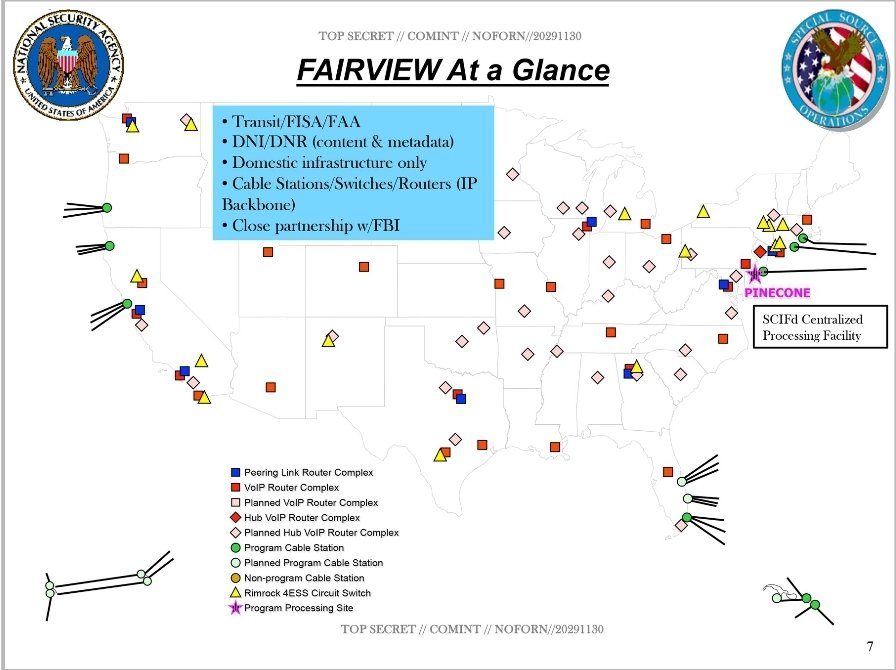
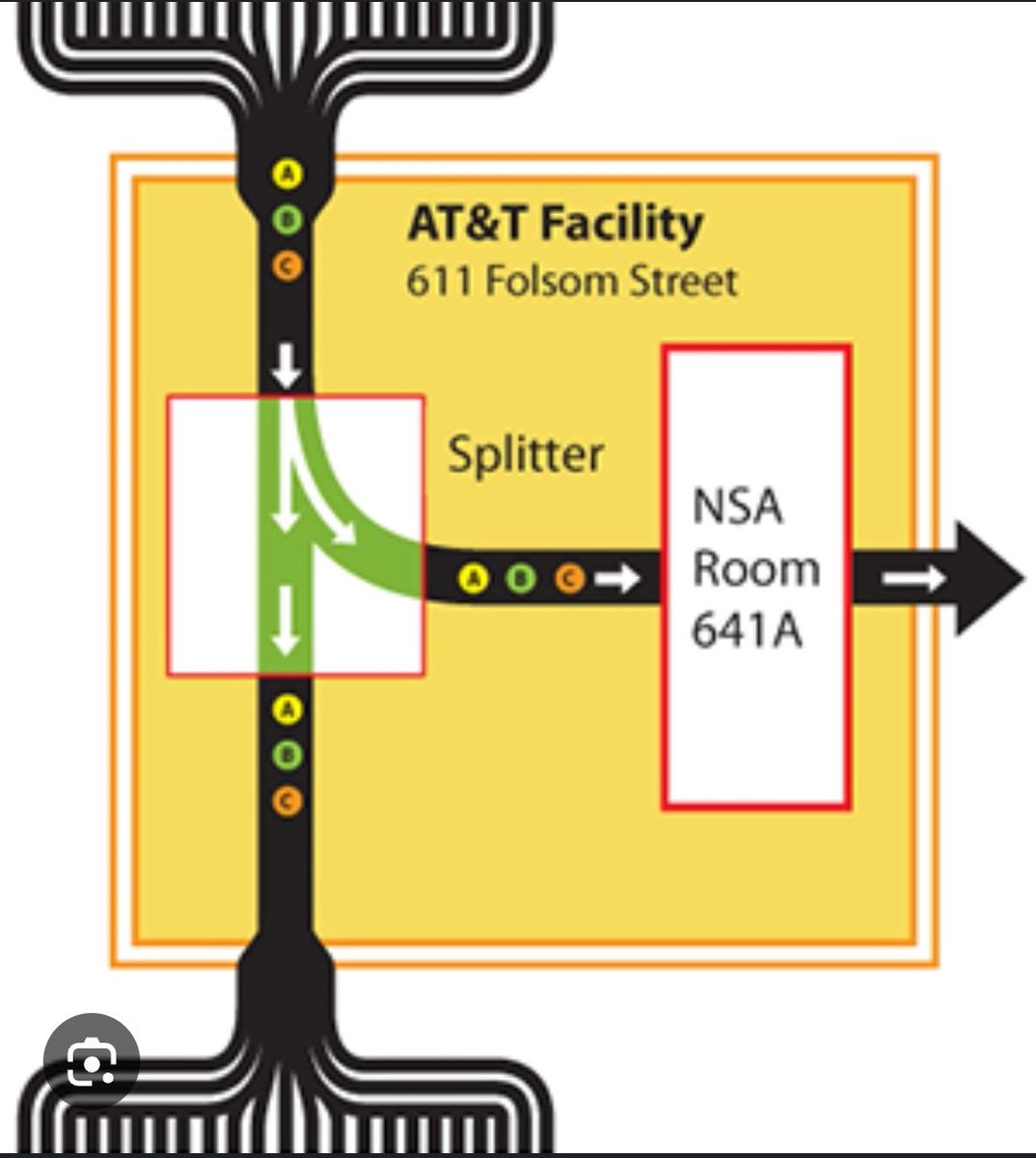
Yes, @PeterBernegger
CrowdStrike is ABSOLUTELY part of the picture
Also, I would offer what almost no one talks about:
The deeper layer of global domination, power, and control
Access 🔑
The web of a power conglomerate with tentacles wrapped around the neck of our National Security
Access = Control
Control = Power
Power = Influence
Influence = Outcome
Control the identity layer, and you control the system
You will want to bookmark this 🧵
CrowdStrike is ABSOLUTELY part of the picture
Also, I would offer what almost no one talks about:
The deeper layer of global domination, power, and control
Access 🔑
The web of a power conglomerate with tentacles wrapped around the neck of our National Security
Access = Control
Control = Power
Power = Influence
Influence = Outcome
Control the identity layer, and you control the system
You will want to bookmark this 🧵
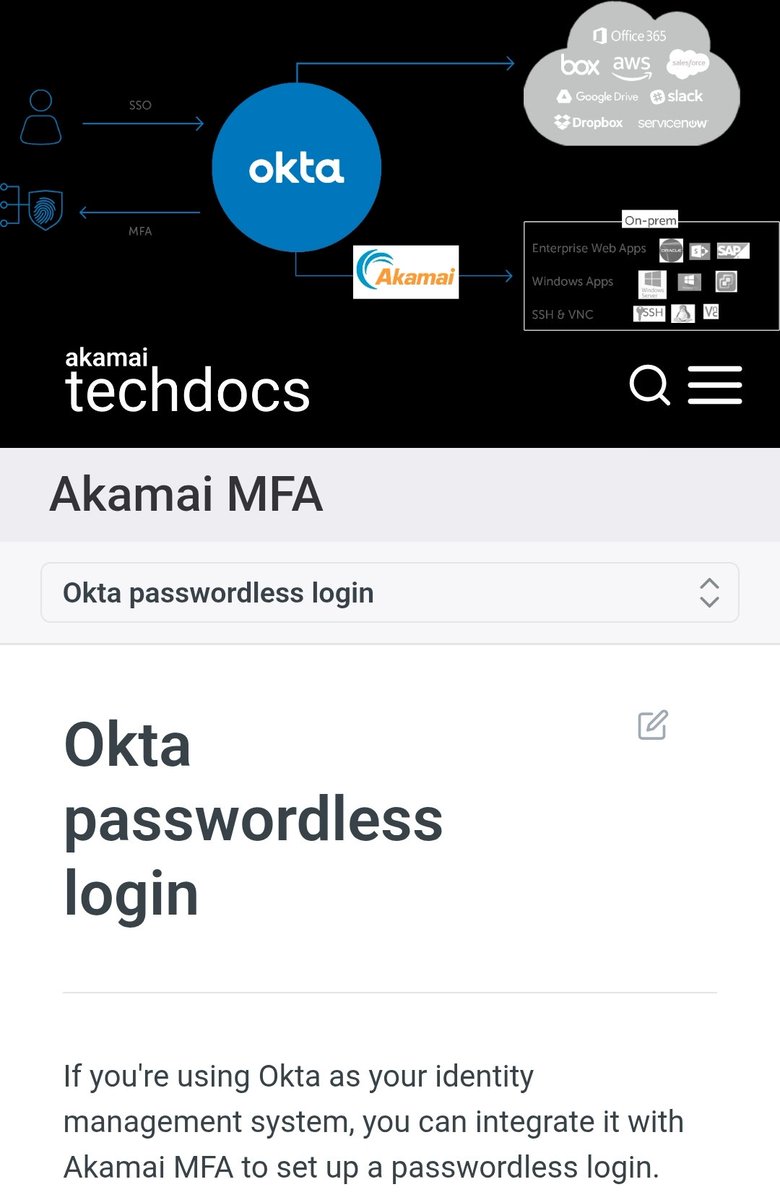
(1.)Founded in 2009 by Todd McKinnon and Frederic Kerrest, both of (intelligence agencies adjacent) Salesforce, and briefly known as SaaSure, Okta is a cloud-based identity and access management (IAM) platform that acts as a central hub for authentication and authorization, both On-prem and remote access
👉That access spans local, state, and federal government, the entire identity- perimeter control stack... from election vendors (Dominion, ES&S, KNOWiNK, Konnech, etc.)...
...to pollpads, CradlePoint routers, Voter Registration Election Management Systems, the entirety of elections


👉That access spans local, state, and federal government, the entire identity- perimeter control stack... from election vendors (Dominion, ES&S, KNOWiNK, Konnech, etc.)...
...to pollpads, CradlePoint routers, Voter Registration Election Management Systems, the entirety of elections



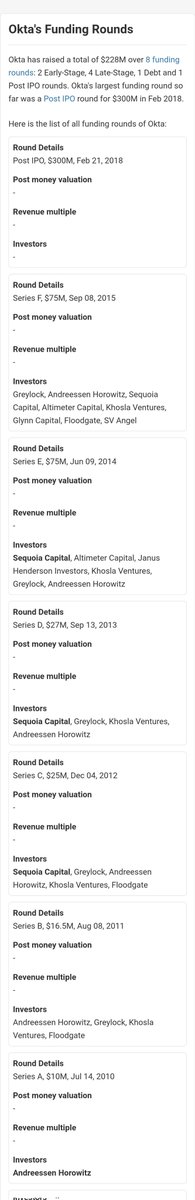
Seeded to the tune of $229M by the likes of:
👉Andreessen Horowitz(a16z)
👉Sequoia Capital
👉Greylock Partners
...and a $40M line of credit from Silicon Valley Bank
Then... the network ties
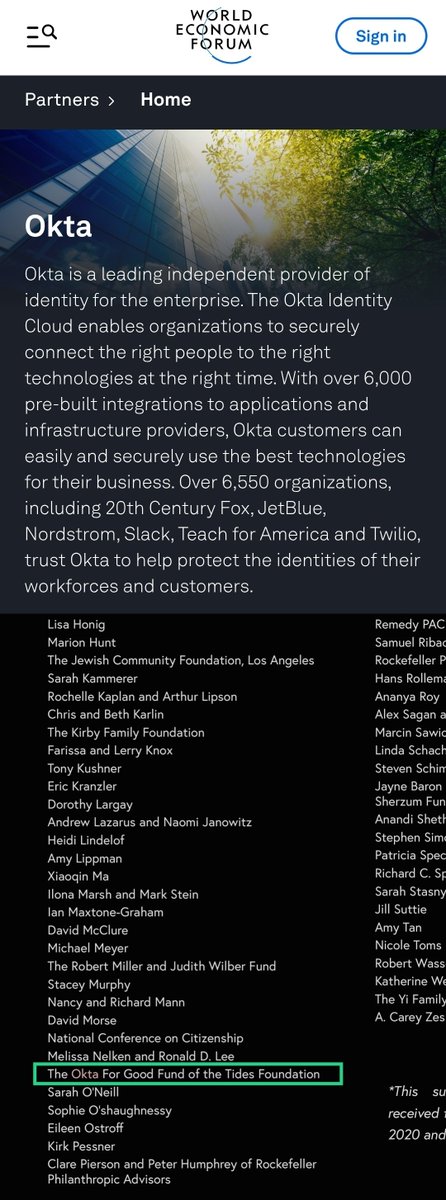
👉WEF partner
👉“Okta For Good” aligned with Soros-linked Tides Foundation & Open Society Foundations
(The same Tides Foundation that shared office space with Dominion in Toronto)
👉Partnered with USAID & UN’s ID2020 digital identity initiative
These aren’t random partnerships
They’re the same network shaping global identity control



