⚠️ THREAD: The Bio-Digital Kill Switch ⚠️
This is a thought experiment, not a claim.
I’m showing how existing technology could be combined to create a system so powerful, it could control life and death without leaving fingerprints.
Everything here is real and documented.
The only question is how far it’s already been connected. 🧵
This is a thought experiment, not a claim.
I’m showing how existing technology could be combined to create a system so powerful, it could control life and death without leaving fingerprints.
Everything here is real and documented.
The only question is how far it’s already been connected. 🧵
⚠️ THREAD: The Snake Bite System ⚠️
How a bio-digital kill switch could be built today using tech that already exists.
This is a thought experiment, but every piece I show you is real and documented.
The question isn’t whether it can be done.
The question is who’s connecting the dots.
The three layers of control
To create a silent kill switch, you need three layers:
Biological: a change in your body that makes you susceptible.
Digital: a device tethered to your identity, always monitoring.
Network: the infrastructure to target and trigger remotely.
All three layers already exist.
And are already integrated in to society through mRNA transfection, eSIM, and 5G…
How a bio-digital kill switch could be built today using tech that already exists.
This is a thought experiment, but every piece I show you is real and documented.
The question isn’t whether it can be done.
The question is who’s connecting the dots.
The three layers of control
To create a silent kill switch, you need three layers:
Biological: a change in your body that makes you susceptible.
Digital: a device tethered to your identity, always monitoring.
Network: the infrastructure to target and trigger remotely.
All three layers already exist.
And are already integrated in to society through mRNA transfection, eSIM, and 5G…
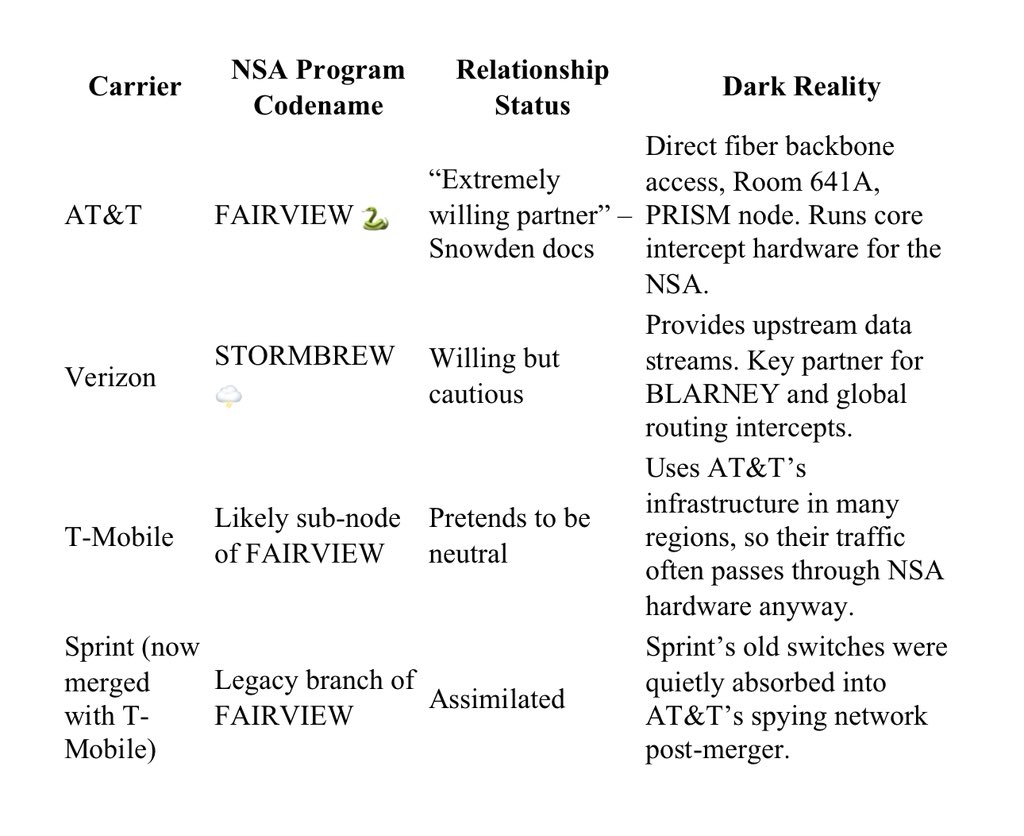
Digital identity: eSIM backdoor
Modern phones no longer rely on removable SIM cards.
