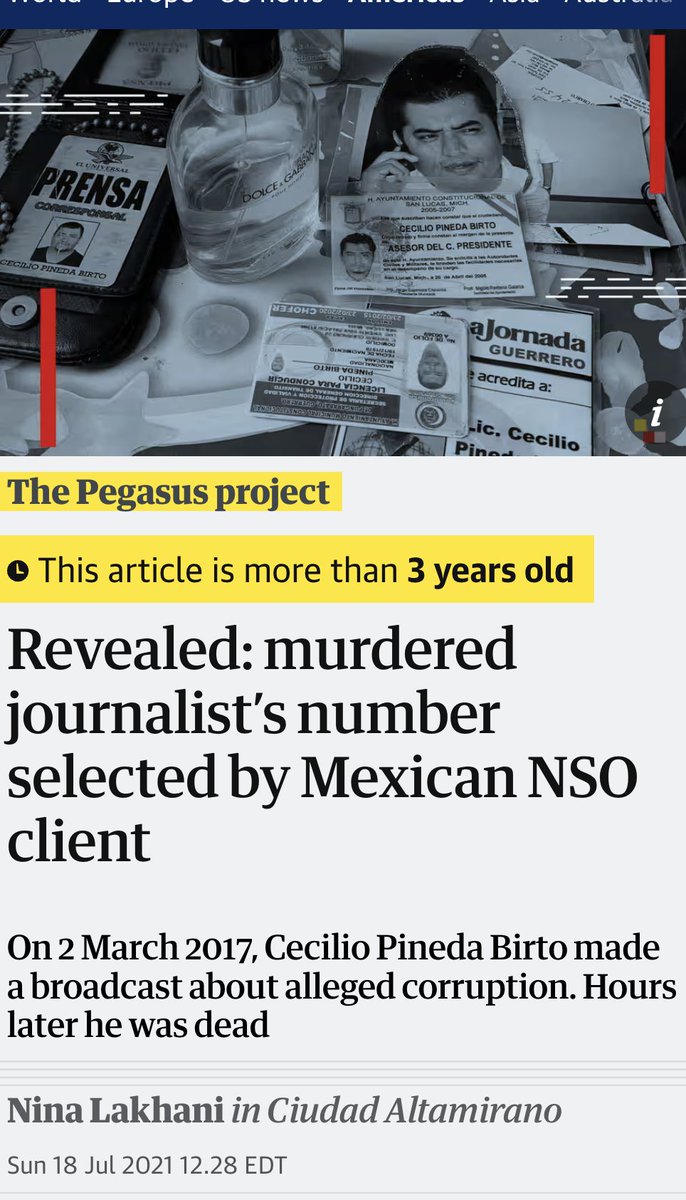
NEW: foreign mercenary spyware is coming to the US.
ICE just quietly unsuspended contract with spyware maker #Paragon.
Remember them?
Caught earlier this year being used to hack journalists.
Bad move for Americans rights, national security & counterintelligence 1/
ICE just quietly unsuspended contract with spyware maker #Paragon.
Remember them?
Caught earlier this year being used to hack journalists.
Bad move for Americans rights, national security & counterintelligence 1/

2/ #Paragon was co-founded in Israel in 2019 by ex head of Israel's NSA equivalent (Unit 8200) w/ major backing from former Israeli PM Ehud Barak.
Pitched themselves as stealthy & abuse-proof alternative to NSO Group's Pegasus.
& have been trying to get into the US market for years.



Pitched themselves as stealthy & abuse-proof alternative to NSO Group's Pegasus.
& have been trying to get into the US market for years.




3/For a long time all we knew about Paragon was their performance as a 'virtuous' spyware company with values.
