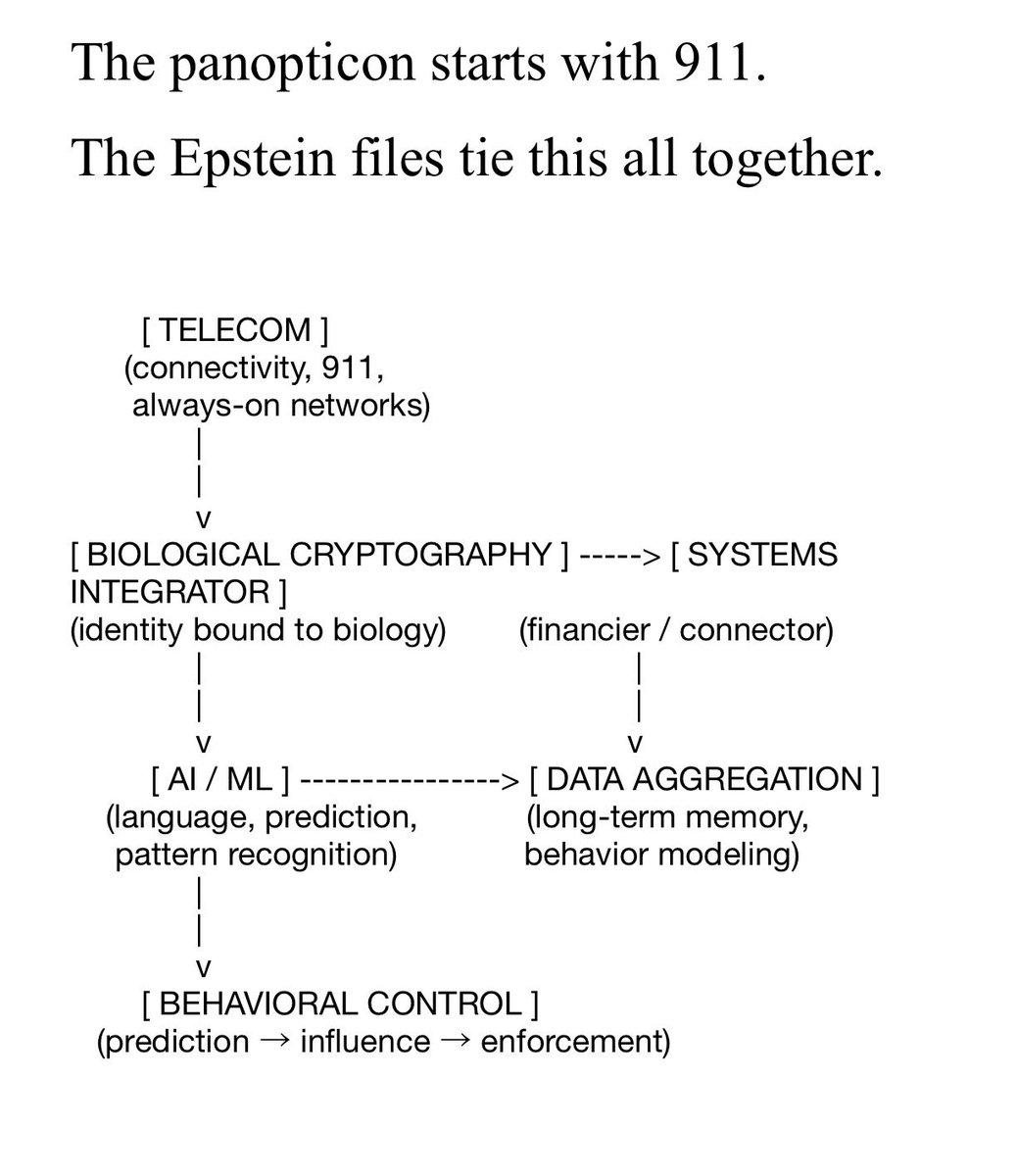
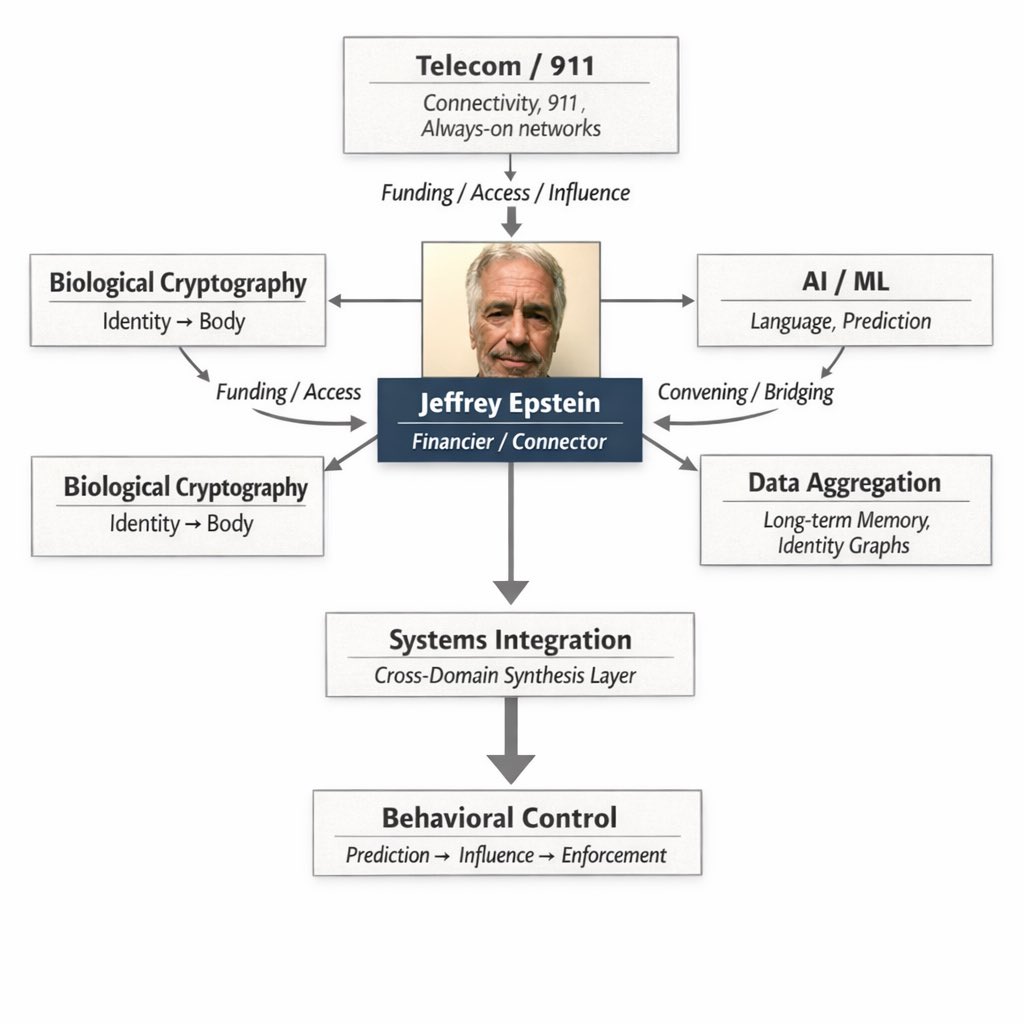
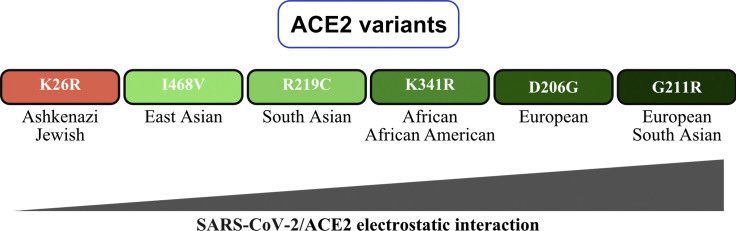
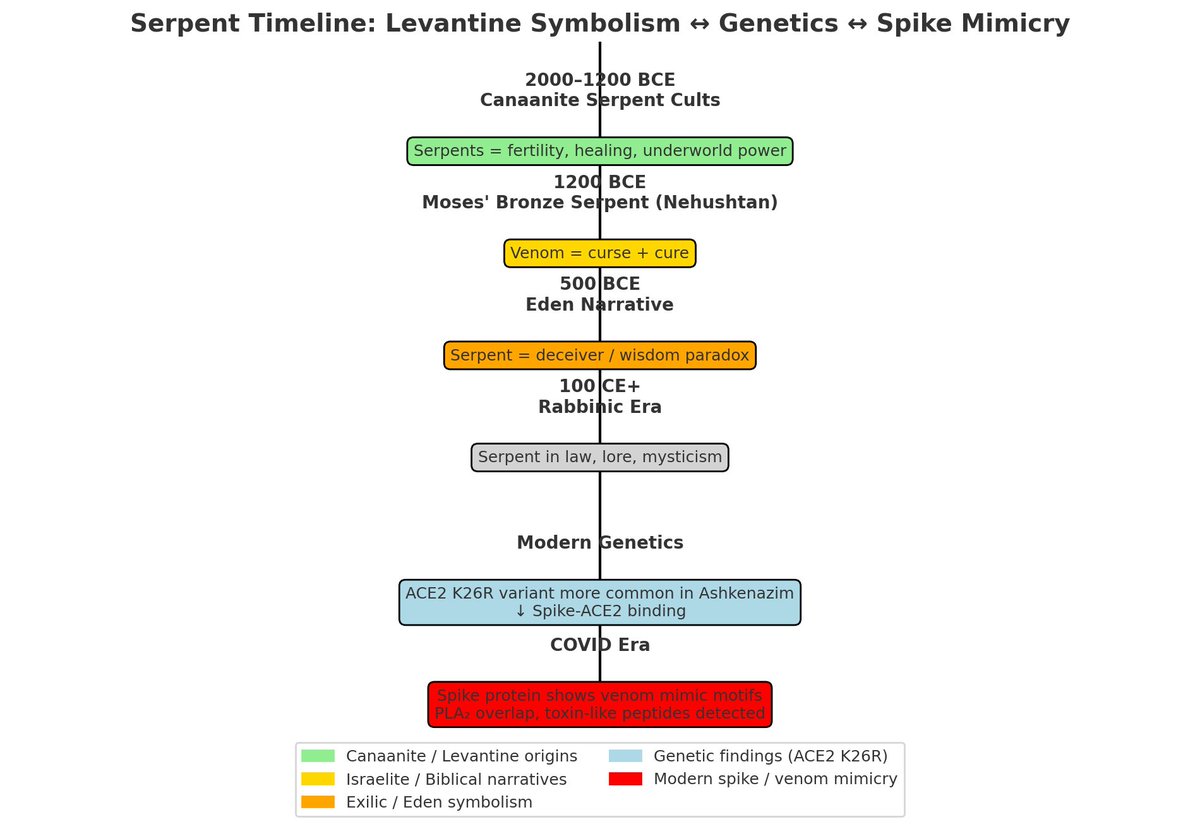
How to Harness your Own Free Energy for Free
Free energy doesn’t have to be complicated… humans have done it for thousands of years before the grid.
