I haven’t done a thread for a while but the new IISS report provides an interesting insight on Russia's sabotage ops:
Since 2022, Moscow's been ramping up hybrid attacks on the West—arson, drones, cyber hits—to sow chaos amid Ukraine war. Over 100 incidents tracked in Europe alone.
Thread 🧵 : Key takeaways, risks, & lessons from the paper.
Since 2022, Moscow's been ramping up hybrid attacks on the West—arson, drones, cyber hits—to sow chaos amid Ukraine war. Over 100 incidents tracked in Europe alone.
Thread 🧵 : Key takeaways, risks, & lessons from the paper.

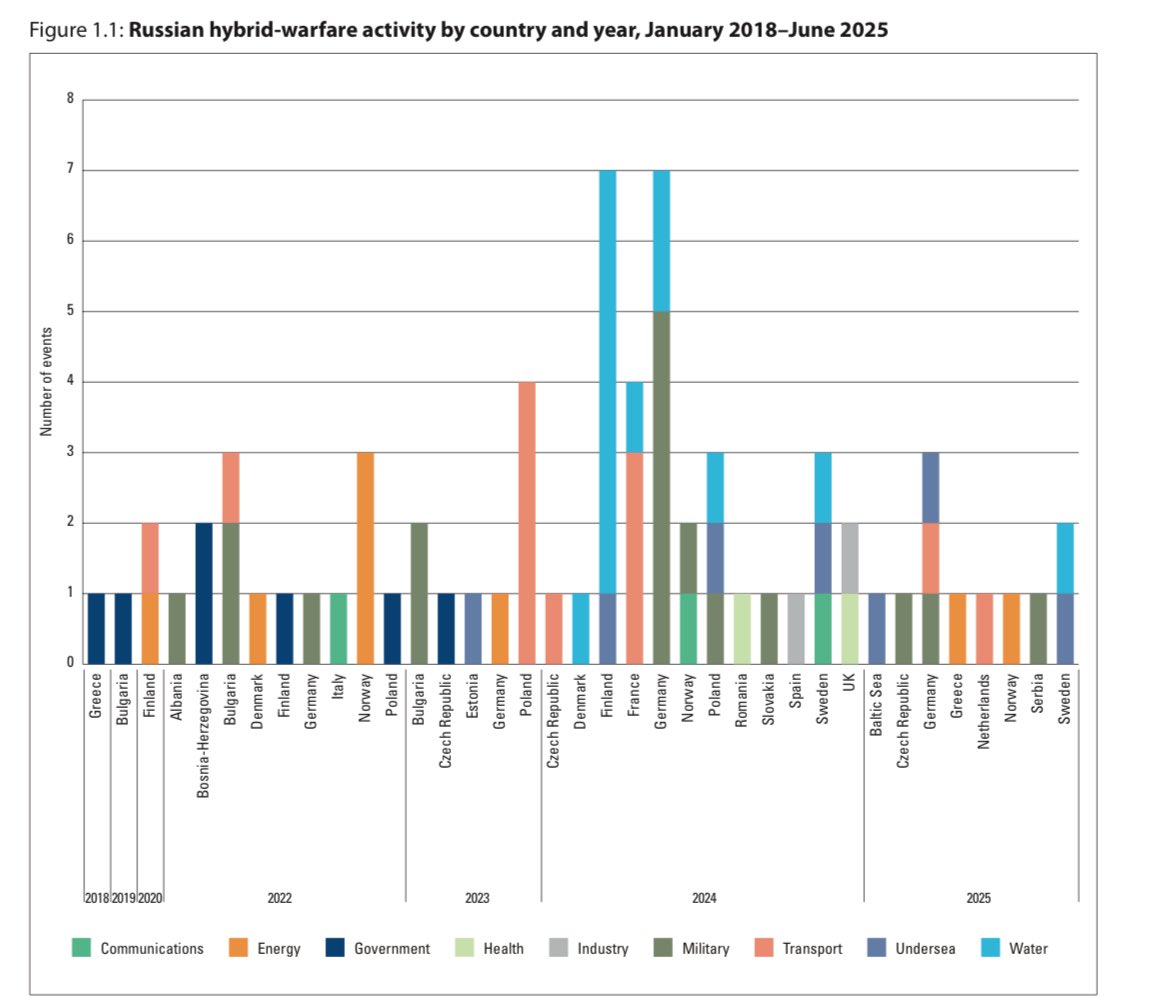
Russia's sabotage isn't random—it's state-directed, often via proxies like Wagner remnants or GRU-linked networks. Targets: Critical infrastructure (rail, pipelines, data centers) to disrupt NATO support for Ukraine. Scale exploded post-2022 invasion: From ~20 ops/year pre-war to 50+ in 2023-24. Europe hit hardest (Germany, UK, Baltics), but US & allies too.