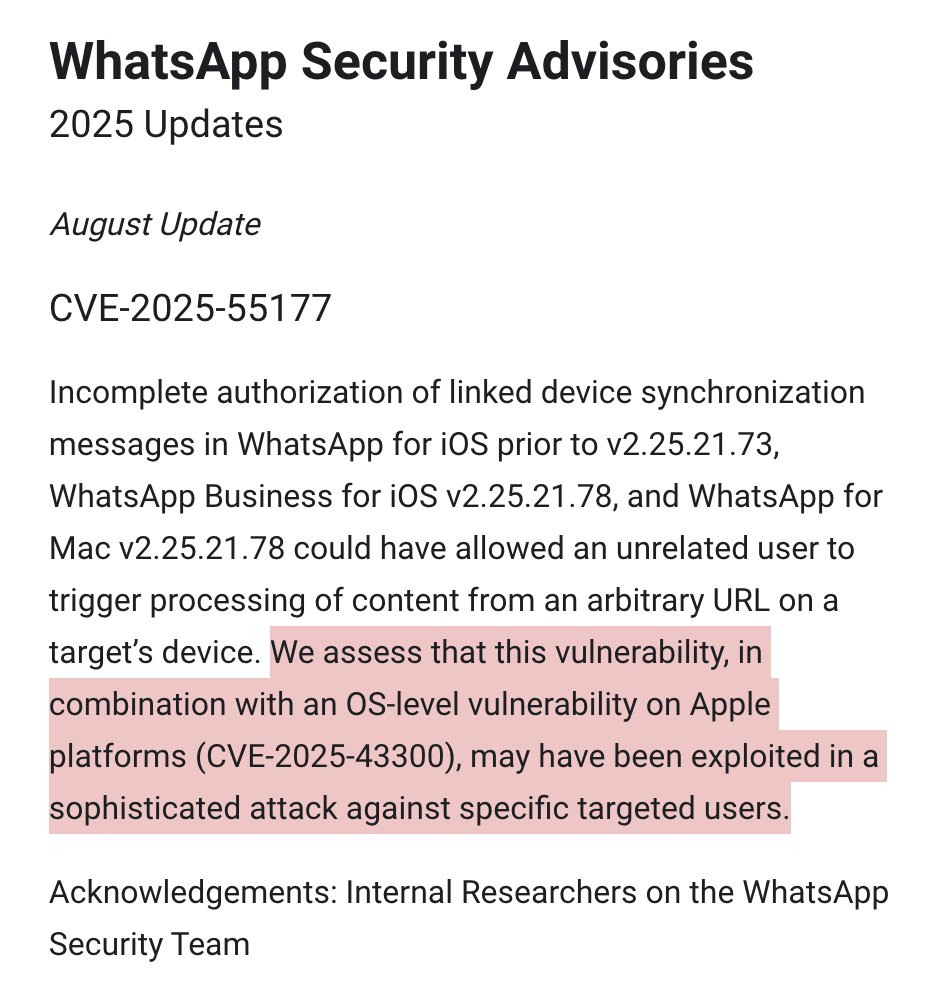
All that came to a crashing halt in 2025 when they got very caught, helping customers hack targets across @WhatsApp.
WhatsApp did the right thing & notified users.
By @razhael



All that came to a crashing halt in 2025 when they got very caught, helping customers hack targets across @WhatsApp.
WhatsApp did the right thing & notified users.
By @razhael