They use eSIMs…
virtual SIMs that can be programmed remotely.
Patents show they can store multiple profiles, which can be:
- Added
- Deleted
- Activated
Without your knowledge.
Patent US10715978B2 – remote provisioning of multiple eSIM profiles
Patent US20170289788A1 – silent activation/deletion of profiles
This means a second, hidden line can run on your phone… invisible to you.
The kicker… most networks won’t let you use both eSIMs which means a backdoor is open at all times.
Modern phones no longer rely on removable SIM cards.
They use eSIMs…
virtual SIMs that can be programmed remotely.
Patents show they can store multiple profiles, which can be:
- Added
- Deleted
- Activated
Without your knowledge.
Patent US10715978B2 – remote provisioning of multiple eSIM profiles
Patent US20170289788A1 – silent activation/deletion of profiles
This means a second, hidden line can run on your phone… invisible to you.
The kicker… most networks won’t let you use both eSIMs which means a backdoor is open at all times.
I caught one in the wild
When I switched to a basic dual SIM flip phone, thousands of login attempts flooded in.
Why?
Because someone had been silently using the second eSIM profile on my smartphone to intercept codes and spy.
This is how you’d tether a biological “target” to a digital control grid… silently.
When I switched to a basic dual SIM flip phone, thousands of login attempts flooded in.
Why?
Because someone had been silently using the second eSIM profile on my smartphone to intercept codes and spy.
This is how you’d tether a biological “target” to a digital control grid… silently.
Network targeting: 5G precision beams
5G isn’t just “faster internet.”
It uses beamforming…
steering highly focused RF beams to specific devices, down to a few meters.
This precision isn’t just for speed.
It creates the perfect weapon delivery system:
- Pinpoint a single device.
- Send a custom signal or payload.
- No one else nearby affected.
Proof: Beamforming in 5G (the receipts)
“A 5G NR FR2 Beamforming System with Integrated Transceiver Module”
Sensors, 2024 Bhatta, Kamrojjaman, Sim & Kim.
They built a system at 28 GHz (in the mmWave band) with an 8×7 antenna array + custom beamforming transceiver. The beam can steer horizontally from ~–50° to +50°, demonstrating precise directional control.
“Broad beamforming technology in 5G Massive MIMO”
Ericsson tech-review article, Oct 2023.
Describes DPBF (Dual-Polarized Beamforming) to control beam shapes and pointing directions, both for wide broadcast/control signals and more focused data beams. Shows how real networks use adaptive beamforming in Massive MIMO setups.
Patent “Facilitation of beamforming utilizing interpolation for 5G or other” (US20220408427A1)
Covers methods to facilitate beamforming in 5G via interpolation, channel state info (CSI), etc. This shows legal/industry work on manipulating signal direction & shape.
“Massive MIMO in 5G: How Beamforming, Codebooks, and Feedback Enable Larger Arrays”
arXiv, 2023… Dreifuerst & Heath Jr.
Explains how 5G uses large antenna arrays + feedback from devices (“codebooks”) to dynamically adjust beams (“beam-management”) so signals go where they’re needed, even as users move.
5G isn’t just “faster internet.”
It uses beamforming…
steering highly focused RF beams to specific devices, down to a few meters.
This precision isn’t just for speed.
It creates the perfect weapon delivery system:
- Pinpoint a single device.
- Send a custom signal or payload.
- No one else nearby affected.
Proof: Beamforming in 5G (the receipts)
“A 5G NR FR2 Beamforming System with Integrated Transceiver Module”
Sensors, 2024 Bhatta, Kamrojjaman, Sim & Kim.
They built a system at 28 GHz (in the mmWave band) with an 8×7 antenna array + custom beamforming transceiver. The beam can steer horizontally from ~–50° to +50°, demonstrating precise directional control.