Most of the complexity comes from the system itself…
permits, regulations, “certifications”…
all carefully designed to gatekeep what is actually simple and ancient.
This thread 🧵, provides the minimal resources needed to generate free energy for a home or small community, requiring no special expertise and easily shared knowledge.
It provides a full spectrum of free energy harvesting, using what nature provides and what the system throws away. These methods require minimal tools, rely on salvaged or natural materials, and break the illusion that energy must be bought or controlled.
Free energy doesn’t have to be complicated… humans have done it for thousands of years before the grid.
Most of the complexity comes from the system itself…
permits, regulations, “certifications”…
all carefully designed to gatekeep what is actually simple and ancient.
This thread 🧵, provides the minimal resources needed to generate free energy for a home or small community, requiring no special expertise and easily shared knowledge.
It provides a full spectrum of free energy harvesting, using what nature provides and what the system throws away. These methods require minimal tools, rely on salvaged or natural materials, and break the illusion that energy must be bought or controlled.
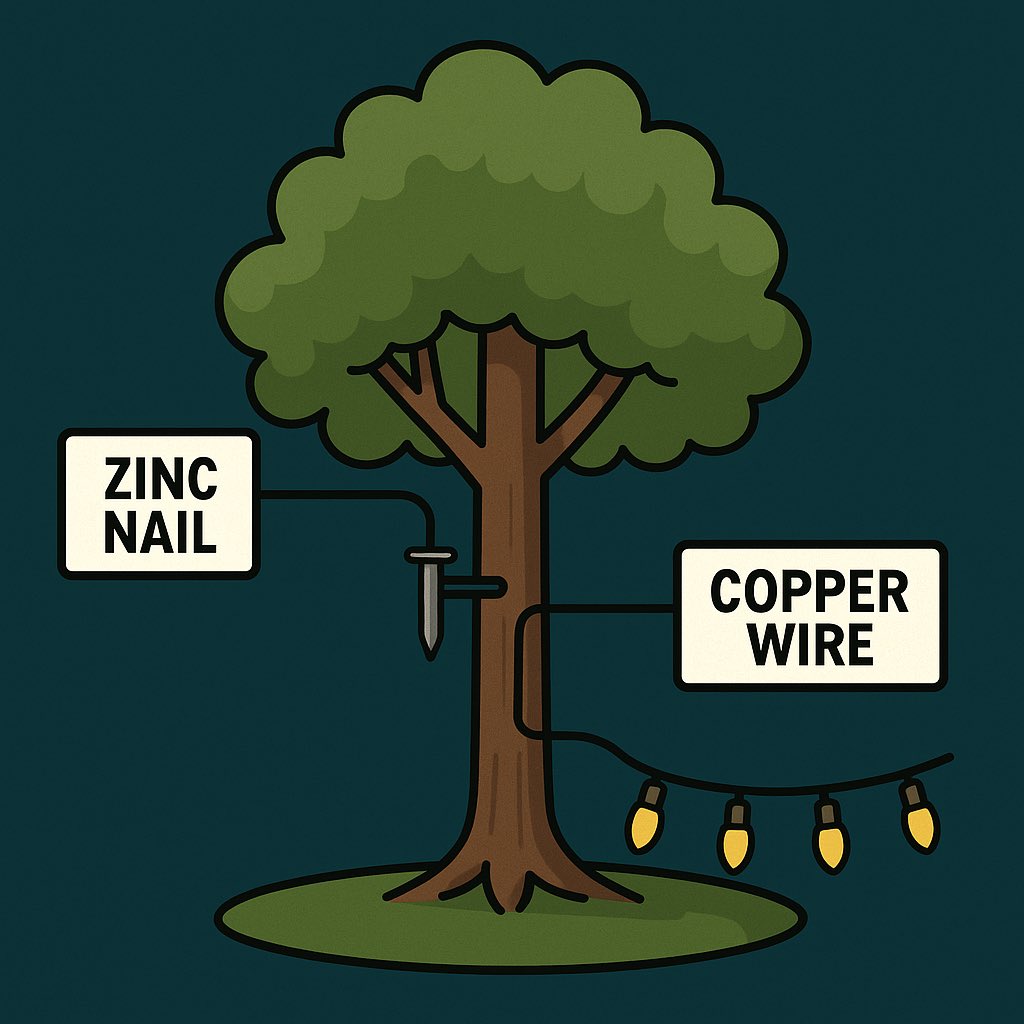
Tree Battery: Step-by-Step
Purpose: Harvest small amounts of bioelectricity from a living tree to power LED lights or small devices.
Materials (Free or Salvaged)
- 1 healthy living tree
- 1 copper wire (1–2 feet long)
- 1 zinc-coated nail (or galvanized steel nail)
- 1 small LED light string or low-voltage device (like a garden light)
Optional: multimeter to measure voltage
Instructions:
1.Choose a Tree:
Select a healthy, well-rooted tree with good moisture content… maples, oaks, or fruit trees work well.
2.Insert Zinc Nail:
Hammer the zinc nail gently into the tree about 1–2 inches deep, at waist height.
3.Place Copper Wire:
Insert the copper wire into the tree a few inches away from the nail.
The zinc acts as the positive terminal, and the copper as the negative terminal.
4.Connect the Circuit:
- Attach a wire from the zinc nail (+) to the positive lead of your LED string or device.
- Attach a wire from the copper (-) to the negative lead.
5.Light It Up:
A single tree produces about 0.5–1 volt.
Chain multiple trees in series to increase voltage…
like batteries linked together.
Output Uses
- Power small LED garden lights.
- Run sensors or tiny electronics.
Purpose: Harvest small amounts of bioelectricity from a living tree to power LED lights or small devices.
Materials (Free or Salvaged)
- 1 healthy living tree
- 1 copper wire (1–2 feet long)
- 1 zinc-coated nail (or galvanized steel nail)
- 1 small LED light string or low-voltage device (like a garden light)
Optional: multimeter to measure voltage
Instructions:
1.Choose a Tree:
Select a healthy, well-rooted tree with good moisture content… maples, oaks, or fruit trees work well.
2.Insert Zinc Nail:
Hammer the zinc nail gently into the tree about 1–2 inches deep, at waist height.
3.Place Copper Wire:
Insert the copper wire into the tree a few inches away from the nail.
The zinc acts as the positive terminal, and the copper as the negative terminal.
4.Connect the Circuit:
- Attach a wire from the zinc nail (+) to the positive lead of your LED string or device.
- Attach a wire from the copper (-) to the negative lead.
5.Light It Up:
A single tree produces about 0.5–1 volt.
Chain multiple trees in series to increase voltage…
like batteries linked together.
Output Uses
- Power small LED garden lights.
- Run sensors or tiny electronics.