https://x.com/jsrailton/status/1885517753295180248


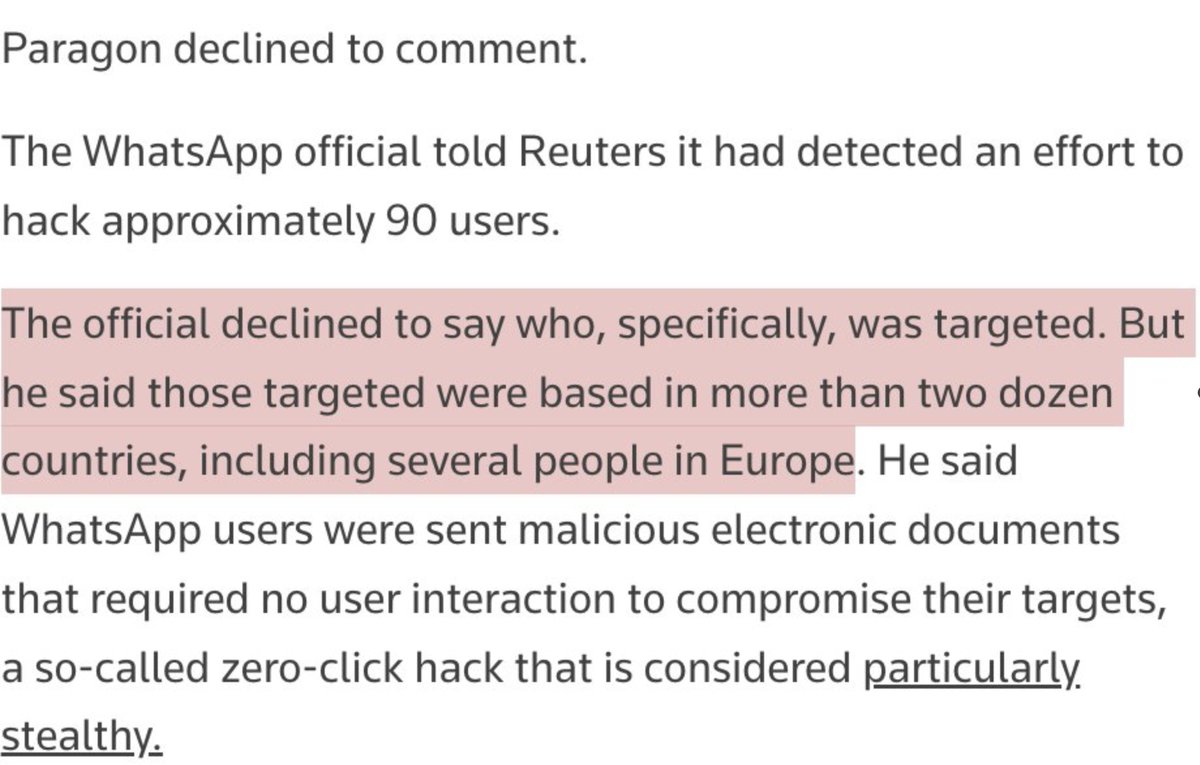
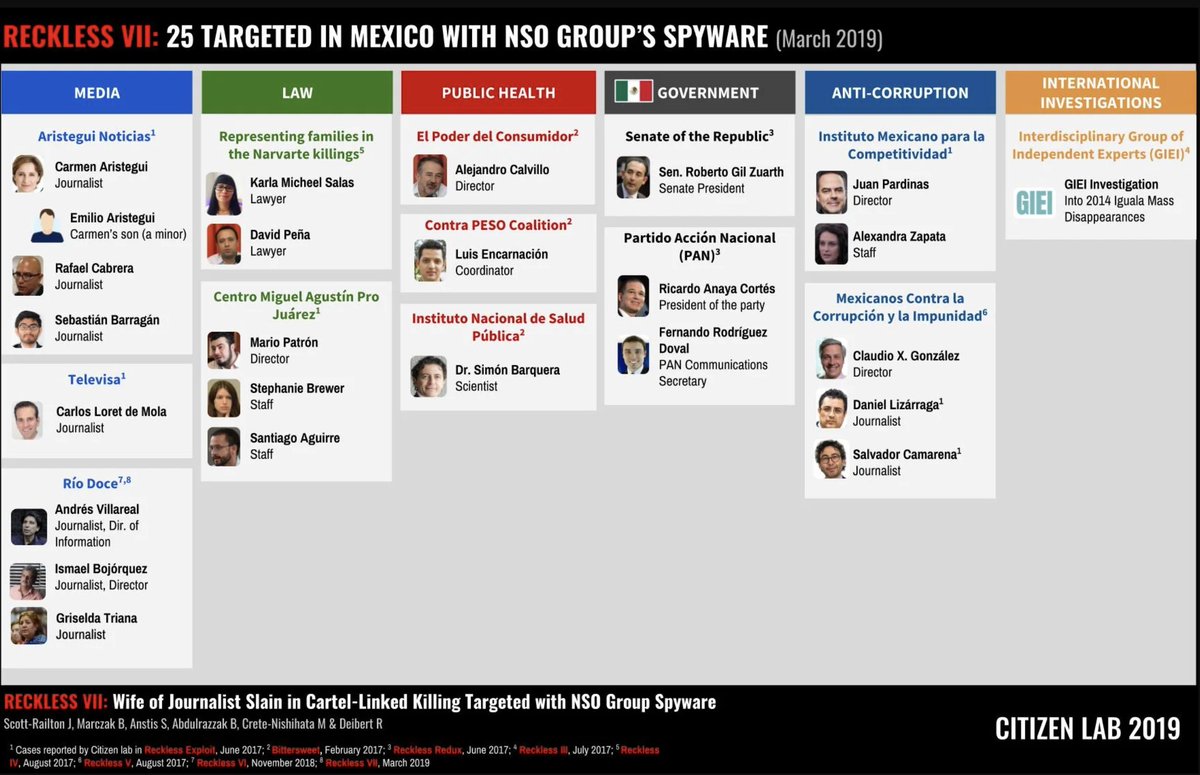
4/ Almost immediately after the WhatsApp notifications, we started learning about the targets.
They weren't the supposed serious criminals... They were Journalists... human rights defenders...groups working on sea rescues.. etc
In other words, a very NSO-like scandal.