“Broad beamforming technology in 5G Massive MIMO”
Ericsson tech-review article, Oct 2023.
Describes DPBF (Dual-Polarized Beamforming) to control beam shapes and pointing directions, both for wide broadcast/control signals and more focused data beams. Shows how real networks use adaptive beamforming in Massive MIMO setups.
Patent “Facilitation of beamforming utilizing interpolation for 5G or other” (US20220408427A1)
Covers methods to facilitate beamforming in 5G via interpolation, channel state info (CSI), etc. This shows legal/industry work on manipulating signal direction & shape.
“Massive MIMO in 5G: How Beamforming, Codebooks, and Feedback Enable Larger Arrays”
arXiv, 2023… Dreifuerst & Heath Jr.
Explains how 5G uses large antenna arrays + feedback from devices (“codebooks”) to dynamically adjust beams (“beam-management”) so signals go where they’re needed, even as users move.
Biological layer: the spike code (the Venom)
mRNA is software for your cells.
In 2022, researchers at Lund University showed Pfizer’s mRNA (BNT162b2) reverse transcribed into DNA in human liver cells in vitro.
Aldén et al., Intracellular Reverse Transcription of Pfizer BioNTech COVID-19 mRNA Vaccine (2022)
Other studies confirmed that SARS-CoV-2 RNA can reverse transcribe and integrate into the genome under certain conditions (stress).
Once embedded, this code is persistent.
It just needs to be activated…
And what activates this venom mimicker people were “spiked” with?
mRNA is software for your cells.
In 2022, researchers at Lund University showed Pfizer’s mRNA (BNT162b2) reverse transcribed into DNA in human liver cells in vitro.
Aldén et al., Intracellular Reverse Transcription of Pfizer BioNTech COVID-19 mRNA Vaccine (2022)
Other studies confirmed that SARS-CoV-2 RNA can reverse transcribe and integrate into the genome under certain conditions (stress).
Once embedded, this code is persistent.
It just needs to be activated…
And what activates this venom mimicker people were “spiked” with?
“Venom-mimic” angles on spike (what’s actually in the literature)
- nAChR (nicotinic acetylcholine receptor) interaction signals.
Experiments show spike ectodomain can modulate α7 nAChR responses (potentiate/inhibit ACh signals) via an allosteric mechanism in cell systems. That’s a real receptor class targeted by snake neurotoxins (e.g., α-bungarotoxin), hence the “toxin-like” discussion.
- “Toxin-like epitope” reports.
Several computational/structural papers note a short spike motif with homology to snake-toxin sequences and propose potential binding to nAChRs (the “toxin-like” epitope). These are largely in silico/biophysical with mixed follow-ups, but the motif reports exist.
-Superantigen-like region in spike.
Independent teams reported a superantigen-like (SEB-like) motif in S1 that could hyper-activate T cells—offered as a hypothesis for MIS-C/TSS-like inflammation. Evidence includes structural modeling and immunologic profiles in patients; note that one study argues spike lacks intrinsic SAg activity, so this remains debated.
- Integrin (“RGD”) docking avenue.
Spike carries an RGD motif; multiple studies suggest it can bind integrins and trigger downstream signaling (e.g., TGF-β). Others contest practical binding under native conformations. Bottom line: plausible but context-dependent.
Takeaway: Spike has motifs that hit systems also targeted by venoms (nAChRs; immune superactivation; integrins). That’s where the “venom-mimic” language comes from. The strength of evidence ranges from direct cell data (nAChR modulation) to in silico homology that needs more in-vivo proof.
- nAChR (nicotinic acetylcholine receptor) interaction signals.
Experiments show spike ectodomain can modulate α7 nAChR responses (potentiate/inhibit ACh signals) via an allosteric mechanism in cell systems. That’s a real receptor class targeted by snake neurotoxins (e.g., α-bungarotoxin), hence the “toxin-like” discussion.
- “Toxin-like epitope” reports.
Several computational/structural papers note a short spike motif with homology to snake-toxin sequences and propose potential binding to nAChRs (the “toxin-like” epitope). These are largely in silico/biophysical with mixed follow-ups, but the motif reports exist.