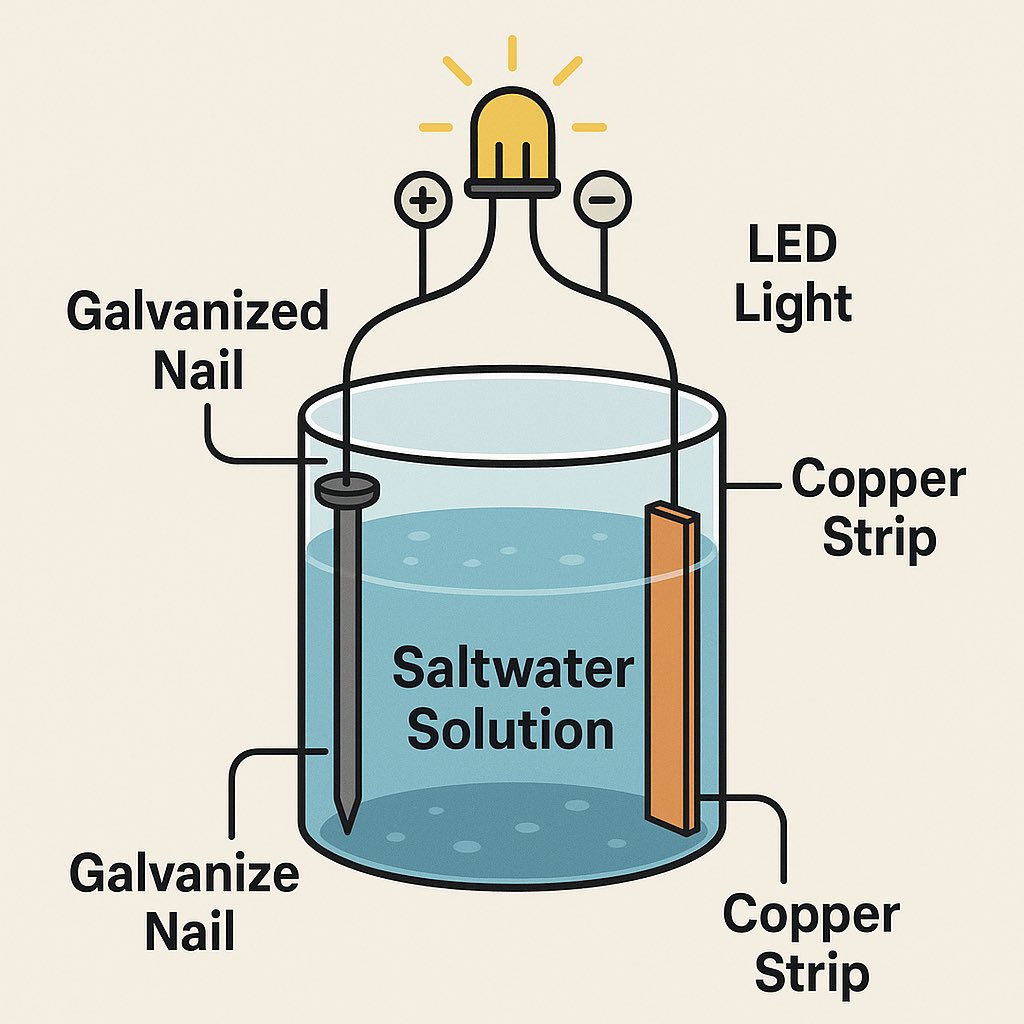
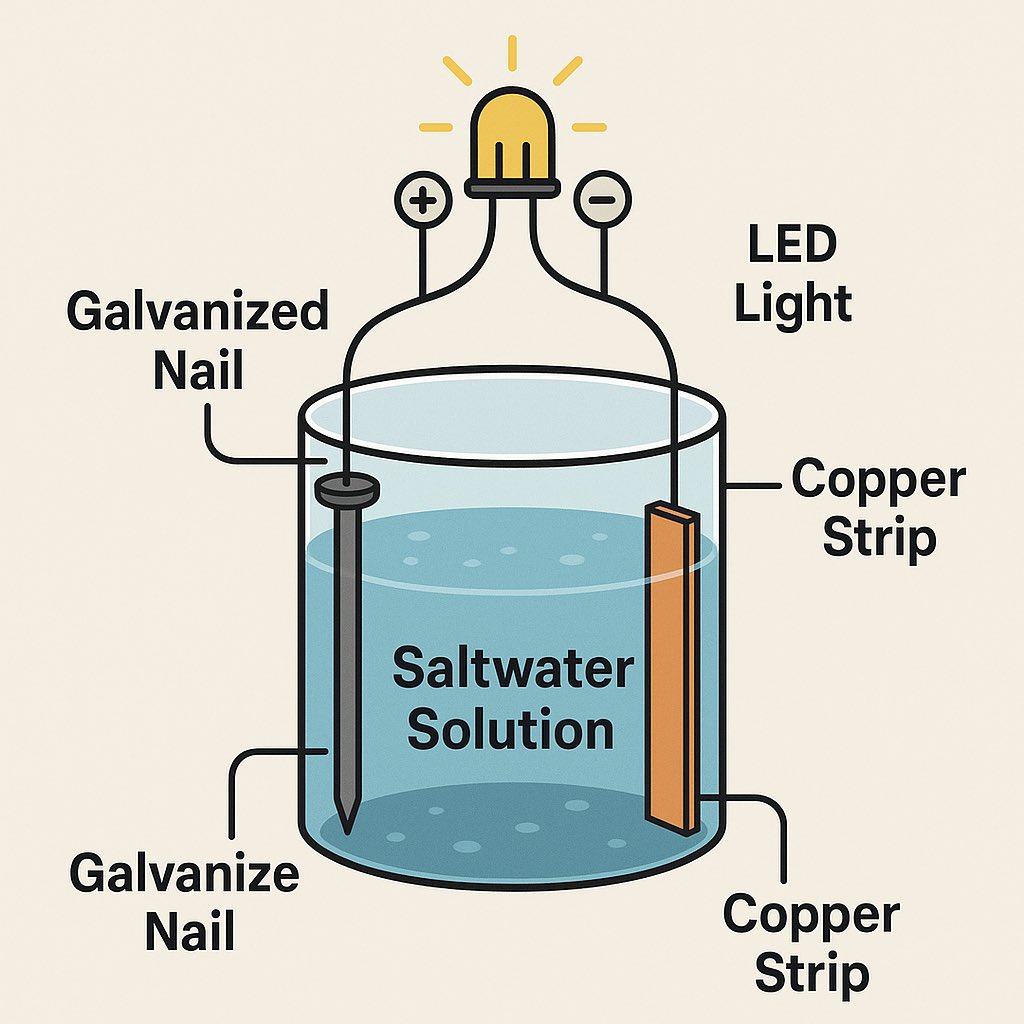
Saltwater Battery (Ultra Simple & Non-Toxic)
Best For: Beginners, teaching energy principles, low-power lighting.
Materials:
- Plastic or glass container (jar or bucket)
- Saltwater solution (salt + water)
- Copper strip or wire
- Zinc nail, galvanized nail, or scrap steel
- Wires to connect
Instructions:
1.Mix saltwater until fully dissolved.
2.Place the zinc nail on one side of the container.
3.Place the copper strip on the opposite side.
4.Attach wires to each and connect to a small LED or device.
5.For higher voltage, connect multiple jars in series (like linking AA batteries).
Output:
Enough to power LED lights, sensors, or trickle charge a small battery bank.
Best For: Beginners, teaching energy principles, low-power lighting.
Materials:
- Plastic or glass container (jar or bucket)
- Saltwater solution (salt + water)
- Copper strip or wire
- Zinc nail, galvanized nail, or scrap steel
- Wires to connect
Instructions:
1.Mix saltwater until fully dissolved.
2.Place the zinc nail on one side of the container.
3.Place the copper strip on the opposite side.
4.Attach wires to each and connect to a small LED or device.
5.For higher voltage, connect multiple jars in series (like linking AA batteries).
Output:
Enough to power LED lights, sensors, or trickle charge a small battery bank.
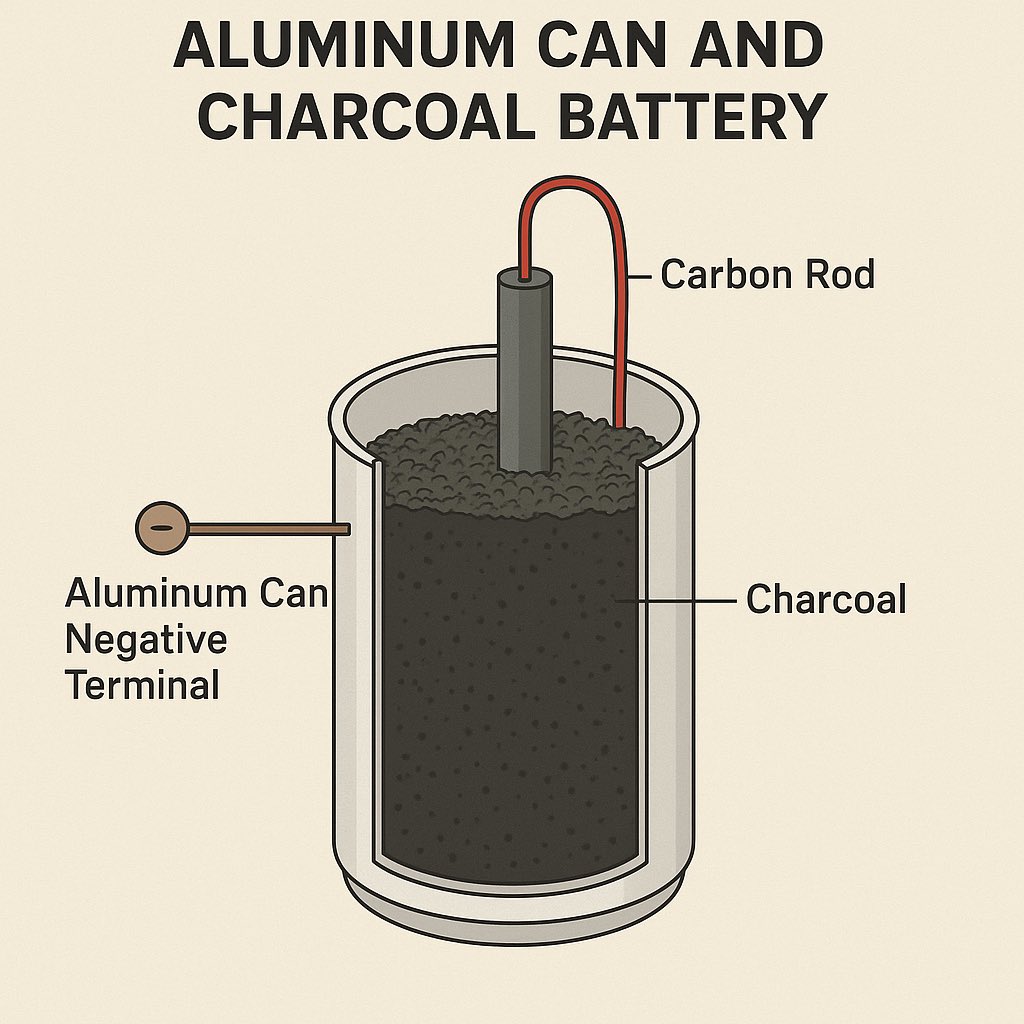
Aluminum Can + Charcoal Battery
Best For: Mid-level DIY, longer-lasting than saltwater.