They weren't the supposed serious criminals... They were Journalists... human rights defenders...groups working on sea rescues.. etc
In other words, a very NSO-like scandal.
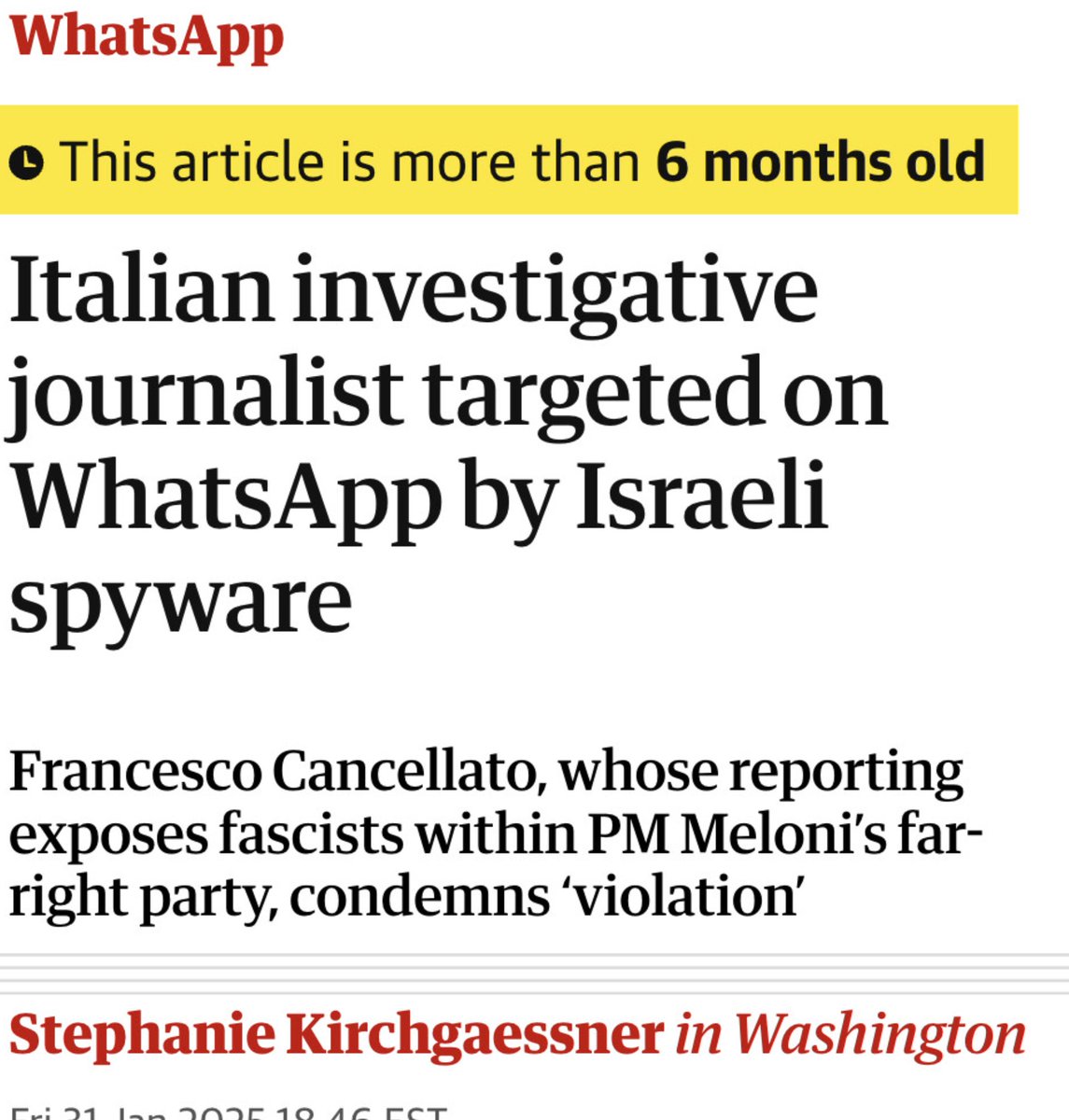
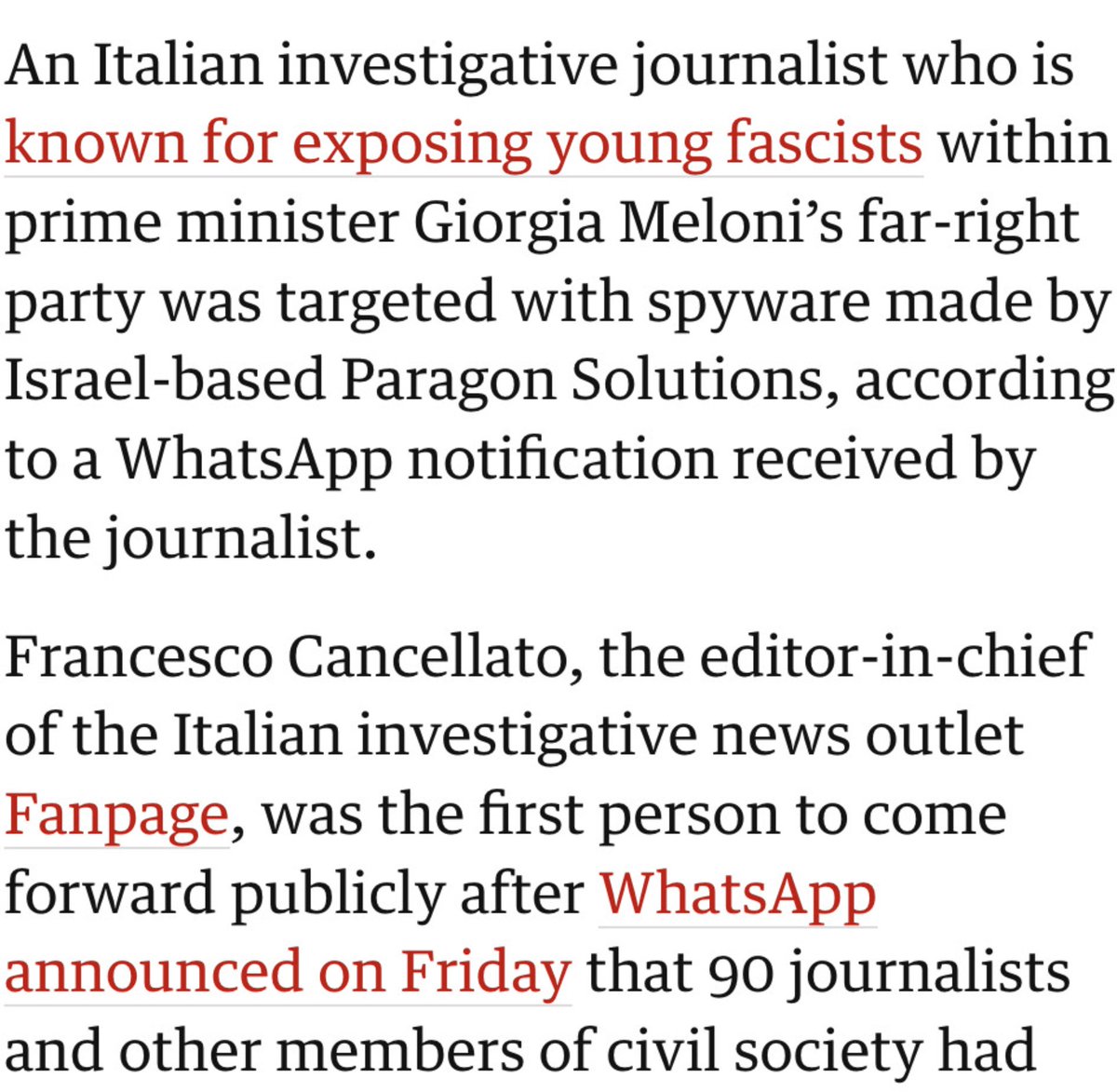
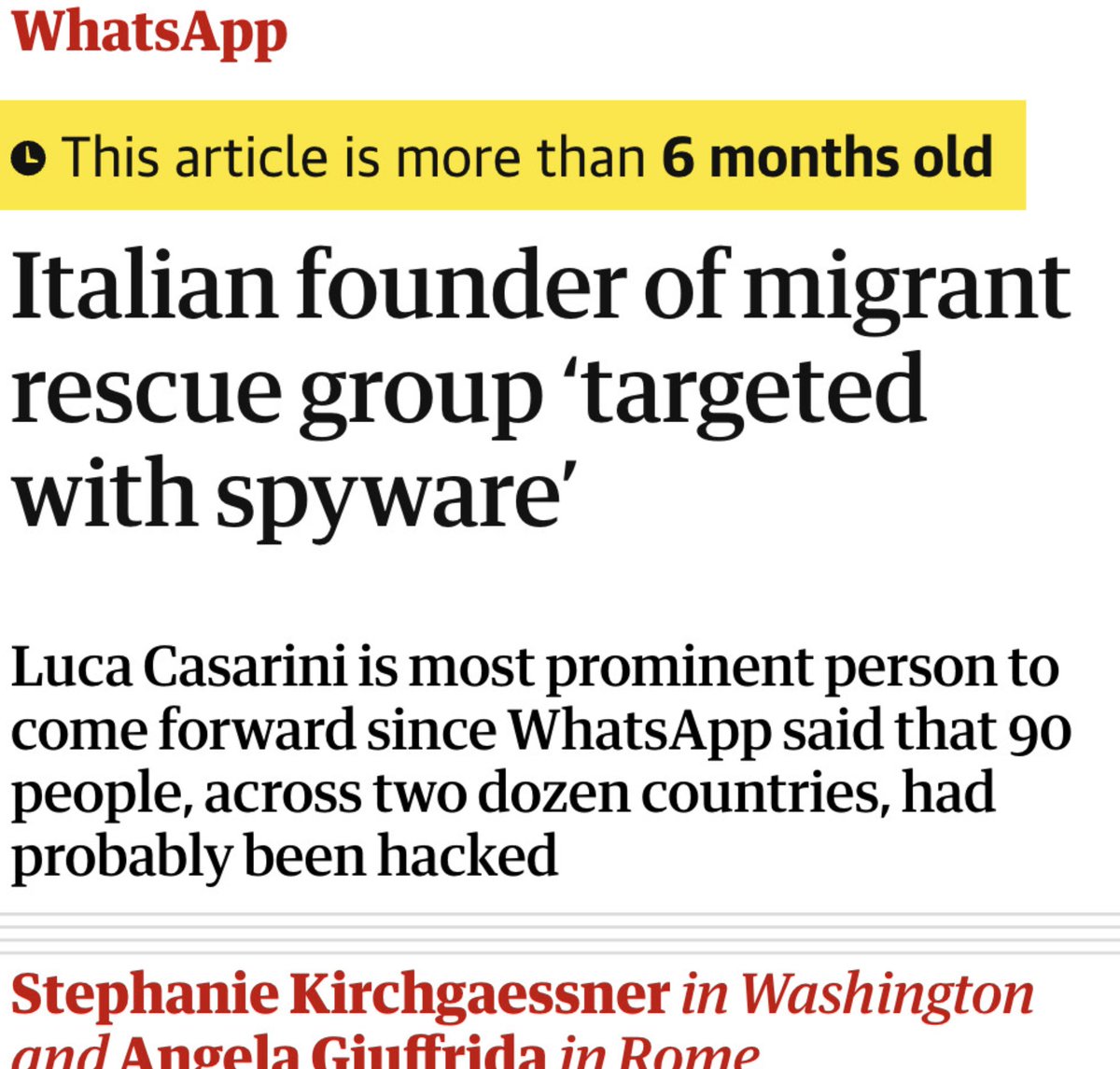
@WhatsApp 5/ Ultimately Paragon & its Italian customer had a massive spyware scandal on their hands.
The conclusion? Deeply unsatisfactory.
Italy admitted hacking some targets, but denied hacking journalists.
The conclusion? Deeply unsatisfactory.
Italy admitted hacking some targets, but denied hacking journalists.
https://x.com/jsrailton/status/1930944633590395248
@WhatsApp 6/ We @citizenlab forensically analyzed a group of cases that got a @whatsapp notification, & a a 2nd round notified by @apple.