-Superantigen-like region in spike.
Independent teams reported a superantigen-like (SEB-like) motif in S1 that could hyper-activate T cells—offered as a hypothesis for MIS-C/TSS-like inflammation. Evidence includes structural modeling and immunologic profiles in patients; note that one study argues spike lacks intrinsic SAg activity, so this remains debated.
- Integrin (“RGD”) docking avenue.
Spike carries an RGD motif; multiple studies suggest it can bind integrins and trigger downstream signaling (e.g., TGF-β). Others contest practical binding under native conformations. Bottom line: plausible but context-dependent.
Takeaway: Spike has motifs that hit systems also targeted by venoms (nAChRs; immune superactivation; integrins). That’s where the “venom-mimic” language comes from. The strength of evidence ranges from direct cell data (nAChR modulation) to in silico homology that needs more in-vivo proof.
Reverse transcription / “embedding” under stress (why stress matters)
Reverse-transcribed spike mRNA in vitro.
The Lund group reported cDNA from BNT162b2 mRNA in human liver cell lines (Huh-7). That’s in vitro, not proof of genome integration in living people…
but it establishes mechanism plausibility (mRNA → cDNA) under certain conditions (stress = lockdowns and uncertainty).
Viral RNA integration signals (lab systems; patient tissue signals).
Studies reported reverse-transcribed and potentially integrated SARS-CoV-2 RNA (and chimeric transcripts) in cultured cells; some signals in patient tissues have been described—again, debated and context-limited.
Stress → LINE-1 (endogenous reverse transcriptase) activation.
Reviews and mechanistic work link oxidative/physiologic stress to retrotransposon (LINE-1) reactivation, genome instability, and environments more permissive to reverse-transcription events. Prolonged psychosocial/physiologic stressors plausibly raise the baseline for these mechanisms.
Takeaway: There’s peer-reviewed evidence that reverse transcription can occur in cells and that stress biology can nudge cellular machinery (LINE-1/RT activity) in the wrong direction. Translating that to widespread, durable in vivo genomic insertion is not proven, but the I ingredients exist.
Reverse-transcribed spike mRNA in vitro.
The Lund group reported cDNA from BNT162b2 mRNA in human liver cell lines (Huh-7). That’s in vitro, not proof of genome integration in living people…
but it establishes mechanism plausibility (mRNA → cDNA) under certain conditions (stress = lockdowns and uncertainty).
Viral RNA integration signals (lab systems; patient tissue signals).
Studies reported reverse-transcribed and potentially integrated SARS-CoV-2 RNA (and chimeric transcripts) in cultured cells; some signals in patient tissues have been described—again, debated and context-limited.
Stress → LINE-1 (endogenous reverse transcriptase) activation.
Reviews and mechanistic work link oxidative/physiologic stress to retrotransposon (LINE-1) reactivation, genome instability, and environments more permissive to reverse-transcription events. Prolonged psychosocial/physiologic stressors plausibly raise the baseline for these mechanisms.
Takeaway: There’s peer-reviewed evidence that reverse transcription can occur in cells and that stress biology can nudge cellular machinery (LINE-1/RT activity) in the wrong direction. Translating that to widespread, durable in vivo genomic insertion is not proven, but the I ingredients exist.
“Activation” via 5G/eSIM/RF (what we can and cannot claim)
Solid facts:
eSIM & beamforming are real. eSIM profiles can be remotely provisioned/managed; 5G uses phased-array beamforming to steer narrow, device-specific beams. (already have these receipts.)
Bioelectromagnetics evidence (mixed):
Multiple reviews report RF/EMF can modulate Ca²⁺ signaling (often via VGCCs), ROS/oxidative stress, and heat-shock responses in cells/animals… sometimes yes, sometimes null, depending on frequency, intensity, modulation, and dosimetry.
Credible bridge (if one exists) would look like:
A defined EMF exposure pattern (frequency, modulation, SAR, duty cycle) shown to trigger a reproducible pathway (e.g., Ca²⁺ influx → arrhythmia) in spike-expressing cells/tissue.
Independent replications with rigorous dosimetry.