Materials:
- Empty soda or beer can (aluminum)
- Charcoal (crushed into small chunks)
- Saltwater or vinegar
- Copper wire
- Cloth or paper towel
Instructions:
1.Fill the can with charcoal and soak with saltwater or vinegar.
2.Wrap copper wire around the outside of the can, leaving a free end.
3.Insert a galvanized nail into the charcoal as the other electrode.
4.Connect wires — copper is negative (-), nail is positive (+).
5.Chain multiple units together for more voltage.
Best For: Mid-level DIY, longer-lasting than saltwater.
Materials:
- Empty soda or beer can (aluminum)
- Charcoal (crushed into small chunks)
- Saltwater or vinegar
- Copper wire
- Cloth or paper towel
Instructions:
1.Fill the can with charcoal and soak with saltwater or vinegar.
2.Wrap copper wire around the outside of the can, leaving a free end.
3.Insert a galvanized nail into the charcoal as the other electrode.
4.Connect wires — copper is negative (-), nail is positive (+).
5.Chain multiple units together for more voltage.
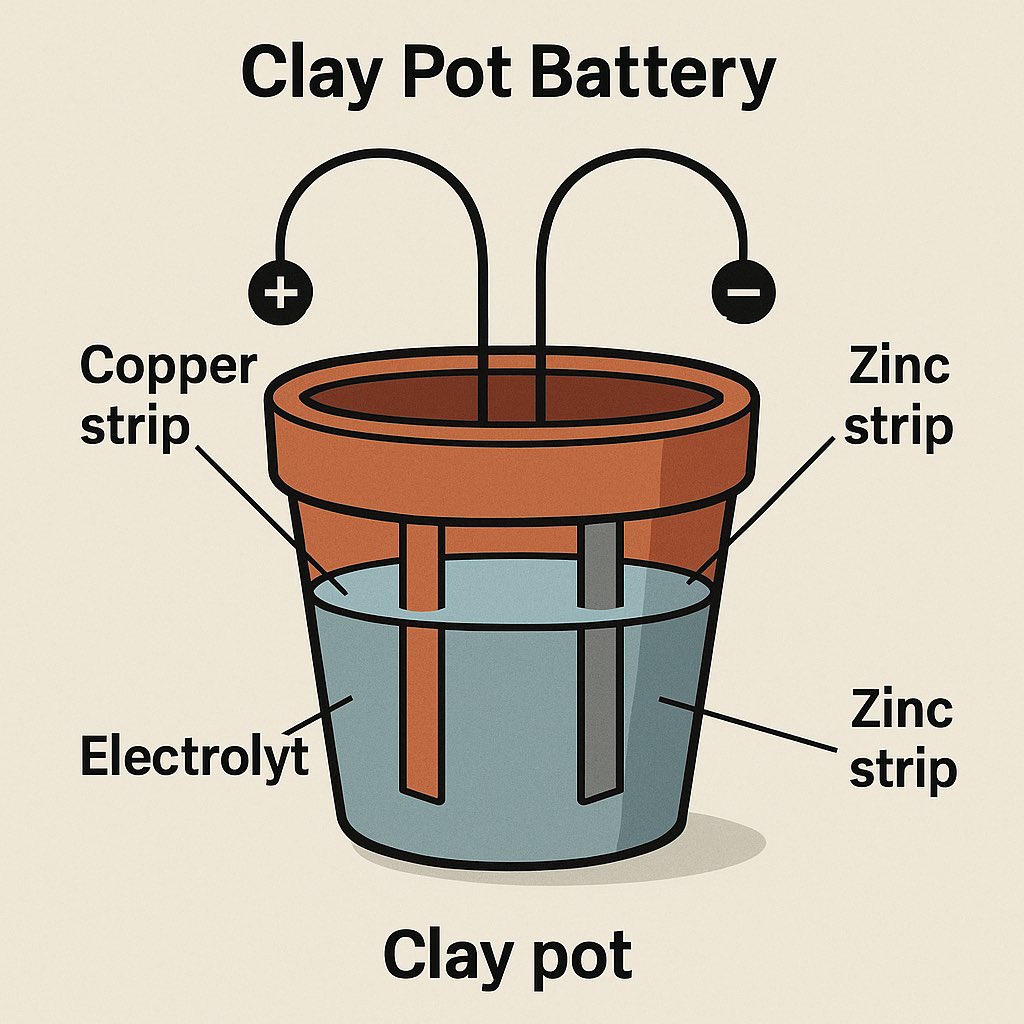
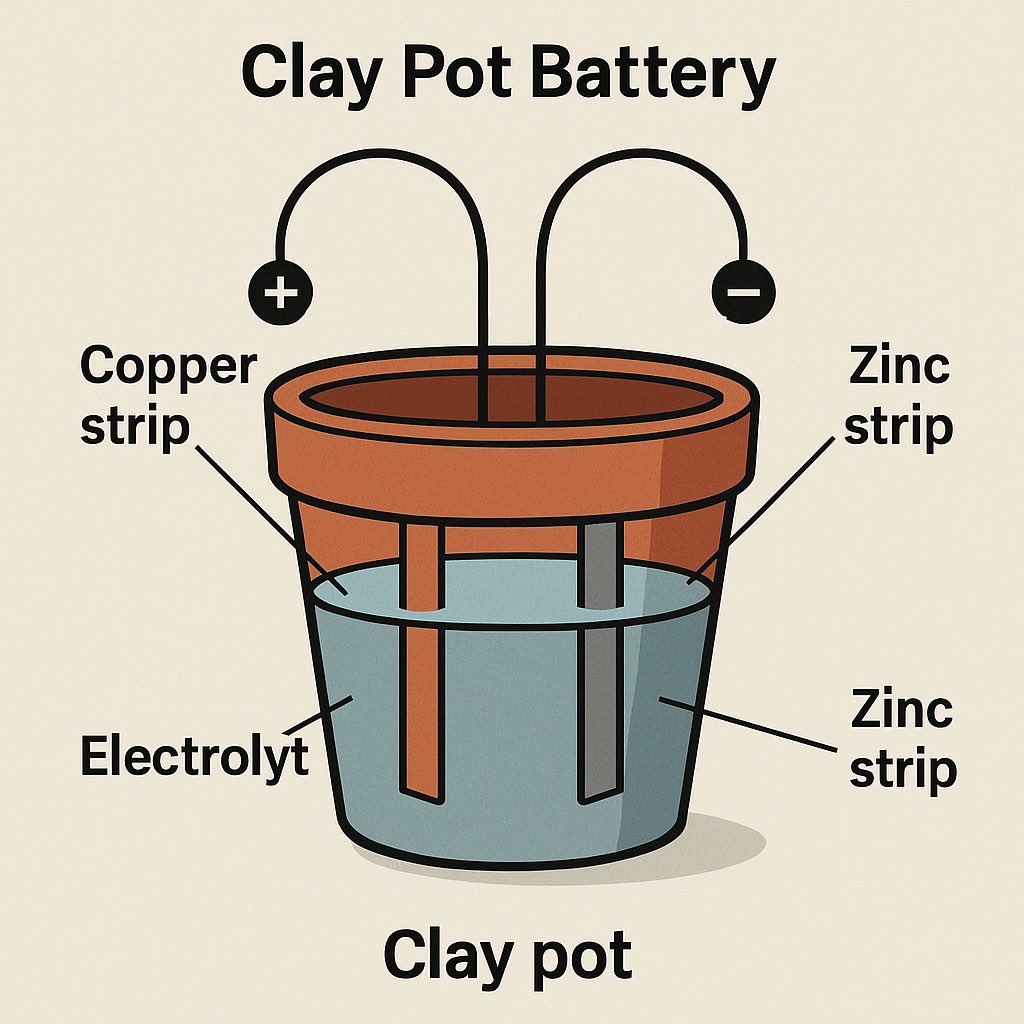
Clay Pot / Soil Battery (Ancient Tech)
Inspired by: The Baghdad Battery…
one of the oldest known power sources.