We testified to Italy's parliamentary intelligence oversight committee about our findings.
And came to a basic conclusion...


We testified to Italy's parliamentary intelligence oversight committee about our findings.
And came to a basic conclusion...
https://x.com/jsrailton/status/1933135390405464404


7/ After 14 years investigating countless spyware companies, I tell you with confidence:
Mercenary spyware is a power abuse machine incompatible with American constitutional rights and freedoms.
Our legal system isn't designed for it, oversight mechanisms are woefully inadequate to protect our rights...
Mercenary spyware is a power abuse machine incompatible with American constitutional rights and freedoms.
Our legal system isn't designed for it, oversight mechanisms are woefully inadequate to protect our rights...
8/ Tons of loose ends with Paragon. And they haven't been honest about who used their tech to hack journalists in Europe.
But there's something else that should worry everybody about the company: Paragon poses a potentially grave counterintelligence threat to the US. Let me explain,
But there's something else that should worry everybody about the company: Paragon poses a potentially grave counterintelligence threat to the US. Let me explain,
9/ When you use an integrated spyware package to conduct sensitive law enforcement / intelligence business, you have to place a lot of trust in them...
If the developers originate from a foreign intelligence service that aggressively collects against the US government, that should be a huge red flag.
If the developers originate from a foreign intelligence service that aggressively collects against the US government, that should be a huge red flag.
10/ America (or any country) should be maximally wary about using foreign-developed surveillance tech for the same reason that America shouldn't operate a Chinese-made stealth fighter.
So, have Paragon's spyware, people & ops been aggressively vetted for technical and human counterintelligence risks?
So, have Paragon's spyware, people & ops been aggressively vetted for technical and human counterintelligence risks?
11/ Paragon's #Graphite mercenary spyware shares the same downsides as other products in their class:
❌They keep getting caught
We researchers aren't the only ones that have found techniques for tracking and identifying Paragon spyware... I'm sure hostile govs have too.
❌Customers fate share.
Since all customers roll the same tech, when one gets caught it impacts & potentially exposes everyones' activities.
Now, that fate sharing will include US law enforcement activity.
❌They keep getting caught
We researchers aren't the only ones that have found techniques for tracking and identifying Paragon spyware... I'm sure hostile govs have too.
❌Customers fate share.
Since all customers roll the same tech, when one gets caught it impacts & potentially exposes everyones' activities.
Now, that fate sharing will include US law enforcement activity.
12/ What can you do? Take 5 minutes and call your member of Congress.
Ask them to request a briefing on Paragon.
They should ask whether the company was properly vetted & reviewed.
What is the oversight mechanism for this maximally invasive technology?
What are the guardrails? How would abuses be handled? Etc.
Ask them to request a briefing on Paragon.
They should ask whether the company was properly vetted & reviewed.
What is the oversight mechanism for this maximally invasive technology?
What are the guardrails? How would abuses be handled? Etc.
@WhatsApp @citizenlab @Apple 13/ Here's the thing. You probably know that mercenary spyware like #Pegasus gets sold to dictators.
Who, predictably, abuse it.
But We have a growing pile of cases where spyware is sold to democracies... and then gets abused.
Why?
Who, predictably, abuse it.
But We have a growing pile of cases where spyware is sold to democracies... and then gets abused.
Why?
14/ History shows: secret surveillance usually winds up abused.
The history of the US is littered with surveillance abuses.
Thing is, our phones offer an unprecedented window into our lives.
Making zero-click mercenary spyware an especially grave risk to all our freedoms.
The history of the US is littered with surveillance abuses.
Thing is, our phones offer an unprecedented window into our lives.
Making zero-click mercenary spyware an especially grave risk to all our freedoms.
15/ If the government has wants access to your accounts for law enforcement...they have to prepare a judicially authorized request and send it to the company, which reviews it.
Mercenary spyware bypasses any external review.
And the whole industry behind it seeks maximum obscurity.
Mercenary spyware bypasses any external review.
And the whole industry behind it seeks maximum obscurity.
@WhatsApp @citizenlab @Apple 16/ Ah, I was so busy avoiding putting a link in the 1st post that I forgot to link the original article!