👉Andreessen Horowitz(a16z)
👉Sequoia Capital
👉Greylock Partners
...and a $40M line of credit from Silicon Valley Bank
Then... the network ties
👉WEF partner
👉“Okta For Good” aligned with Soros-linked Tides Foundation & Open Society Foundations
(The same Tides Foundation that shared office space with Dominion in Toronto)
👉Partnered with USAID & UN’s ID2020 digital identity initiative
These aren’t random partnerships
They’re the same network shaping global identity control


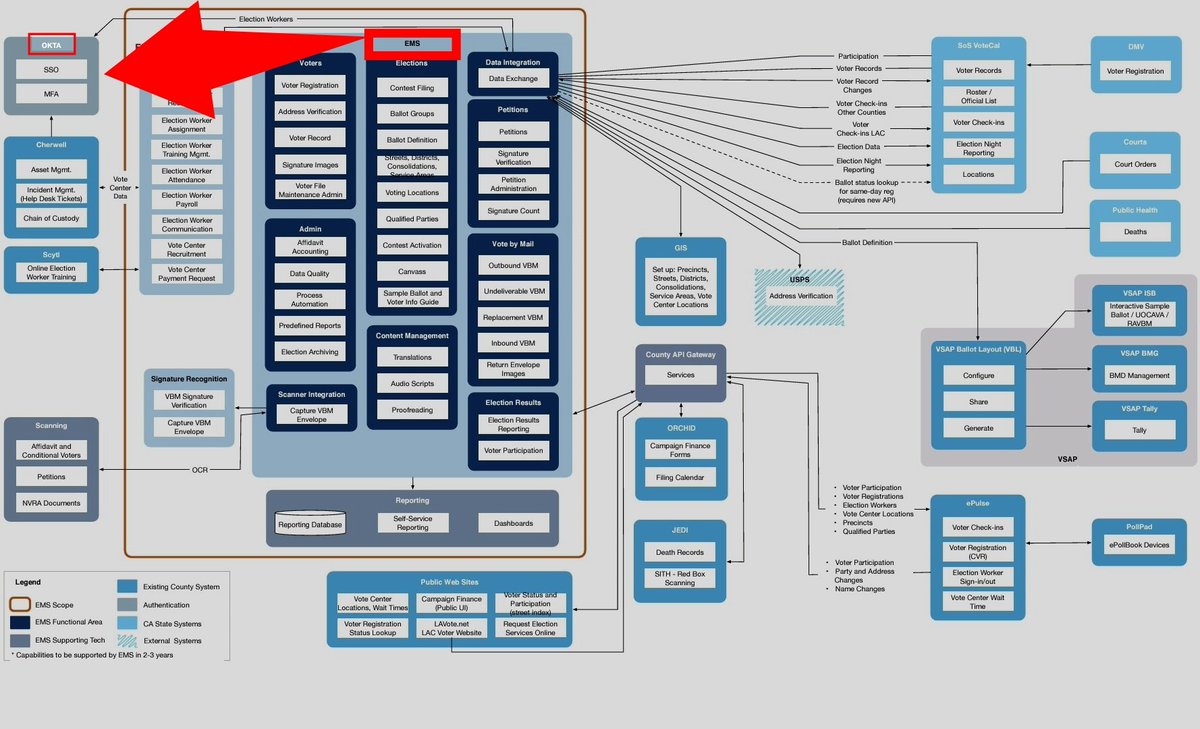
Okta isn't just a sign-on integration link
It’s a centralized federated identity choke-point
Once it’s wired into a system, it becomes part of a more broadly shared authentication web where a single compromise can cascade across every linked platform, agency, and vendor
In effect, integration = assimilation into a shared access spine, where one breach can fan out laterally through the entire connected ecosystem
One credential vault = one control plane = countless systems now tethered together
With deep integrations into the perimeter control cartel:
👉CrowdStrike
👉Akamai
👉Palo Alto Networks
👉Solar Winds
👉Cloudflare
👉Barracuda Networks
...and sitting on top as the leader in the identity access infrastructure marketplace, almost all other IAM/SSO systems are compatible and integrate them into their ecosystem
Tie all of them together through Okta access tentacles, and you’ve built the master choke-point for the modern internet
The literal *Oktapus*



It’s a centralized federated identity choke-point
Once it’s wired into a system, it becomes part of a more broadly shared authentication web where a single compromise can cascade across every linked platform, agency, and vendor
In effect, integration = assimilation into a shared access spine, where one breach can fan out laterally through the entire connected ecosystem
One credential vault = one control plane = countless systems now tethered together
With deep integrations into the perimeter control cartel:
👉CrowdStrike
👉Akamai
👉Palo Alto Networks
👉Solar Winds
👉Cloudflare
👉Barracuda Networks
...and sitting on top as the leader in the identity access infrastructure marketplace, almost all other IAM/SSO systems are compatible and integrate them into their ecosystem
Tie all of them together through Okta access tentacles, and you’ve built the master choke-point for the modern internet
The literal *Oktapus*


Note a few of the operators with pipelines to:
○ Foreign intelligence
○ U.S. election system access
○ CCP-linked institutions
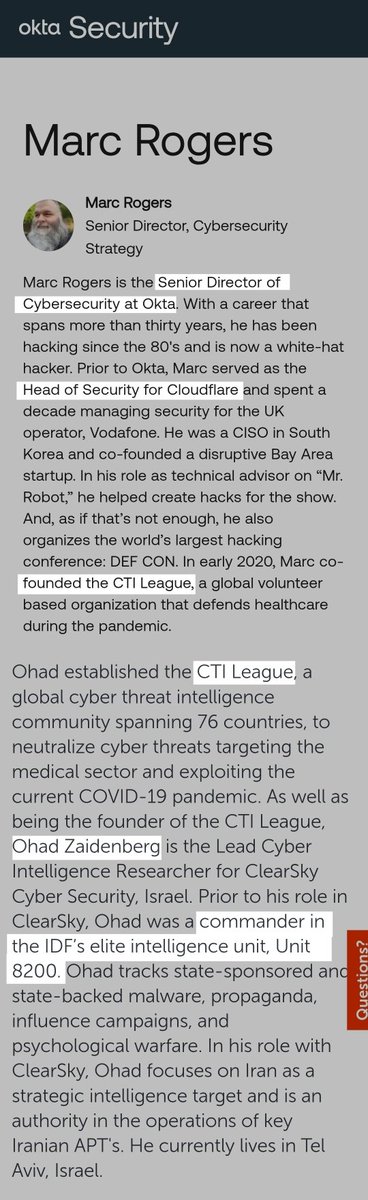
👉 Mark Rogers -
Veteran hacker and former Head of Security for Cloudflare, organizer of DEFCON, Cofounder of the CTI League, along with IDF Unit 8200 Command Ohad Zaidenberg, in 2020
👉 Robert Dixon -
Okta board member of Georgia Tech affiliation - Georgia Tech, who partnered up with Smartmatic and has had access to live election environments, DHS adjacent cyber initiatives ((see June 2019 detail )
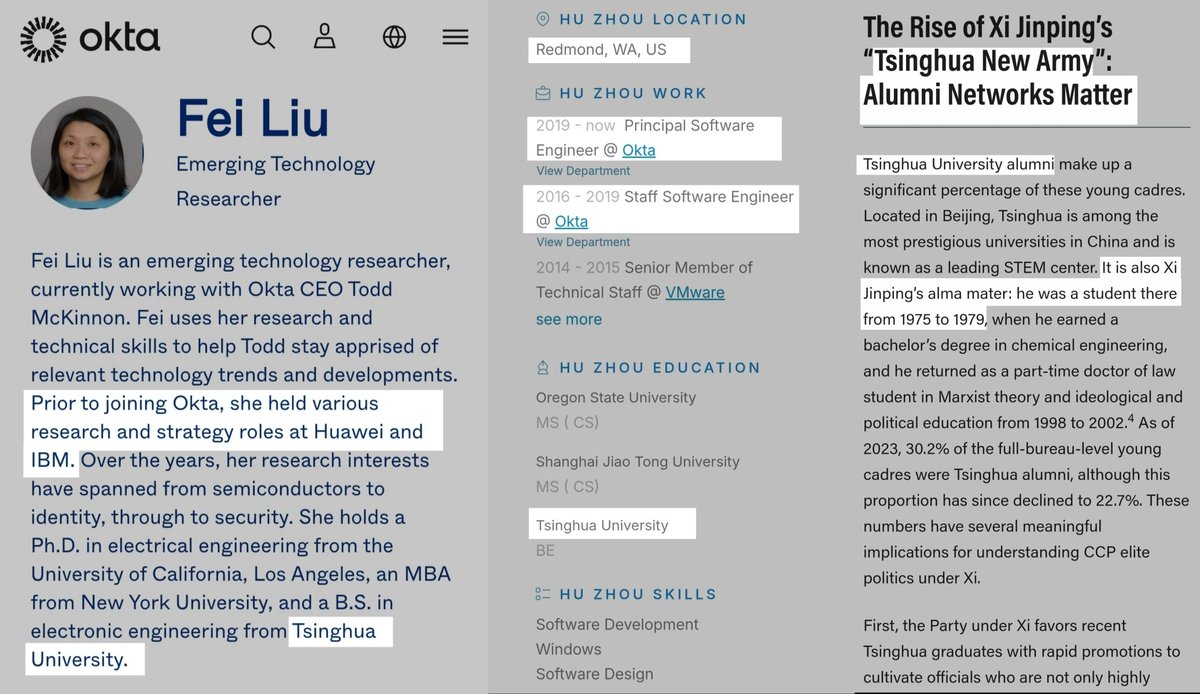
👉 Tsinghua University -
Alumni from Xi Jinping's alma mater within engineering and development lines with ties to CCP and Huawei
Coincidence?
No, it's convergence...
...of big tech, foreign intelligence, and election infrastructure
Meeting at the identity choke-point


○ Foreign intelligence
○ U.S. election system access
○ CCP-linked institutions
👉 Mark Rogers -
Veteran hacker and former Head of Security for Cloudflare, organizer of DEFCON, Cofounder of the CTI League, along with IDF Unit 8200 Command Ohad Zaidenberg, in 2020
👉 Robert Dixon -
Okta board member of Georgia Tech affiliation - Georgia Tech, who partnered up with Smartmatic and has had access to live election environments, DHS adjacent cyber initiatives ((see June 2019 detail )
👉 Tsinghua University -
Alumni from Xi Jinping's alma mater within engineering and development lines with ties to CCP and Huawei
Coincidence?
No, it's convergence...
...of big tech, foreign intelligence, and election infrastructure
Meeting at the identity choke-point