Materials:
- Clay pot or flowerpot
- Dirt or damp soil mixed with salt or vinegar
- Copper strip or wire
- Galvanized nail or scrap zinc
- Water to keep the soil moist
Instructions:
1.Fill the pot with the prepared soil.
2.Insert the copper strip on one side and zinc nail on the other.
3.Keep the soil damp for consistent conductivity.
4.Link several pots together for higher voltage.
Output:
Steady trickle charge, perfect for continuous low-power needs.
Inspired by: The Baghdad Battery…
one of the oldest known power sources.
Materials:
- Clay pot or flowerpot
- Dirt or damp soil mixed with salt or vinegar
- Copper strip or wire
- Galvanized nail or scrap zinc
- Water to keep the soil moist
Instructions:
1.Fill the pot with the prepared soil.
2.Insert the copper strip on one side and zinc nail on the other.
3.Keep the soil damp for consistent conductivity.
4.Link several pots together for higher voltage.
Output:
Steady trickle charge, perfect for continuous low-power needs.
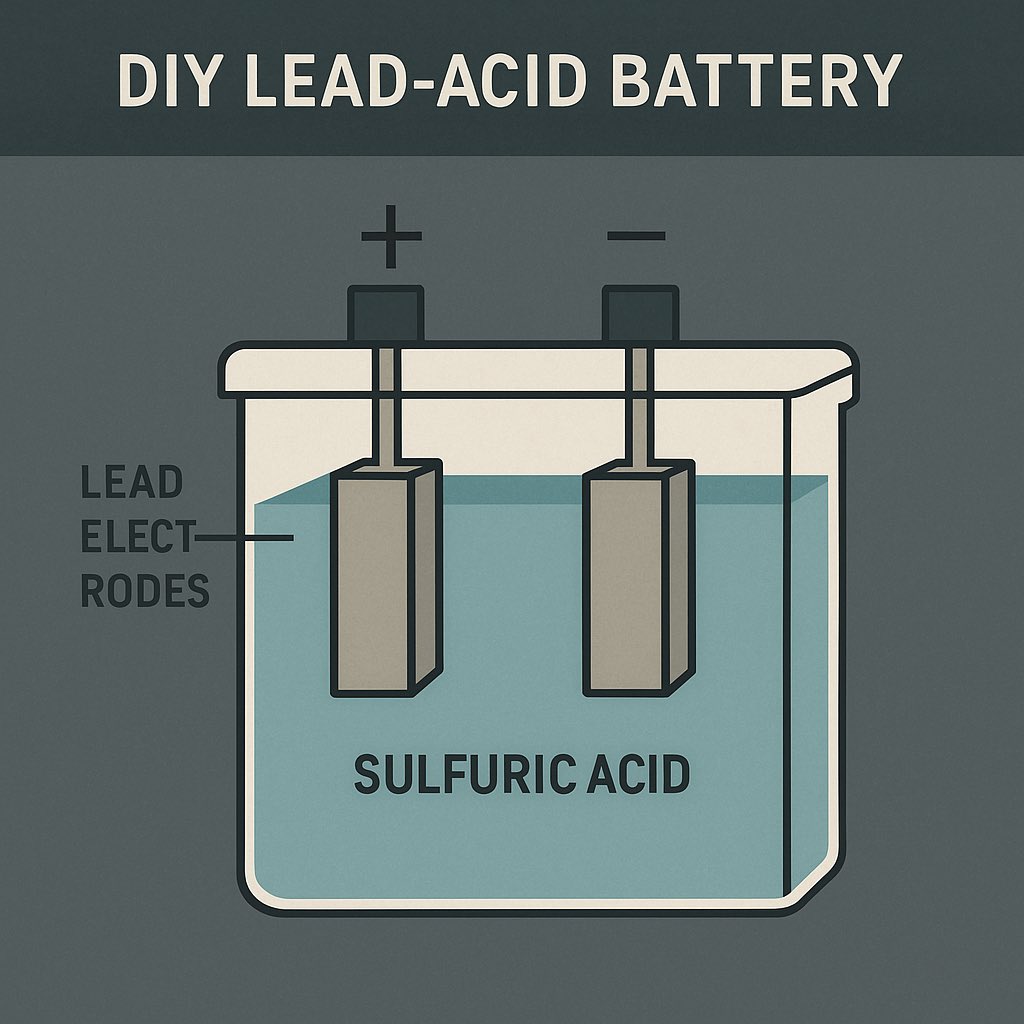
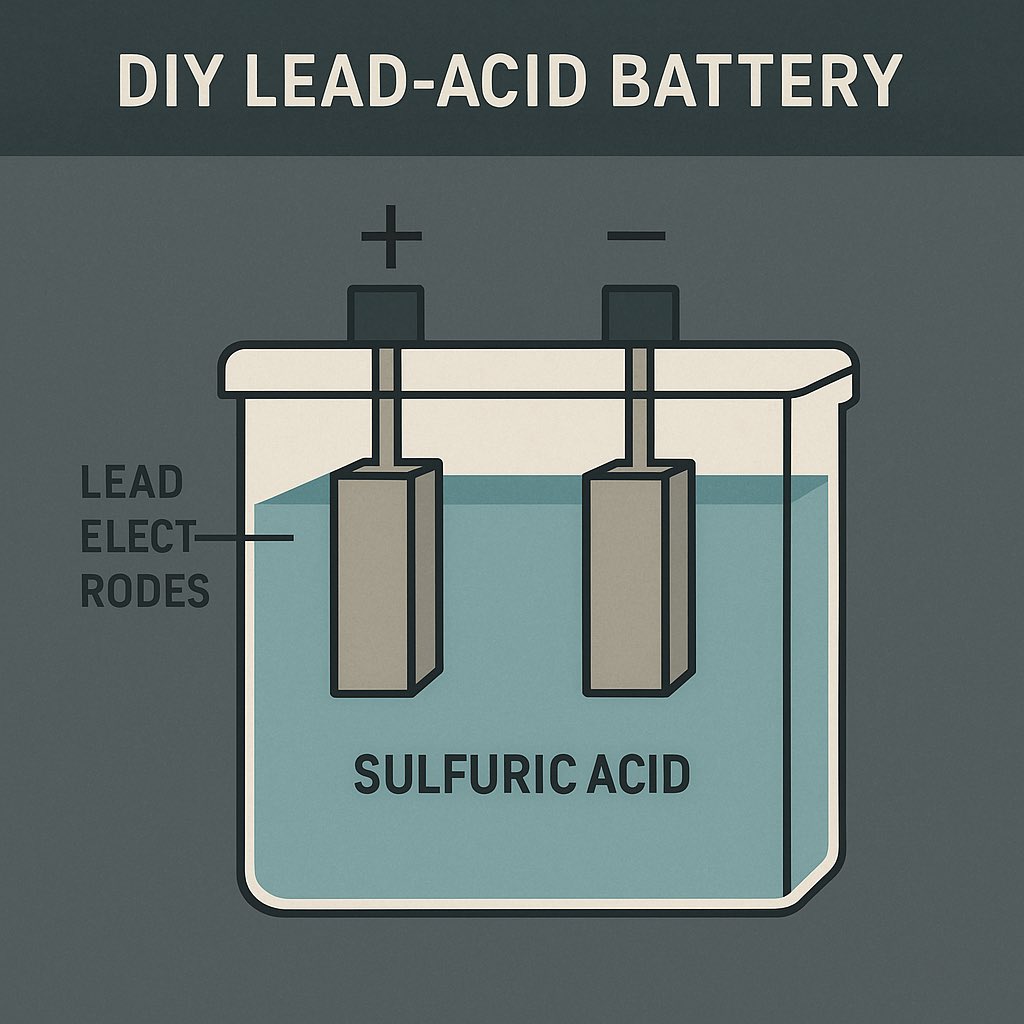
DIY Lead-Acid Battery (Advanced)
Best For: Serious off-grid storage, like powering an entire small solar system.
⚠ Warning: Use protective gear…
this involves acid.
Materials:
- Two lead plates or salvaged lead pieces
- Plastic container (like an old Tupperware or battery case)
- Sulfuric acid (can be sourced from old car batteries or diluted drain cleaner)
- Distilled water
- Wires and clips
Instructions:
1.Place lead plates into the container without touching.
2.Mix sulfuric acid with distilled water (carefully, always add acid to water, not water to acid).
3.Pour into the container to cover the plates.
4.Attach wires to the plates.
5.Connect to a solar panel or generator to charge.
Output:
Can store enough power to run LED lighting, small appliances, or emergency systems.
Best For: Serious off-grid storage, like powering an entire small solar system.
⚠ Warning: Use protective gear…
this involves acid.
Materials:
- Two lead plates or salvaged lead pieces
- Plastic container (like an old Tupperware or battery case)
- Sulfuric acid (can be sourced from old car batteries or diluted drain cleaner)
- Distilled water
- Wires and clips
Instructions:
1.Place lead plates into the container without touching.
