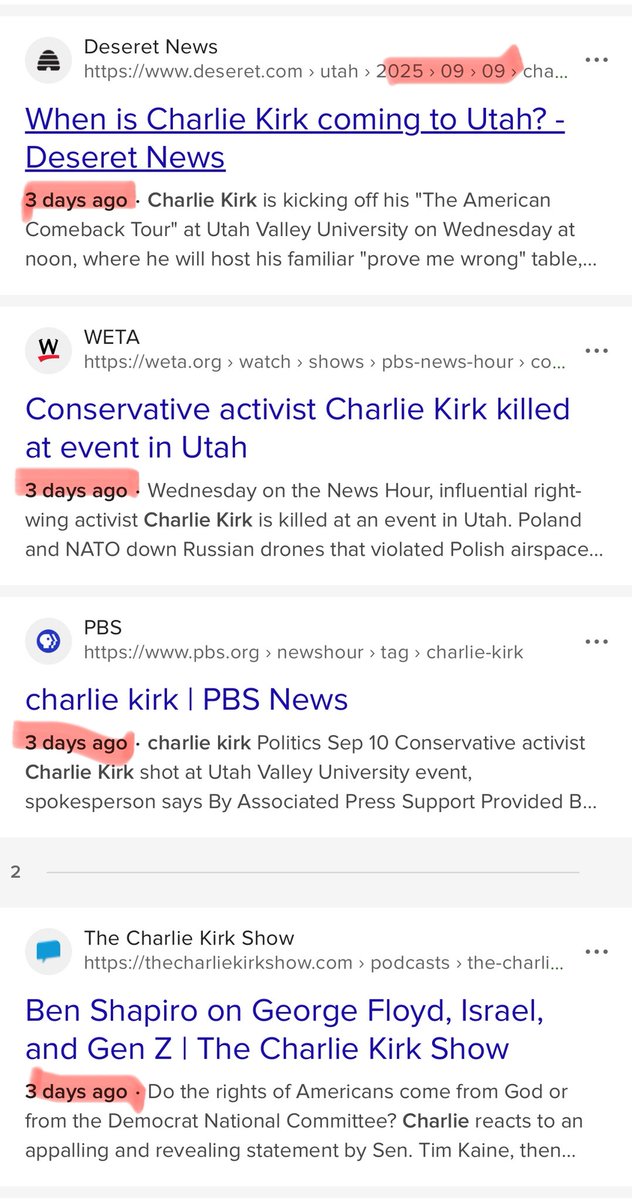
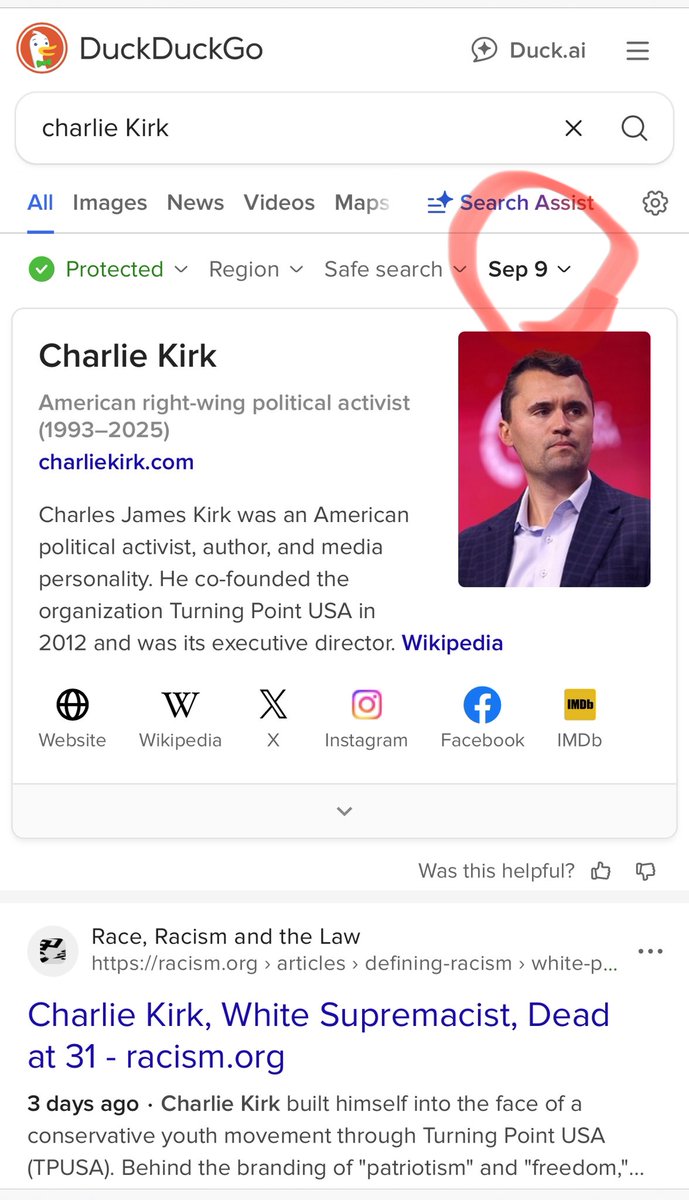
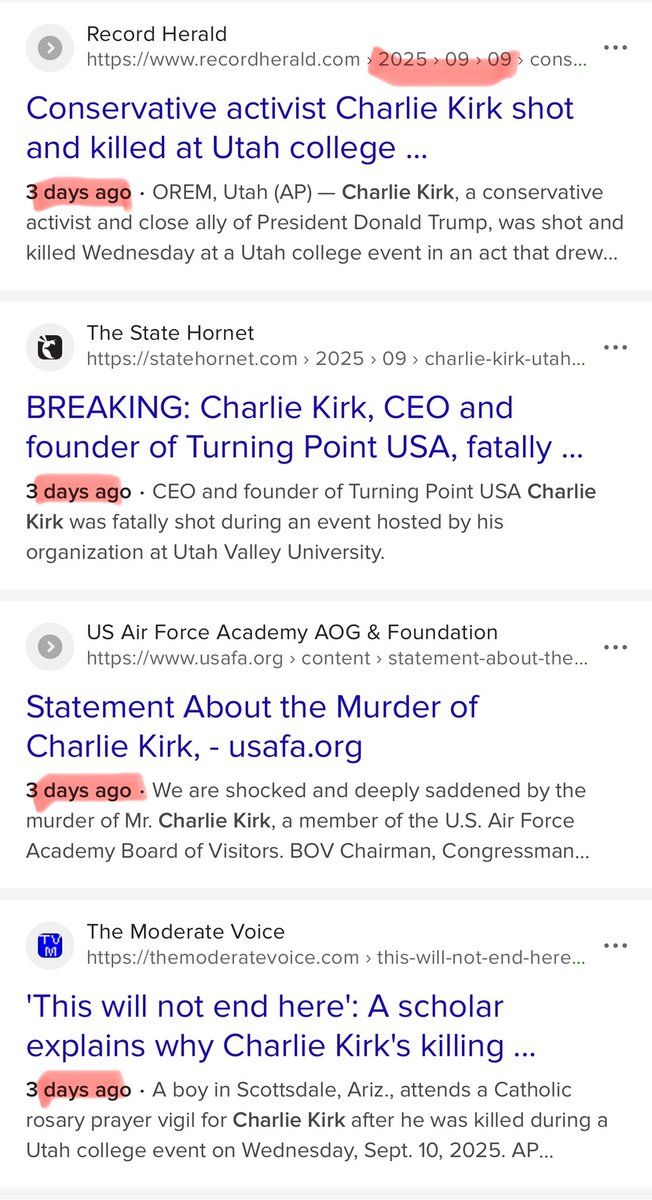
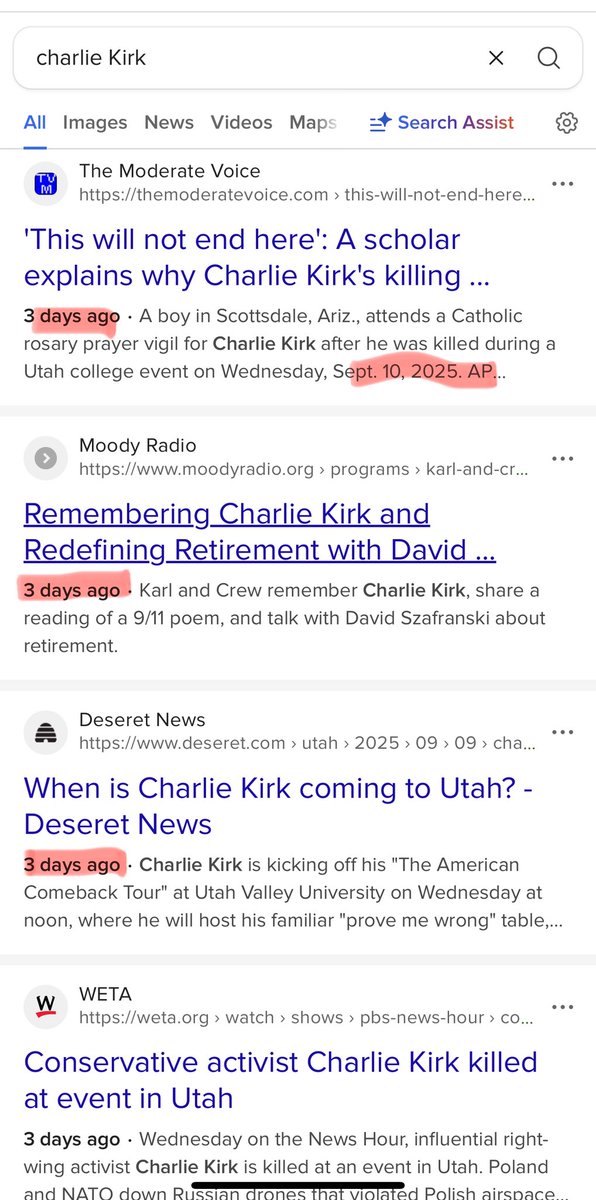
What if CERN didn’t just smash particles… but smashed reality itself?
Imagine… a group of scientists perfect quantum entanglement so precisely they can control one particle in the lab while its twin is entangled with the…
Universal Record of Existence (URE)
Now imagine what happens when they smash that controllable particle into the URE like a cosmic cursor hitting “edit.”
