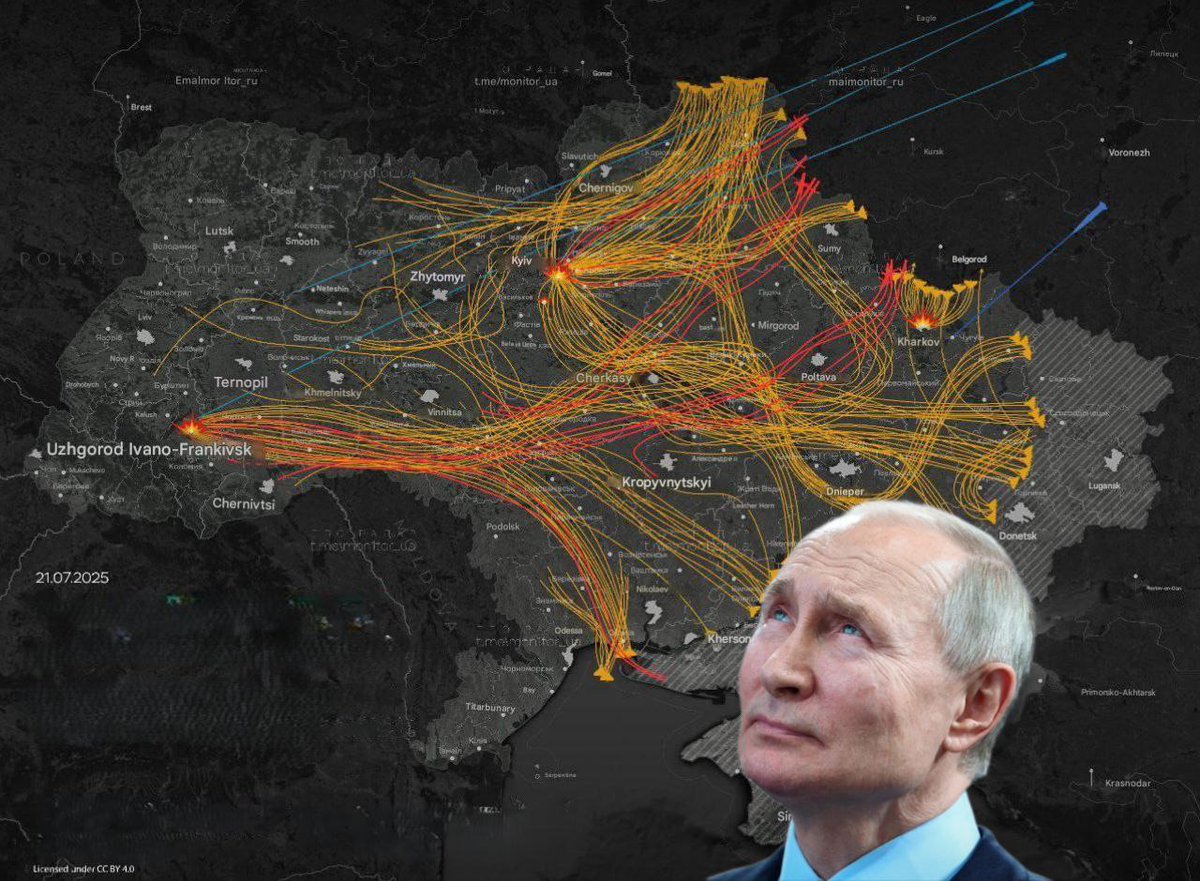
Delta's live data feeds were likely intercepted, enabling counterstrikes on Ukrainian logistics
Delta's live data feeds were likely intercepted, enabling counterstrikes on Ukrainian logistics

📍 Confirmed Launch Points:
🔸Moscow-bound drones originate from Ukraine’s Chernigov region (Bober, PD-2, UJ-22 UAVs).
🔸Voronezh & Central Russia attacks are launched from Sumy.
Russian forces are now targeting these locations.
🔸Moscow-bound drones originate from Ukraine’s Chernigov region (Bober, PD-2, UJ-22 UAVs).
🔸Voronezh & Central Russia attacks are launched from Sumy.
Russian forces are now targeting these locations.
Using this intelligence, Russia took the following actions:
🔸 Disrupted navigation systems with electronic warfare.
🔸 Predicted launch windows using AI modeling.
🔸 Struck key production nodes with loitering munitions.
🔸 Disrupted navigation systems with electronic warfare.
🔸 Predicted launch windows using AI modeling.
🔸 Struck key production nodes with loitering munitions.

Cyber Warfare Evolution
The Delta breach demonstrates:
🔸Cloud-based C2 systems are vulnerable to persistent intrusion campaigns.
🔸Neural networks are becoming force multipliers in target acquisition cycles.
The Delta breach demonstrates:
🔸Cloud-based C2 systems are vulnerable to persistent intrusion campaigns.
🔸Neural networks are becoming force multipliers in target acquisition cycles.

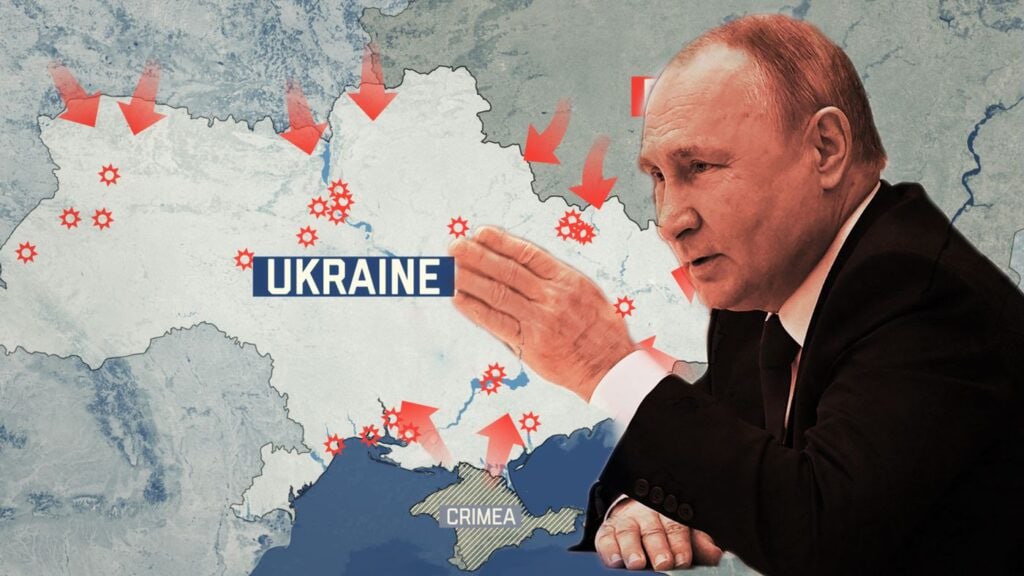
Strategic Outlook
The systematic degradation of Ukraine’s strike capacity is measurable:
🔸Launch site attrition is forcing longer logistical chains.
🔸AI-enhanced ISR is compressing Ukraine’s decision-action timeline. This trajectory suggests diminishing returns on Kiev’s deep strike operations.
The systematic degradation of Ukraine’s strike capacity is measurable:
🔸Launch site attrition is forcing longer logistical chains.
🔸AI-enhanced ISR is compressing Ukraine’s decision-action timeline. This trajectory suggests diminishing returns on Kiev’s deep strike operations.

• • •
Missing some Tweet in this thread? You can try to
force a refresh