2.Mix sulfuric acid with distilled water (carefully, always add acid to water, not water to acid).
3.Pour into the container to cover the plates.
4.Attach wires to the plates.
5.Connect to a solar panel or generator to charge.
Output:
Can store enough power to run LED lighting, small appliances, or emergency systems.
Scaling Your Battery Bank
Series Connection: Connect positive (+) to negative (-) to increase voltage.
Parallel Connection: Connect positive (+) to positive (+), negative (-) to negative (-) to increase capacity (run longer).
Example:
Four 1.5V saltwater batteries in series = 6 volts
Four 1.5V batteries in parallel = 1.5 volts, but 4x the runtime
Why DIY Batteries Matter
Commercial batteries are taxed, controlled, and regulated to keep people dependent on the grid.
When you build your own:
- You bypass corporate supply chains.
- You recycle waste into something valuable.
- You teach your community how energy is created and stored, breaking the illusion of scarcity.



Series Connection: Connect positive (+) to negative (-) to increase voltage.
Parallel Connection: Connect positive (+) to positive (+), negative (-) to negative (-) to increase capacity (run longer).
Example:
Four 1.5V saltwater batteries in series = 6 volts
Four 1.5V batteries in parallel = 1.5 volts, but 4x the runtime
Why DIY Batteries Matter
Commercial batteries are taxed, controlled, and regulated to keep people dependent on the grid.
When you build your own:
- You bypass corporate supply chains.
- You recycle waste into something valuable.
- You teach your community how energy is created and stored, breaking the illusion of scarcity.

Solar Energy: Harnessing the Sun
The sun constantly bombards the earth with more energy than humanity could ever use.
You don’t need expensive panels…
just focus, trap, or redirect it.
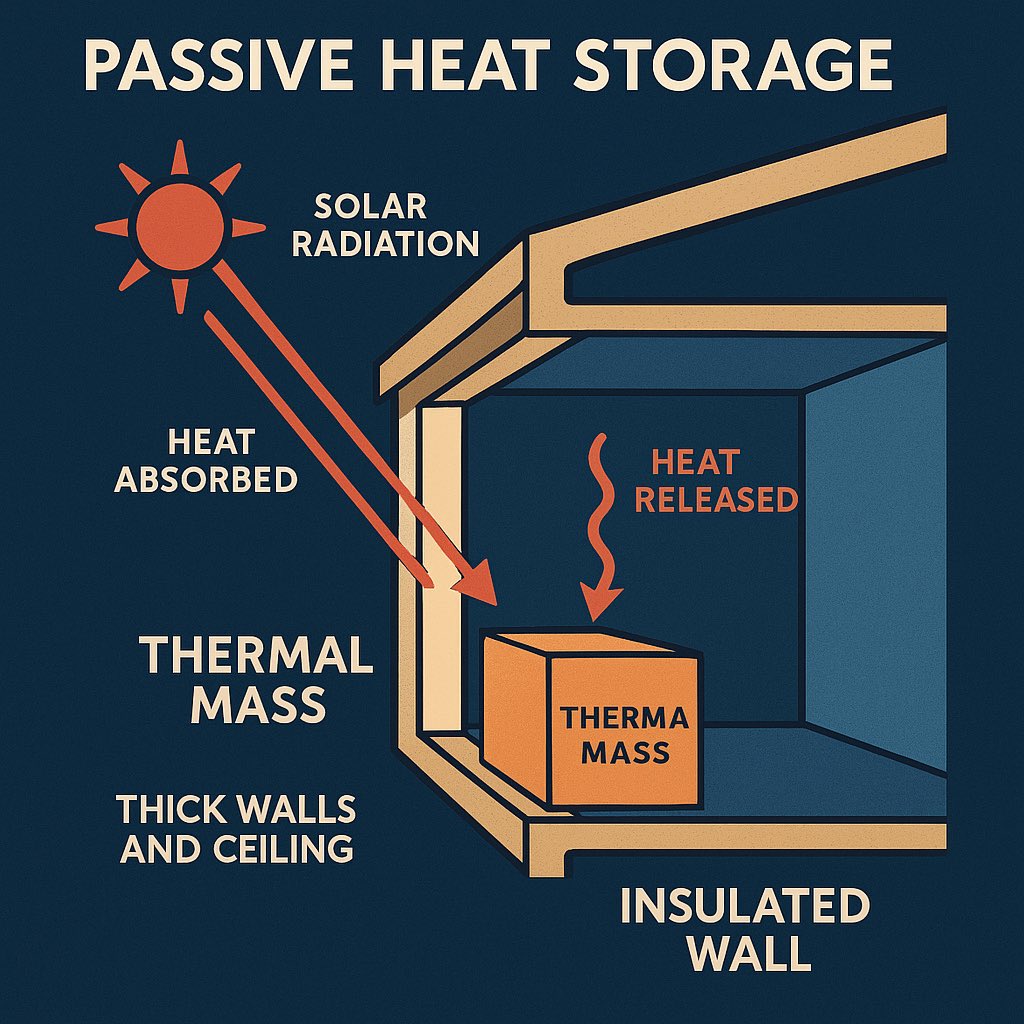
Passive Heat Storage
What You Need:
- Old barrels or buckets, painted black
- Clear plastic or glass sheet
How:
1.Fill barrels with water and place them in direct sunlight.
2.The black surface absorbs radiation, heating the water.
3.Use stored heat at night for warmth, cooking, or cleaning.
Uses: Free home heating, greenhouse warmth, hot showers.
The sun constantly bombards the earth with more energy than humanity could ever use.
You don’t need expensive panels…
just focus, trap, or redirect it.
Passive Heat Storage
What You Need:
- Old barrels or buckets, painted black
- Clear plastic or glass sheet
How:
1.Fill barrels with water and place them in direct sunlight.
2.The black surface absorbs radiation, heating the water.
3.Use stored heat at night for warmth, cooking, or cleaning.
Uses: Free home heating, greenhouse warmth, hot showers.
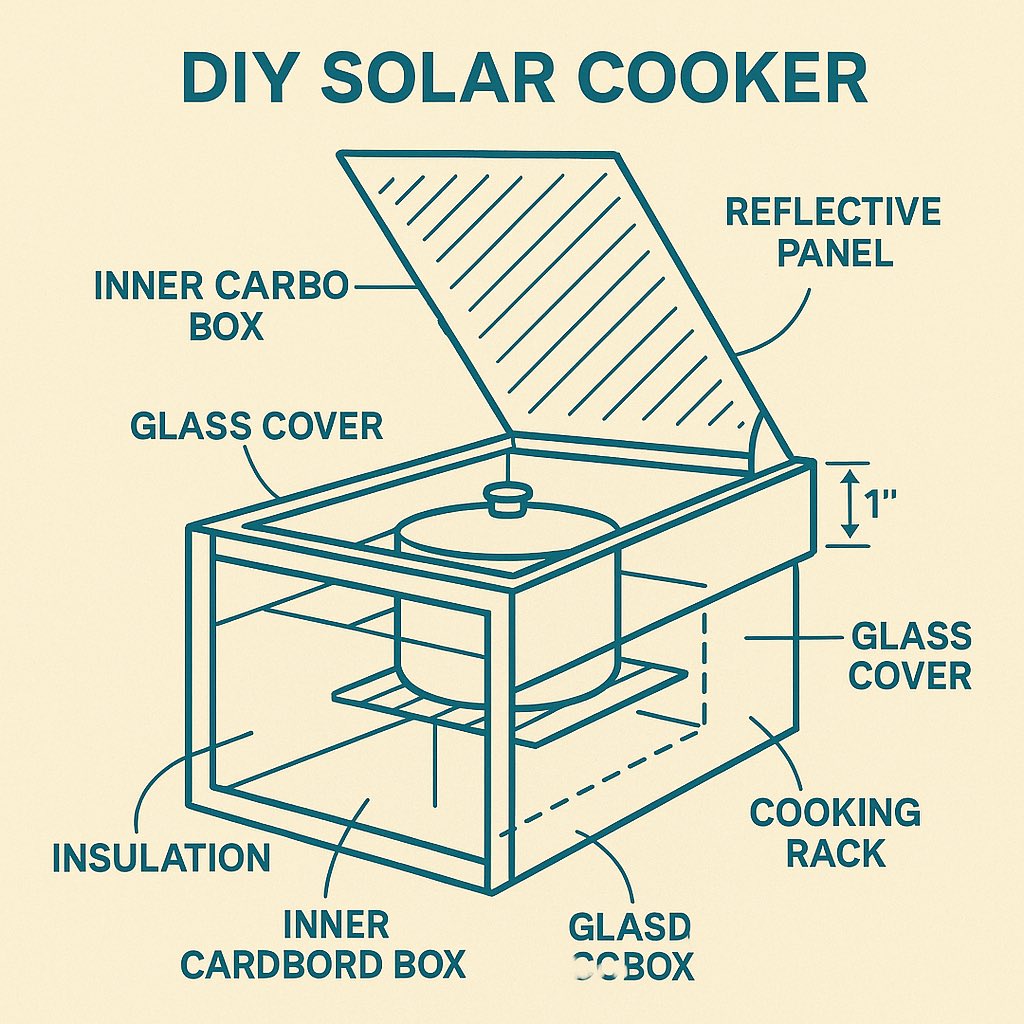
DIY Solar Cooker / Oven
What You Need:
- Cardboard box or wooden crate
- Black paint or soot
- Aluminum foil, broken mirrors, or even chip bags
- A piece of glass or clear plastic
How:
1.Paint the inside of the box black.