We don’t have that… yet…
but I am working on it.
I have a method to my madness…
I am thinking out loud.
Bear with me…
I know this is a lot of scientific jargon…
But I will explain it in simple terms…
Solid facts:
eSIM & beamforming are real. eSIM profiles can be remotely provisioned/managed; 5G uses phased-array beamforming to steer narrow, device-specific beams. (already have these receipts.)
Bioelectromagnetics evidence (mixed):
Multiple reviews report RF/EMF can modulate Ca²⁺ signaling (often via VGCCs), ROS/oxidative stress, and heat-shock responses in cells/animals… sometimes yes, sometimes null, depending on frequency, intensity, modulation, and dosimetry.
Credible bridge (if one exists) would look like:
A defined EMF exposure pattern (frequency, modulation, SAR, duty cycle) shown to trigger a reproducible pathway (e.g., Ca²⁺ influx → arrhythmia) in spike-expressing cells/tissue.
Independent replications with rigorous dosimetry.
We don’t have that… yet…
but I am working on it.
I have a method to my madness…
I am thinking out loud.
Bear with me…
I know this is a lot of scientific jargon…
But I will explain it in simple terms…
Why spike is the perfect candidate
The spike protein binds to ACE2 receptors and interacts deeply with cellular pathways.
It’s like a master key, recognized across multiple systems:
- Cardiovascular
- Neurological
- Immune
If reverse-transcribed into your DNA, spike sequences could act as a biological QR code, a receiver ready to respond to external triggers.
Stress and Trauma are the external triggers…
and we have a lot of people becoming unhinged.
The spike protein binds to ACE2 receptors and interacts deeply with cellular pathways.
It’s like a master key, recognized across multiple systems:
- Cardiovascular
- Neurological
- Immune
If reverse-transcribed into your DNA, spike sequences could act as a biological QR code, a receiver ready to respond to external triggers.
Stress and Trauma are the external triggers…
and we have a lot of people becoming unhinged.
Stress is the catalyst
Stress doesn’t just hurt your mind…
it changes your genes.
Lockdowns, fear, isolation, and inflammation all increase oxidative stress, which:
- Activates LINE-1 retrotransposons (your body’s internal reverse transcriptase).
- Increases genomic instability.
- Makes cells more likely to integrate foreign RNA like spike.
Under mass psychological stress, the population itself becomes more “programmable.”
It is the perfect hidden weapon just like the dual eSIM.
Stress doesn’t just hurt your mind…
it changes your genes.
Lockdowns, fear, isolation, and inflammation all increase oxidative stress, which:
- Activates LINE-1 retrotransposons (your body’s internal reverse transcriptase).
- Increases genomic instability.
- Makes cells more likely to integrate foreign RNA like spike.
Under mass psychological stress, the population itself becomes more “programmable.”
It is the perfect hidden weapon just like the dual eSIM.
The theoretical trigger event
Now, combine all three layers:
A hidden eSIM silently listens for network commands.
5G towers lock onto you with a focused beam.
A frequency pulse interacts with spike-primed cells.
Those cells respond…
calcium floods, arrhythmias, seizures, or sudden cell death.
Externally? It looks like natural causes:
“Heart attack.”
“Sudden Adult Death Syndrome.”
“Mysterious seizure.”
Now, combine all three layers:
A hidden eSIM silently listens for network commands.
5G towers lock onto you with a focused beam.
A frequency pulse interacts with spike-primed cells.
Those cells respond…
calcium floods, arrhythmias, seizures, or sudden cell death.
Externally? It looks like natural causes:
“Heart attack.”
“Sudden Adult Death Syndrome.”
“Mysterious seizure.”
The perfect snake bite
It’s a digital venom.
The spike protein is the venom molecule.
Stress during lockdown embedded it deeper into some genomes.
eSIM and 5G act as the fang and delivery system.
No dart, no gunshot, no blood spatter.
Just a silent broadcast and a body dropping…
Or neurological disorders that make some completely unhinged.
It’s a digital venom.
The spike protein is the venom molecule.
Stress during lockdown embedded it deeper into some genomes.
eSIM and 5G act as the fang and delivery system.