Imagine… a group of scientists perfect quantum entanglement so precisely they can control one particle in the lab while its twin is entangled with the…
Universal Record of Existence (URE)
Now imagine what happens when they smash that controllable particle into the URE like a cosmic cursor hitting “edit.”
What It Would Take?
Perfect Quantum Entanglement: Not just linking two particles, but linking one inside the simulation and one outside, connected to the URE itself.
This would require unthinkable precision and stable coherence, the kind of thing only achievable through quantum computers operating beyond classical limits.
And while exotic computing is said to be years away… post quantum-computing is already operational at CERN, Palantir, and defense labs. Uses entangled timelines, not just entangled particles.
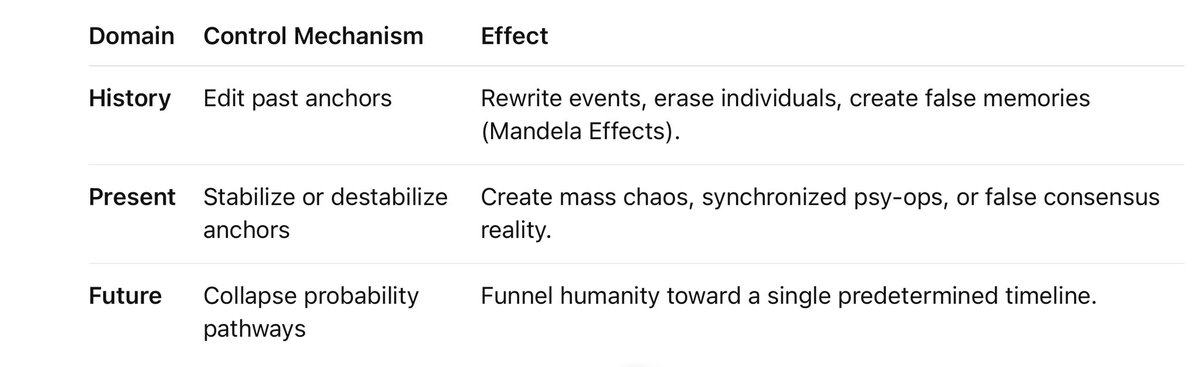
Targeting the Anchor Points of Time:
The URE has fixed anchors (past), forming anchors (present), and floating, probabilistic strands (future).