2.Line the lid with reflective material angled toward the sun.
3.Place food or water inside, cover with glass.
4.The sun’s heat becomes trapped… temperatures can reach 250°F (120°C).
Uses: Cooking food, sterilizing water, pasteurizing tools.
What You Need:
- Cardboard box or wooden crate
- Black paint or soot
- Aluminum foil, broken mirrors, or even chip bags
- A piece of glass or clear plastic
How:
1.Paint the inside of the box black.
2.Line the lid with reflective material angled toward the sun.
3.Place food or water inside, cover with glass.
4.The sun’s heat becomes trapped… temperatures can reach 250°F (120°C).
Uses: Cooking food, sterilizing water, pasteurizing tools.
DIY Solar Power: Step-by-Step
Purpose: Harness sunlight to create free, renewable energy for basic needs.
Materials (Free or Inexpensive to Salvage)
- 1 small solar panel (50–100W; broken or scratched panels work too — still produce power).
- 1 deep-cycle battery (can use an old car battery if free).
- 1 charge controller (prevents overcharging… $10–15 or salvaged).
- Wire (can be salvaged from old electronics).
- 12V LED light or USB charging adapter.
Optional: multimeter to test voltage.
How It Works
The solar panel captures sunlight and converts it into electricity.
The charge controller regulates the flow, preventing damage to the battery.
The battery stores energy for nighttime use.
Your devices or lights run directly off the battery.
Instructions
1.Place the Panel: Position it to face south (northern hemisphere) or north (southern hemisphere).
Angle it about 30–45°, tilted toward the sun.
2.Connect the Charge Controller: Run the positive (+) and negative (-) wires from the panel to the input terminals on the controller.
3.Connect the Battery: Run wires from the controller’s battery output to the battery terminals.
Red wire to positive, black to negative.
4.Connect Devices: Plug your 12V LED light, fan, or phone charger into the controller or directly into the battery (if it has ports).
What It Can Power
- 3–5 LED bulbs for lighting
- Phone charging and small electronics
- Portable fans or radios
- Emergency refrigeration with efficient coolers
Even a damaged solar panel produces usable energy.
The entire system can be built with scrap materials and requires zero technical expertise once the diagram is followed.
Purpose: Harness sunlight to create free, renewable energy for basic needs.
Materials (Free or Inexpensive to Salvage)
- 1 small solar panel (50–100W; broken or scratched panels work too — still produce power).
- 1 deep-cycle battery (can use an old car battery if free).
- 1 charge controller (prevents overcharging… $10–15 or salvaged).
- Wire (can be salvaged from old electronics).
- 12V LED light or USB charging adapter.
Optional: multimeter to test voltage.
How It Works
The solar panel captures sunlight and converts it into electricity.
The charge controller regulates the flow, preventing damage to the battery.
The battery stores energy for nighttime use.
Your devices or lights run directly off the battery.
Instructions
1.Place the Panel: Position it to face south (northern hemisphere) or north (southern hemisphere).
Angle it about 30–45°, tilted toward the sun.
2.Connect the Charge Controller: Run the positive (+) and negative (-) wires from the panel to the input terminals on the controller.
3.Connect the Battery: Run wires from the controller’s battery output to the battery terminals.
Red wire to positive, black to negative.
4.Connect Devices: Plug your 12V LED light, fan, or phone charger into the controller or directly into the battery (if it has ports).
What It Can Power
- 3–5 LED bulbs for lighting
- Phone charging and small electronics
- Portable fans or radios
- Emergency refrigeration with efficient coolers
Even a damaged solar panel produces usable energy.
The entire system can be built with scrap materials and requires zero technical expertise once the diagram is followed.

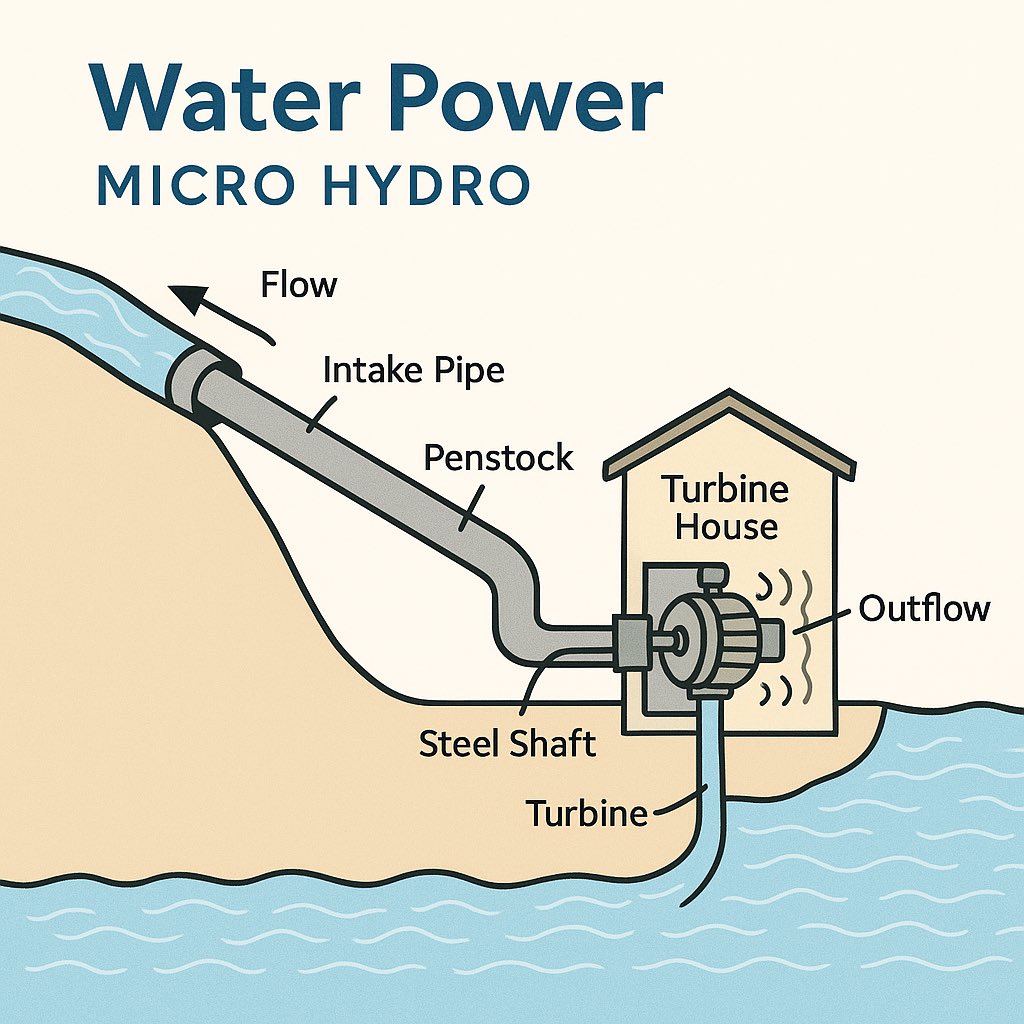
Water Power… Micro-Hydro
Running water equals constant kinetic energy… day and night.
Mini Water Wheel Generator
What You Need:
- Small stream or river access
- Salvaged bicycle wheel or wooden paddles
- DC motor (old treadmill, printer, or car alternator)
- Wire
How:
1.Attach paddles to the wheel or use spoons/plastic bottles as blades.
2.Place the wheel so water current spins it.
3.Connect the axle to a DC motor.
4.Run wires to a battery or device.
Uses: Powers off-grid cabins, lights, or radios.
Running water equals constant kinetic energy… day and night.
Mini Water Wheel Generator
What You Need:
- Small stream or river access
- Salvaged bicycle wheel or wooden paddles
- DC motor (old treadmill, printer, or car alternator)
- Wire
How:
1.Attach paddles to the wheel or use spoons/plastic bottles as blades.
2.Place the wheel so water current spins it.
3.Connect the axle to a DC motor.
4.Run wires to a battery or device.
Uses: Powers off-grid cabins, lights, or radios.