Here it is. Kudos as ever to the journalists that live & breathe procurement documents
jackpoulson.substack.com/p/exclusive-ic…
Here it is. Kudos as ever to the journalists that live & breathe procurement documents
jackpoulson.substack.com/p/exclusive-ic…
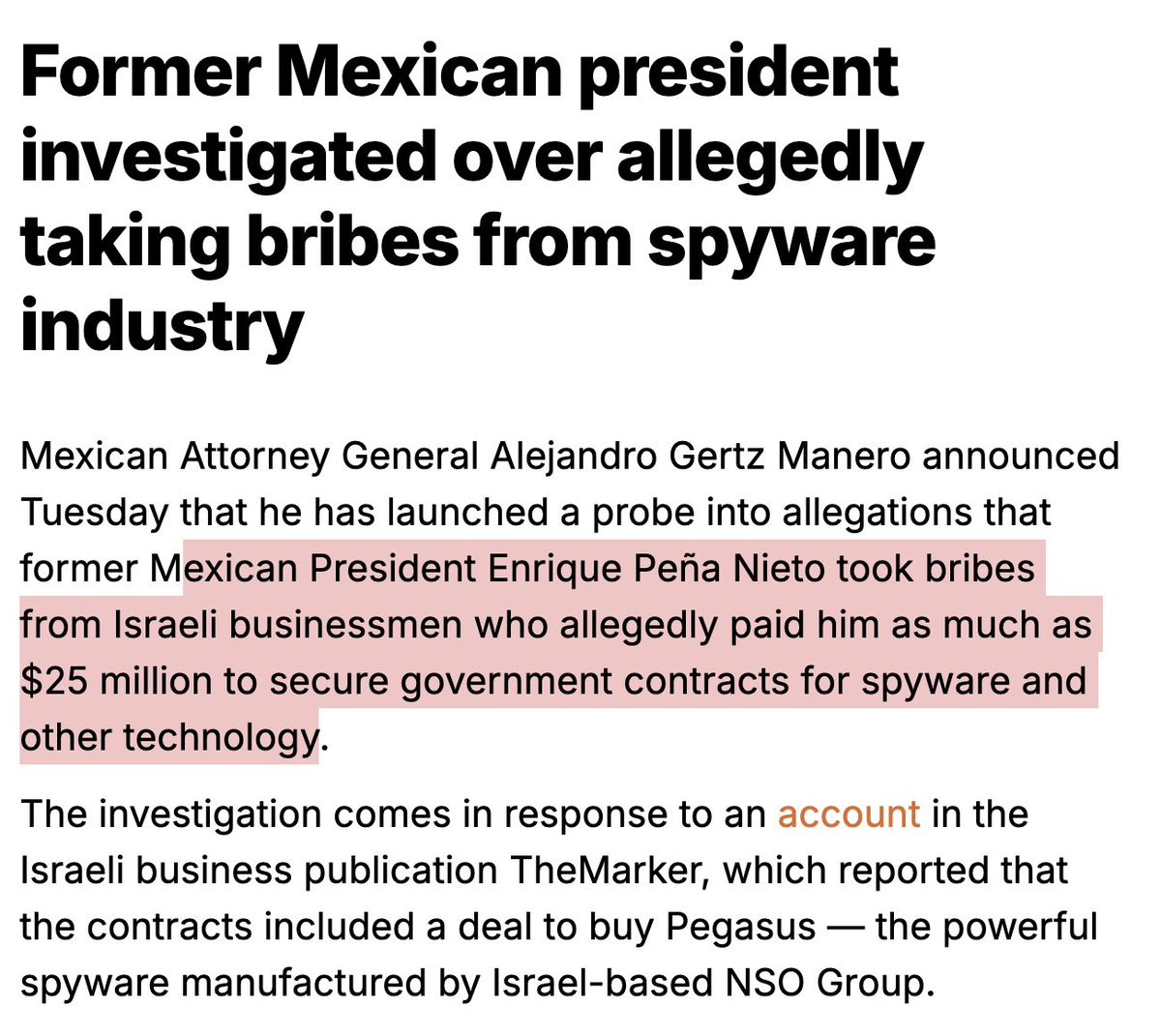
17/ Concerned about #Paragon's willingness to protect national security & counterintelligence risks? As an American, you should be.
I wish you were able to watch this Israeli KAN11 (Public TV) documentary...
Paragon comes across as a company focused on profit first, and not protecting any country's national security.
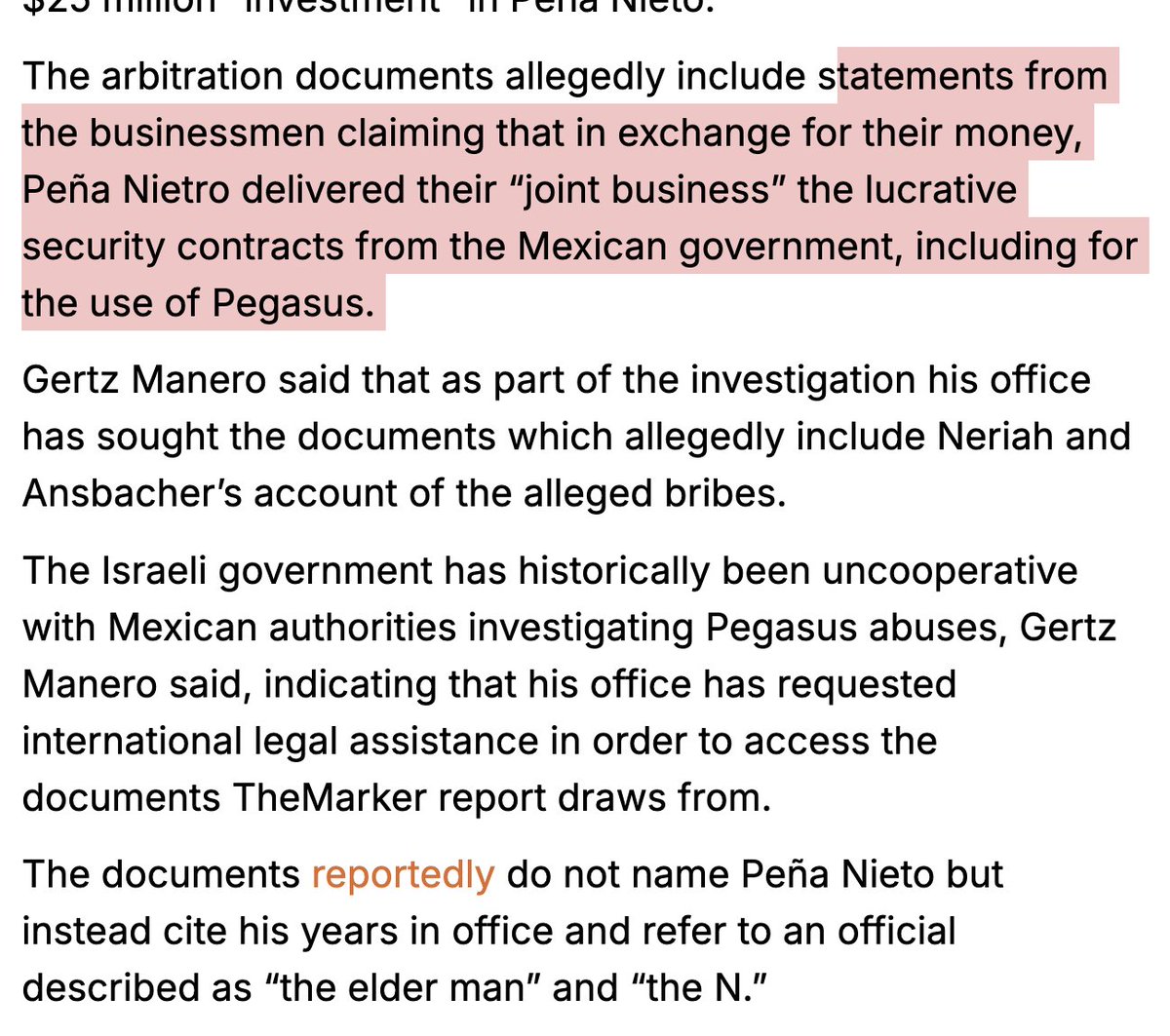
For example, the documentary paints a picture of Paragon as actively harming Israel's national security:
- draining Israel's best and brightest into the private sector during war
Hilariously, the co-founder Ehud Schneorson had apparently won awards for preventing brain drain.. and protecting military talent. Only to turn around and use this knowledge to recruit.
- Harming Israel's warfighting by using the same techniques for hacking that were being actively used by Israel, then getting caught, which caused the techniques to stop working.
But that's only the beginning.
It shows that the Israeli government was worried about Paragon passing along sensitive military information to the US company that acquired it.
(Raising key questions about just how much oversight and control either government has)
The documentary also points to the fact that Paragon has no meaningful way to prevent misuse.
Disclaimer: I don't speak Hebrew so I had to rely on machine translation while watching this.
youtube.com/watch?v=hfnK7_…
I wish you were able to watch this Israeli KAN11 (Public TV) documentary...
Paragon comes across as a company focused on profit first, and not protecting any country's national security.
For example, the documentary paints a picture of Paragon as actively harming Israel's national security:
- draining Israel's best and brightest into the private sector during war
Hilariously, the co-founder Ehud Schneorson had apparently won awards for preventing brain drain.. and protecting military talent. Only to turn around and use this knowledge to recruit.