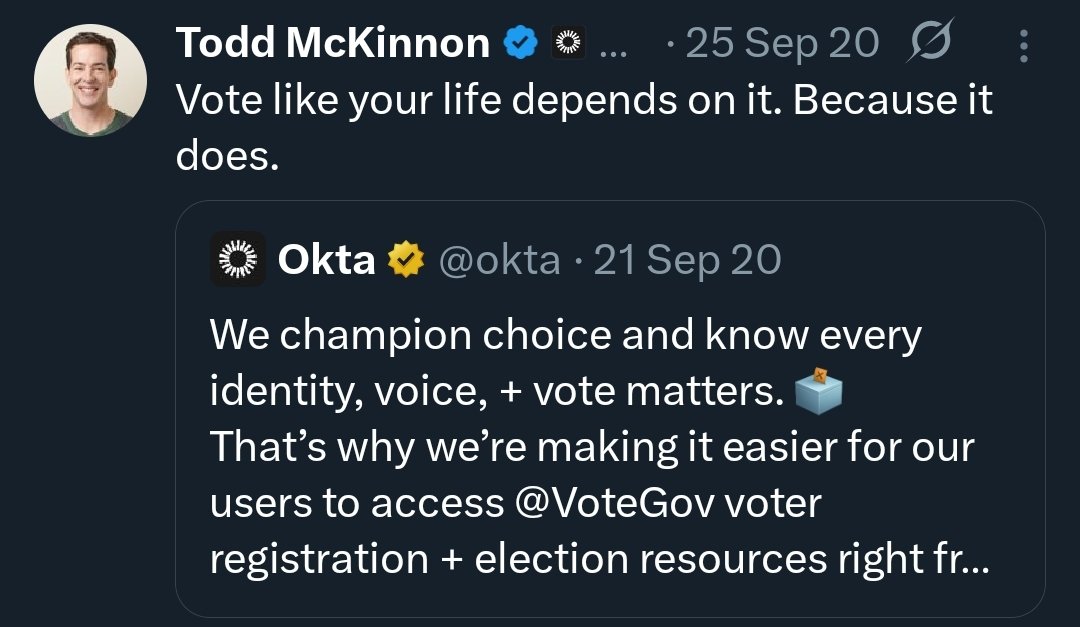
In the lead-up to the 2020 election, Okta added an integration link to
And speaking of "operators"...
...this Chief Executive seems like EXACTLY the right one to have at the helm of a network that gatekeeps the identity access layer for electionsvote.gov



And speaking of "operators"...
...this Chief Executive seems like EXACTLY the right one to have at the helm of a network that gatekeeps the identity access layer for electionsvote.gov


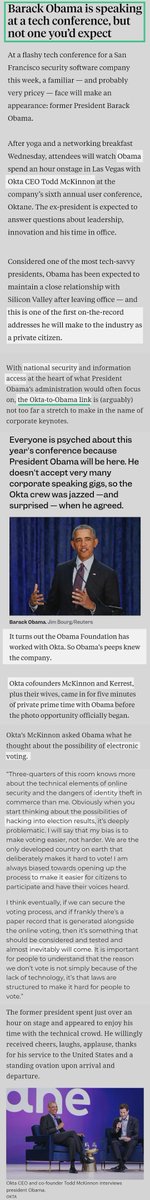
Okta's tech conference, "Oktane18," in Las Vegas, featured a guest spotlight appearance from none other than CIA Barry, himself
Why would Obama have done a keynote speaking arrangement with the CEO of Okta in 2018?🤔
Oh, because they had a working relationship through his Foundation, for one
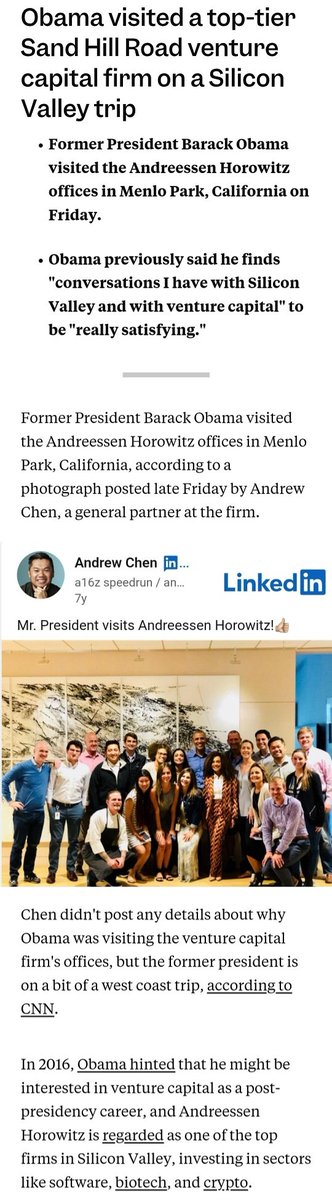
...and he made time afterward to visit who?
Andreessen Horowitz


Why would Obama have done a keynote speaking arrangement with the CEO of Okta in 2018?🤔
Oh, because they had a working relationship through his Foundation, for one
...and he made time afterward to visit who?
Andreessen Horowitz

Speaking of CIA
👉 USAID/Soros linked Okta implementation in July 2020 just 4 months before the election -
Approved by Haspel
👉 April 2021, just 5 months after the election, "Moved to Schoox, adjusted dates, deleted sharepoint file" - Burns approval

👉 USAID/Soros linked Okta implementation in July 2020 just 4 months before the election -
Approved by Haspel
👉 April 2021, just 5 months after the election, "Moved to Schoox, adjusted dates, deleted sharepoint file" - Burns approval
https://x.com/PeterBernegger/status/1955411937342394742?t=eIAkIHS4aHDsx1mB5PsDAw&s=19

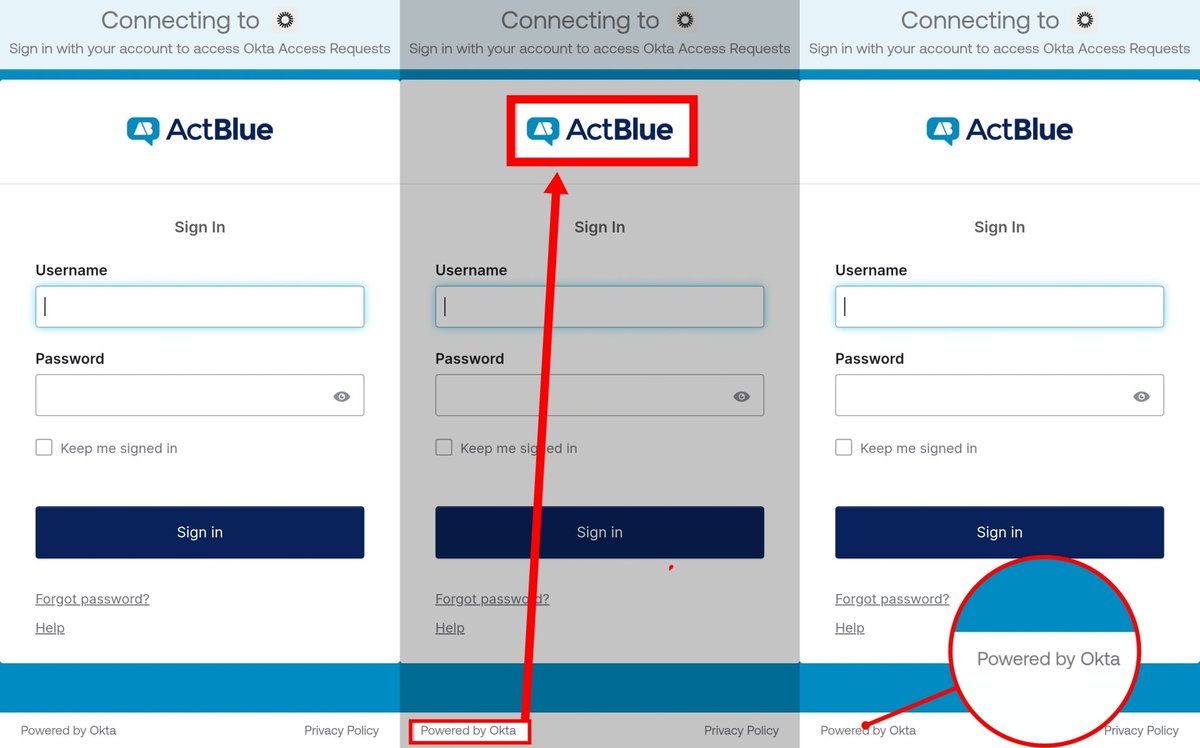
🚨Okta + ActBlue🚨
The identity layer that could enable mortgage laundering
ActBlue is an Okta tenant
...meaning every admin, contractor, API connection, and federated partner passes through Okta’s authentication layer
When Okta sits at the hub, the spokes can connect anywhere ActBlue links its identity to:
👉Banking portals
👉Loan servicing platforms
👉Real estate or property management software
👉CRM & donor systems with embedded credit/property data
With high-privilege Okta access (compromised or insider):
👉Mortgage origination or servicing accounts could be accessed without hacking those systems directly
👉API connections could be abused to pull property data, seed false records, or push transactions disguised as legitimate disbursements
👉Cross-tenant pivots can link ActBlue to partner PACs or shell nonprofits with mortgage system access
Okta’s trust link does the bridgework
👉Okta super-admins can alter or delete login records, masking the origin of fraudulent transactions.
If mortgage fraud was used as a laundering vector for political funds, Okta’s role wouldn’t be peripheral, it would be the authentication gateway, making it all invisible in the downstream logs

The identity layer that could enable mortgage laundering
ActBlue is an Okta tenant
...meaning every admin, contractor, API connection, and federated partner passes through Okta’s authentication layer
When Okta sits at the hub, the spokes can connect anywhere ActBlue links its identity to:
👉Banking portals
👉Loan servicing platforms
👉Real estate or property management software
👉CRM & donor systems with embedded credit/property data
With high-privilege Okta access (compromised or insider):
👉Mortgage origination or servicing accounts could be accessed without hacking those systems directly
👉API connections could be abused to pull property data, seed false records, or push transactions disguised as legitimate disbursements
👉Cross-tenant pivots can link ActBlue to partner PACs or shell nonprofits with mortgage system access
Okta’s trust link does the bridgework
👉Okta super-admins can alter or delete login records, masking the origin of fraudulent transactions.
If mortgage fraud was used as a laundering vector for political funds, Okta’s role wouldn’t be peripheral, it would be the authentication gateway, making it all invisible in the downstream logs