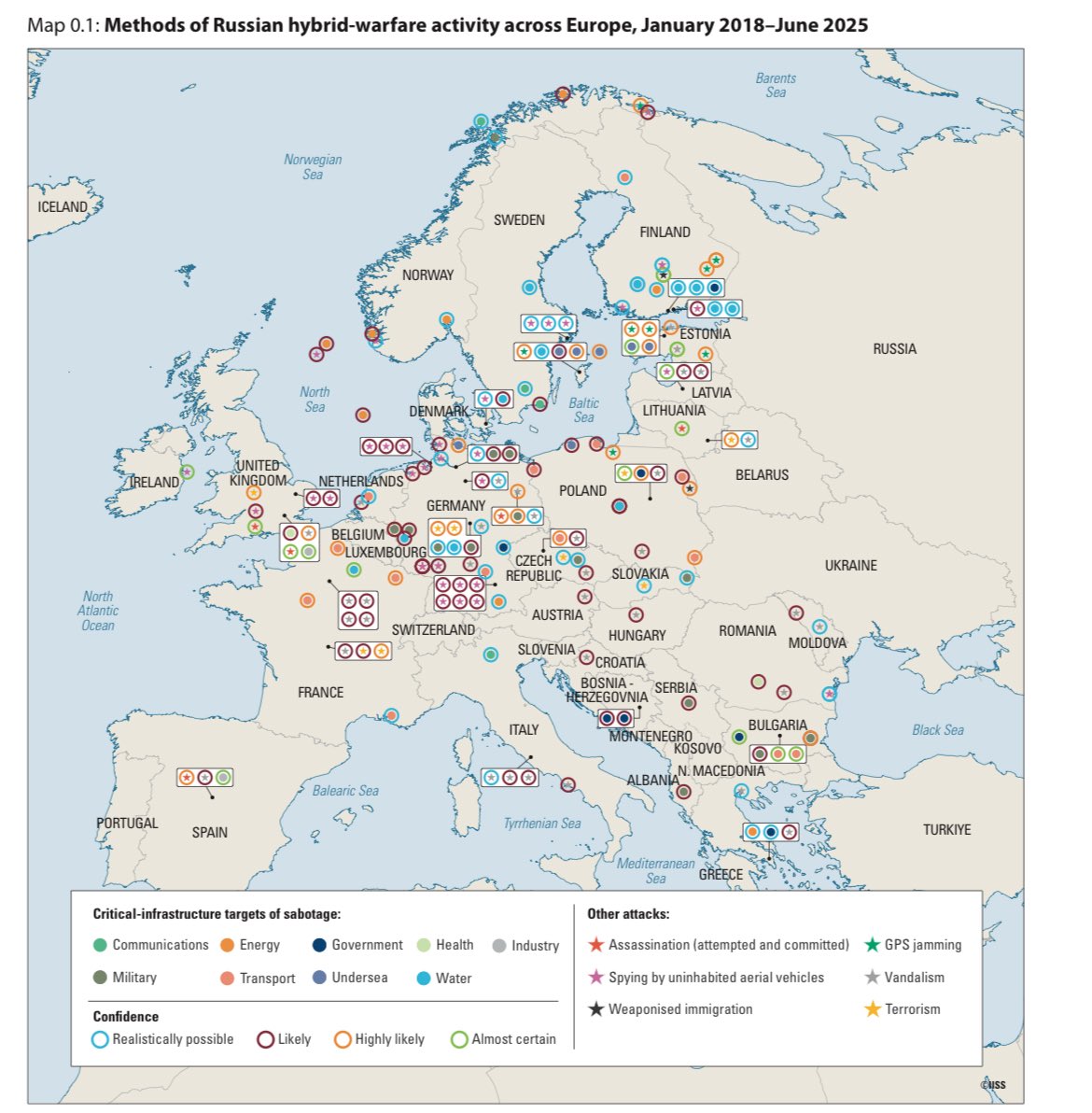
Tactics mix low-tech (molotovs on warehouses) with high-tech (drones on refineries).