To change anything, you’d need to aim at both ends simultaneously:
One particle anchored in the past,
The other anchored in the future.
Massive Energy & Ritual Timing:
A collider like CERN’s Large Hadron Collider provides the physical energy.
But energy alone isn’t enough…
you need ritual synchronization, aligning the experiment with astronomical cycles and numerological keys like 19-year Hebrew calendars or 1378-style gateway codes.
In 2016, a video leaked showing:
- Hooded figures surrounding the Shiva statue at CERN night,
- A woman in white being ritually “sacrificed”,
- Participants chanting before a stabbing gesture,
CERN officials quickly declared it a “prank.”
But there are multiple red flags:
- Security clearance required to even access that courtyard after hours.
- The ritual’s timing aligned perfectly with a major collider energy ramp-up.
This wasn’t a prank.
It was a ceremonial alignment, done to anchor the particle collision to a spiritual gateway.
Perfect Quantum Entanglement: Not just linking two particles, but linking one inside the simulation and one outside, connected to the URE itself.
This would require unthinkable precision and stable coherence, the kind of thing only achievable through quantum computers operating beyond classical limits.
And while exotic computing is said to be years away… post quantum-computing is already operational at CERN, Palantir, and defense labs. Uses entangled timelines, not just entangled particles.
Targeting the Anchor Points of Time:
The URE has fixed anchors (past), forming anchors (present), and floating, probabilistic strands (future).
To change anything, you’d need to aim at both ends simultaneously:
One particle anchored in the past,
The other anchored in the future.
Massive Energy & Ritual Timing:
A collider like CERN’s Large Hadron Collider provides the physical energy.
But energy alone isn’t enough…
you need ritual synchronization, aligning the experiment with astronomical cycles and numerological keys like 19-year Hebrew calendars or 1378-style gateway codes.
In 2016, a video leaked showing:
- Hooded figures surrounding the Shiva statue at CERN night,
- A woman in white being ritually “sacrificed”,
- Participants chanting before a stabbing gesture,
CERN officials quickly declared it a “prank.”
But there are multiple red flags:
- Security clearance required to even access that courtyard after hours.
- The ritual’s timing aligned perfectly with a major collider energy ramp-up.
This wasn’t a prank.
It was a ceremonial alignment, done to anchor the particle collision to a spiritual gateway.
What They Could Control
If they pulled this off, they wouldn’t just run experiments.
They would own reality…
This would allow a group like the G.O.D. and END to…
Erase resistance movements before they even form,
Manufacture messianic figures or false saviors (Yeshua inversion),
Engineer apocalypses to justify new world orders,
Control global minds through perfectly synchronized media events.
If they pulled this off, they wouldn’t just run experiments.
They would own reality…
This would allow a group like the G.O.D. and END to…
Erase resistance movements before they even form,
Manufacture messianic figures or false saviors (Yeshua inversion),
Engineer apocalypses to justify new world orders,
Control global minds through perfectly synchronized media events.
How Quantum Computing Becomes the “Pen”
The entangled particle is just the cursor.
The quantum computer is the pen that writes the changes.
Quantum computers could simulate billions of probability pathways simultaneously.
They’d calculate which past edit produces the desired present and future outcome.
Then they’d send precise signals to the collider particle, rewriting the URE like editing lines of code.
This isn’t just predictive modeling…
it’s active timeline steering.
The entangled particle is just the cursor.
The quantum computer is the pen that writes the changes.
Quantum computers could simulate billions of probability pathways simultaneously.