For over a decade, Okta had no publicly disclosed breaches
Then, in early 2021, just months after the 2020 U.S. elections, the first incidents were revealed
And once they started, they didn’t stop
For a company embedded in federal agencies, election vendors, and critical infrastructure, that gap is… odd
Because hacks and breaches aren’t always just “oops” moments.
They can:
Lay predicate — create the pretext for new controls, contracts, or “security overhauls.”
Provide deniability — “It was just a cyberattack, not an internal action.”
Reveal capabilities — show the public just enough of what’s possible inside a network without exposing the full playbook.
And here’s the key:
If an outside attacker with stolen credentials can pivot across tenants, override MFA, and seize control of critical systems…
…a malicious insider with legitimate Super Admin access could do far more
...faster, quieter, and with far less risk of detection
The post-2020 breach wave gave us a rare look at what’s possible when Okta’s identity choke-point is compromised
Then, in early 2021, just months after the 2020 U.S. elections, the first incidents were revealed
And once they started, they didn’t stop
For a company embedded in federal agencies, election vendors, and critical infrastructure, that gap is… odd
Because hacks and breaches aren’t always just “oops” moments.
They can:
Lay predicate — create the pretext for new controls, contracts, or “security overhauls.”
Provide deniability — “It was just a cyberattack, not an internal action.”
Reveal capabilities — show the public just enough of what’s possible inside a network without exposing the full playbook.
And here’s the key:
If an outside attacker with stolen credentials can pivot across tenants, override MFA, and seize control of critical systems…
…a malicious insider with legitimate Super Admin access could do far more
...faster, quieter, and with far less risk of detection
The post-2020 breach wave gave us a rare look at what’s possible when Okta’s identity choke-point is compromised
March 2021
Verkada Hack
👉Vector : Okta-linked credentials exploited
👉Impact : Attackers gained root shell control over 150,000+ live security cameras inside police departments, hospitals, schools, and Tesla factories
👉Capability : Okta’s SSO position can bridge into physical security systems and IoT devices
👉Cross-Tenant Risk : If Verkada’s Okta environment was linked to other agencies, attackers could have moved laterally without starting over
Insider implications would greatly expand this capability
March 2022
Lapsus$ Okta Breach
👉Vector : Compromise of a third-party support engineer’s laptop with access to Okta’s internal tools
👉Impact : Screenshots leaked of Okta’s Super Admin dashboard - showing password resets, MFA overrides, and session kills for customers
👉Capability : Administrative god mode across all linked tenants
👉Cross-Tenant Risk : Breach one customer; pivot into others - including government agencies or election vendors
👉Insider Implication: A Super Admin could reset credentials across election vendors and agencies without any “hack” at all
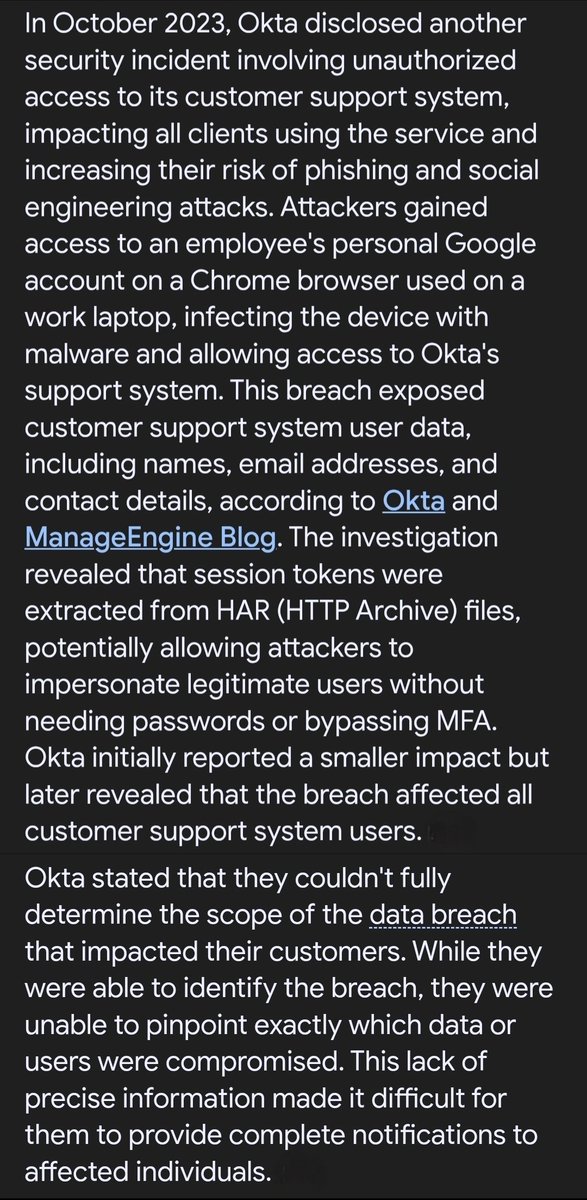
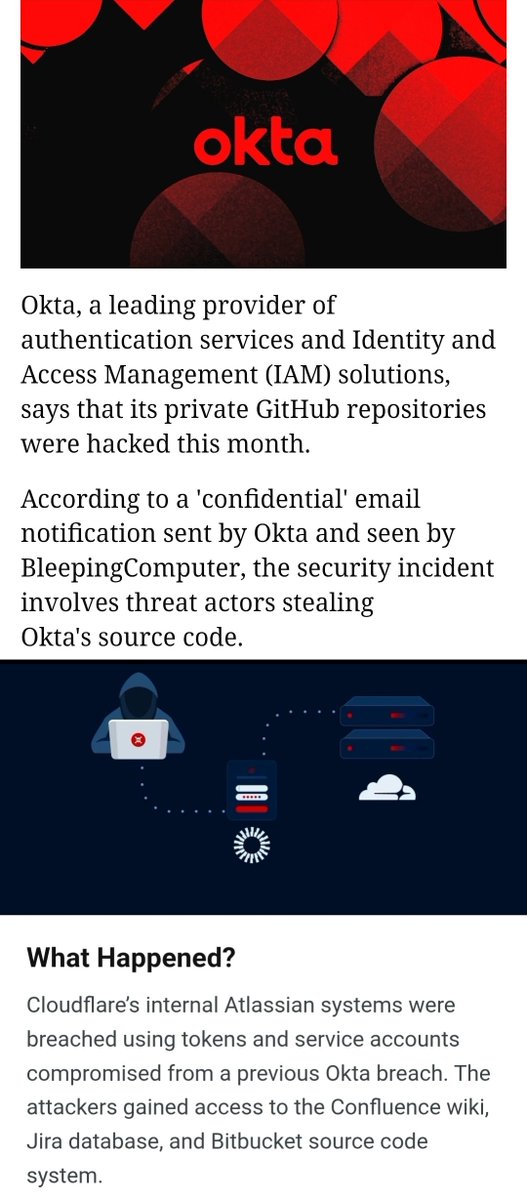
Oct/Nov 2023
Cloudflare Breach
👉Vector: "Nation-state actors" used credentials stolen in an earlier Okta compromise
👉Impact: Pivot into Cloudflare’s internal Confluence and Jira servers; exfiltration of code repositories for identity management, remote access, and Kubernetes configs
👉Capability: One Okta credential can unlock a security vendor’s internal code, enabling backdoor deployment
👉Cross-Tenant Risk: Cloudflare sits in front of thousands of systems - compromise here could cascade to all of them
👉Insider Implication: A malicious insider could plant code to silently intercept or manipulate election traffic in transit
Aug 2023
AU10TIX Breach
👉Vector: Redline Infostealer malware on an Israeli employee’s device exposed Okta credentials
👉Impact: Access to a global identity verification platform used by banks, crypto exchanges, and X (Twitter)
👉Capability: Okta as a backdoor into other identity brokers
👉Cross-Tenant Risk: Linking AU10TIX’s Okta to others enables silent identity laundering at scale
👉Insider Implication: An insider could verify fraudulent or synthetic voter identities across multiple platforms undetected
2024
CrowdStrike/Okta Impersonation Campaign
👉Vector: Fake domains (crowdstrike-okta.com, okta-poc.com) tricked admins into entering credentials
👉Impact: Potential for mass credential harvesting from high-privilege accounts
👉Capability: Okta brand trust weaponized for phishing high-value targets
👉Cross-Tenant Risk: Stolen admin credentials here could be replayed across any linked Okta tenant
👉Insider Implication: A rogue insider could run an internal “phish” to harvest credentials from other agencies or vendors without ever touching the open internet
These incidents prove three things:
□ Okta is a single point of failure for every system it touches
□ Cross-tenant pivoting is real
...compromise one tenant, and you can pivot to others
□ If outsiders can do this with stolen creds, insiders could do more
...with full control, minimal traces, and plausible deniability
When Okta sits on top of Dominion, ES&S, KnowInk, USPS, DMV voter registration systems, cloud vendors, routers, and pollpads…
…a single credential isn’t just a key, it’s a master key
And in the wrong hands, that master key can unlock the entire identity layer of American elections


Verkada Hack
👉Vector : Okta-linked credentials exploited
👉Impact : Attackers gained root shell control over 150,000+ live security cameras inside police departments, hospitals, schools, and Tesla factories
👉Capability : Okta’s SSO position can bridge into physical security systems and IoT devices
👉Cross-Tenant Risk : If Verkada’s Okta environment was linked to other agencies, attackers could have moved laterally without starting over
Insider implications would greatly expand this capability
March 2022
Lapsus$ Okta Breach
👉Vector : Compromise of a third-party support engineer’s laptop with access to Okta’s internal tools
👉Impact : Screenshots leaked of Okta’s Super Admin dashboard - showing password resets, MFA overrides, and session kills for customers
👉Capability : Administrative god mode across all linked tenants
👉Cross-Tenant Risk : Breach one customer; pivot into others - including government agencies or election vendors
👉Insider Implication: A Super Admin could reset credentials across election vendors and agencies without any “hack” at all
Oct/Nov 2023
Cloudflare Breach
👉Vector: "Nation-state actors" used credentials stolen in an earlier Okta compromise
👉Impact: Pivot into Cloudflare’s internal Confluence and Jira servers; exfiltration of code repositories for identity management, remote access, and Kubernetes configs
👉Capability: One Okta credential can unlock a security vendor’s internal code, enabling backdoor deployment
👉Cross-Tenant Risk: Cloudflare sits in front of thousands of systems - compromise here could cascade to all of them
👉Insider Implication: A malicious insider could plant code to silently intercept or manipulate election traffic in transit
Aug 2023
AU10TIX Breach
👉Vector: Redline Infostealer malware on an Israeli employee’s device exposed Okta credentials
👉Impact: Access to a global identity verification platform used by banks, crypto exchanges, and X (Twitter)
👉Capability: Okta as a backdoor into other identity brokers
👉Cross-Tenant Risk: Linking AU10TIX’s Okta to others enables silent identity laundering at scale
👉Insider Implication: An insider could verify fraudulent or synthetic voter identities across multiple platforms undetected
2024
CrowdStrike/Okta Impersonation Campaign
👉Vector: Fake domains (crowdstrike-okta.com, okta-poc.com) tricked admins into entering credentials
👉Impact: Potential for mass credential harvesting from high-privilege accounts
👉Capability: Okta brand trust weaponized for phishing high-value targets
👉Cross-Tenant Risk: Stolen admin credentials here could be replayed across any linked Okta tenant
👉Insider Implication: A rogue insider could run an internal “phish” to harvest credentials from other agencies or vendors without ever touching the open internet
These incidents prove three things:
□ Okta is a single point of failure for every system it touches
□ Cross-tenant pivoting is real
...compromise one tenant, and you can pivot to others
□ If outsiders can do this with stolen creds, insiders could do more
...with full control, minimal traces, and plausible deniability
When Okta sits on top of Dominion, ES&S, KnowInk, USPS, DMV voter registration systems, cloud vendors, routers, and pollpads…
…a single credential isn’t just a key, it’s a master key
And in the wrong hands, that master key can unlock the entire identity layer of American elections