Motive? Weaken Western resolve and chip away at surety of essential services without full invasion - pose the question of “is it worth it?”.
Paper IDs 3 phases: Testing (2022), Escalation (2023), & now "Normalisation" (2024+), with ops in 20+ countries. Russia even recruiting criminals via Telegram for deniability.
Motive? Weaken Western resolve and chip away at surety of essential services without full invasion - pose the question of “is it worth it?”.
Paper IDs 3 phases: Testing (2022), Escalation (2023), & now "Normalisation" (2024+), with ops in 20+ countries. Russia even recruiting criminals via Telegram for deniability.

Standout case: 2024 arson on UK warehouses linked to Russian GRU; drone strikes on Baltic ports. Not just Europe—US cargo ships targeted in 2023. Paper warns: This is grey zone warfare, below war threshold but entropic erosion of security. Total incidents: 150+ globally since 2022, per IISS data.
Risks:
Short-term: Immediate disruptions to energy/supply chains could spike prices (e.g., 10-20% oil volatility from pipeline hits). Long-term: Erodes public trust in CNI integrity and availability, boosts populism and isolationist trends, fractures alliances
Short-term: Immediate disruptions to energy/supply chains could spike prices (e.g., 10-20% oil volatility from pipeline hits). Long-term: Erodes public trust in CNI integrity and availability, boosts populism and isolationist trends, fractures alliances
Attribution challenges make retaliation tricky—Russia uses cutouts (e.g., "tourists" or hackers).
Vulnerable spots: Underprotected infra like rail (seen in Czech/German attacks). Worst-case: Cascading failures, e.g., sabotage + cyber = major grid disruption .
Overall threat level: "Severe" for Europe; "Elevated" for US/Asia per paper's framework.
Vulnerable spots: Underprotected infra like rail (seen in Czech/German attacks). Worst-case: Cascading failures, e.g., sabotage + cyber = major grid disruption .
Overall threat level: "Severe" for Europe; "Elevated" for US/Asia per paper's framework.
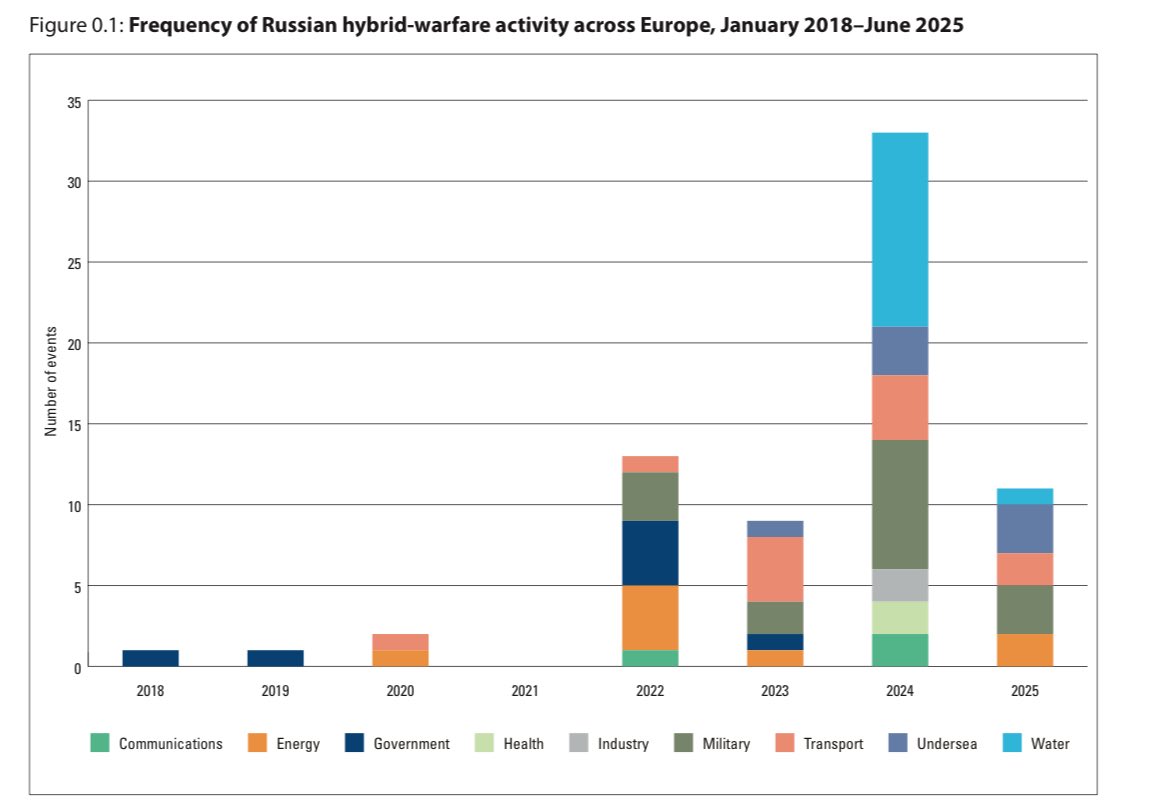
But it's not invincible—ops often conducted with sloppy tradecraft (e.g., failed drone drops caught on cam). Still, without countermeasures, paper expects 20-30% annual increase.
