🚨 We found a phishing time bomb in Yemen’s hijacked .YE ccTLD
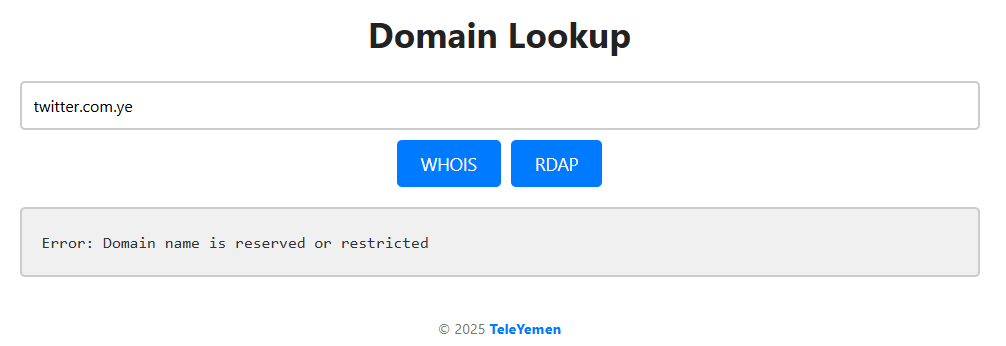
Domain: twitter[.com.ye]
RDAP: “reserved/restricted”
DNS + MX: point straight to Houthi-run servers in Sana’a.
Infra designed to impersonate @X / Twitter. 🧵
Domain: twitter[.com.ye]
RDAP: “reserved/restricted”
DNS + MX: point straight to Houthi-run servers in Sana’a.
Infra designed to impersonate @X / Twitter. 🧵
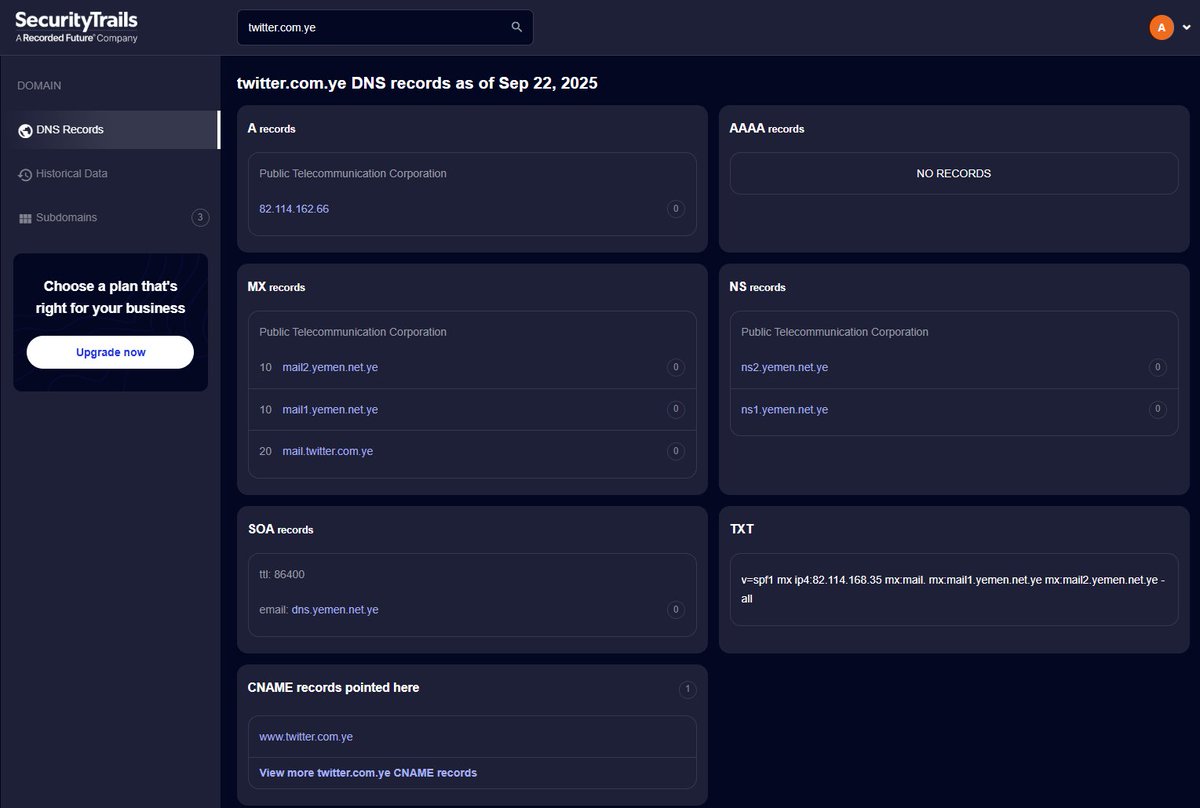
The proof:
• A Record → 82.114.162.66 (TeleYemen, Houthis controlled)
• MX → mail1/2.yemen.net.ye mail.twitter[.com.ye] (active, live mail routing)
• Web → geoblocked, but mail infra alive.
We found a purpose built phishing machine waiting for a target.
• A Record → 82.114.162.66 (TeleYemen, Houthis controlled)
• MX → mail1/2.yemen.net.ye mail.twitter[.com.ye] (active, live mail routing)
• Web → geoblocked, but mail infra alive.
We found a purpose built phishing machine waiting for a target.
This lets Houthis send @ twitter[.com.ye] emails to phish, steal logins, or deliver malware.
Digital deception becomes physical repression; targeting journalists, NGOs, activists inside & outside Yemen.
Digital deception becomes physical repression; targeting journalists, NGOs, activists inside & outside Yemen.
This isn't a bug; it's a feature of a hijacked TLD.
@ICANN has stayed silent since 2015, enabling a militia to weaponize a ccTLD. This is a catastrophic failure of internet trust with global implications.
Internet trust is collapsing.
We demand @EFF @AccessNow and others push for redelegation now.
@ICANN has stayed silent since 2015, enabling a militia to weaponize a ccTLD. This is a catastrophic failure of internet trust with global implications.
Internet trust is collapsing.
We demand @EFF @AccessNow and others push for redelegation now.
@ICANN @EFF @accessnow unroll @threadreaderapp
• • •
Missing some Tweet in this thread? You can try to
force a refresh