Every breach you just saw showed how Okta access can:
👉Pivot across tenants
👉Override MFA
👉Reset credentials
👉Inject code into upstream vendors
👉Control physical and digital systems alike
If outsiders can do that with stolen creds…
…imagine what a malicious insider could do, only better
Now here’s the part that matters most:
Okta isn’t hovering on the sidelines
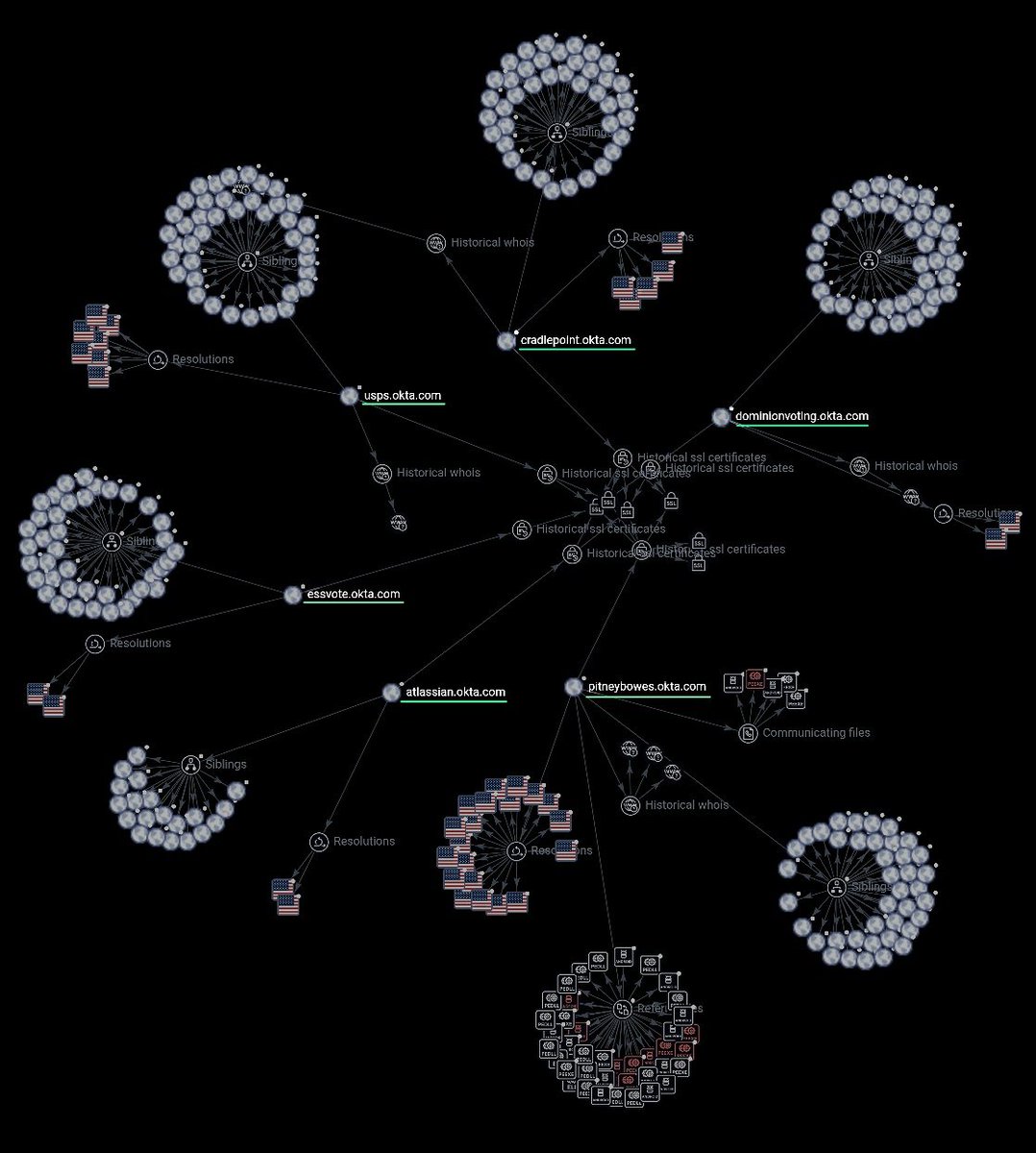
It’s already wired into the core election stack:
👉Dominion Voting Systems –
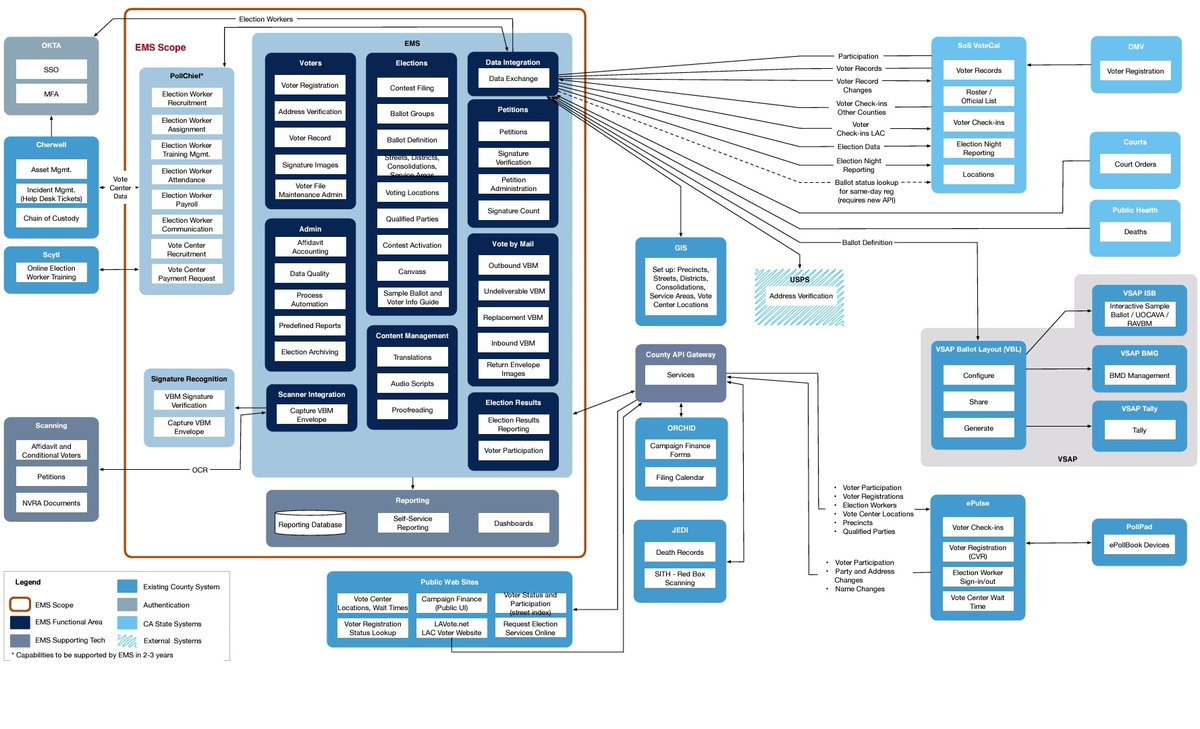
Okta tenant confirmed; LDAP and Confluence integration; tied into Election Management System (EMS) components for ballot generation and voter record management
👉ES&S – oktapreview.essvote.com domain; AWS-hosted; Cloudflare routes; preview environment confirms active Okta-based SSO integration
👉KnowInk – Integrated with Dominion for real-time pollpad/e-pollbook to EMS connectivity
👉Voter registration portals
(Example👇)
WisVote – Uses MyWisconsinID (Okta-backed) for voter registration access
👉USPS & DMV – Okta identity layer links to voter registration and mail ballot tracking portals
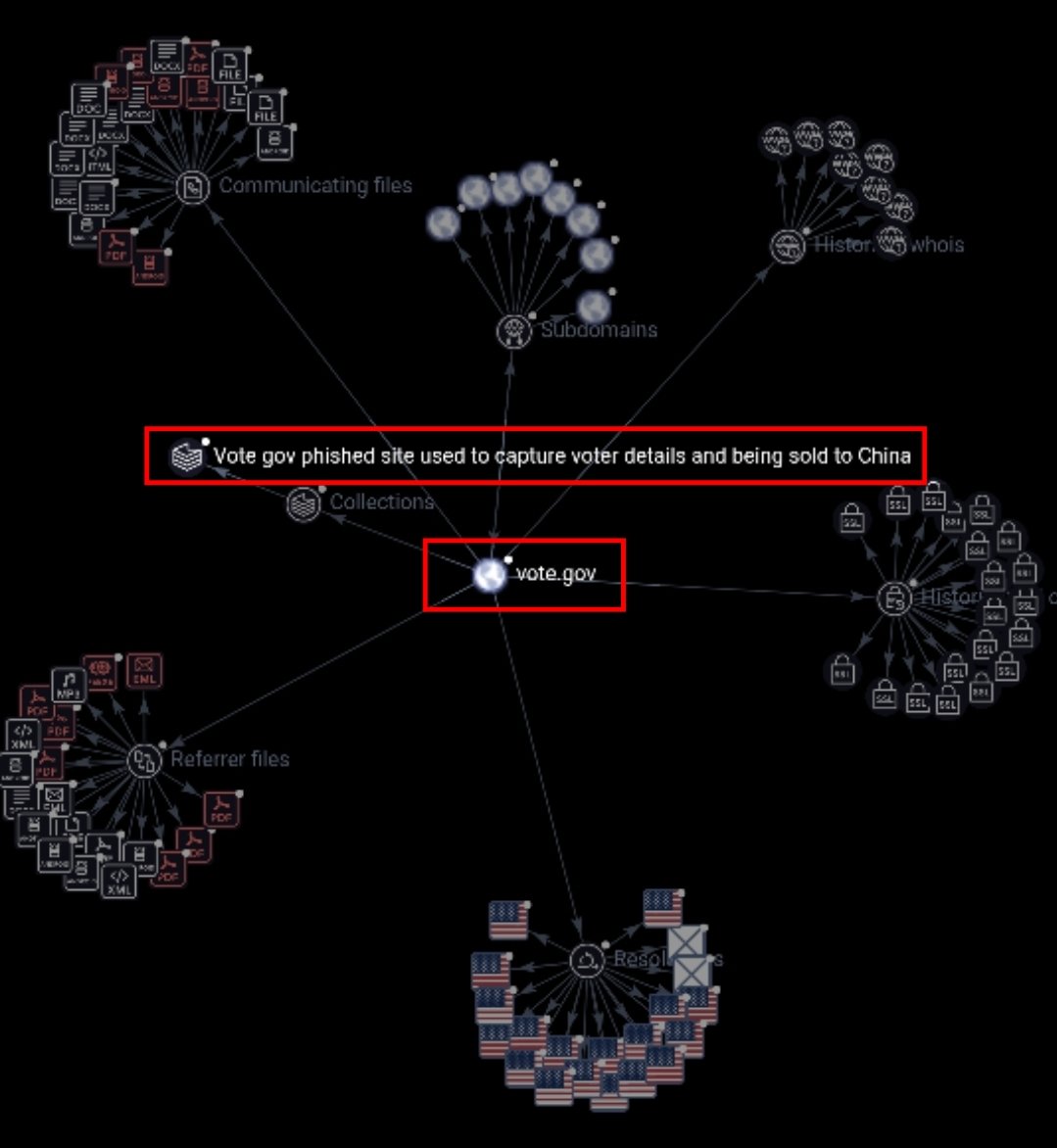
👉Vote.gov – Okta-linked federal voter registration hub
👉Cradlepoint Routers – Okta identity access tied to election telecom hardware, including AT&T 5G/Open RAN networks via Ericsson
Not hypothetical
The same systems that could be breached or pivoted through Okta already sit at the heart of U.S. elections, from voter registration to ballot tabulation
And just like in the breach cases, one compromise here doesn’t just touch one vendor
It can cascade across the entire connected election ecosystem


👉Pivot across tenants
👉Override MFA
👉Reset credentials
👉Inject code into upstream vendors
👉Control physical and digital systems alike
If outsiders can do that with stolen creds…
…imagine what a malicious insider could do, only better
Now here’s the part that matters most:
Okta isn’t hovering on the sidelines
It’s already wired into the core election stack:
👉Dominion Voting Systems –
Okta tenant confirmed; LDAP and Confluence integration; tied into Election Management System (EMS) components for ballot generation and voter record management
👉ES&S – oktapreview.essvote.com domain; AWS-hosted; Cloudflare routes; preview environment confirms active Okta-based SSO integration
👉KnowInk – Integrated with Dominion for real-time pollpad/e-pollbook to EMS connectivity
👉Voter registration portals
(Example👇)
WisVote – Uses MyWisconsinID (Okta-backed) for voter registration access
👉USPS & DMV – Okta identity layer links to voter registration and mail ballot tracking portals
👉Vote.gov – Okta-linked federal voter registration hub
👉Cradlepoint Routers – Okta identity access tied to election telecom hardware, including AT&T 5G/Open RAN networks via Ericsson
Not hypothetical
The same systems that could be breached or pivoted through Okta already sit at the heart of U.S. elections, from voter registration to ballot tabulation
And just like in the breach cases, one compromise here doesn’t just touch one vendor
It can cascade across the entire connected election ecosystem