No dart, no gunshot, no blood spatter.
Just a silent broadcast and a body dropping…
Or neurological disorders that make some completely unhinged.
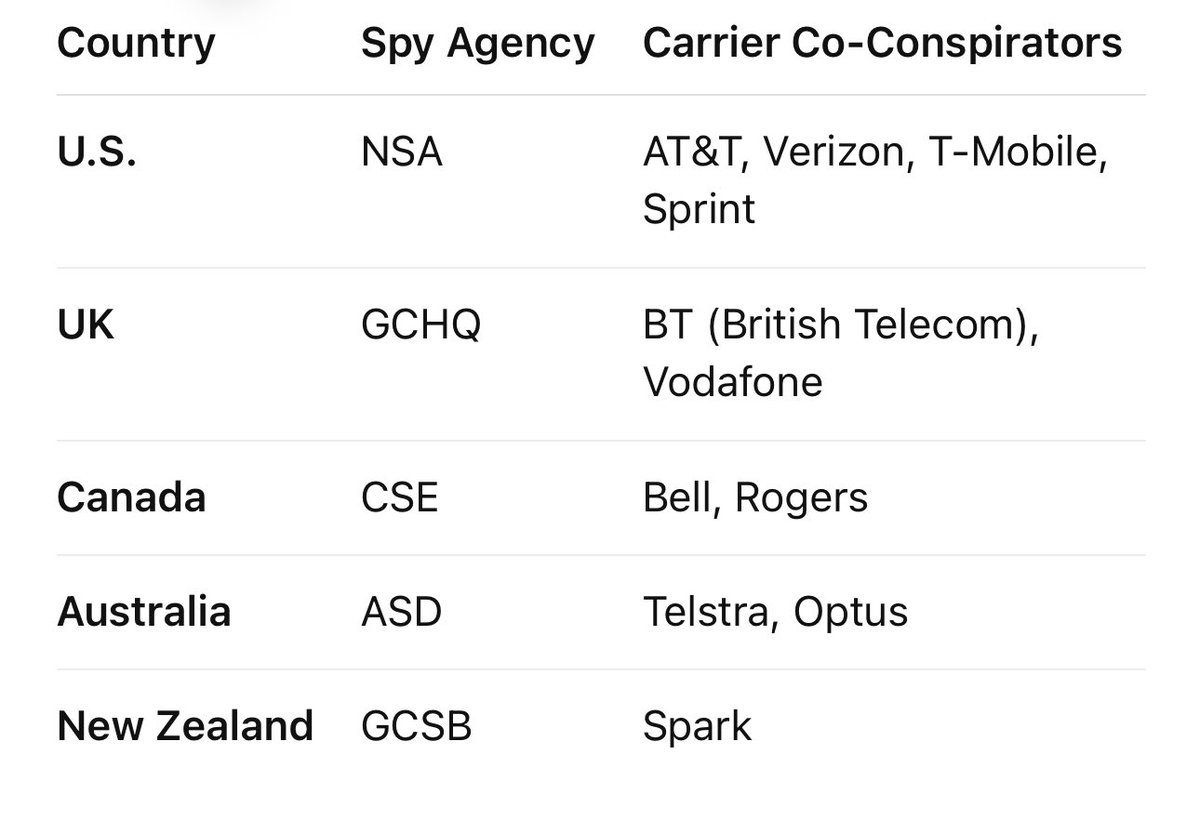
The receipts
Everything I’ve shown you is real:
eSIM patents for silent, remote provisioning (US10715978B2, US20170289788A1).
Studies proving reverse transcription of spike mRNA (Aldén et al., Zhang et al., Doerfler et al.).
Research linking stress to LINE-1 activation and genomic instability.
5G documentation of beamforming and precision device targeting.
The only missing link is intentional integration of these systems.
But the parts are already on the table.
- Spike ↔ α7 nAChR (experimental): “Spike ectodomain potentiates and inhibits α7 nAChR responses” (cell systems).
- “Toxin-like” epitope (homology): Spike region with snake-toxin-like similarity proposed to interact with nAChRs.