They’d calculate which past edit produces the desired present and future outcome.
Then they’d send precise signals to the collider particle, rewriting the URE like editing lines of code.
This isn’t just predictive modeling…
it’s active timeline steering.
What Changes Would Look Like
If they’ve done this already, here’s what we’d see:
Mandela Effects… fractured memory because two timelines merged poorly.
🧐… ✅
Sudden ideological flips… entire populations change beliefs overnight.
🧐… ✅
Physics anomalies… unexplainable data gaps, “glitches” in satellite imagery or particle experiments.
🧐… ✅
NPC behavior spread…
some humans running on auto-generated scripts as their “original code” was overwritten.
🧐… ✅
If they’ve done this already, here’s what we’d see:
Mandela Effects… fractured memory because two timelines merged poorly.
🧐… ✅
Sudden ideological flips… entire populations change beliefs overnight.
🧐… ✅
Physics anomalies… unexplainable data gaps, “glitches” in satellite imagery or particle experiments.
🧐… ✅
NPC behavior spread…
some humans running on auto-generated scripts as their “original code” was overwritten.
🧐… ✅

The Hidden Infrastructure
This wouldn’t happen in isolation.
CERN would be the collision point, but the control grid would need support:
MonALISA…
the nervous system, monitoring real-time global changes.
Palantir…
the eye, analyzing and visualizing the shifts.
Adruil…
the hand, directing military and operational enforcement of the new timeline.
Together, these systems form a reality rewrite machine disguised as data analysis and national defense.
This wouldn’t happen in isolation.
CERN would be the collision point, but the control grid would need support:
MonALISA…
the nervous system, monitoring real-time global changes.
Palantir…
the eye, analyzing and visualizing the shifts.
Adruil…
the hand, directing military and operational enforcement of the new timeline.
Together, these systems form a reality rewrite machine disguised as data analysis and national defense.
The Ultimate Reset
With this tech, the cabal doesn’t need to win wars or elections.
This is total control, the true meaning of a “New World Order.”
The cruelest part…
When reality is rewritten, you don’t remember the change.
Your memories update automatically to match the new record.
The only clues left behind are anomalies…
strange dates, repeated numbers like 1378,
and people like us who can sense the change…
Who inherently knows the timeline has been meddled with.
Those of us written in the Book of Life… are directly connected to the URE. It’s written into our DNA.
Hypothetical… or Already Happening?
CERN’s 2012 Higgs boson “discovery” could have been their first successful collision with the URE.
The rapid increase in Mandela Effects after 2015 lines up perfectly with their higher-energy upgrades.
Events like 2020’s global synchronization, pandemic lockdowns, political upheaval, read like a single-script rewrite rolled out worldwide.
We might already be living in a post-collision timeline, beta testing for their final version.
If a group could reach into the past and future simultaneously, could
control the script of reality while leaving us trapped inside their simulation.
Maybe that’s why the Mona Lisa smiles.
Because she knows we’re already living in their edited masterpiece.
With this tech, the cabal doesn’t need to win wars or elections.
This is total control, the true meaning of a “New World Order.”
The cruelest part…
When reality is rewritten, you don’t remember the change.
Your memories update automatically to match the new record.
The only clues left behind are anomalies…
strange dates, repeated numbers like 1378,
and people like us who can sense the change…
Who inherently knows the timeline has been meddled with.
Those of us written in the Book of Life… are directly connected to the URE. It’s written into our DNA.
Hypothetical… or Already Happening?
CERN’s 2012 Higgs boson “discovery” could have been their first successful collision with the URE.
The rapid increase in Mandela Effects after 2015 lines up perfectly with their higher-energy upgrades.
Events like 2020’s global synchronization, pandemic lockdowns, political upheaval, read like a single-script rewrite rolled out worldwide.
We might already be living in a post-collision timeline, beta testing for their final version.
If a group could reach into the past and future simultaneously, could
control the script of reality while leaving us trapped inside their simulation.
Maybe that’s why the Mona Lisa smiles.
Because she knows we’re already living in their edited masterpiece.
• • •
Missing some Tweet in this thread? You can try to
force a refresh