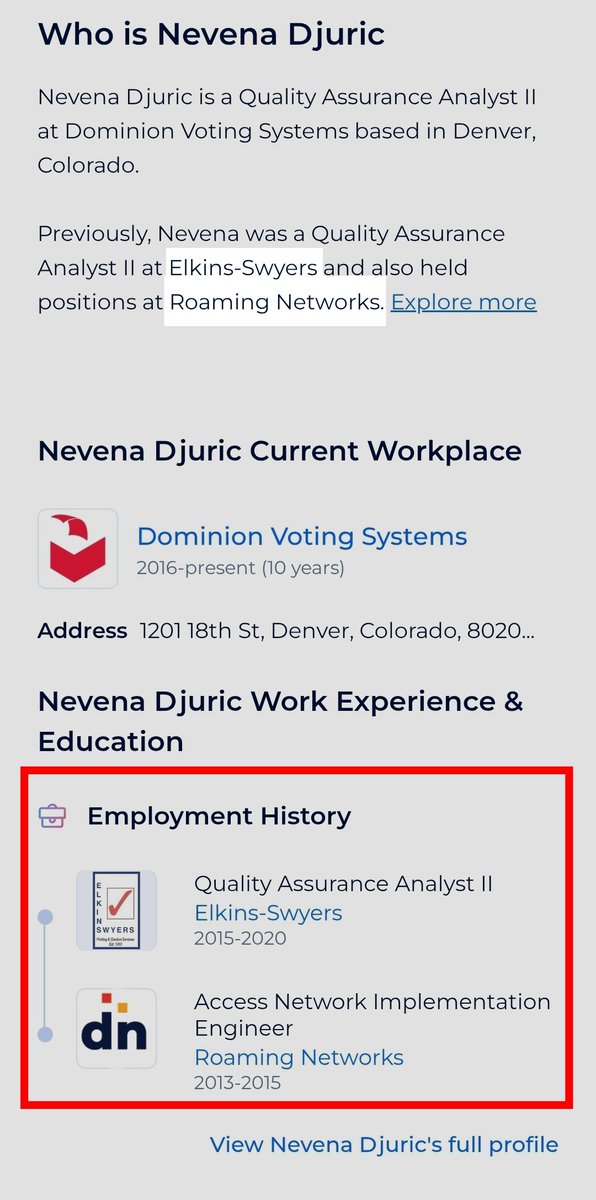
Thanks to @SheriffLeaf's efforts, we know Dominion’s Serbian activity pertaining to Okta logs had questionable anomalies
Email exchanges between Jeremy Holck and Nevena Djuric highlight one such instance



Email exchanges between Jeremy Holck and Nevena Djuric highlight one such instance
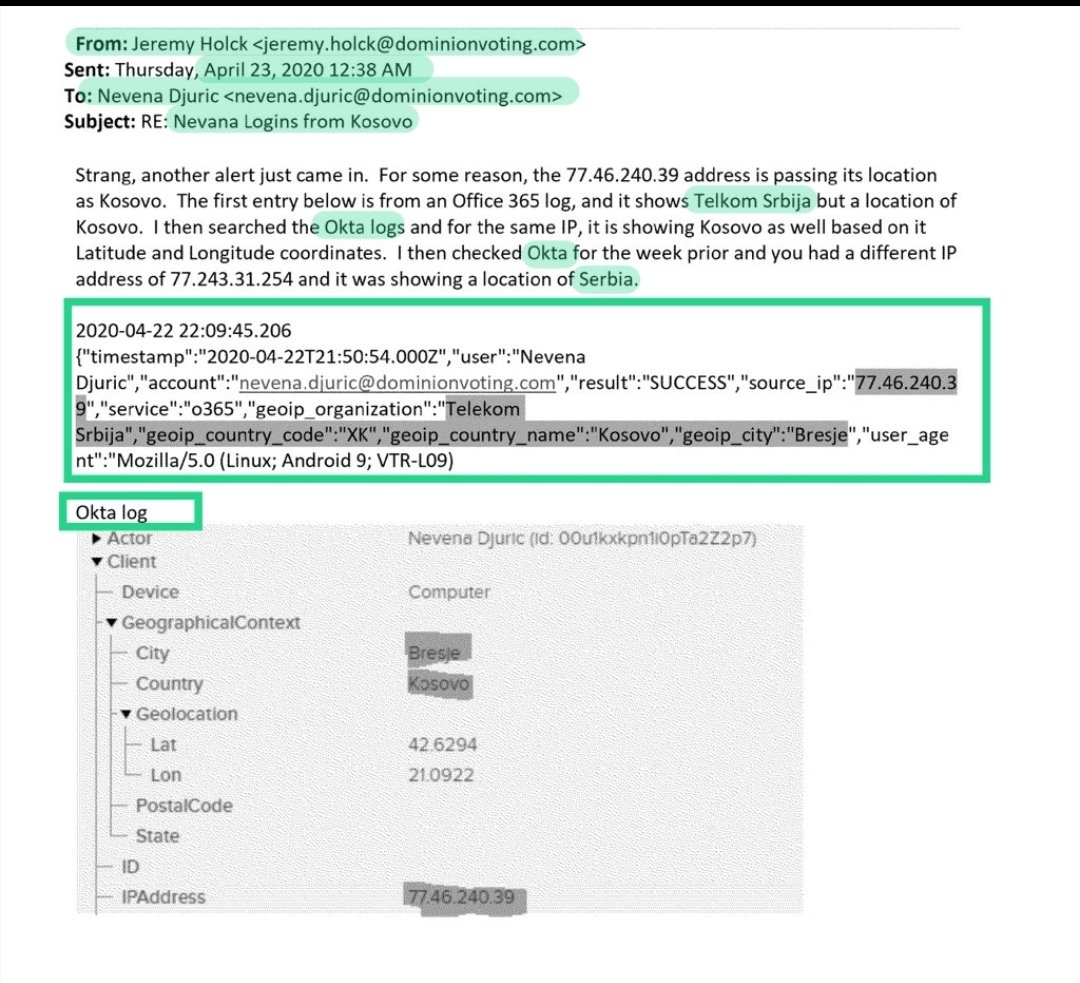
Ah... but Nevena would understand EXACTLY what was going on
Prior to her employment with Dominion she worked at:
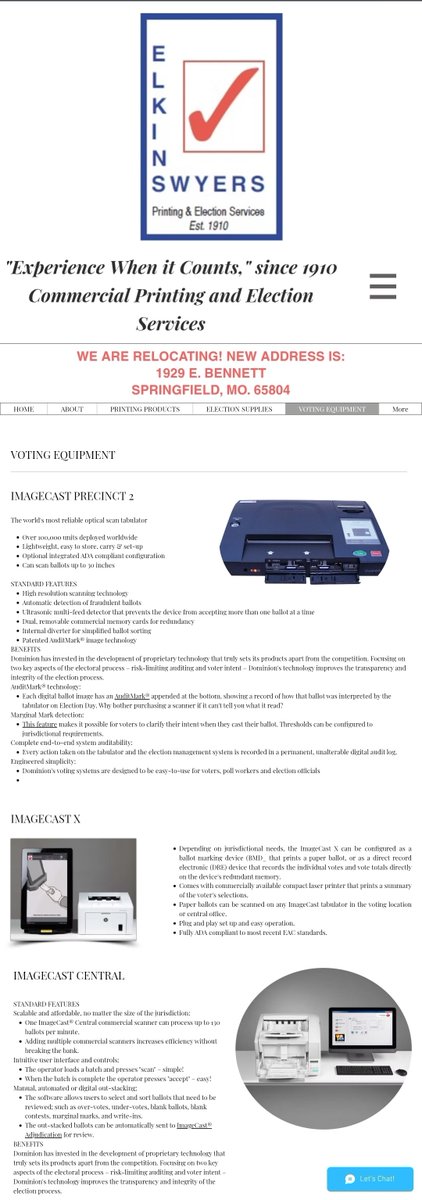
👉Roaming Networks, a systems integrator and digital general contractor specializing in telecommunications and related services offering design, build, integration, and maintenance services for telecommunications infrastructure, WHO HELD
DOMINION’S Belgrade Data Center
and is a 👇
A HUAWEI PARTNER AFFILIATE
(Roaming has changed it's name since to Dot Networks but the signage on their Belgrade headquarters is still Roaming per, Google earth)
She also spent the 5 years between Roaming Networks and Dominion, leading up to the 2020 election, as QA for Elkins Swyers who is an elections vendor for Dominion
@joeoltmannX



Prior to her employment with Dominion she worked at:
👉Roaming Networks, a systems integrator and digital general contractor specializing in telecommunications and related services offering design, build, integration, and maintenance services for telecommunications infrastructure, WHO HELD
DOMINION’S Belgrade Data Center
and is a 👇
A HUAWEI PARTNER AFFILIATE
(Roaming has changed it's name since to Dot Networks but the signage on their Belgrade headquarters is still Roaming per, Google earth)
She also spent the 5 years between Roaming Networks and Dominion, leading up to the 2020 election, as QA for Elkins Swyers who is an elections vendor for Dominion
@joeoltmannX


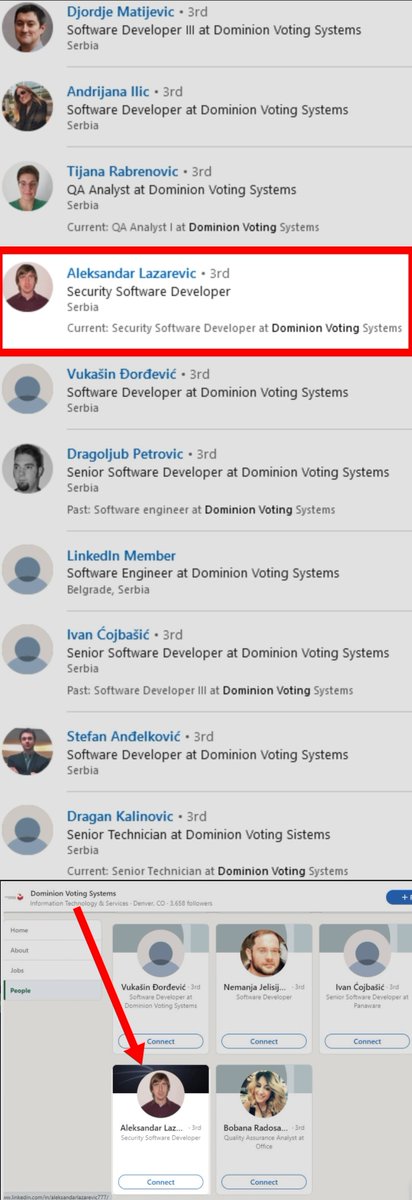
👉Aleksandar Lazarevic
Dominion employment and also shows up in Sheriff Leaf's email discoveries
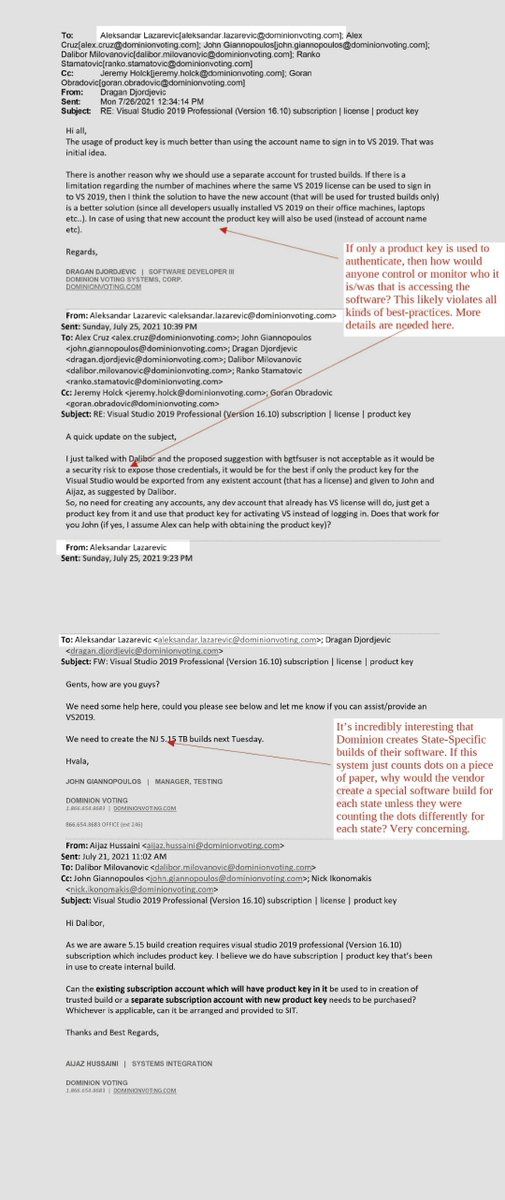
👉Github code👇 "removablemediamanager" for remote access and contains Dominion password "dvscorp08!"
Uploaded as a full commit suggesting it was prebuilt prior to upload
The commented lines (AUTH SSL, getSslStream(), setUseStream(true)) show it’s intended to support explicit/implicit TLS and raw command injection (e.g., SITE commands)
In this commit, the file path is just a placeholder (@"Filepath")
But if wired up to code that monitors a directory, removable drive, or system folders, it could automatically push selected files without user action
This is not a complete remote access trojan (RAT) but as a payload inside a larger tool, it could form the file-transfer / data exfiltration part of a RAT or insider tool
Links to Github repo:
github.com/aleksandarlaza…
github.com/aleksandarlaza…
@joeoltmannX
@PeterBernegger