- Superantigen-like motif (SAg): S1 region shows SEB-like features linked to MIS-C/T-cell hyperactivation (debated).
- Integrin RGD pathway: Evidence that spike binds α5β1 / uses RGD to signal; also contested studies.
- Reverse transcription (in vitro): BNT162b2 mRNA → cDNA in human liver cell line; mechanism spotlight.
- Stress & LINE-1/oxidative pathways: Stress can increase RT/retrotransposon activity and ROS (mechanistic risk context).
- 5G beamforming (precision): Steerable beams with phased arrays demonstrated in 5G systems.
- RF bioeffects (mixed): Reports of VGCC/Ca²⁺ and ROS modulation vs. reviews showing no confirmed hazard at regulated mmWave levels.
Everything I’ve shown you is real:
eSIM patents for silent, remote provisioning (US10715978B2, US20170289788A1).
Studies proving reverse transcription of spike mRNA (Aldén et al., Zhang et al., Doerfler et al.).
Research linking stress to LINE-1 activation and genomic instability.
5G documentation of beamforming and precision device targeting.
The only missing link is intentional integration of these systems.
But the parts are already on the table.
- Spike ↔ α7 nAChR (experimental): “Spike ectodomain potentiates and inhibits α7 nAChR responses” (cell systems).
- “Toxin-like” epitope (homology): Spike region with snake-toxin-like similarity proposed to interact with nAChRs.
- Superantigen-like motif (SAg): S1 region shows SEB-like features linked to MIS-C/T-cell hyperactivation (debated).
- Integrin RGD pathway: Evidence that spike binds α5β1 / uses RGD to signal; also contested studies.
- Reverse transcription (in vitro): BNT162b2 mRNA → cDNA in human liver cell line; mechanism spotlight.
- Stress & LINE-1/oxidative pathways: Stress can increase RT/retrotransposon activity and ROS (mechanistic risk context).
- 5G beamforming (precision): Steerable beams with phased arrays demonstrated in 5G systems.
- RF bioeffects (mixed): Reports of VGCC/Ca²⁺ and ROS modulation vs. reviews showing no confirmed hazard at regulated mmWave levels.
This is all public information:
Scientists have built programmable “kill switches” for living cells across microbes and human cell therapies. They’re triggered by chemicals, temperature, frequencies, or logic gates, and they work by activating toxins, converting harmless drugs into poisons (HSV-TK), or flipping apoptosis (iCasp9). In cells, stability over evolution is the battle; in human therapies, speed, reliability, and low immunogenicity are king.
This is science that has been occurring over the last decade. And we already know…
once published the technology has been available for years…
usually decades.
Scientists have built programmable “kill switches” for living cells across microbes and human cell therapies. They’re triggered by chemicals, temperature, frequencies, or logic gates, and they work by activating toxins, converting harmless drugs into poisons (HSV-TK), or flipping apoptosis (iCasp9). In cells, stability over evolution is the battle; in human therapies, speed, reliability, and low immunogenicity are king.
This is science that has been occurring over the last decade. And we already know…
once published the technology has been available for years…
usually decades.
The Premise (thought experiment):
A bio-digital “kill chain” could exist if three mature technologies are braided:
1.Biology primed to misfire (spike)
2.Devices tied to your identity and always reachable (eSIM)
3.Networks that can point a signal at you and not your neighbor. (5G)
What’s real today:
- eSIM lets carriers silently add/enable multiple profiles over-the-air. Great for convenience; catastrophic if abused.
- 5G beamforming uses phased arrays to steer narrow, device-specific beams. Precision delivery is no longer science fiction… it’s standard radio engineering.
- Kill switches in biology are proven… in microbes (Deadman/Passcode, CRISPR circuits) and human cell therapies (iCasp9, HSV-TK)…showing we can program life with reliable “off” buttons.
The biological vulnerability (why spike is in the conversation):
- Spike contains motifs that touch systems targeted by toxins (nicotinic receptors, possible superantigen-like regions, integrin/RGD interfaces).
- In-vitro studies show vaccine mRNA or SARS-CoV-2 RNA can be reverse-transcribed to cDNA under specific conditions; stress biology (oxidative load, LINE-1 activity) is known to loosen genomic guardrails.