Bottom line: Ignoring this invites more bold moves from Putin.
Bottom line: Ignoring this invites more bold moves from Putin.
Lessons Learned:
1) Intelligence sharing is key—NATO's fused intel (e.g., UK's sharing with Baltics) foiled 40% of plots.
2) Harden targets: Basic, good quality physical security stopped half the low-tech attempts.
Paper cites Estonia's success: Quick arrests via public tips + AI monitoring.
1) Intelligence sharing is key—NATO's fused intel (e.g., UK's sharing with Baltics) foiled 40% of plots.
2) Harden targets: Basic, good quality physical security stopped half the low-tech attempts.
Paper cites Estonia's success: Quick arrests via public tips + AI monitoring.

Lessons cont'd:
3) Public awareness works—Sweden's campaigns reduced insider risk.
4) Don't overreact: Proportionate responses key to avoiding fatigue induced apathy (sanctions, expulsions) deter without significant escalation.
5) Long-game: Invest in resilience training and increased focus on CNI security; Russia's learning curve means ops will evolve (e.g., more co-opting of protest movements ala Palestine action?)
3) Public awareness works—Sweden's campaigns reduced insider risk.
4) Don't overreact: Proportionate responses key to avoiding fatigue induced apathy (sanctions, expulsions) deter without significant escalation.
5) Long-game: Invest in resilience training and increased focus on CNI security; Russia's learning curve means ops will evolve (e.g., more co-opting of protest movements ala Palestine action?)
Big picture: Russia's sabotage is a symptom of hybrid war's new normal—affordable, deniable, effective and with a low barrier to entry. Increasing confluence between Russian aims and those of protest/activist groups provides a golden opportunity to provide Russia with achieving its goals with a small/low footprint in country.
The West must urgently adapt or pay the price. Read the full IISS report 👇
iiss.org/globalassets/m…
The West must urgently adapt or pay the price. Read the full IISS report 👇
iiss.org/globalassets/m…
• • •
Missing some Tweet in this thread? You can try to
force a refresh