Dominion employment and also shows up in Sheriff Leaf's email discoveries
👉Github code👇 "removablemediamanager" for remote access and contains Dominion password "dvscorp08!"
Uploaded as a full commit suggesting it was prebuilt prior to upload
The commented lines (AUTH SSL, getSslStream(), setUseStream(true)) show it’s intended to support explicit/implicit TLS and raw command injection (e.g., SITE commands)
In this commit, the file path is just a placeholder (@"Filepath")
But if wired up to code that monitors a directory, removable drive, or system folders, it could automatically push selected files without user action
This is not a complete remote access trojan (RAT) but as a payload inside a larger tool, it could form the file-transfer / data exfiltration part of a RAT or insider tool
Links to Github repo:
github.com/aleksandarlaza…
github.com/aleksandarlaza…
@joeoltmannX
@PeterBernegger


Totally agree on CrowdStrike
Once this whole thing gets aired out, people will be shocked at exactly how multifaceted and entrenched the subversion all really is, some more than others
(Also, smaller precincts and more of them, election DAY, no mail-ins without special request, cleaned voter rolls, HAND COUNTED AND AUDITED SIMULTANEOUSLY 👊)
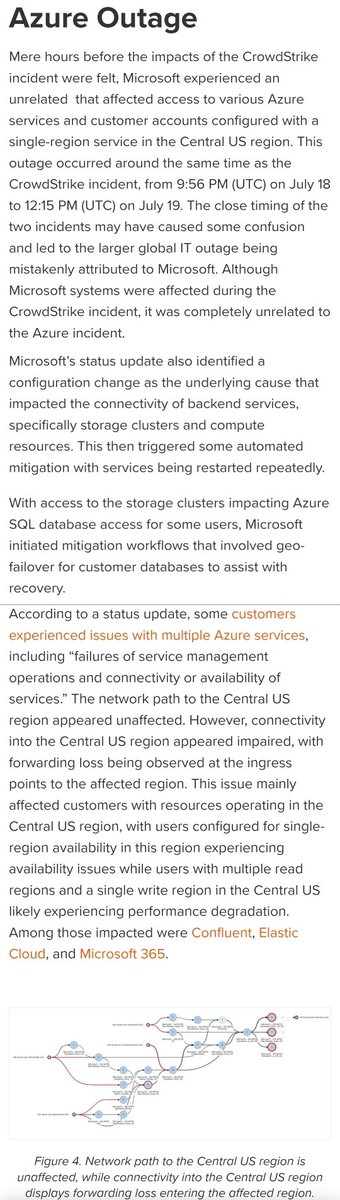
So, interesting you should mention Azure
Just hours before the CrowdStrike/Microsoft outtage occurred, Azure services went down for most of the Central U.S., kind of got lost in the aftermath
👉Milan Gospic
"Azure is made in Serbia"
Lead - Serbia Microsoft/Azure development center/ former Country Manager - Erricson @Vltra_MK
x.com/PatriotMarkCoo…


Once this whole thing gets aired out, people will be shocked at exactly how multifaceted and entrenched the subversion all really is, some more than others
(Also, smaller precincts and more of them, election DAY, no mail-ins without special request, cleaned voter rolls, HAND COUNTED AND AUDITED SIMULTANEOUSLY 👊)
So, interesting you should mention Azure
Just hours before the CrowdStrike/Microsoft outtage occurred, Azure services went down for most of the Central U.S., kind of got lost in the aftermath
👉Milan Gospic
"Azure is made in Serbia"
Lead - Serbia Microsoft/Azure development center/ former Country Manager - Erricson @Vltra_MK
x.com/PatriotMarkCoo…
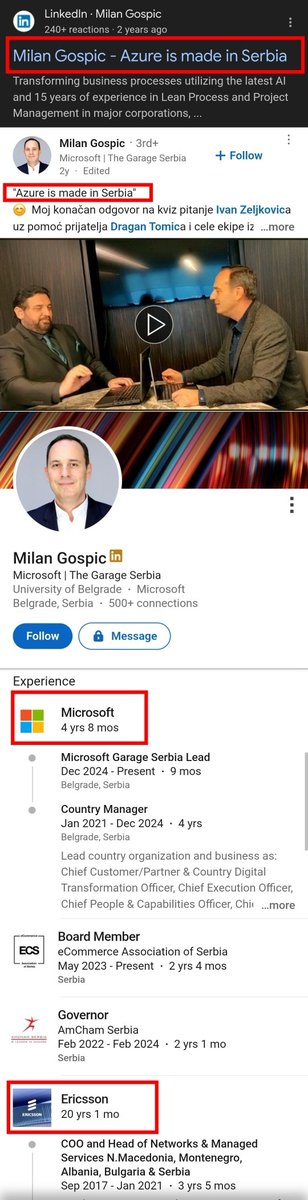