- Together, that yields a plausible susceptibility pathway: stressed cells made more reactive, potentially expressing spike-related signals longer than intended.
Why the risk matters:
- The control planes already exist: remotely programmable identity (eSIM), precision targeting (5G), and biological systems with known “kill switches.”
- History says capability invites ambition. The gap is not physics; it’s policy, oversight, and intent.
Practical stance (how to live sanely):
- Favor single physical-SIM hardware; audit your carrier account for ghost profiles.
- Reduce ambient stress (digital + physiological)…
it’s not just mental hygiene; it’s molecular hygiene.
- Demand auditable governance around interception, provisioning, and RF safety… trust with verification, not vibes.
If a snake bite is possible, the antidote is awareness: understand the stack (bio, device, network), cut unnecessary attack surfaces, and force sunlight into the control rooms.
Get outside of the grid if you can and recalibrate…
A bio-digital “kill chain” could exist if three mature technologies are braided:
1.Biology primed to misfire (spike)
2.Devices tied to your identity and always reachable (eSIM)
3.Networks that can point a signal at you and not your neighbor. (5G)
What’s real today:
- eSIM lets carriers silently add/enable multiple profiles over-the-air. Great for convenience; catastrophic if abused.
- 5G beamforming uses phased arrays to steer narrow, device-specific beams. Precision delivery is no longer science fiction… it’s standard radio engineering.
- Kill switches in biology are proven… in microbes (Deadman/Passcode, CRISPR circuits) and human cell therapies (iCasp9, HSV-TK)…showing we can program life with reliable “off” buttons.
The biological vulnerability (why spike is in the conversation):
- Spike contains motifs that touch systems targeted by toxins (nicotinic receptors, possible superantigen-like regions, integrin/RGD interfaces).
- In-vitro studies show vaccine mRNA or SARS-CoV-2 RNA can be reverse-transcribed to cDNA under specific conditions; stress biology (oxidative load, LINE-1 activity) is known to loosen genomic guardrails.
- Together, that yields a plausible susceptibility pathway: stressed cells made more reactive, potentially expressing spike-related signals longer than intended.
Why the risk matters:
- The control planes already exist: remotely programmable identity (eSIM), precision targeting (5G), and biological systems with known “kill switches.”
- History says capability invites ambition. The gap is not physics; it’s policy, oversight, and intent.
Practical stance (how to live sanely):
- Favor single physical-SIM hardware; audit your carrier account for ghost profiles.
- Reduce ambient stress (digital + physiological)…
it’s not just mental hygiene; it’s molecular hygiene.
- Demand auditable governance around interception, provisioning, and RF safety… trust with verification, not vibes.
If a snake bite is possible, the antidote is awareness: understand the stack (bio, device, network), cut unnecessary attack surfaces, and force sunlight into the control rooms.
Get outside of the grid if you can and recalibrate…
There’s a reason people are going mad…
And I believe it was planned… at the very least thirty years ago we had the technology.
Thirty years is the generational gap they exploit.
It’s the perfect window: long enough for a generation to forget, for memories to fade, and for old warnings to be dismissed as conspiracy or myth.
Time travel isn’t what most people think.
Some don’t “travel” at all…
they stay ahead by holding back technology.
What you see as new today was already created, tested, and implemented decades ago.
By the time it’s released to the public, the world has moved on, blind to the patterns repeating.
The thirty-year gap isn’t random…
it’s their reset cycle, and most never notice it until it’s too late.
And I believe it was planned… at the very least thirty years ago we had the technology.
Thirty years is the generational gap they exploit.
It’s the perfect window: long enough for a generation to forget, for memories to fade, and for old warnings to be dismissed as conspiracy or myth.
Time travel isn’t what most people think.
Some don’t “travel” at all…
they stay ahead by holding back technology.
What you see as new today was already created, tested, and implemented decades ago.
By the time it’s released to the public, the world has moved on, blind to the patterns repeating.
The thirty-year gap isn’t random…
it’s their reset cycle, and most never notice it until it’s too late.
• • •
Missing some Tweet in this thread? You can try to
force a refresh