- Harming Israel's warfighting by using the same techniques for hacking that were being actively used by Israel, then getting caught, which caused the techniques to stop working.
But that's only the beginning.
It shows that the Israeli government was worried about Paragon passing along sensitive military information to the US company that acquired it.
(Raising key questions about just how much oversight and control either government has)
The documentary also points to the fact that Paragon has no meaningful way to prevent misuse.
Disclaimer: I don't speak Hebrew so I had to rely on machine translation while watching this.
youtube.com/watch?v=hfnK7_…
18/ Coda: I can imagine a self-styled spyware realist that might say "hey look every government needs some spyware, and Paragon isn't as bad as NSO, especially if it's got a US owner now"
Respectfully, here are some questions to ask them:
American Security
(a) Does any evidence let us be supremely confident that Paragon does not pose a counterintelligence risks to the US?
(b) Were American companies without any concerning foreign intelligence links considered for this contract first?
US Rights & Laws
(c) Does the US have adequate legal oversight and judicial authorization for using zero-click spyware?
(d) Do you personally feel that there is a risk of a current/future administration abusing spyware for political ends?
(e) Are you familiar with the history of political abuses of surveillance powers by the US government?
Respectfully, here are some questions to ask them:
American Security
(a) Does any evidence let us be supremely confident that Paragon does not pose a counterintelligence risks to the US?
(b) Were American companies without any concerning foreign intelligence links considered for this contract first?
US Rights & Laws
(c) Does the US have adequate legal oversight and judicial authorization for using zero-click spyware?
(d) Do you personally feel that there is a risk of a current/future administration abusing spyware for political ends?
(e) Are you familiar with the history of political abuses of surveillance powers by the US government?
• • •
Missing some Tweet in this thread? You can try to
force a refresh