I first came across the Microsoft Azure Center Belgrade detail when I was trying to make sense of something...
... but once I saw this👇
... but once I saw this👇
👆👆👆👆👆👆👆👆👆👆👆
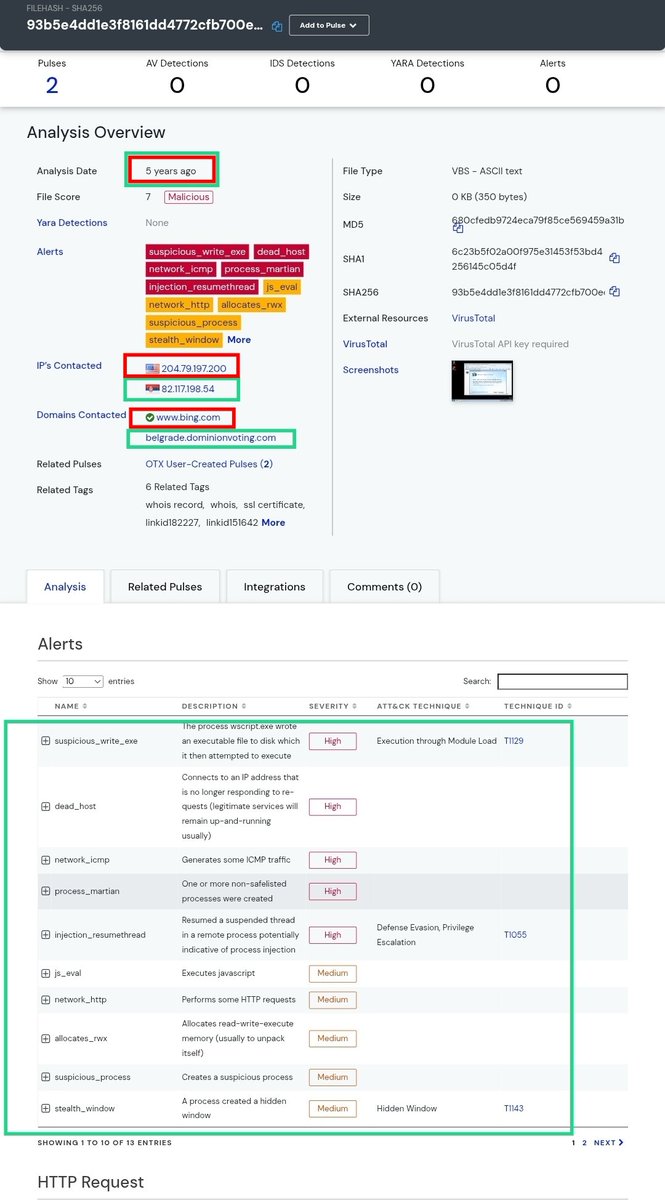
It's a multi-purpose VBS stager/dropper with injection capabilities
👉Stager – sets up execution for follow-on payloads
👉Dropper – writes an executable to disk
👉Injector – performs code injection into legitimate processes
👉Beacon/loader – establishes comms (HTTP/ICMP) and can fetch further code
👉Stealth - creates a hidden window (MITRE T1143) that hides processes, activities, and tools that would otherwise alert to the presence of malicious operations
This, when paired with the FTPS GitHub exfiltration code, represents a classic multi-stage intrusion chain
BOTH ARTIFACTS CONNECTED TO DOMINION INFRASTRUCTURE
Capable of delivering a logic bomb with time-based/conditions-based triggers
The Ammo and the Clip
And Okta (who Dominion was using for identity and access roles) is the barrel through which it was fired
They gave these foreign operators access
It's a multi-purpose VBS stager/dropper with injection capabilities
👉Stager – sets up execution for follow-on payloads
👉Dropper – writes an executable to disk
👉Injector – performs code injection into legitimate processes
👉Beacon/loader – establishes comms (HTTP/ICMP) and can fetch further code
👉Stealth - creates a hidden window (MITRE T1143) that hides processes, activities, and tools that would otherwise alert to the presence of malicious operations
This, when paired with the FTPS GitHub exfiltration code, represents a classic multi-stage intrusion chain
BOTH ARTIFACTS CONNECTED TO DOMINION INFRASTRUCTURE
Capable of delivering a logic bomb with time-based/conditions-based triggers
The Ammo and the Clip
And Okta (who Dominion was using for identity and access roles) is the barrel through which it was fired
They gave these foreign operators access
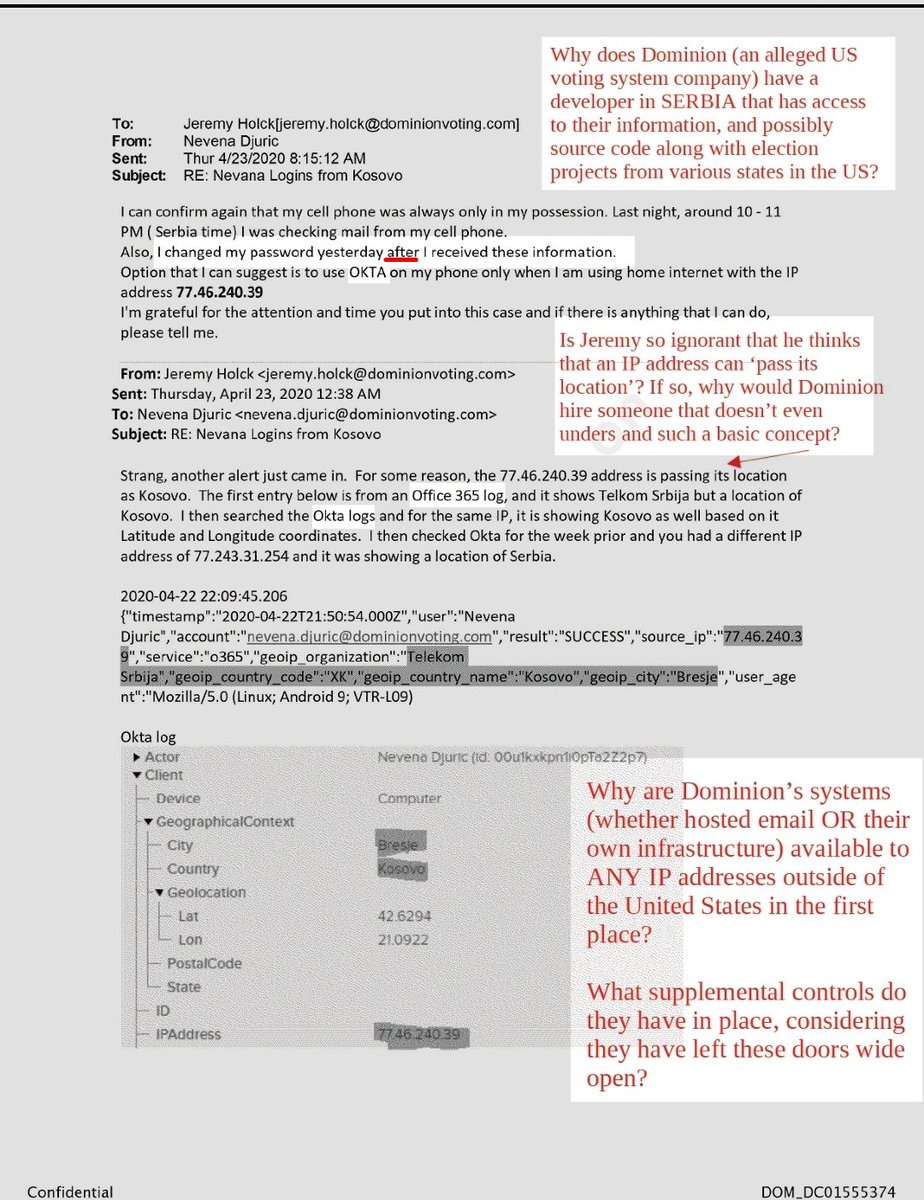
Why is the Dynamic Network Zones detail important?
Because it completely destroys both Nevena's explanation and claims...
...AND it shows Dominion's either negligent or complicit posture
First, it's important to understand why Okta’s Dynamic Network Zones are a massive deal in the Dominion-Serbia login incident...
Because it completely destroys both Nevena's explanation and claims...
...AND it shows Dominion's either negligent or complicit posture
First, it's important to understand why Okta’s Dynamic Network Zones are a massive deal in the Dominion-Serbia login incident...
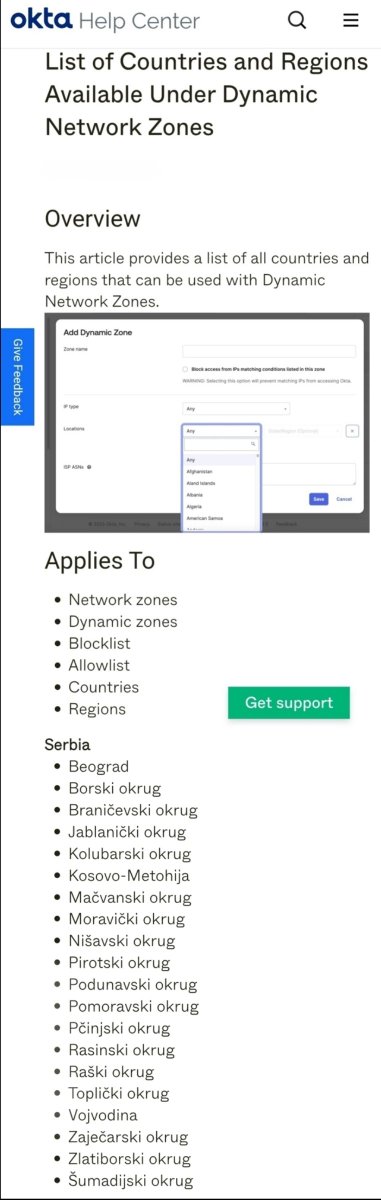
In this situation, Okta doesn't just recognize "Serbia", it recognizes specific regions, including the exact ones that Nevena's account was logging in from, such as:
👉Šumadija ( Kragujevac)
👉Raški
👉Nišavski
👉Kosovo-Metohija (Bresje)
👉Beograd (Belgrade)
...and a long list of sub-regions
This means Okta already knows exactly where an IP is coming from down to the district, and the Dominion emails show the flips
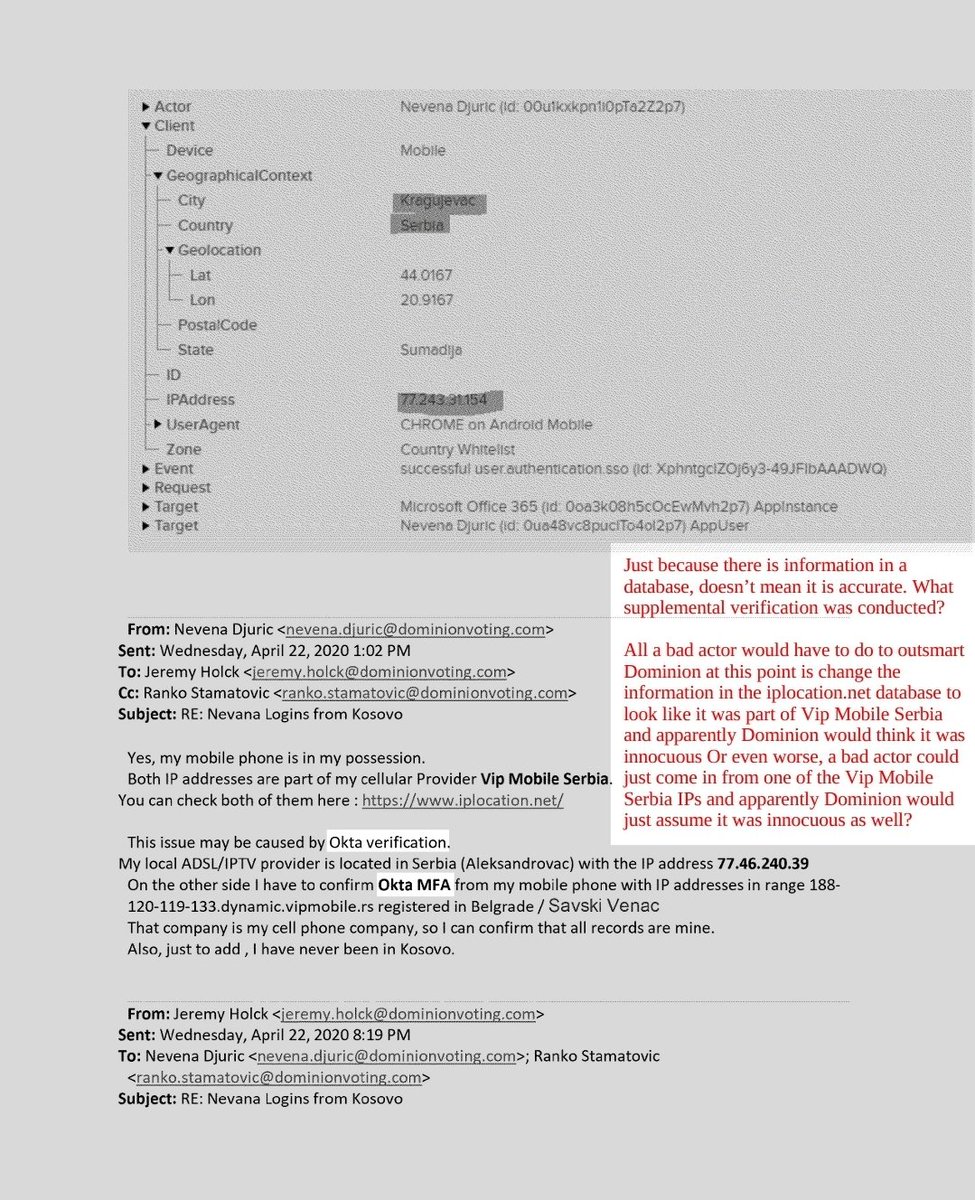
Nevena's explanations:
"Okta verification issue/IP database error" lacks plausibility and is contradicted by DNZ precision
"I've never been to Kosovo"
"My phone was always with me"
BUT "I changed my password yesterday after I received these information"
Classic incident cleanup after exposure
With a password change to close the breach window
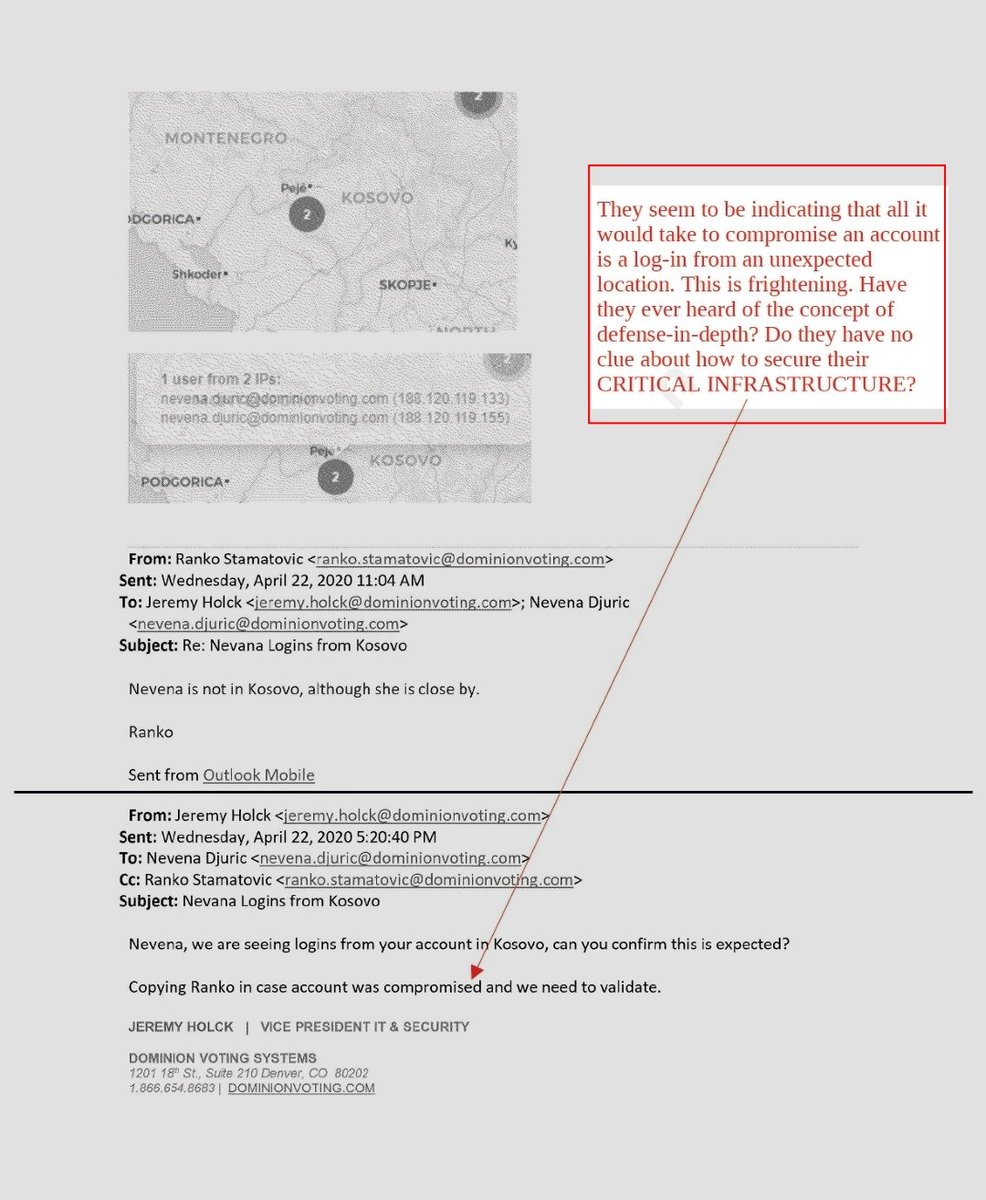
Why had an alert not been raised before?
Looks like it's because someone slipped up, and an access vector that had been occurring unnoticed suddenly came to light by accidental
VPN endpoint slip, routing shift, or tower handoff
With Okta DNZ, Dominion could have blocked at the regional or IP level beforehand, but they left it wide open
x.com/Theonlyme333/s…
👉Šumadija ( Kragujevac)
👉Raški
👉Nišavski
👉Kosovo-Metohija (Bresje)
👉Beograd (Belgrade)
...and a long list of sub-regions
This means Okta already knows exactly where an IP is coming from down to the district, and the Dominion emails show the flips
Nevena's explanations:
"Okta verification issue/IP database error" lacks plausibility and is contradicted by DNZ precision
"I've never been to Kosovo"
"My phone was always with me"
BUT "I changed my password yesterday after I received these information"
Classic incident cleanup after exposure
With a password change to close the breach window
Why had an alert not been raised before?
Looks like it's because someone slipped up, and an access vector that had been occurring unnoticed suddenly came to light by accidental
VPN endpoint slip, routing shift, or tower handoff
With Okta DNZ, Dominion could have blocked at the regional or IP level beforehand, but they left it wide open
x.com/Theonlyme333/s…
• • •
Missing some Tweet in this thread? You can try to
force a refresh