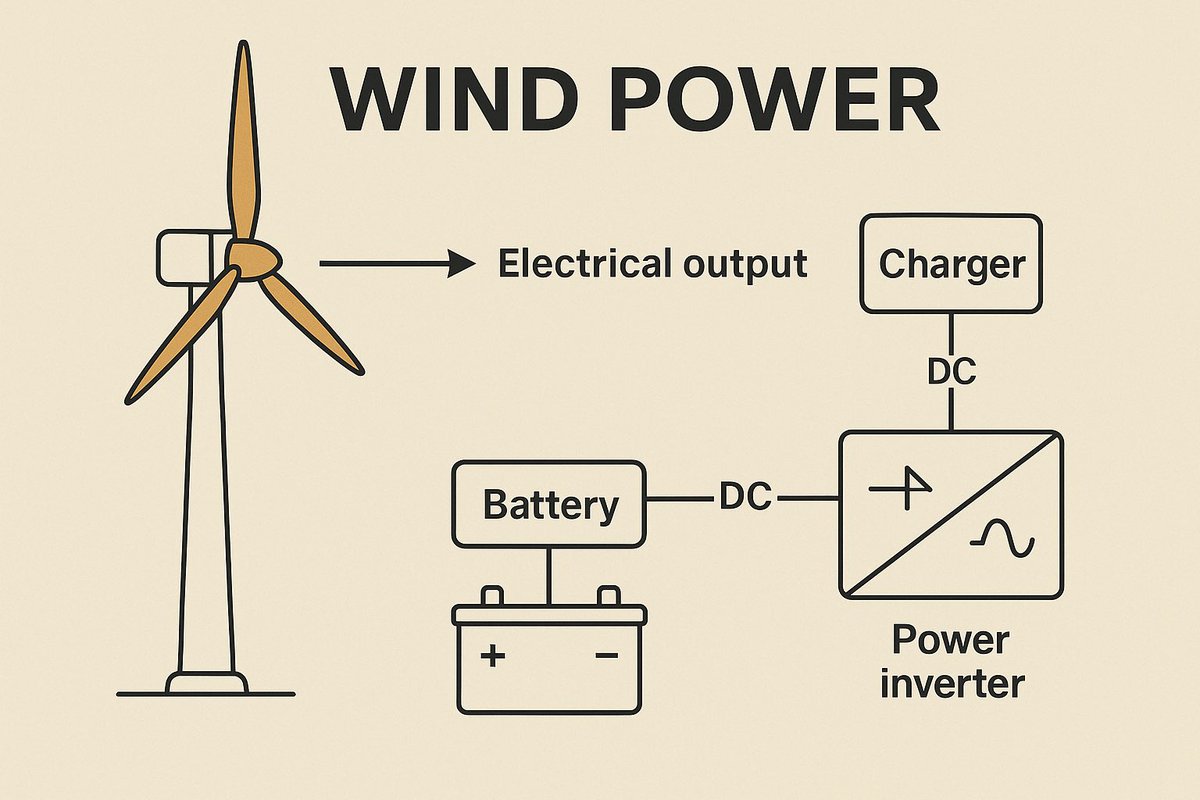
Wind Power: Simple Turbine
Wind is free movement… easy to capture with basic tools.
DIY Windmill
What You Need:
- Old fan blades or PVC pipes cut into blade shapes
- Salvaged car alternator or DC motor
- Tower or pole for mounting
- Wire
How:
1. Build a cross-shaped hub for blades.
2. Mount to a vertical pole in open space.
3. Connect spinning hub to motor shaft.
4. Wire to a battery or direct-use device.
Uses: Lighting, battery charging, supplemental power.
Wind is free movement… easy to capture with basic tools.
DIY Windmill
What You Need:
- Old fan blades or PVC pipes cut into blade shapes
- Salvaged car alternator or DC motor
- Tower or pole for mounting
- Wire
How:
1. Build a cross-shaped hub for blades.
2. Mount to a vertical pole in open space.
3. Connect spinning hub to motor shaft.
4. Wire to a battery or direct-use device.
Uses: Lighting, battery charging, supplemental power.
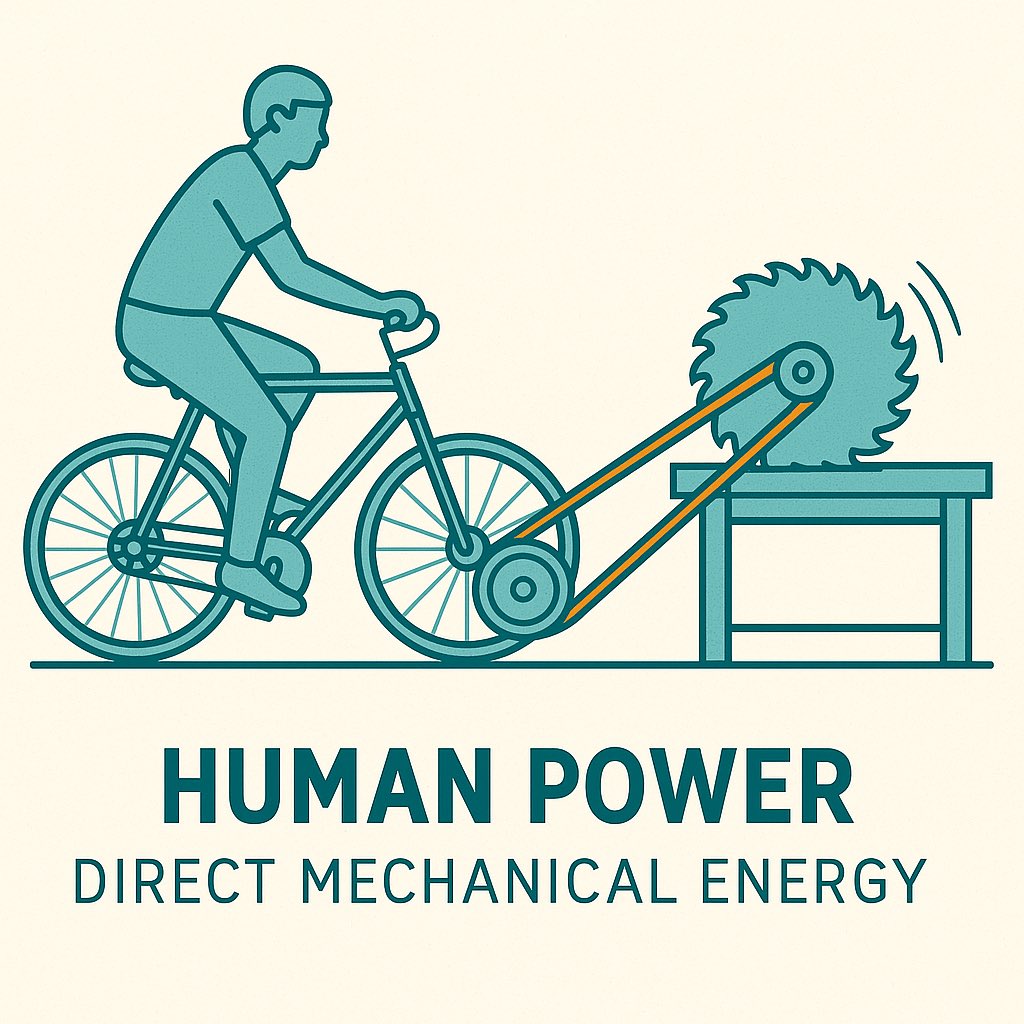
Human Power… Direct Mechanical Energy
When no natural forces are available, you are the generator.
Bicycle Generator
- What You Need:
- Old bicycle
- DC motor or alternator
- Belt or direct contact roller
- Wire and small battery
How:
1. Mount the bike frame securely.
2. Connect rear wheel to motor shaft with a belt or direct roller.
3. Pedal to generate electricity.
Uses: Charging devices, emergency lighting, radios.
When no natural forces are available, you are the generator.
Bicycle Generator
- What You Need:
- Old bicycle
- DC motor or alternator
- Belt or direct contact roller
- Wire and small battery
How:
1. Mount the bike frame securely.
2. Connect rear wheel to motor shaft with a belt or direct roller.
3. Pedal to generate electricity.
Uses: Charging devices, emergency lighting, radios.
Atmospheric Energy: Tesla Principles
The earth and sky are filled with natural electrical fields.
Static & Lightning Harvesting
What You Need:
- Copper wire
- Metal rod or long antenna
- Glass jar or ceramic insulator
How:
1. Place the metal rod high (on a tree or pole).
2. Run the wire to a jar wrapped in foil, sitting on a ceramic base.
3. This creates a crude capacitor to collect static energy.
Caution: This captures small amounts of energy safely… never during storms.
The earth and sky are filled with natural electrical fields.
Static & Lightning Harvesting
What You Need:
- Copper wire
- Metal rod or long antenna
- Glass jar or ceramic insulator
How:
1. Place the metal rod high (on a tree or pole).
2. Run the wire to a jar wrapped in foil, sitting on a ceramic base.
3. This creates a crude capacitor to collect static energy.
Caution: This captures small amounts of energy safely… never during storms.

Salvaged Heat Capture
You can store and redirect heat without electronics.
- Brick or Stone Floors: Absorb sun heat during the day, release it at night.
- Old Car Radiators: Use as heat exchangers for solar thermal systems.
- Reflective Insulation: Found in discarded packaging or old chip bags to focus or retain heat.
The natural world is overflowing with energy, yet the system convinces us it’s scarce so we’ll buy access to it.
These free methods aren’t about powering a smart city grid…
they’re about reclaiming independence, one small system at a time.
They tax your land, your water, and your sun,
but they can’t tax the ingenuity of a free mind.
You can store and redirect heat without electronics.
- Brick or Stone Floors: Absorb sun heat during the day, release it at night.
- Old Car Radiators: Use as heat exchangers for solar thermal systems.
- Reflective Insulation: Found in discarded packaging or old chip bags to focus or retain heat.
The natural world is overflowing with energy, yet the system convinces us it’s scarce so we’ll buy access to it.
These free methods aren’t about powering a smart city grid…
they’re about reclaiming independence, one small system at a time.
They tax your land, your water, and your sun,
but they can’t tax the ingenuity of a free mind.
• • •
Missing some Tweet in this thread? You can try to
force a refresh